100 Security The only system which is truly






- Slides: 23

100% Security “ The only system which is truly secure is one which is switched off and unplugged, locked in a titanium lined safe, buried in a concrete bunker, and is surrounded by nerve gas and very highly paid armed guards. Even then, I wouldn’t stake my life on it …. Gene Spafford—Director, Computer Operations, Audit, and Security Technology (COAST), Purdue University ” 1

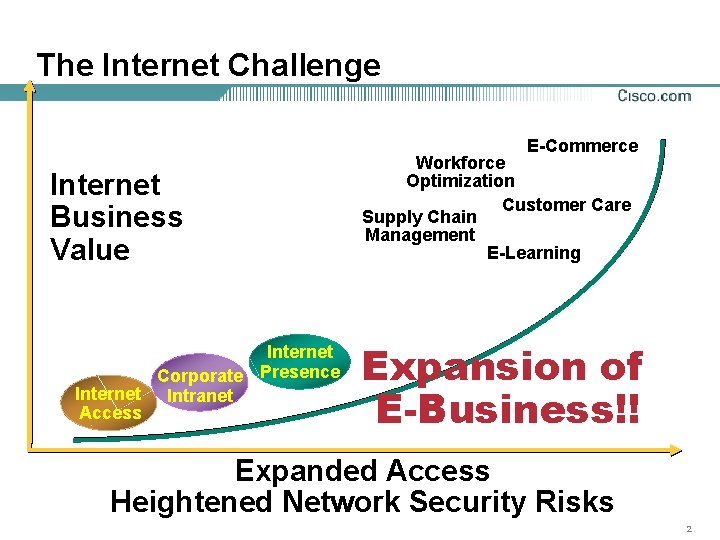
The Internet Challenge E-Commerce Internet Business Value Internet Corporate Presence Internet Intranet Access Workforce Optimization Customer Care Supply Chain Management E-Learning Expansion of E-Business!! Expanded Access Heightened Network Security Risks 2

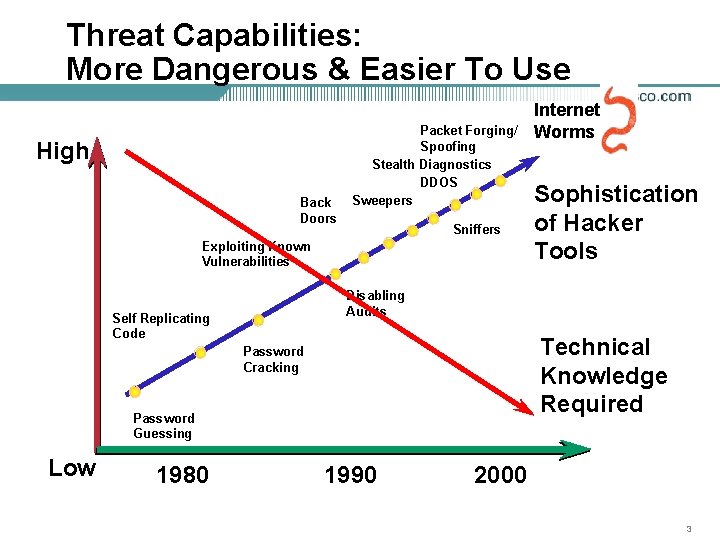
Threat Capabilities: More Dangerous & Easier To Use High Back Doors Packet Forging/ Spoofing Stealth Diagnostics DDOS Sweepers Sniffers Exploiting Known Vulnerabilities Technical Knowledge Required Password Cracking Password Guessing 1980 Sophistication of Hacker Tools Disabling Audits Self Replicating Code Low Internet Worms 1990 2000 3

