University of Parma Department of Information Engineering Parma




- Slides: 15

University of Parma Department of Information Engineering Parma, Italy Byzantine Generals Problem in the Light of P 2 P Computing Natalya Fedotova Luca Veltri International Workshop on Ubiquitous Access Control Julygenerals 17, 2006 – in. San Jose, California, USA Byzantine problem the light IWUAC - July 17, 2006 of P 2 P computing

DHT based P 2 P networks n Efficient routing performance n High scalability n High exact-match accuracy of search n Simple API IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 2

DHT based P 2 P networks Main types of attacks: n n n Incorrect lookup routing Incorrect routing updates Partition Rapid joins and leaves Inconsistent behavior Storage and retrieval attack IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 3

Byzantine Generals Problem n n Takes place in distributed computer systems in the presence of malfunctioning components that give conflicting information to other parts of the system Causes a Byzantine failure, an arbitrary fault that occurs during the execution of some algorithm by a distributed computer system, and as a result: a failure to pass to the next step in the algorithm ¨ system’s inability to correctly implement the actual algorithm ¨ arbitrary execution of a step different from one predicated by the algorithm (incorrect hops) ¨ n Originally described by L. Lamport, R. Shostak and M. Pease in 1982, who were the first to apply the concept of BGP to distributed computer systems IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 4

Byzantine Generals Problem: the original concept n n There are n generals of Byzantine army with their divisions They have to reach an agreement on a common plan of action These generals are geographically separated and they have to communicate with each other through messengers Some of them are traitors IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 5

Byzantine Generals Problem: the original concept To cope with t traitors there must be at least 3 t +1 generals and, given the possibility for all generals to exchange the messages with each other, must exist some recursive algorithm of information exchange, equal for all generals, so, that: ¨ all generals make the final decisions ¨ all loyal generals decide upon the same plan of action ¨ this final plan of loyal generals must coincide with final decision of one loyal general at least IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 6

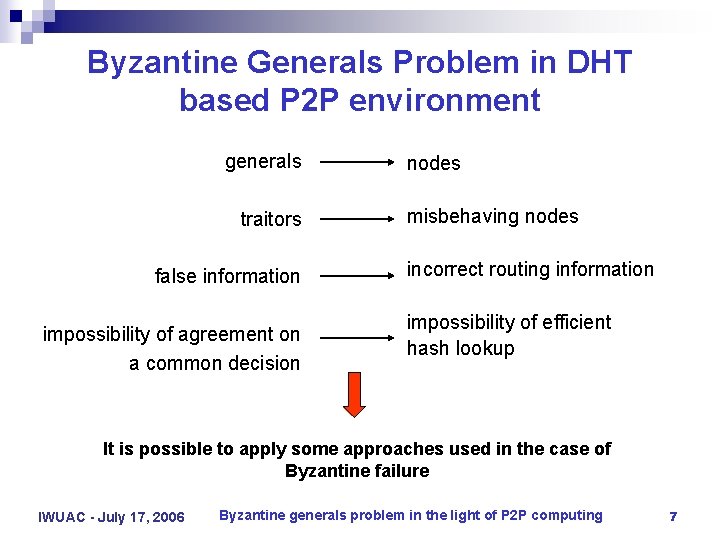
Byzantine Generals Problem in DHT based P 2 P environment generals traitors false information impossibility of agreement on a common decision nodes misbehaving nodes incorrect routing information impossibility of efficient hash lookup It is possible to apply some approaches used in the case of Byzantine failure IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 7

