2005 TRES meeting Computer Science Research on Sensor









- Slides: 27

2005 TRES meeting Computer Science Research on Sensor Network Security Peng Ning Cyber Defense Laboratory Department of Computer Science NC State University 1

Outline • • Background Challenges Our research strategy Investigated problems – Key management – Broadcast authentication – Secure location discovery – Secure clock synchronization • Possible collaboration Computer Science 2

Background on Sensor Networks • A sensor network consists of a large number of sensor nodes – Low cost – Resource constrained – Wireless communication • Sensor networks are ideal candidates for – Critical infrastructure protection – Environment monitoring – Military operations –… Computer Science 3

Challenges in Sensor Network Security • Resource constraints – Limited storage, computation, and communication • Expensive mechanisms such as public key cryptography is not practical – Depletable resources (e. g. battery power) • Resource consumption attacks • Threat of node compromises – Sensor nodes are usually deployed in an unattended fashion – Subject to node captures Computer Science 4

Challenges (Cont’d) • Local computation/communication v. s. global threat – Sensor network applications often depend on local computation and communication due to resource constraints – A determined attacker may • Attack any node in a network, and • Use information gathered from compromised nodes to attack non-compromised ones Computer Science 5

Research Strategy • Cryptographic services – Broadcast authentication – Key management • Security mechanisms for fundamental services – Clock synchronization – Secure location discovery – Secure aggregation and in-network processing – Cluster formation/cluster head election Computer Science 6

Research Strategy (Cont’d) • Securing sensor network applications – Surveillance – Tracking of moving targets –… • Other desirable security services – Example: Intrusion detection • A desirable component • Require different solutions than traditional techniques Computer Science 7

Investigated Research Problems • • Pairwise key establishment Broadcast authentication Secure location discovery Secure clock synchronization Supported by NSF Cyber Trust and CAREER Computer Science 8

Pairwise Key Establishment • Problem: How to establish pairwise keys between nodes that may communicate with each other? – Between arbitrary pairs of nodes – Between neighbor nodes • Challenges – Resource constraints (limited computation, storage, communication capabilities) – Threat of compromised nodes • Our solutions – Polynomial-pool based key pre-distribution (Tiny. Key. Man) – Location-based key pre-distribution – Group-based key pre-distribution Computer Science 9

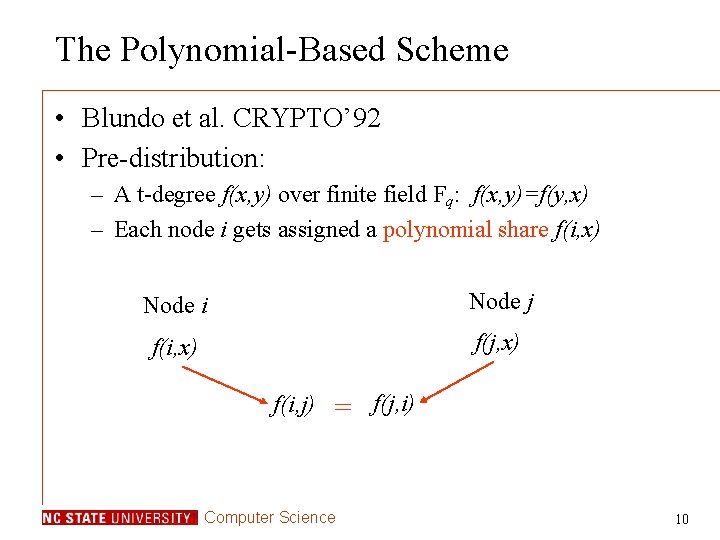
The Polynomial-Based Scheme • Blundo et al. CRYPTO’ 92 • Pre-distribution: – A t-degree f(x, y) over finite field Fq: f(x, y)=f(y, x) – Each node i gets assigned a polynomial share f(i, x) Node i Node j f(i, x) f(j, x) f(i, j) = Computer Science f(j, i) 10

Properties and Limitations • Properties – Threshold property: unconditionally secure for up to t compromised nodes even they collude together – Storage: (t +1)log q bits – Computation: t modular multiplications and t modular additions – No communication overhead • Limitations – Insecure when more than t sensor nodes are compromised – An invitation for node compromise attacks Computer Science 11