Examples 4

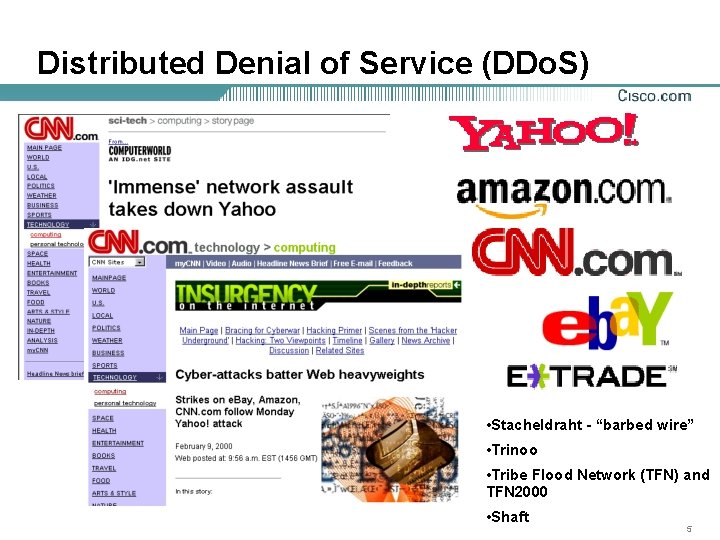
Distributed Denial of Service (DDo. S) • Stacheldraht - “barbed wire” • Trinoo • Tribe Flood Network (TFN) and TFN 2000 • Shaft 5

Attacks Keep Getting Easier www. test. com Connected to www. test. com 6

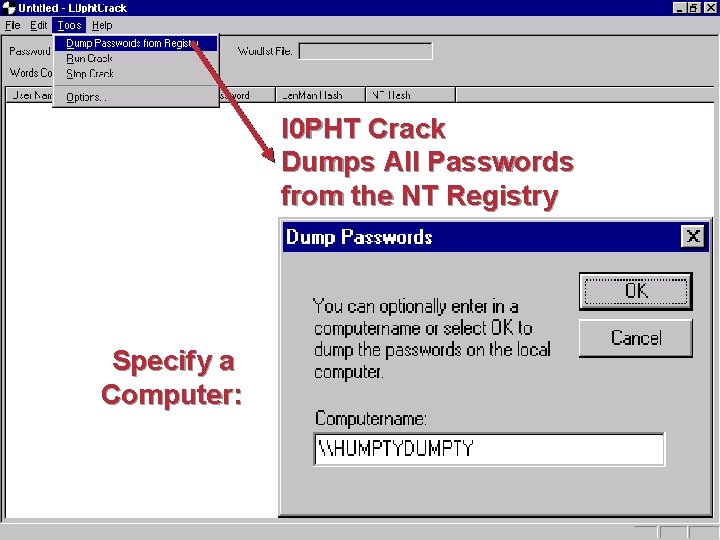
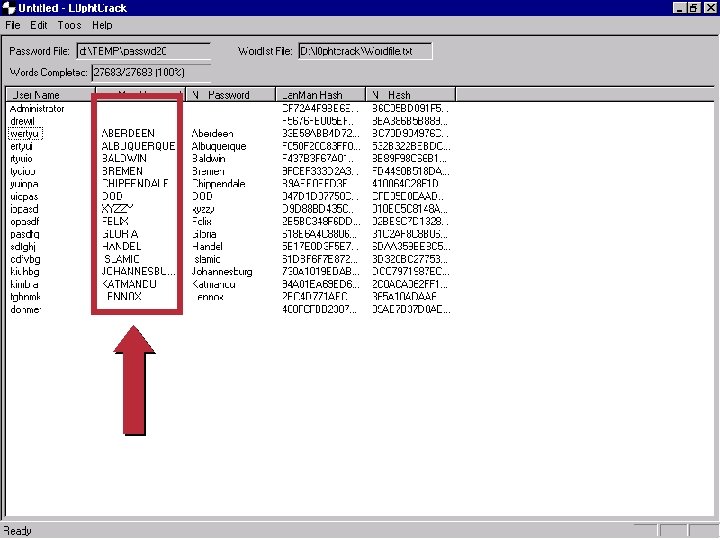
l 0 PHT Crack Dumps All Passwords from the NT Registry Specify a Computer: 7