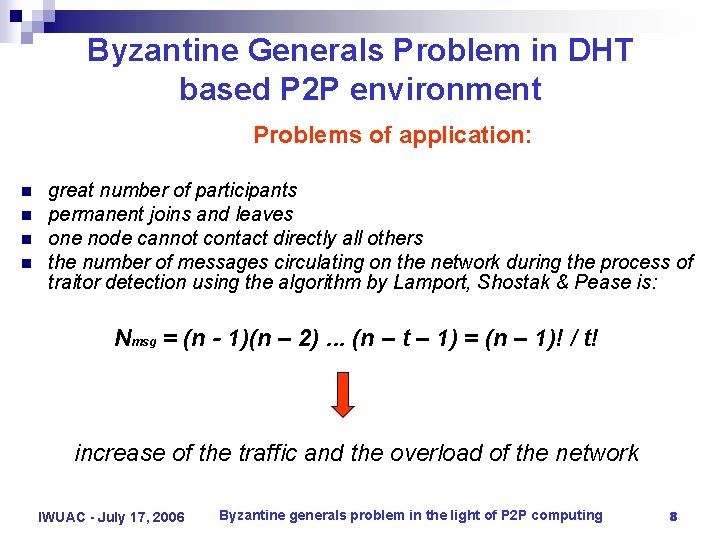
Byzantine Generals Problem in DHT based P 2 P environment Problems of application: n n great number of participants permanent joins and leaves one node cannot contact directly all others the number of messages circulating on the network during the process of traitor detection using the algorithm by Lamport, Shostak & Pease is: Nmsg = (n - 1)(n – 2). . . (n – t – 1) = (n – 1)! / t! increase of the traffic and the overload of the network IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 8

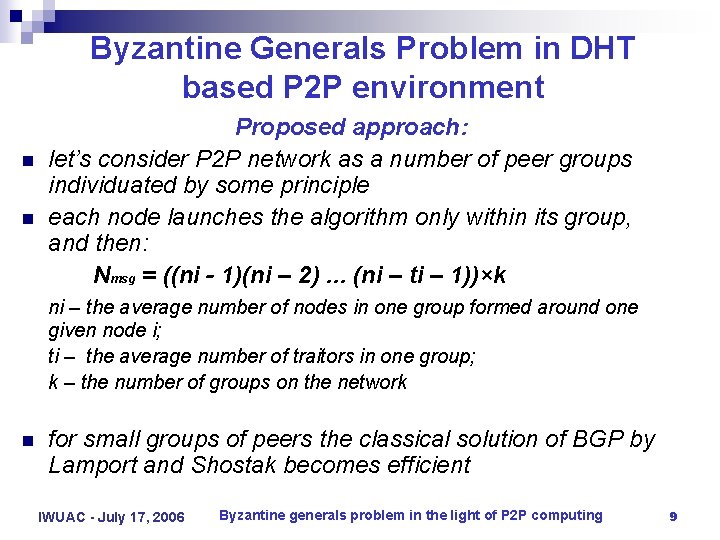
Byzantine Generals Problem in DHT based P 2 P environment n n Proposed approach: let’s consider P 2 P network as a number of peer groups individuated by some principle each node launches the algorithm only within its group, and then: Nmsg = ((ni - 1)(ni – 2). . . (ni – ti – 1))×k ni – the average number of nodes in one group formed around one given node i; ti – the average number of traitors in one group; k – the number of groups on the network n for small groups of peers the classical solution of BGP by Lamport and Shostak becomes efficient IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 9

Possible criteria to individuate the groups n the most frequent contacts among the nodes n common interests n “closeness” of identifiers according to XOR-metric IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 10

“Codat” concept as one of possible mechanisms to individuate the groups Codat = Code + Data n n n originally described by JXTA platform developers is a unit of information shared and exchanged within a peer group means a content that could be either code or data and is used as a placeholder for any types of data is uniquely identified via a unique Codat. ID and can belong to only one peer group contains a document (a content advertisement) that represents the data it holds IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 11

