4 1 General Requirements n n Develop implement
















- Slides: 18


4. 1 General Requirements n n Develop, implement, maintain and continually improve a documented ISMS Process based on PDCA

4. 2 Establishing and Managing the ISMS n n Estalish the ISMS Implement and operate the ISMS Monitor and review the ISMS Maintain and improve the ISMS

4. 3 Documentation Requirements n n n General Control of documents Control of records

Extent of ISMS Documentation n Range and details depend upon n n n complexity of products and processes customer and regulatory requirements industry standards and codes education, experence and training workforce stability past security problems

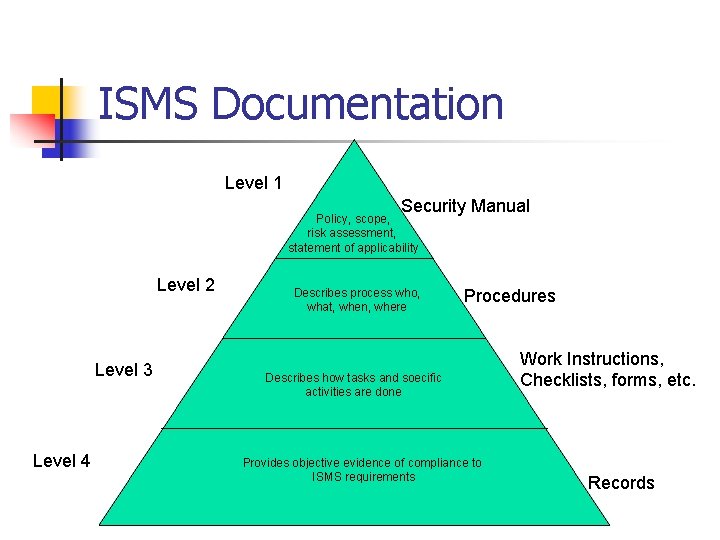
ISMS Documentation Level 1 Security Manual Policy, scope, risk assessment, statement of applicability Level 2 Level 3 Level 4 Describes process who, what, when, where Procedures Describes how tasks and soecific activities are done Provides objective evidence of compliance to ISMS requirements Work Instructions, Checklists, forms, etc. Records

ISMS Documentation n Level 1 Security Policy Manual n n summary of the management framework including the information security policy and the control objectives and implemented controls given in the statement of applicability. Level 2 Procedures n procedures adopted to implement the controls required. Describe the who, what, when, and where of security processes and inter-department controls

ISMS Documentation n Level 3 n n Explains details of specifis tasks or activities Level 4 n Records objectives evidence of activities carried out in compliance with levels 1, 2 and 3 documentation

Contents of the Desk Top review n Clause 4. 1 General Requirements n Evidence of a documented ISMS. Establish that there is a documented ISMS, that the client has identified all information assets that require protection, has defined an approach to risk management and documented the degree of assurance required.

Contents of the Desk Top review n Clause 4. 2 Requirements n Evidence of the following activities/documentation n n n n Scope of the ISMS Security policy Risk Assessment Risk Management Control Selection Risk Treatment Plan Statement of Applicability Review of the above

Clause 4. 2 Requirements n Scope n n Must be clearly defined, where relevant , scope must not mislead. Security Policy n Published, management approval, communicated to all employees, relevent to the organization, mechanisms in place to review and update.

Clause 4. 2 Requirements n Risk Assessment n Has this been conducted, if so have all assets been included, is there a comprehensive threat and vulnerability analysis, is the process documented and repeatable, is the risk assessment current, is the risk being managed. The selection of the controls must be based on the risk assessment.

Clause 4. 2 Requirements n Risk management n Are selected controls based on risk assessment results, is it clear from the risk assessment which controls are baseline measures, which are mandatory and which may be considered optional?

Clause 4. 2 Requirements n Control Selection n n Understand why controls have been selected, seek objective evidence to support why certain controls have not been selected. Risk Treatment Plan n Has a risk treatment plan that identifies the appropriate management action, responsibilities and priorities for managing information security risks.

Clause 4. 2 Requirements n Statement of Applicability n n has it been prepared, have the reasons for control selection and exclusions been documented? Review of the above n Have reviews been planned of the policy, scope, risk assessment, is there evidence to support such reviews have taken place.

Clause 4. 3 Documentation Requirements n Documentation n objective evidence i. e. electronic or hard copy documentation of all mandatory elements of the ISMS framework, overall security policy, and policies relating to each of the controls where applicable, security procedures, management system procedures, formal document control, records.

Clause 4. 3 Documentation Requirements n Document Control n A formal written procedure/s need to be established to ensure that all documentation is managed in accordance with company policies. The organization must clearly identify who/which function has the responsibility for maintaining and updateing procedures with a mechanism in place to review and ensure the procedures are kept up to date and withdrawn when obsolete. It is a requirement that documentation must be readily available for the staff who wish to it only where appropriate. All documentation must be legible, dated and readily identifiable.

Clause 4. 3 Documentation Requirements n Records n evidence must be available to demonstrate that the ISMS is working. Without any objective evidence of the operation of the ISMS the audit will have to be conducted at the end of State 1.