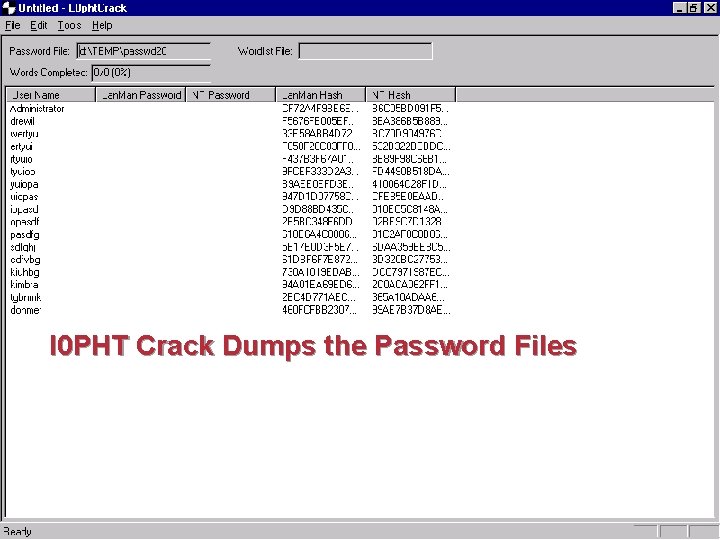
l 0 PHT Crack Dumps the Password Files 8

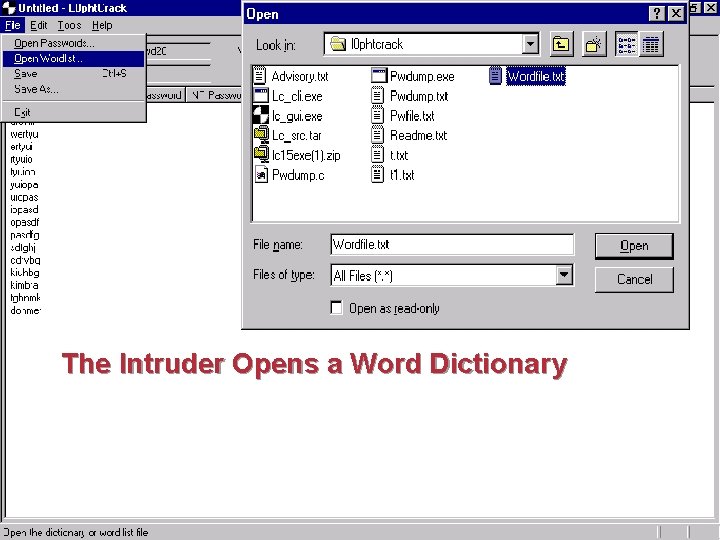
The Intruder Opens a Word Dictionary 9

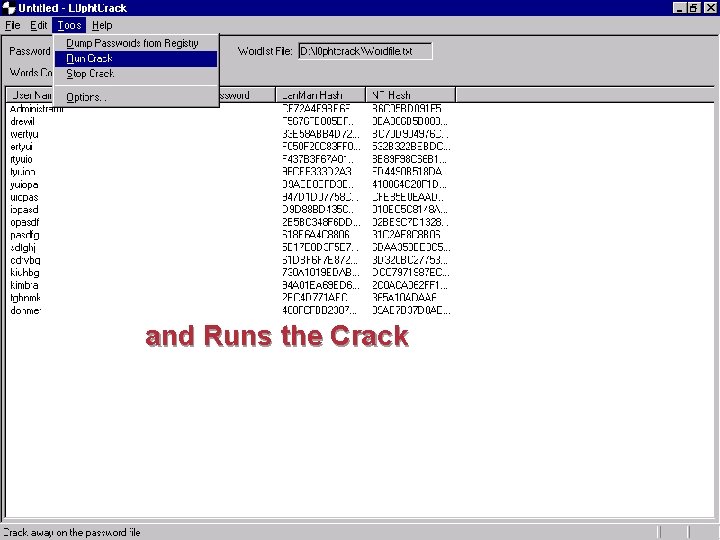
and Runs the Crack 10

11

A new generation of attacks: The Internet Worms © 2001, Cisco Systems, Inc. All rights reserved. 12

