Stream Control Transmission Protocol SCTP Acknowledgements Prof Paul









- Slides: 34

Stream Control Transmission Protocol (SCTP) Acknowledgements Prof. Paul Amer Randall Stewart ~ Philip Conrad ~ Janardhan Iyengar CISC 856: TCP/IP and Upper Layer Protocols Presented By : Nikhil Shirude November 15, 2007

Overview • • • Motivation for SCTP PDU and Chunk Format SCTP 4 -Way Association SCTP Association Shutdown SCTP Multi-Homing Summary 2

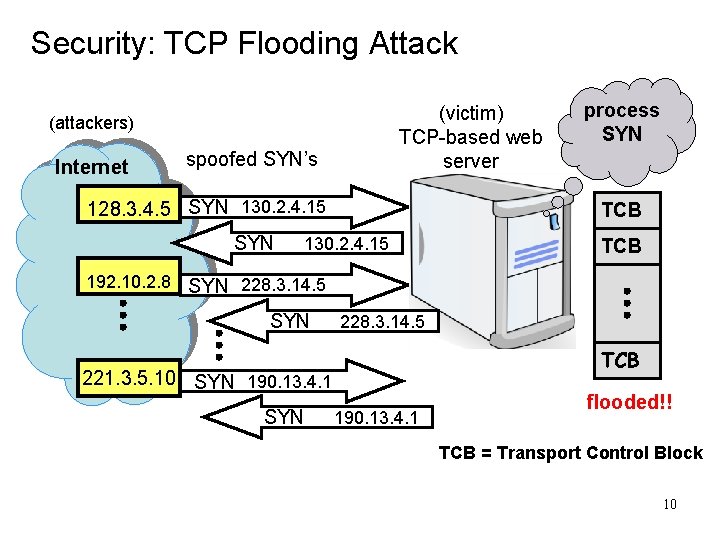
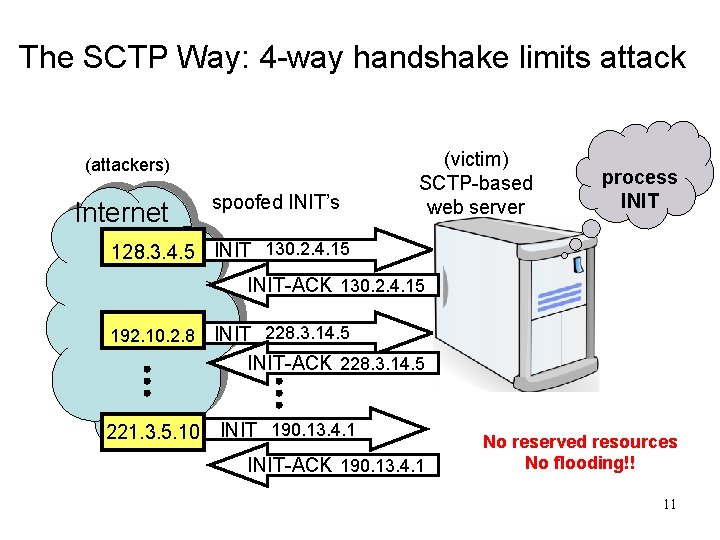
SCTP Motivation • Primary Motivation – Transportation of telephony signaling messages over IP networks • Telephony Signaling – rigid timing & reliability requirements • TCP Limitations Ø head-of-line blocking Ø does not preserve A-PDU boundaries Ø no support for multi-homing Ø vulnerable to SYN Flooding attacks • SCTP Features Ø 4 way handshake Ø multihoming Ø multistreaming Ø framing

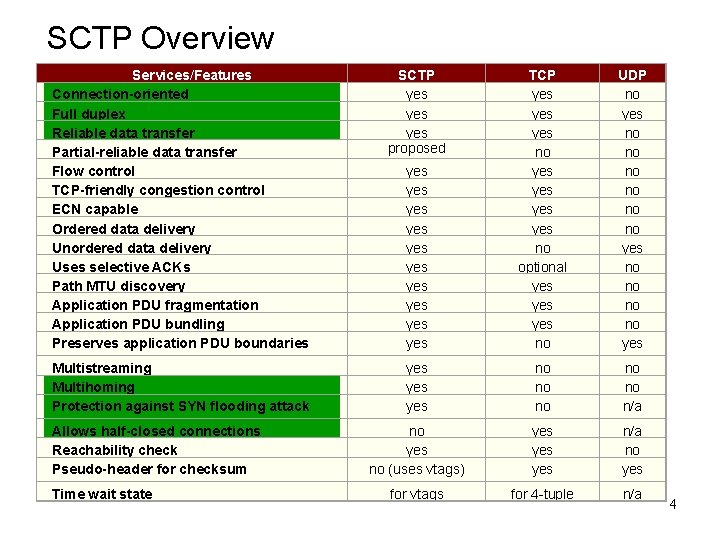
SCTP Overview Services/Features Connection-oriented Full duplex Reliable data transfer Partial-reliable data transfer Flow control TCP-friendly congestion control ECN capable Ordered data delivery Unordered data delivery Uses selective ACKs Path MTU discovery Application PDU fragmentation Application PDU bundling Preserves application PDU boundaries SCTP yes yes proposed Multistreaming Multihoming Protection against SYN flooding attack Allows half-closed connections Reachability check Pseudo-header for checksum Time wait state yes yes yes TCP yes yes no optional yes yes no UDP no yes no no yes yes no no no n/a no yes no (uses vtags) yes yes n/a no yes for vtags for 4 -tuple n/a 4

