Swords Dragons and Spells Vendor study on Security









- Slides: 12

Swords, Dragons, and Spells: Vendor study on Security and Privacy controls Marshall Breeding Independent Consultant, Author, Founder and Publisher, Library Technology Guides http: //www. librarytechnology. org/ http: //twitter. com/mbreeding 07 December 2014 CNI Breakout Session

Abstract This presentation describes an introductory study performed to benchmark the current levels of privacy and security controls offered in some of the major library automation and discovery products. The study examines the levels of security and privacy enabled by the selected products related to the interactions with library patrons, for tasks conducted by library personnel, and in the internal storage of sensitive categories of data. Vendors were also polled on how their APIs might expose sensitive data and for any potential vulnerabilities introduced through interactions with third party products. The presentation concludes with some actions that librarians might take to strengthen the security of their systems and reduce the exposure of data related to patron interactions on the platforms they provide.

Vendors Invited Proprietary Traditional ILS Library Services Platforms Discovery Open Source

Introductory Study Not a comprehensive list of products or providers Topics limited to basic privacy and security Network transmission Data storage More detailed investigation needed Include all ILS vendors and discovery services Related providers: e-book lending platforms, content delivery products, etc. Many privacy and security issues related to the library’s Web site or top-level portal

Categories of Questions Patron-facing interactions Staff operations Storage of sensitive data Other security measures Vulnerability through APIs and third party integration Security compliance framework

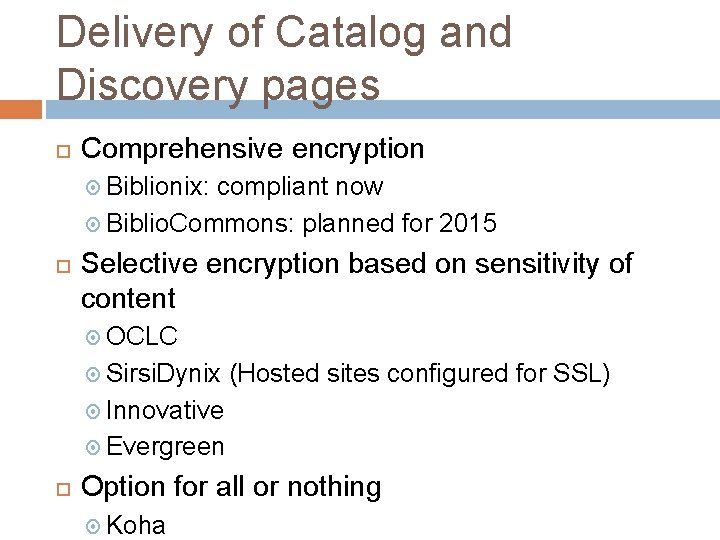
Delivery of Catalog and Discovery pages Comprehensive encryption Biblionix: compliant now Biblio. Commons: planned for 2015 Selective encryption based on sensitivity of content OCLC Sirsi. Dynix (Hosted sites configured for SSL) Innovative Evergreen Option for all or nothing Koha

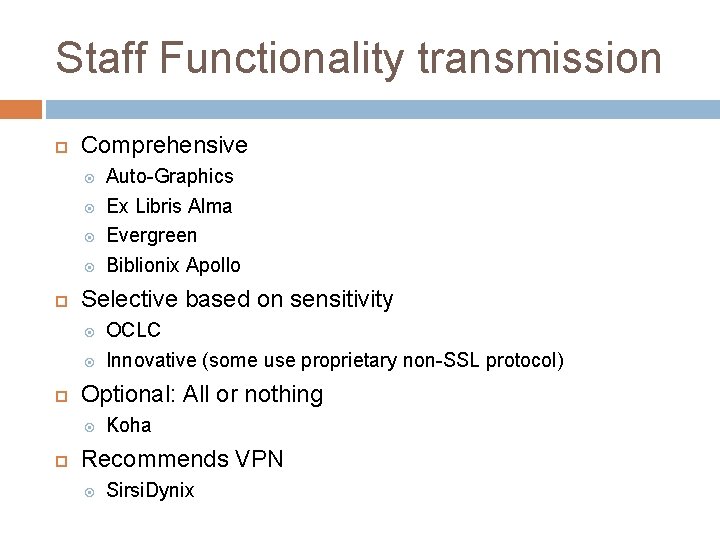
Staff Functionality transmission Comprehensive Selective based on sensitivity OCLC Innovative (some use proprietary non-SSL protocol) Optional: All or nothing Auto-Graphics Ex Libris Alma Evergreen Biblionix Apollo Koha Recommends VPN Sirsi. Dynix

Internal storage of sensitive data All store authentication credentials security None use encryption for all potentially sensitive data patron-related data is encrypted on disk storage: Auto-Graphics , Biblio. Commons , Sirsi. Dynix , OCLC, Ex Libris Alma Patron data stored unencrypted Biblionix, Koha, Evergreen Patron activity logs usually anonymized but not encrypted

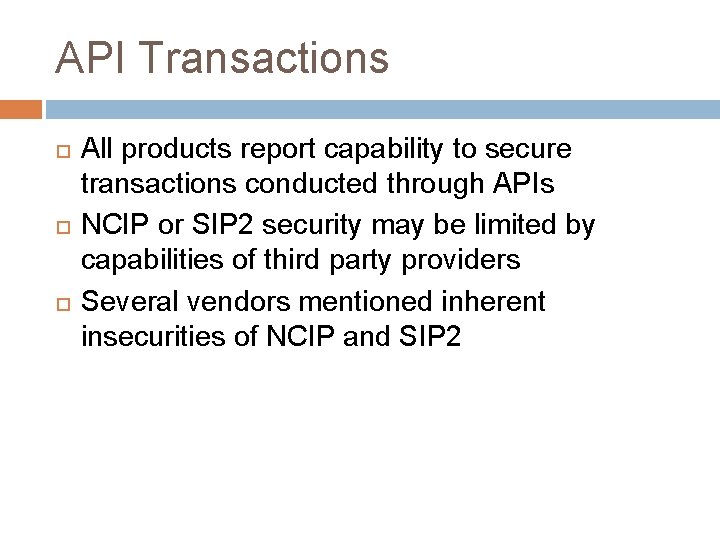
API Transactions All products report capability to secure transactions conducted through APIs NCIP or SIP 2 security may be limited by capabilities of third party providers Several vendors mentioned inherent insecurities of NCIP and SIP 2

Framework for Privacy and security compliance Modelled after PCI for e-commerce Educate libraries regarding available options Set higher standards Define a comprehensive audit methodology for assessing the privacy and security of a library’s technical infrastructure

Complete findings Will appear in the January 2015 issue of Smart Libraries Newsletter published by ALA Tech. Source Available for CNI attendees by request

From Awareness to Action Only a few systems currently offer comprehensive SSL delivery Libraries should exercise options to enable maximal security and privacy Libraries and vendors collaborate to shift all systems to comprehensive secure page delivery Campaign to effect change in less than a year Further awareness of privacy exposure beyond network and file storage level Advise comprehensive self-audit of all services