The Code Red & NIMDA Worms What Happened? ? - - Code Red July 19 -20/2001 359, 104 Hosts in 13 hours $2. 6 Billion in Damages! Estimates from Computer Economics (Carlsbad, CA) - NIMDA September 18, 2001 Fastest spreading virus 300 K+ Hosts, 2. 2 M devices Damage still being assessed 13

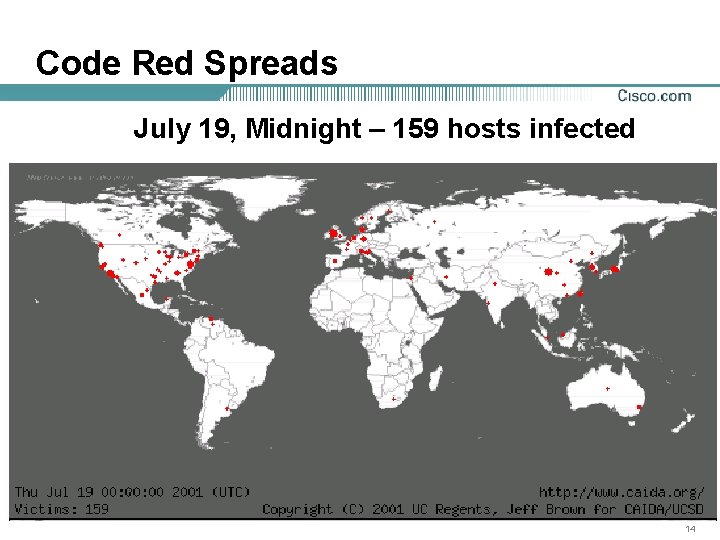
Code Red Spreads July 19, Midnight – 159 hosts infected 14

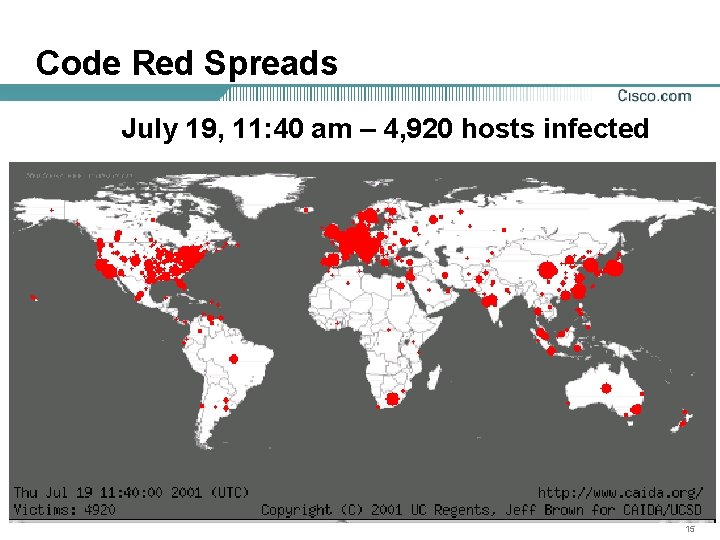
Code Red Spreads July 19, 11: 40 am – 4, 920 hosts infected 15

Code Red Spreads July 20, Midnight – 341, 015 hosts infected 16

The Code Red Worm How It Works • Conceals itself in HTTP Packets. Firewalls alone cannot safeguard against the virus • The worm exploits vulnerabilities found in Microsoft’s Internet Information Server (IIS) v 4&5 via a buffer overflow attack • It then exploits arbitrary code and installs a copy of itself into the infected computer’s memory – which infects other hosts. 17