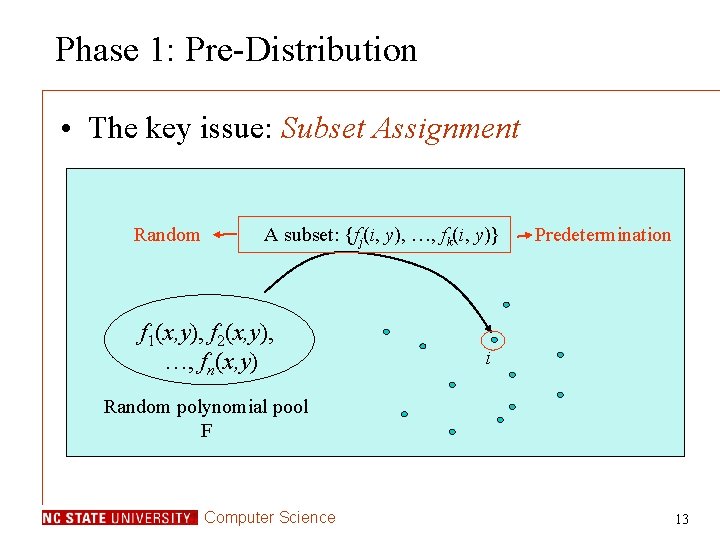
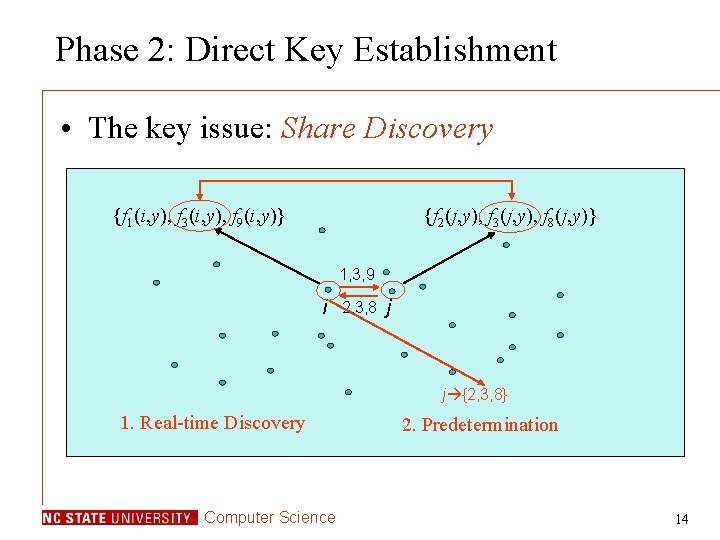
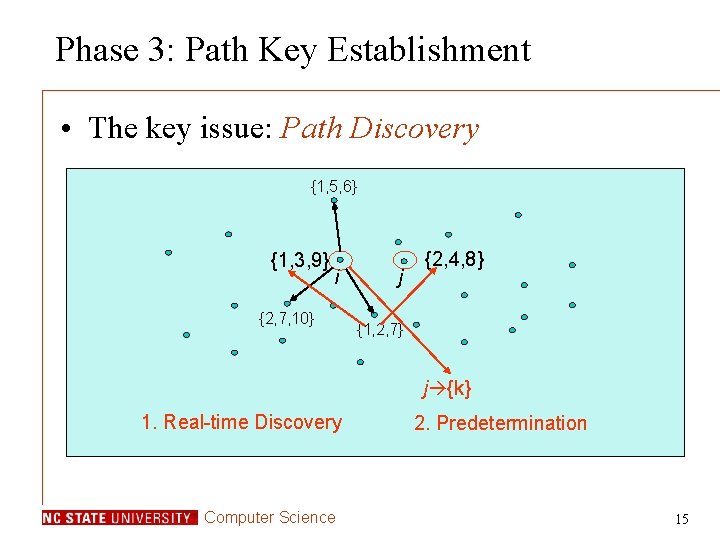
Polynomial Pool Based Key Pre-Distribution • The main idea – Use multiple polynomials (polynomial pool) • Three phases: – Pre-Distribution: pre-distribute secrets – Direct key establishment: setup direct keys – Path key establishment: setup indirect keys Computer Science 12

Phase 1: Pre-Distribution • The key issue: Subset Assignment Random A subset: {fj(i, y), …, fk(i, y)} f 1(x, y), f 2(x, y), …, fn(x, y) Predetermination i Random polynomial pool F Computer Science 13

Phase 2: Direct Key Establishment • The key issue: Share Discovery {f 1(i, y), f 3(i, y), f 9(i, y)} {f 2(j, y), f 3(j, y), f 8(j, y)} 1, 3, 9 i 2, 3, 8 j j {2, 3, 8} 1. Real-time Discovery Computer Science 2. Predetermination 14

Phase 3: Path Key Establishment • The key issue: Path Discovery {1, 5, 6} {1, 3, 9} i {2, 7, 10} j {2, 4, 8} {1, 2, 7} j {k} 1. Real-time Discovery Computer Science 2. Predetermination 15

