Trespass to Chattels Spam Richard Warner Compu Serve
















- Slides: 17

Trespass to Chattels: Spam Richard Warner

Compu. Serve v. Cyber Promotion o o : “Compu. Serve has received many complaints from subscribers threatening to discontinue their subscription unless Compu. Serve prohibits electronic mass mailers from using its equipment to send unsolicited advertisements. ” “Compu. Serve asserts that the volume of messages generated by such mass mailings places a significant burden on its equipment which has finite processing and storage capacity. ”

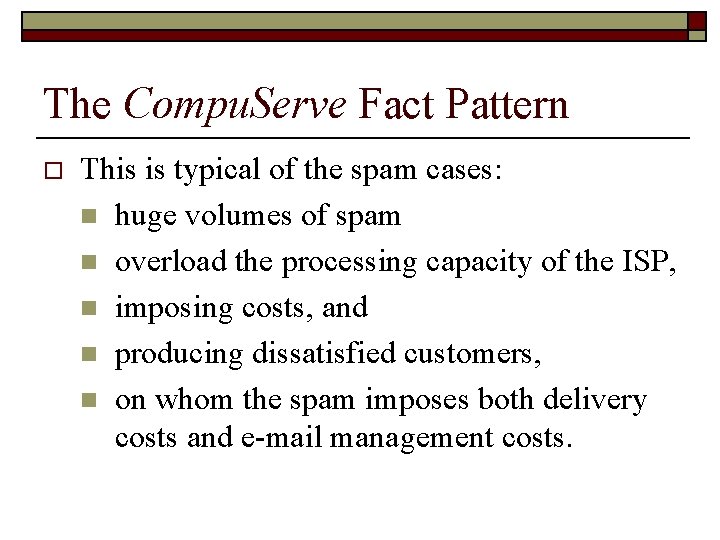
The Compu. Serve Fact Pattern o This is typical of the spam cases: n huge volumes of spam n overload the processing capacity of the ISP, n imposing costs, and n producing dissatisfied customers, n on whom the spam imposes both delivery costs and e-mail management costs.

Did Compu. Serve Consent? o o When you connect a publicly accessible system to the Internet, you impliedly consent to access by the general public to that system. Did Compu. Serve consent in this way to receiving e-mails from Cyber Promotions?

Limited Scope and Revocability o o o Connecting to the Internet does not constitute an invitation to commit hack into the system and delete data, for example. Moreover: even if Compu. Serve did consent, can’t it revoke that consent? It certainly tried to do so.

The Compu. Serve Fact Pattern o o “Compu. Serve has notified defendants that they are prohibited from using its proprietary computer equipment to process and store unsolicited e-mail and has requested them to cease and desist from sending unsolicited email to its subscribers. ” Is this revocation effective?

Revocability o o Courts have held that ISPs can effectively revoke whatever consent they might have initially given to access by a spammer. Cyber Promotions continued to send e-mails after consent was revoked.

Summary o o o Cyber Promotions intentionally accessed Compu. Serve’s system, without authorization, and caused significant harm in form of n n slow downs, delays, personnel costs; and dissatisfied customers, some of whom terminate their accounts because of the delivery and e-mail management costs they bear.

Two Questions o o o What liability, if any, does Cyber Promotions have for these harms? The common law doctrine of trespass to chattels provides an answer. A chattel is personal property. What is the personal property involved here?

What Is the Chattel? o o o Compu. Serve’s computers. Cyber Promotions must send the necessary message data and computer code into Compu. Serve’s computers. Those computers follow the instructions in the code to deliver the message to the subscriber’s inbox.

Trespass o “Trespass to a chattel is committed by intentionally dispossessing another of the chattel or using or intermeddling with it. ” o o o Restatement (Second) of Torts, Section 217. Cyber Promotions does not dispossess Compu. Serve of its computers. They stay in Compu. Serve’s possession.

“Using or Intermeddling” o o o Cyber Promotions merely uses some of the computer’s processing capacity. This is “using or intermeddling” with a chattel. To be a trespass, the use must invade the possessory rights of the owner.

Liability o An unauthorized use does so. n o Compu. Serve, at 1024 (citing Restatement (Second) of Torts, Sections 252 and 892(5), 217, Comment f and Comment g). In such a case, the user is liable if n the use impairs the value of the chattel, or n the use harms a legally protected interest.

Value and Harm in Compu. Serve o o o Does sending vast amounts of spam through the Compu. Serve computers impair their value or harm a relevant interest? It impairs value by slowing down or shutting down the computers. It harms a relevant interest by producing dissatisfied customers, some of whom terminate their accounts.

Remedies o o Monetary compensation for the harm done. An injunction against future access.

Effective? o Trespass to chattels is not a particular effective tool against spammers. n n The enormous number of spammers makes it difficult for Internet service providers to track down the source of the spam. It can be difficult to prove damages as the number of different spammers bombarding an ISP can make it difficult to determine which spammer caused what damage.

Beyond the Spam Cases o o o First: to what extent does one impliedly consent to access by the general public when one connects a publicly accessible system to the Internet? Second: can one always revoke such implied consent by explicitly notifying third parties seeking access that their access is unauthorized? Third: when does access by a third party to a publicly accessible system impair the value of that system or harm a relevant interest?
 Apothecary definition to kill a mockingbird
Apothecary definition to kill a mockingbird Compu cell
Compu cell Compu groupe medical
Compu groupe medical Richard iii pursuit of power
Richard iii pursuit of power Warner subotica
Warner subotica Warner hospital and health services
Warner hospital and health services Dr chris warner
Dr chris warner Azure networking deep dive
Azure networking deep dive Warner blatzer
Warner blatzer Xerxes mazda british library
Xerxes mazda british library Warner bros animation movies
Warner bros animation movies Carl warner
Carl warner Nikita warner
Nikita warner Learning foundation and performing arts
Learning foundation and performing arts Reuben warner associates
Reuben warner associates Ilene warner
Ilene warner The vine boutique warner robins ga
The vine boutique warner robins ga Hoot carl hiaasen characters
Hoot carl hiaasen characters