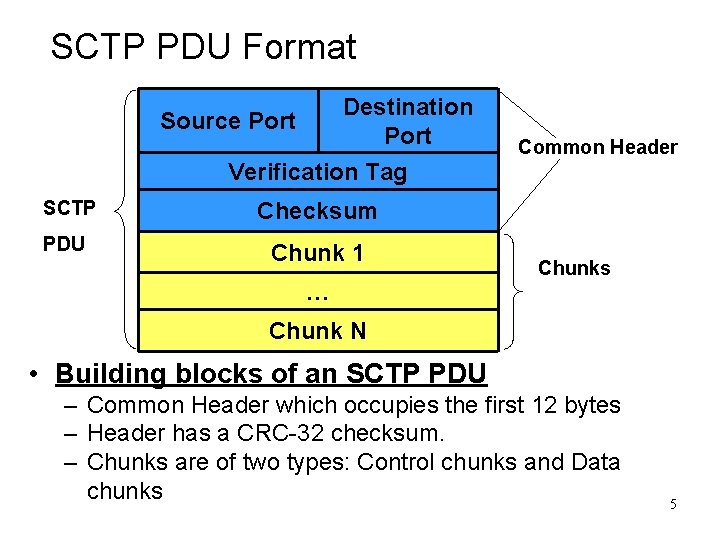
SCTP PDU Format Destination Port Source Port Common Header Verification Tag SCTP Checksum PDU Chunk 1 … Chunks Chunk N • Building blocks of an SCTP PDU – Common Header which occupies the first 12 bytes – Header has a CRC-32 checksum. – Chunks are of two types: Control chunks and Data chunks 5

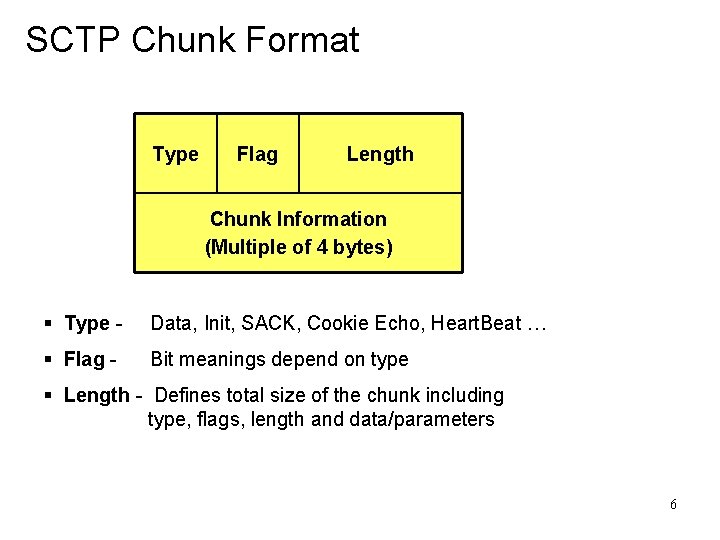
SCTP Chunk Format Type Flag Length Chunk Information (Multiple of 4 bytes) § Type - Data, Init, SACK, Cookie Echo, Heart. Beat … § Flag - Bit meanings depend on type § Length - Defines total size of the chunk including type, flags, length and data/parameters 6