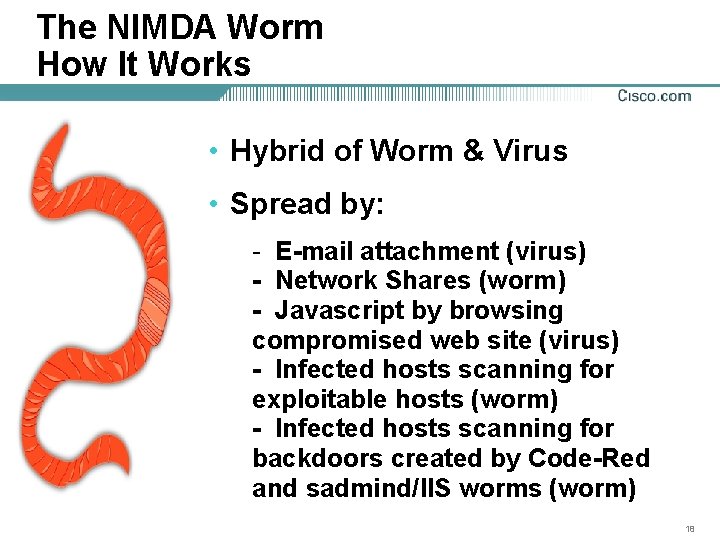
The NIMDA Worm How It Works • Hybrid of Worm & Virus • Spread by: - E-mail attachment (virus) - Network Shares (worm) - Javascript by browsing compromised web site (virus) - Infected hosts scanning for exploitable hosts (worm) - Infected hosts scanning for backdoors created by Code-Red and sadmind/IIS worms (worm) 18

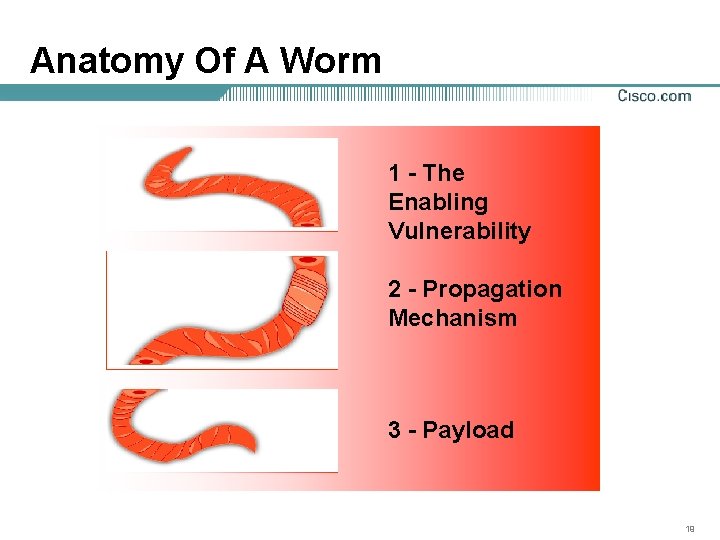
Anatomy Of A Worm 1 - The Enabling Vulnerability 2 - Propagation Mechanism 3 - Payload 19

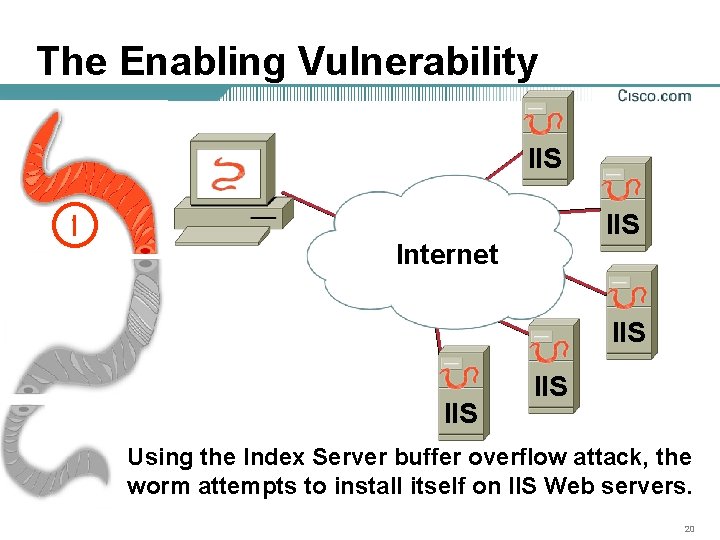
The Enabling Vulnerability IIS 1 IIS Internet IIS IIS Using the Index Server buffer overflow attack, the worm attempts to install itself on IIS Web servers. 20