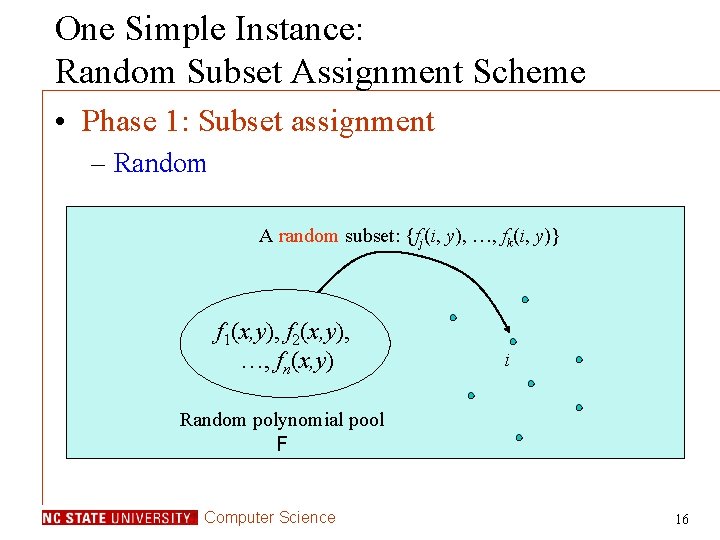
One Simple Instance: Random Subset Assignment Scheme • Phase 1: Subset assignment – Random A random subset: {fj(i, y), …, fk(i, y)} f 1(x, y), f 2(x, y), …, fn(x, y) i Random polynomial pool F Computer Science 16

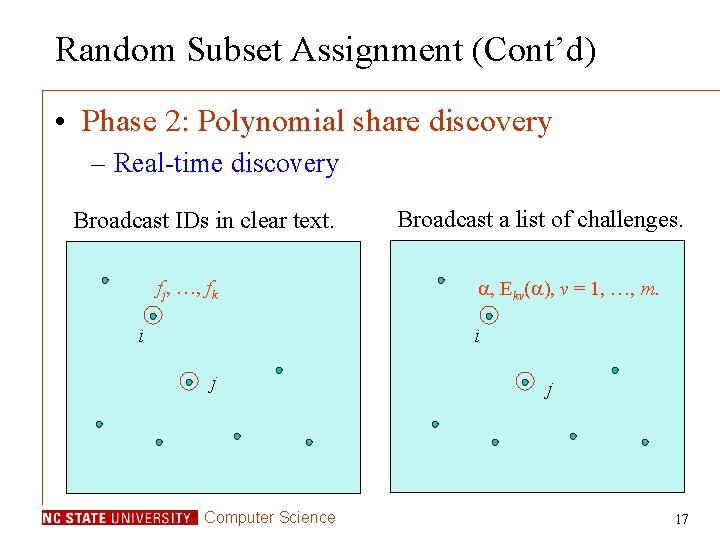
Random Subset Assignment (Cont’d) • Phase 2: Polynomial share discovery – Real-time discovery Broadcast IDs in clear text. fj, …, fk i Broadcast a list of challenges. , Ekv( ), v = 1, …, m. i j Computer Science j 17

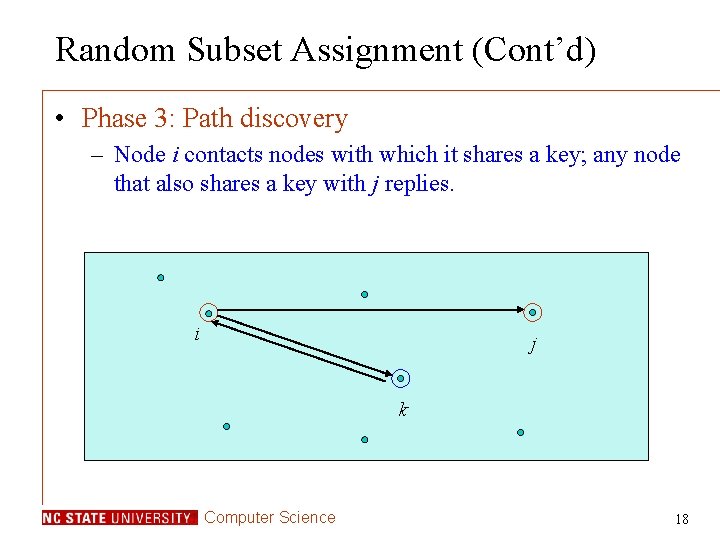
Random Subset Assignment (Cont’d) • Phase 3: Path discovery – Node i contacts nodes with which it shares a key; any node that also shares a key with j replies. i j k Computer Science 18

Resilience against Compromised Sensors • Comparison with basic probability and q-composite schemes – Probability to establish direct keys p = 0. 33 – Each sensor has storage equivalent to 200 keys Computer Science 19

