A Model for New Zealands Identity Verification Service








- Slides: 14

A Model for New Zealand’s Identity Verification Service Prof. Clark Thomborson Trust 2008 Villach, Austria 11 th March 2008

Objectives of this model n To study identification in a hierarchy, in a peerage, and in an aliased relationship. n n To develop a simple yet meaningful model of a complex identification management system. n n I believe these three types of relationships are of crucial importance in trusted computing. Case study: New Zealand’s Identification Verification System To distinguish three types of authentication: n “What you have”, “What you are”, and “What you know”. NZ IVS March 2008 2

The CEO Model 1. Credentials 2. Entities 3. Observations n n n An entity can disclose a self-signed credential, revealing its signing key. Entities can observe their inferiors and aliases. Entities reveal information about other entities to their superiors and aliases. NZ IVS March 2008 3

Three Types of Relationships Hierarchical: A superior observes its inferiors. An inferior entity discloses “everything” to their superior. A superior discloses only its signing key to its inferiors. n n This is a Bell – La Padula system. Superiors do not disclose to inferiors. Inferiors can not observe superiors. Peering: A peer does not disclose their personal identifiers to other peers. Peers cannot observe each other. n n n Peers share an pseudonym: their Peer Identifier. Peers can vote anonymously. Organisations (whether hierarchical or peering) can communicate via any entity which has an alias in each organisation. n n n Aliased entities managed the “bridging relationships” defined in my previous writing. Aliases are observable. Our aliases will publish credentials to their superiors, and are thus a security risk to a confidential hierarchy. NZ IVS March 2008 4

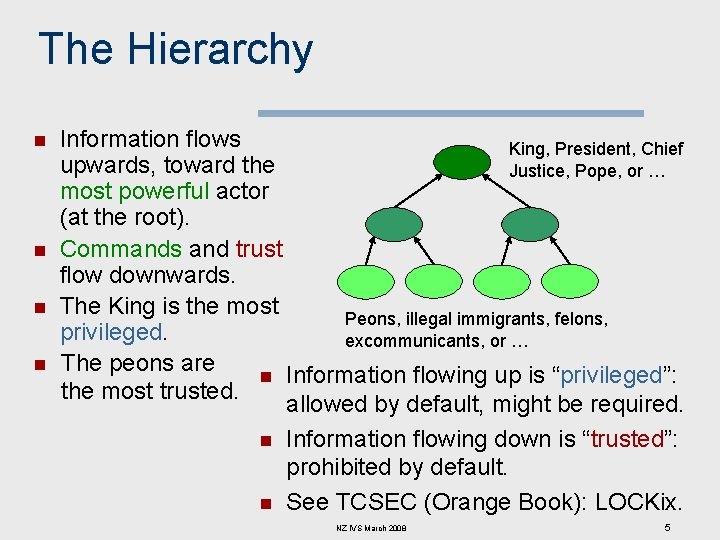
The Hierarchy n n Information flows King, President, Chief upwards, toward the Justice, Pope, or … most powerful actor (at the root). Commands and trust flow downwards. The King is the most Peons, illegal immigrants, felons, privileged. excommunicants, or … The peons are n Information flowing up is “privileged”: the most trusted. allowed by default, might be required. n Information flowing down is “trusted”: prohibited by default. n See TCSEC (Orange Book): LOCKix. NZ IVS March 2008 5

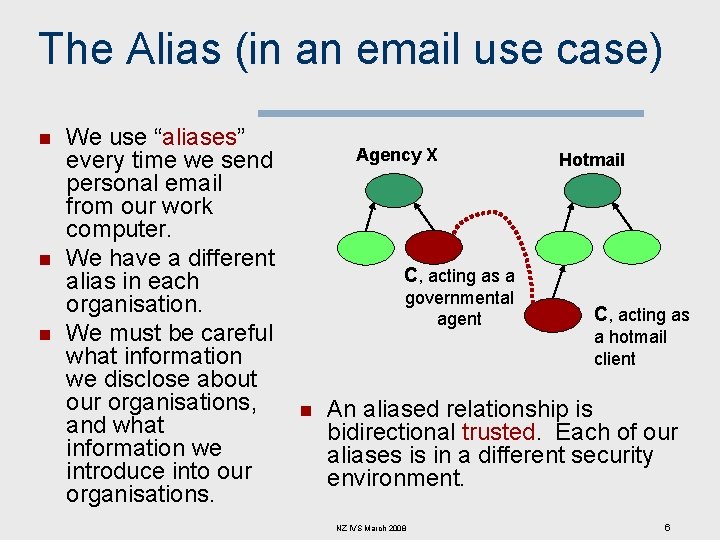
The Alias (in an email use case) n n n We use “aliases” every time we send personal email from our work computer. We have a different alias in each organisation. We must be careful what information we disclose about our organisations, and what information we introduce into our organisations. Agency X Hotmail C, acting as a governmental agent n C, acting as a hotmail client An aliased relationship is bidirectional trusted. Each of our aliases is in a different security environment. NZ IVS March 2008 6