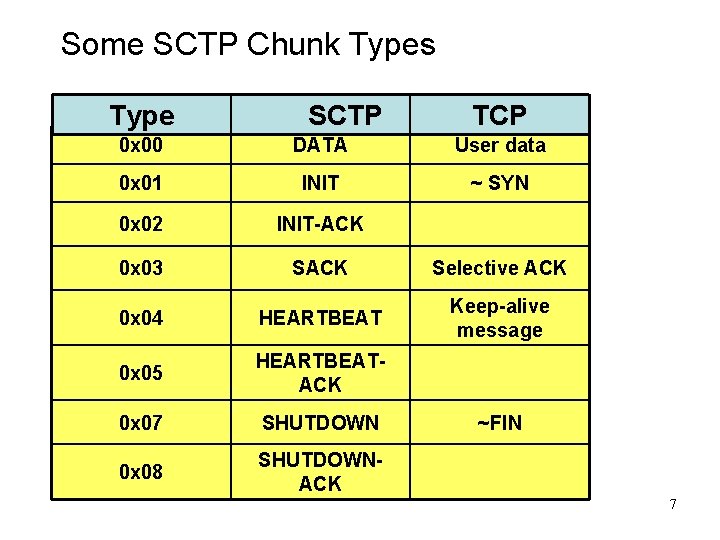
Some SCTP Chunk Types Type SCTP TCP 0 x 00 DATA User data 0 x 01 INIT ~ SYN 0 x 02 INIT-ACK 0 x 03 SACK Selective ACK 0 x 04 HEARTBEAT Keep-alive message 0 x 05 HEARTBEATACK 0 x 07 SHUTDOWN 0 x 08 SHUTDOWNACK ~FIN 7

SCTP Feature Summary What TCP and SCTP both have: ü reliability (retransmissions) ü congestion control ü connection oriented SCTP adds the following: ü 4 -way handshake to reduce vulnerability to Denial of Service attacks ü multihoming instead of one IP address per endpoint a set of IP addresses per endpoint ü framing preserve message boundaries ü multistreaming instead of one ordered stream, up to 64 K independent ordered streams 8

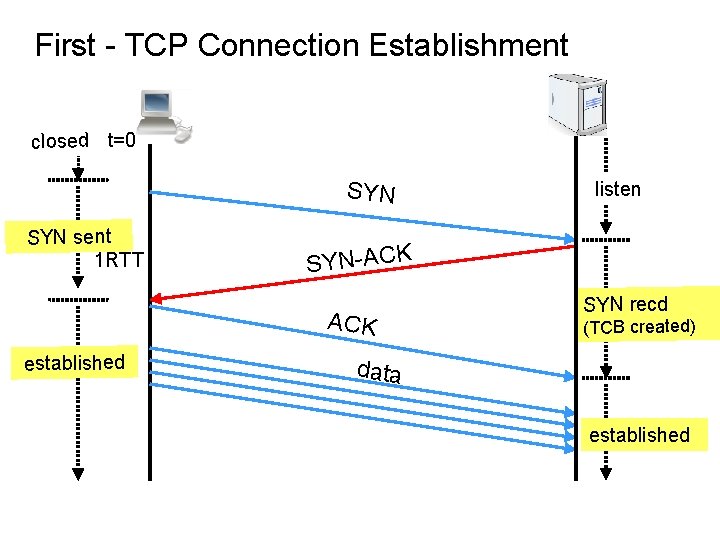
First - TCP Connection Establishment closed t=0 SYN sent 1 RTT SYN-ACK established listen SYN recd (TCB created) data established

Security: TCP Flooding Attack (victim) TCP-based web server (attackers) Internet spoofed SYN’s 128. 3. 4. 5 SYN 130. 2. 4. 15 SYN process SYN TCB 130. 2. 4. 15 TCB 192. 10. 2. 8 SYN 228. 3. 14. 5 TCB 221. 3. 5. 10 SYN 190. 13. 4. 1 flooded!! TCB = Transport Control Block 10

The SCTP Way: 4 -way handshake limits attack (attackers) Internet spoofed INIT’s (victim) SCTP-based web server process INIT 128. 3. 4. 5 INIT 130. 2. 4. 15 INIT-ACK 130. 2. 4. 15 192. 10. 2. 8 INIT 228. 3. 14. 5 INIT-ACK 228. 3. 14. 5 221. 3. 5. 10 INIT 190. 13. 4. 1 INIT-ACK 190. 13. 4. 1 No reserved resources No flooding!! 11