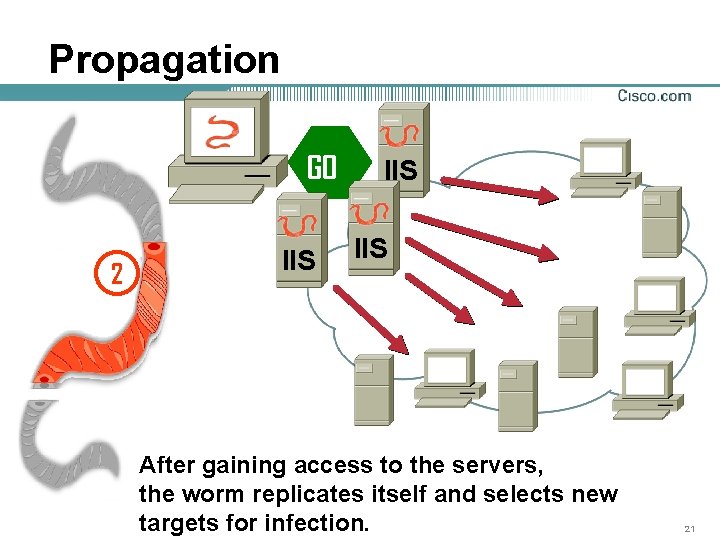
Propagation GO 2 IIS IIS After gaining access to the servers, the worm replicates itself and selects new targets for infection. 21

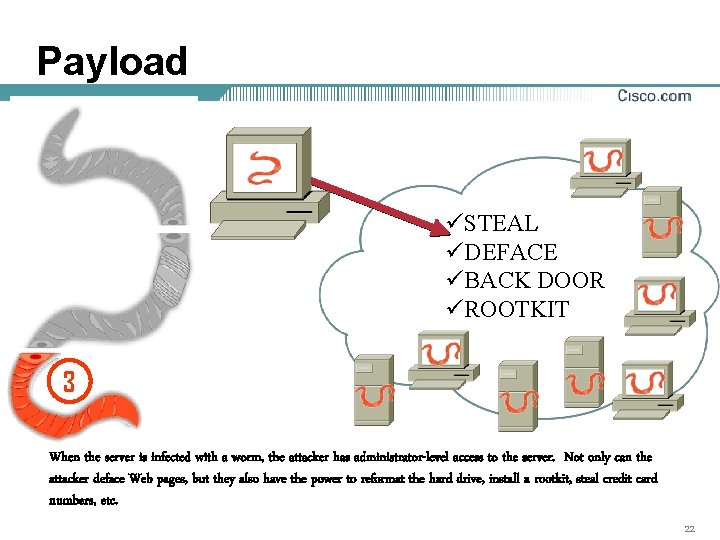
Payload üSTEAL üDEFACE üBACK DOOR üROOTKIT 3 When the server is infected with a worm, the attacker has administrator-level access to the server. Not only can the attacker deface Web pages, but they also have the power to reformat the hard drive, install a rootkit, steal credit card numbers, etc. 22

Additional Information • Compulsory Reading "Hacking Exposed". • Security Links (vulnerabilities, tips, exploits, tools) http: //www. securityfocus. com http: //packetstorm. securify. org http: //www. insecure. org 23