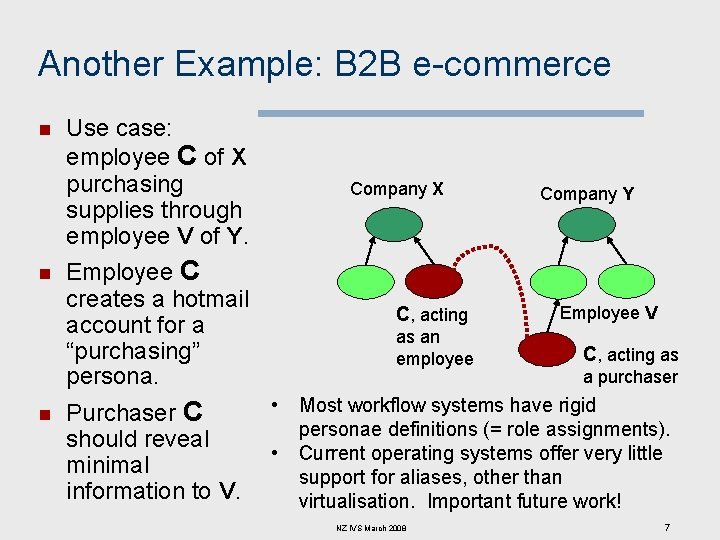
Another Example: B 2 B e-commerce n n n Use case: employee C of X purchasing supplies through employee V of Y. Company X Employee C creates a hotmail account for a “purchasing” persona. Purchaser C should reveal minimal information to V. C, acting as an employee • • Company Y Employee V C, acting as a purchaser Most workflow systems have rigid personae definitions (= role assignments). Current operating systems offer very little support for aliases, other than virtualisation. Important future work! NZ IVS March 2008 7

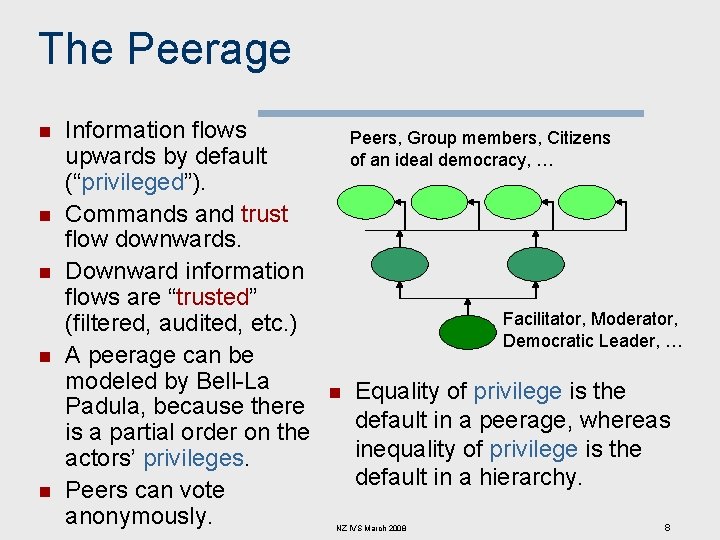
The Peerage n n n Information flows upwards by default (“privileged”). Commands and trust flow downwards. Downward information flows are “trusted” (filtered, audited, etc. ) A peerage can be modeled by Bell-La Padula, because there is a partial order on the actors’ privileges. Peers can vote anonymously. Peers, Group members, Citizens of an ideal democracy, … Facilitator, Moderator, Democratic Leader, … n Equality of privilege is the default in a peerage, whereas inequality of privilege is the default in a hierarchy. NZ IVS March 2008 8

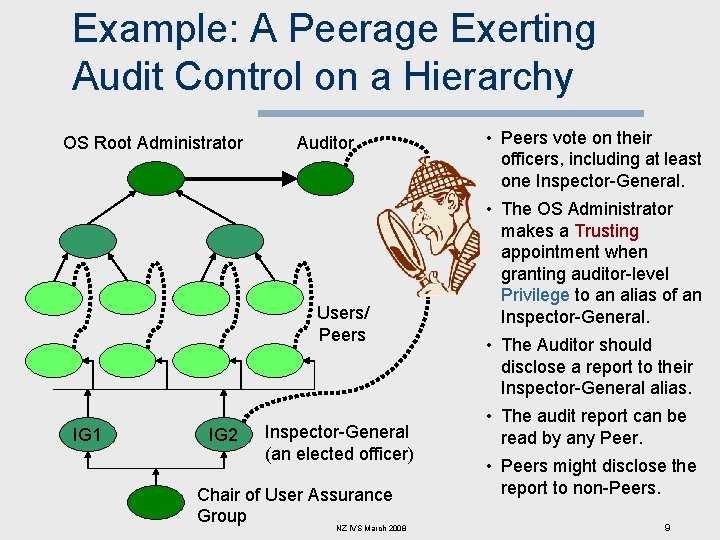
Example: A Peerage Exerting Audit Control on a Hierarchy OS Root Administrator Auditor Users/ Peers IG 1 IG 2 Inspector-General (an elected officer) Chair of User Assurance Group NZ IVS March 2008 • Peers vote on their officers, including at least one Inspector-General. • The OS Administrator makes a Trusting appointment when granting auditor-level Privilege to an alias of an Inspector-General. • The Auditor should disclose a report to their Inspector-General alias. • The audit report can be read by any Peer. • Peers might disclose the report to non-Peers. 9

