TRIPWIRE Karthik Mohanasundaram Wright State University Topics of


![Classification of IDS n n n Network Intrusion Detection System [NIDS] Example: Nessus, Fire. Classification of IDS n n n Network Intrusion Detection System [NIDS] Example: Nessus, Fire.](https://slidetodoc.com/presentation_image/21bd5f6834a2ac1b568270ad4bf5127b/image-3.jpg)



![Bibliography n n Official Red Hat Linux Reference Guide [www. redhat. com] The Design Bibliography n n Official Red Hat Linux Reference Guide [www. redhat. com] The Design](https://slidetodoc.com/presentation_image/21bd5f6834a2ac1b568270ad4bf5127b/image-11.jpg)
- Slides: 11

TRIPWIRE Karthik Mohanasundaram Wright State University

Topics of Interest ü ü Introduction to Intrusion Detection Systems Functionalities of Tripwire
![Classification of IDS n n n Network Intrusion Detection System NIDS Example Nessus Fire Classification of IDS n n n Network Intrusion Detection System [NIDS] Example: Nessus, Fire.](https://slidetodoc.com/presentation_image/21bd5f6834a2ac1b568270ad4bf5127b/image-3.jpg)
Classification of IDS n n n Network Intrusion Detection System [NIDS] Example: Nessus, Fire. Storm Network Node Intrusion Detection System [NNIDS] Example: Real Secure Host Intrusion Detection System [HIDS] Example: Trip. Wire, Intruder Alert

Advantages of HIDS n n A HIDS resides on the system being monitored and tracks changes made to important files and directories A HIDS does not look for patterns and monitors changes within a specified set of rules

Introduction n n Tripwire is a Host Based Intrusion detection System which can be used to ensure the integrity of critical system files and directories by identifying all changes made to them specified in its configuration file Tripwire compares the files and directories with a baseline database that was generated initially

Password phrases n Tripwire uses two password phrases to sign or encrypt the important key files so that they are not altered by normal users. Two password phrases are employed for these purposes n n Site-Key passphrase Local-Key passphrase

continued. . n n The Site-Key password phrase protects the site key which signs Tripwire Configuration File and Policy File The Local-Key password phrase protects the local key which signs the Tripwire database and Tripwire Report

Post-Installation Procedures n Run the Configuration script to sign the important files n Initialize the tripwire database n Run the First Integrity Check n Modify the Configuration and Policy files if necessary

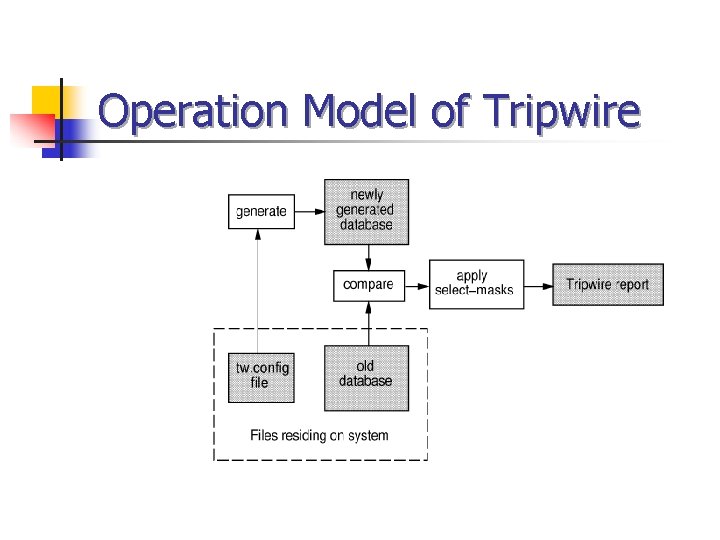
Operation Model of Tripwire

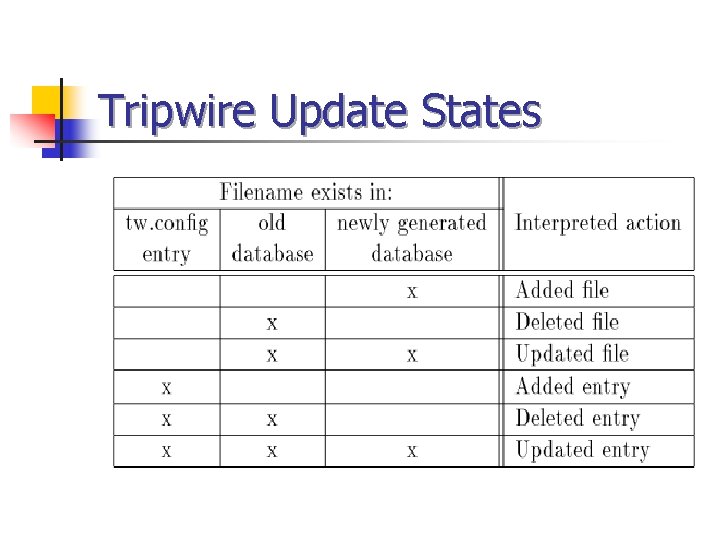
Tripwire Update States
![Bibliography n n Official Red Hat Linux Reference Guide www redhat com The Design Bibliography n n Official Red Hat Linux Reference Guide [www. redhat. com] The Design](https://slidetodoc.com/presentation_image/21bd5f6834a2ac1b568270ad4bf5127b/image-11.jpg)
Bibliography n n Official Red Hat Linux Reference Guide [www. redhat. com] The Design and Implementation of Tripwire: A File System Integrity Checker by Gene H. Kim & Eugene H. Spafford