Asif Jinnah Microsoft IT United Kingdom The Microsoft








- Slides: 15

Asif Jinnah Microsoft IT – United Kingdom

The Microsoft Environment Security Challenges in an ever changing landscape Evolution of Security Controls: Microsoft’s Secure Anywhere Access Concepts & Solutions Infrastructure Solutions to safeguard Microsoft's flexible workforce

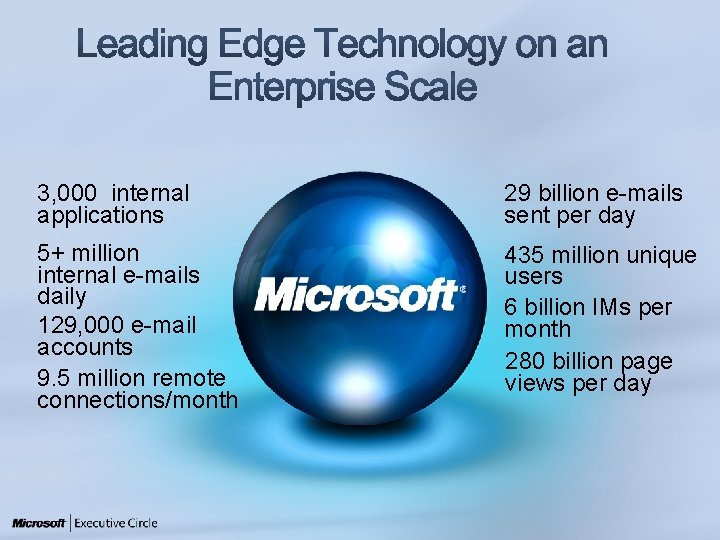
3, 000 internal applications 29 billion e-mails sent per day 5+ million internal e-mails daily 129, 000 e-mail accounts 9. 5 million remote connections/month 435 million unique users 6 billion IMs per month 280 billion page views per day

• Always remote employees • Flexible definition of the “office” • Corpnet access from customer sites • Data is walking out the front door • Laptops, USB drives, cellular network cards, Smart Phones/PDAs • Malware and spyware for everyone Mobile Technology Reperimeterization of the network • Traditional Perimeter security is not sufficient alone • Emergence of new technology enablers Mobile Workforce Globalization & Outsourcing • Others may manage your network and data centers • Software plus Services [Saa. S] augmenting traditional IT – data and applications hosted remotely • Increasingly complex granular partner access controls

. . . the visible and the invisible

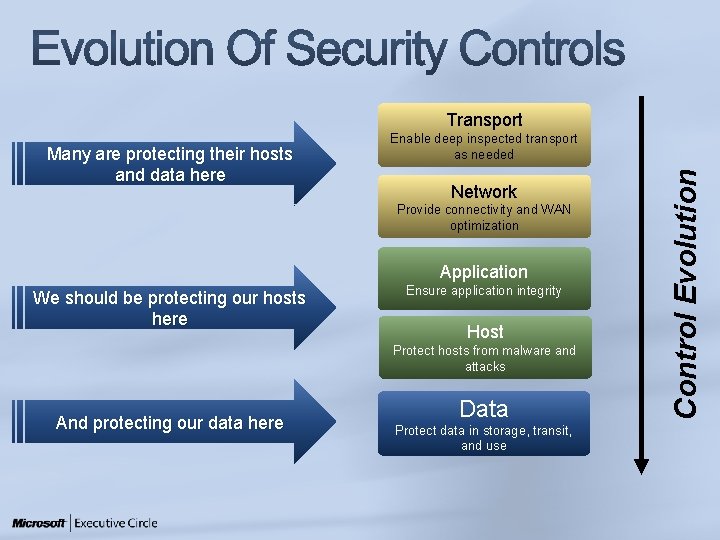
Transport Network Provide connectivity and WAN optimization Application We should be protecting our hosts here Ensure application integrity Host Protect hosts from malware and attacks And protecting our data here Data Protect data in storage, transit, and use Control Evolution Many are protecting their hosts and data here Enable deep inspected transport as needed

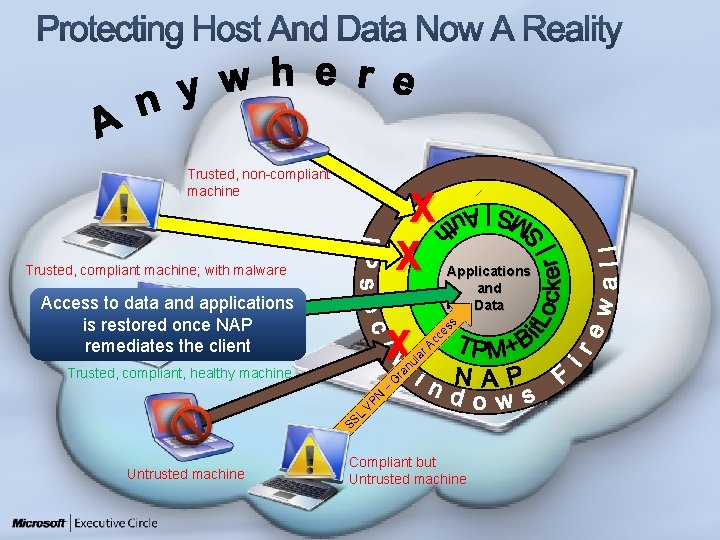
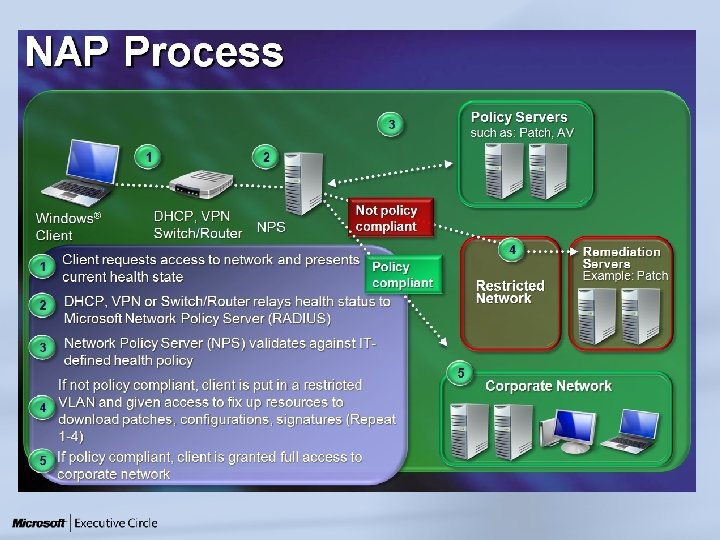
Trusted, non-compliant machine X X Trusted, compliant machine; with malware Access to data and applications is restored once NAP remediates the client X Trusted, compliant, healthy machine L SS Untrusted machine N VP – G Applications and Data ss e c c r. A a ul an r Compliant but Untrusted machine