Application to Identity Management n The system on the preceding slide has very complex security objectives. n n Each entity has complex capabilities, privileges, and trusting relationships with other entities. See the ECO extension of Secure Tropos (Giorgini et al. , 2006). Roughly: “privilege” = “entitlement”. I don’t want to get bogged down on TC UAGs here, but let’s talk offline if you want to help me create one! The CEO model is greatly simplified. n CEO entities have very simple privileges, trusts, capabilities, and objectives – suitable only for identity management systems. NZ IVS March 2008 10

Observations in the CEO model Hierarchical: a superior can observe its inferiors, but an inferior cannot observe its superior. n n n A superior has just one privilege: it can see the “observable identity” (Ob. Id) of all inferiors. Application: a surveillance camera in a workplace can collect biometric data on all employees and visitors. Peering: a peer cannot observe its peers. n n Peers share a Peer Identity (Peer. Id) but are otherwise anonymous. There are two types of entities. n n n Active entities can observe the Ob. Id of all their aliases, and will disclose this information (in a credential) to their superior. Passive entities can be observed, but cannot disclose credentials. Application: our identification tokens are active aliases. Application: any database record that contains one of our identifiers is a passive alias. NZ IVS March 2008 11

Disclosures in the CEO model Hierarchical: inferiors disclose their Peer. Id to their superior. Alias: active entities observe the Ob. Id of all their aliases. Alias: active entities disclose “everything they know” to their other aliases. Hierarchical: inferiors disclose “everything they know” to their superior. n n A CEO model of an identification management system n n will help us explain it; will help us figure out “who learns what” (identification vs. preservation of anonymity); will help us prove that its credentials guarantee a uniqueness property. NZ IVS March 2008 12

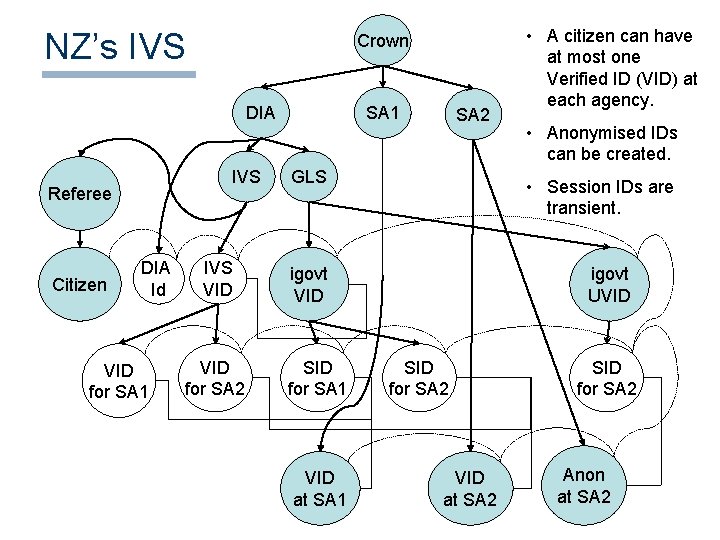
NZ’s IVS Crown DIA IVS Referee Citizen DIA Id VID for SA 1 IVS VID for SA 2 SA 1 SA 2 GLS VID at SA 1 • Anonymised IDs can be created. • Session IDs are transient. igovt VID SID for SA 1 • A citizen can have at most one Verified ID (VID) at each agency. igovt UVID SID for SA 2 VID at SA 2 SID for SA 2 Anon at SA 2

Did I meet my objectives? n To study identification in a hierarchy, in a peerage, and in an aliased relationship. n n To develop a simple yet meaningful model of a complex identification management system. n n Do you understand these relationships? (Do you agree that they are crucial in trusted computing? ) Do you understand how New Zealand’s Identification Verification System would provide semi-anonymous and semi-unique credentials? To distinguish three types of authentication. n Do you believe that the CEO model could distinguish “What you have”, “What you are”, and “What you know”? NZ IVS March 2008 14
 New zealands tests positive
New zealands tests positive Aristotle age verification
Aristotle age verification Ecfmg founded
Ecfmg founded New mexico board of pharmacy license verification
New mexico board of pharmacy license verification Sandata evv arizona
Sandata evv arizona New service development
New service development Social identity mapping
Social identity mapping V model verification and validation
V model verification and validation Deped order no. 31 s. 2019
Deped order no. 31 s. 2019 Forrester identity management
Forrester identity management Fim password reset
Fim password reset Gov.uk verify barclays
Gov.uk verify barclays A new national identity section 1
A new national identity section 1 A new national identity section 1
A new national identity section 1 Kontinuitetshantering i praktiken
Kontinuitetshantering i praktiken