Active Defense 1 0 Instructorled Training Jim Richards



- Slides: 11

Active. Defense 1. 0 Instructor-led Training Jim Richards Learning Programs Manager April 16, 2010

Identify Threats • Need help here

Investigate Threats • When a threat is detected or suspected, triage is the first step of the response process. • The first goal of the triage is to classify the threat, and to determine whether the detection is an incident or not. • The second goal of the triage is to collect salient information to support the formulation of a threat response strategy.

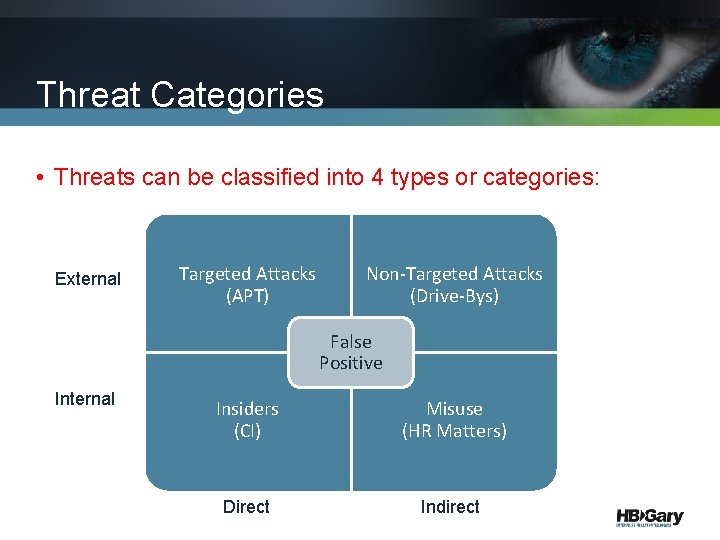
Threat Categories • Threats can be classified into 4 types or categories: External Targeted Attacks (APT) Non-Targeted Attacks (Drive-Bys) False Positive Internal Insiders (CI) Misuse (HR Matters) Direct Indirect

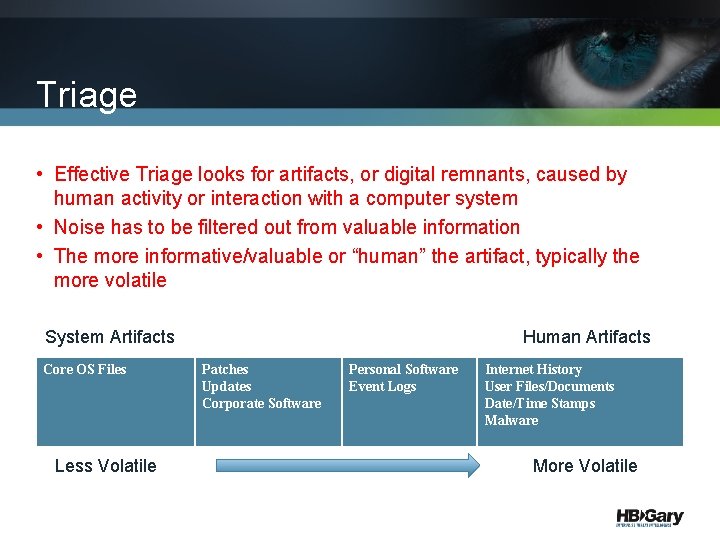
Triage • Effective Triage looks for artifacts, or digital remnants, caused by human activity or interaction with a computer system • Noise has to be filtered out from valuable information • The more informative/valuable or “human” the artifact, typically the more volatile System Artifacts Core OS Files Less Volatile Human Artifacts Patches Updates Corporate Software Personal Software Event Logs Internet History User Files/Documents Date/Time Stamps Malware More Volatile

Digital Artifacts • File System: • Event Logs • Events such as process start/stop, logon/logoff • Internet History Records • URLs accessed, Files downloaded • File System Metadata ($MFT) • Files Created/Accessed/Modified • Files • Malware/Droppers, Hack Tools, Exfil Data • Registry • Modified Keys (Services, Run) • MRU Keys (Open. Save. MRU, Last. Visited. MRU)

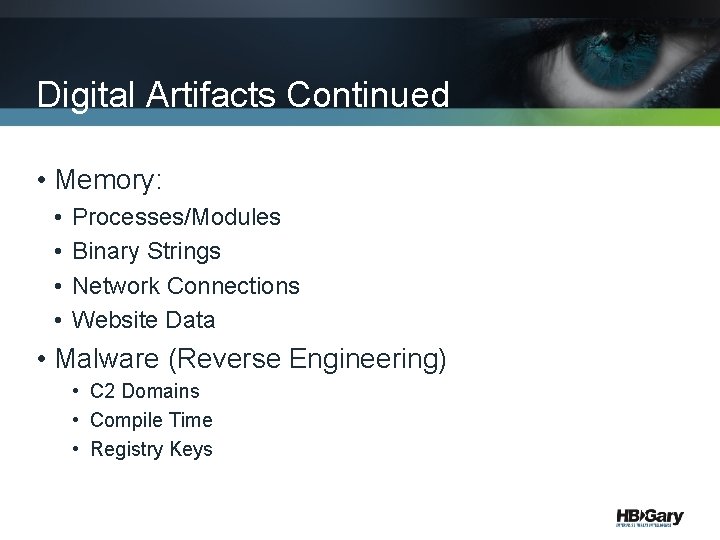
Digital Artifacts Continued • Memory: • • Processes/Modules Binary Strings Network Connections Website Data • Malware (Reverse Engineering) • C 2 Domains • Compile Time • Registry Keys