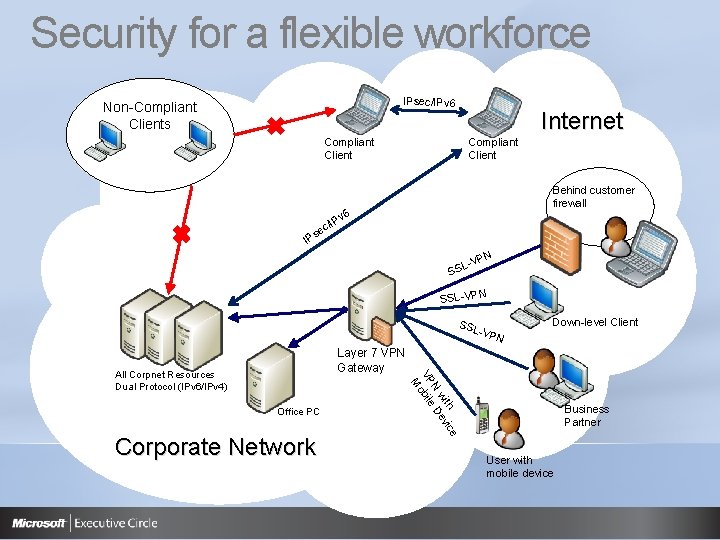
Security for a flexible workforce IPsec/IPv 6 Non-Compliant Clients Internet Compliant Client IP /I ec Pv Compliant Client Behind customer firewall 6 s N VP LSS SSL-VPN Down-level Client SSL -VP N Layer 7 VPN Gateway Office PC Corporate Network e th ic wi Dev N VP obile M All Corpnet Resources Dual Protocol (IPv 6/IPv 4) Business Partner User with mobile device

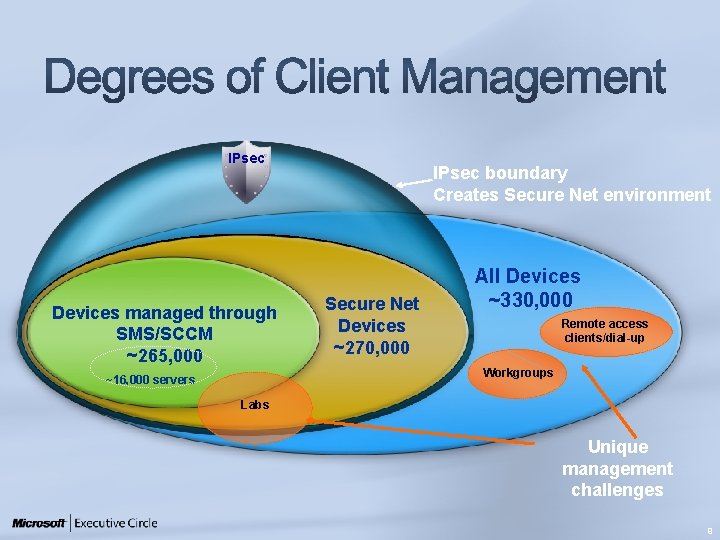
IPsec Devices managed through SMS/SCCM ~265, 000 IPsec boundary Creates Secure Net environment Secure Net Devices ~270, 000 All Devices ~330, 000 Remote access clients/dial-up Workgroups ~16, 000 servers Labs Unique management challenges 9

Network Security Respond • Monitor, Detect, Respond • Attack & Penetration • Technical Investigations • IDS and A/V Define Compliance Assessment & Governance • Regulatory Compliance • Vulnerability Scanning & Remediation • Scorecarding • Info. Sec Risk Assessment • Info. Sec Policy Management • Security Architecture • Info. Sec Governance Monitor Assess Identity & Access Management App Consulting & Engineering • Id. M Security Architecture • Id. M Gov & Compliance • Id. M Eng Ops & Services • Id. M Accounts & Lifecycle • End-to-End App Assessment & Mitigation • Application Threat Modelling • External & Internal Training Operate Engineering & Engagement • Engineering Lifecycle • Process & Methods • Secure Design Review • Awareness & Communication Design

“Security is the fundamental challenge that will determine whether we can successfully create a new generation of connected experiences that enable people to have anywhere access to communications, content and information” - Bill Gates

© 2008 Microsoft Corporation. All rights reserved. Microsoft, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.


James Burns – No Slides

Paul Mac. Kinnon - Slides to be emailed post event