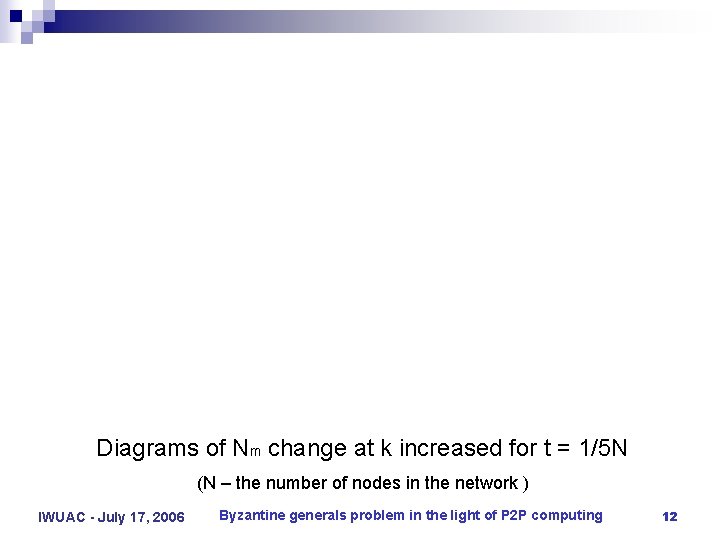
Diagrams of Nm change at k increased for t = 1/5 N (N – the number of nodes in the network ) IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 12

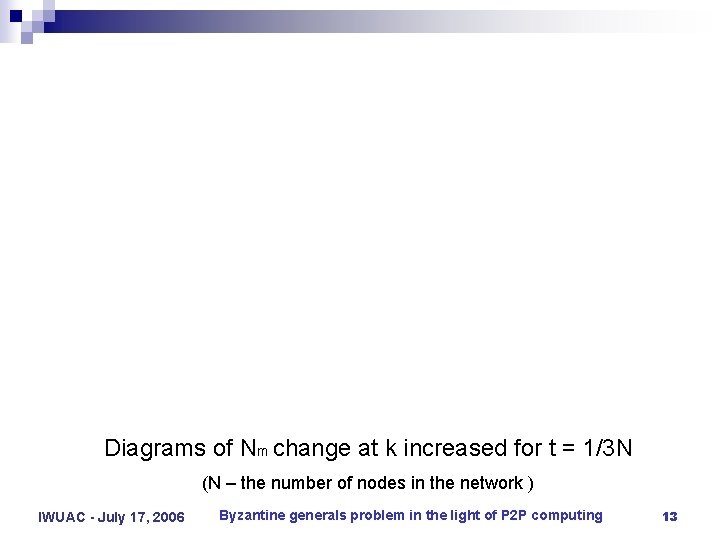
Diagrams of Nm change at k increased for t = 1/3 N (N – the number of nodes in the network ) IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 13

Conclusions n n it is possible to apply successfully the classical solutions for BGP by Lamport and Shostak in P 2 P environment application of these solutions helps to reduce the number of messages circulating on the network BUT: here only completely separated groups are considered in this case we deal with the malicious node who demonstrates poor behavior regarding all the nodes IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 14

Future work n n n What other mechanisms can we use to individuate a group? How can we optimize the algorithm of the traitor detection process in the case of partially coinciding groups? How can we integrate the solutions we have just presented with some mechanisms of reputation evaluation? IWUAC - July 17, 2006 Byzantine generals problem in the light of P 2 P computing 15
 Department of information engineering university of padova
Department of information engineering university of padova Information engineering padova
Information engineering padova University of sargodha engineering department
University of sargodha engineering department Itc bodoni parma
Itc bodoni parma Parma food kiosk
Parma food kiosk Istituto bodoni parma
Istituto bodoni parma Hotel mercure parma
Hotel mercure parma Antonio restori
Antonio restori Paolo bertozzi parma
Paolo bertozzi parma Biblioteche unipr
Biblioteche unipr Parma
Parma Glaxo parma
Glaxo parma Parma city schools bell schedule
Parma city schools bell schedule Ic bocchi
Ic bocchi Itc bodoni parma
Itc bodoni parma Veslonos
Veslonos