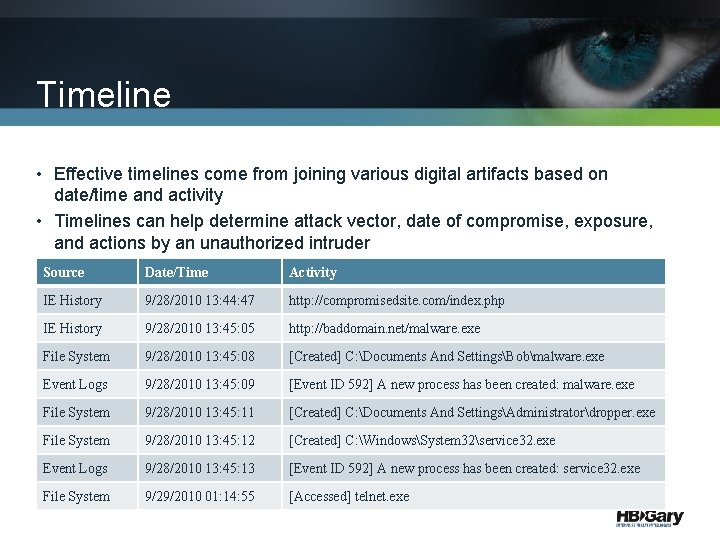
Timeline • Effective timelines come from joining various digital artifacts based on date/time and activity • Timelines can help determine attack vector, date of compromise, exposure, and actions by an unauthorized intruder Source Date/Time Activity IE History 9/28/2010 13: 44: 47 http: //compromisedsite. com/index. php IE History 9/28/2010 13: 45: 05 http: //baddomain. net/malware. exe File System 9/28/2010 13: 45: 08 [Created] C: Documents And SettingsBobmalware. exe Event Logs 9/28/2010 13: 45: 09 [Event ID 592] A new process has been created: malware. exe File System 9/28/2010 13: 45: 11 [Created] C: Documents And SettingsAdministratordropper. exe File System 9/28/2010 13: 45: 12 [Created] C: WindowsSystem 32service 32. exe Event Logs 9/28/2010 13: 45: 13 [Event ID 592] A new process has been created: service 32. exe File System 9/29/2010 01: 14: 55 [Accessed] telnet. exe

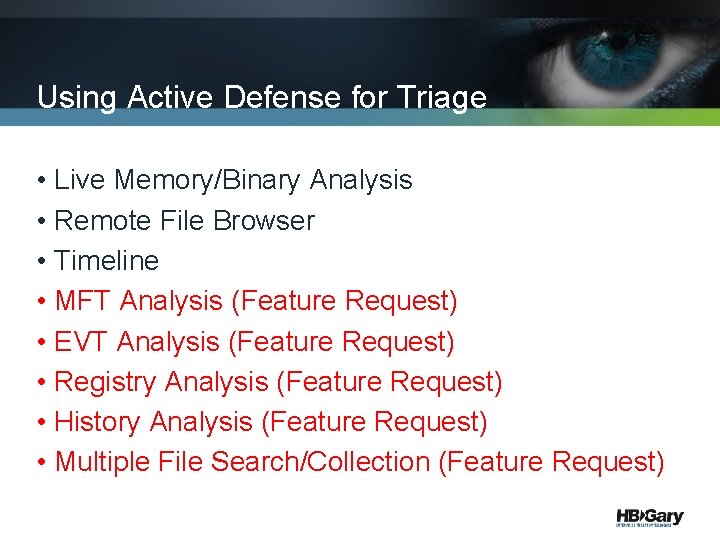
Using Active Defense for Triage • Live Memory/Binary Analysis • Remote File Browser • Timeline • MFT Analysis (Feature Request) • EVT Analysis (Feature Request) • Registry Analysis (Feature Request) • History Analysis (Feature Request) • Multiple File Search/Collection (Feature Request)

Remediate Threats • Extract Indicators of Compromise from Digital Artifacts: • • File Names Binary Strings Registry Keys File Metadata (Create/Access Time) • Scan Network Hosts for same IOCs • Clean Systems with Positive Hits

Reports