More Schemes • Random key pre-distribution – Grid-based pairwise key pre-distribution – Hybercube-based pairwise key pre-distribution • Location-based key pre-distribution – Pre-deployment knowledge • sensors’ expected locations – Post-deployment knowledge • Group-based key pre-distribution • Related publications – ACM CCS 03, ACM SASN 03, ACM TISSEC 05, ACM TOSN (under revision) Computer Science 20

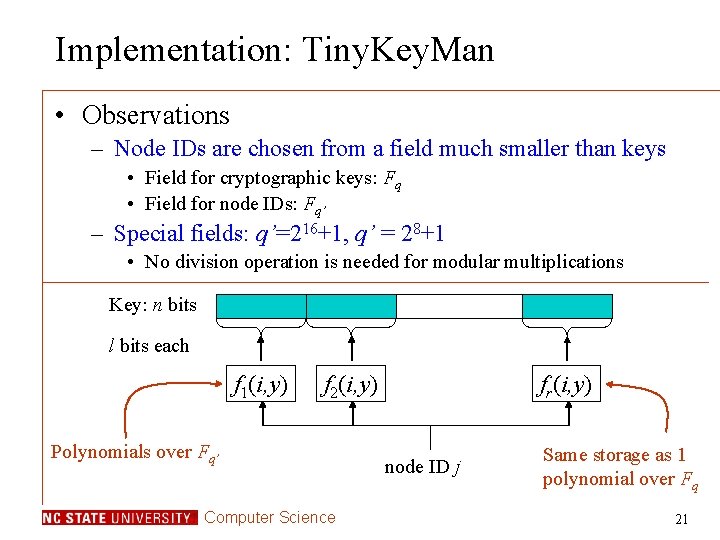
Implementation: Tiny. Key. Man • Observations – Node IDs are chosen from a field much smaller than keys • Field for cryptographic keys: Fq • Field for node IDs: Fq’ – Special fields: q’=216+1, q’ = 28+1 • No division operation is needed for modular multiplications Key: n bits l bits each f 1(i, y) f 2(i, y) Polynomials over Fq’ Computer Science fr(i, y) node ID j Same storage as 1 polynomial over Fq 21

Computational Cost Computer Science 22

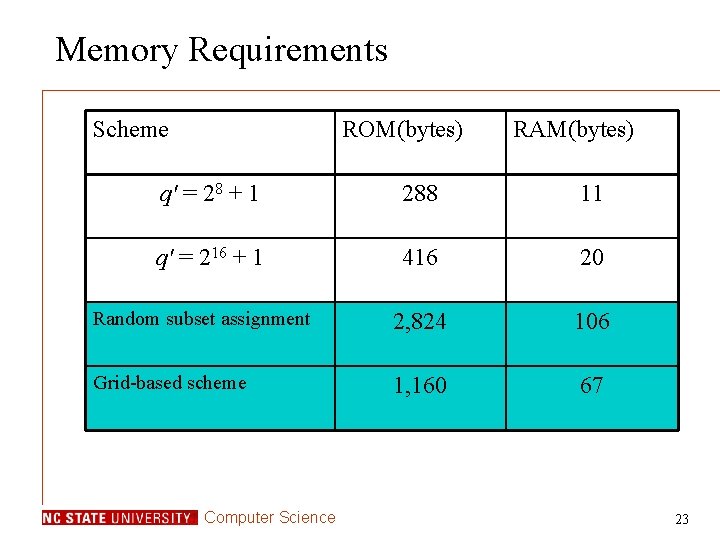
Memory Requirements Scheme ROM(bytes) RAM(bytes) q' = 28 + 1 288 11 q' = 216 + 1 416 20 Random subset assignment 2, 824 106 Grid-based scheme 1, 160 67 Computer Science 23

Broadcast Authentication • Problem: How to broadcast authenticated messages in large sensor networks – Previous solution TESLA isn’t scalable • Our solutions – Multi-level TESLA (NDSS 03, ACM TECS 04) – Merkle tree based TESLA (under review) • Also address revocation of broadcasting nodes Computer Science 24

Secure Location Discovery • Problem: How can sensors securely determine their locations even if there are malicious external or insider attacks • Our solutions – Detect localization anomalies using deployment knowledge (IPDPS 05) – Beaconless location discovery (Infocom 05) – Tolerate malicious location references (under review) – Detect malicious beacon nodes (under review) Computer Science 25

Secure Clock Synchronization • Problem: How to distribute a common clock throughout sensor networks • Our solutions – Resilient clock distribution (under review) – Multi-path-based resilient clock distribution (under review) – Cluster-wise fault tolerant clock synchronization (under revision) Computer Science 26

Possible Collaboration • My interests – Long-term • Anything about information security – Short-term • Sensor and ad-hoc network security • Intrusion detection • Software security Computer Science 27