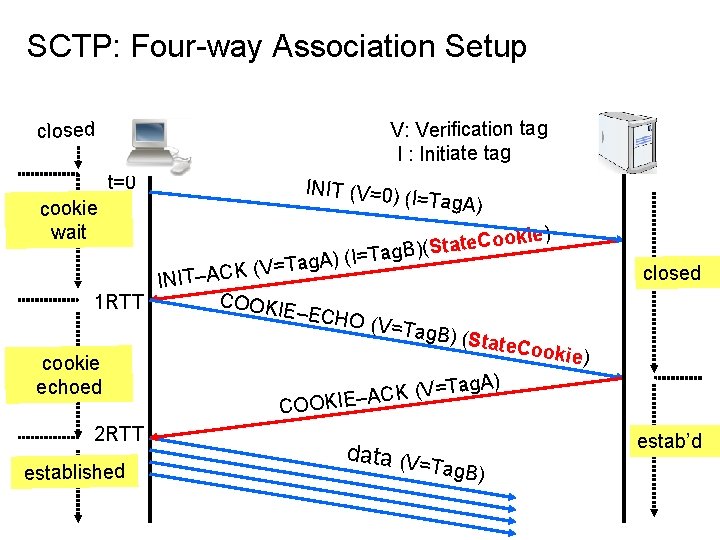
SCTP: Four-way Association Setup V: Verification tag I : Initiate tag closed t=0 cookie wait INIT (V=0) (I=Tag. A ) ookie) C e t a t S ( ) =Tag. B I ( ) A g a T (V= INIT–ACK COOKI 1 RTT E–ECH O (V=T ag. B) (S tate. Coo kie) cookie Tag. A) echoed = V ( K C A COOKIE– 2 RTT data (V= Tag. B) established closed estab’d

What does a Cookie contain? § § § Information from original INIT Information from current INIT-ACK Timestamp Life span of cookie (Time to Live) Signature for authentication (MD 5) 13

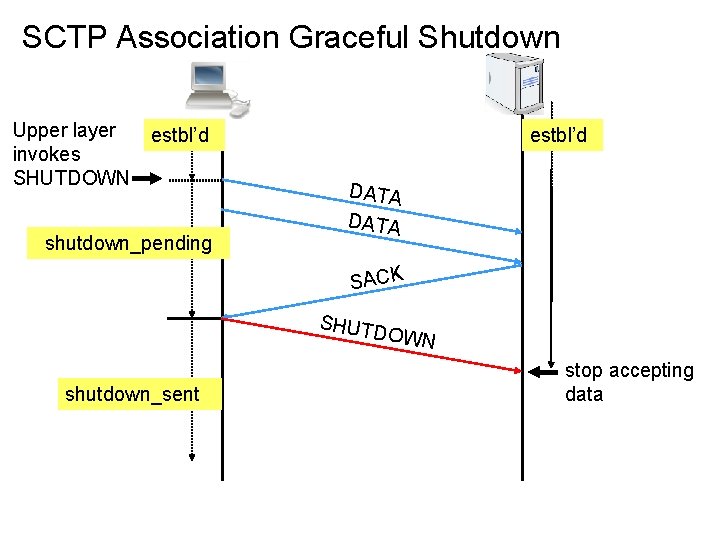
SCTP Association Graceful Shutdown Upper layer invokes SHUTDOWN estbl’d shutdown_pending estbl’d DATA SACK SHUTD OWN shutdown_sent stop accepting data

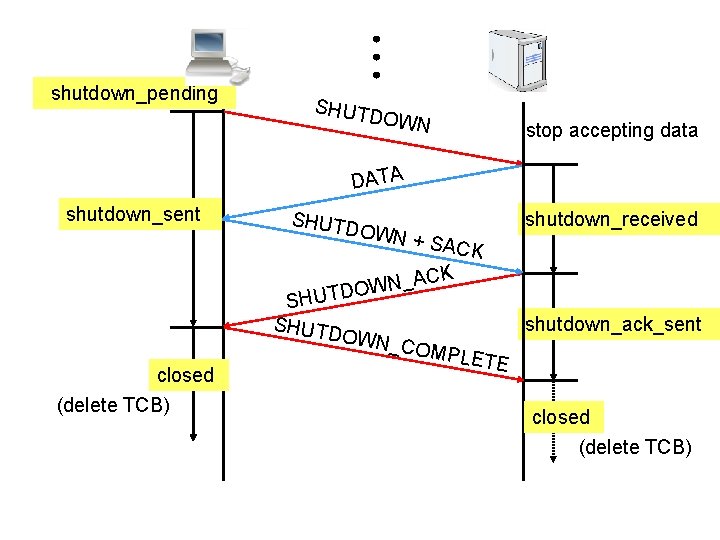
shutdown_pending SHUTD OWN stop accepting data DATA shutdown_sent SHUTD OWN + shutdown_received SACK _ N W UTDO SH SHUTD OW N_COM shutdown_ack_sent closed (delete TCB) PLETE closed (delete TCB)

SCTP Feature Summary What TCP and SCTP both have: ü reliability (retransmissions) ü congestion control ü connection oriented SCTP adds the following: ü 4 -way handshake to reduce vulnerability to Denial of Service attacks ü multihoming instead of one IP address per endpoint a set of IP addresses per endpoint ü framing preserve message boundaries ü multistreaming instead of one ordered stream, up to 64 K independent ordered streams 16

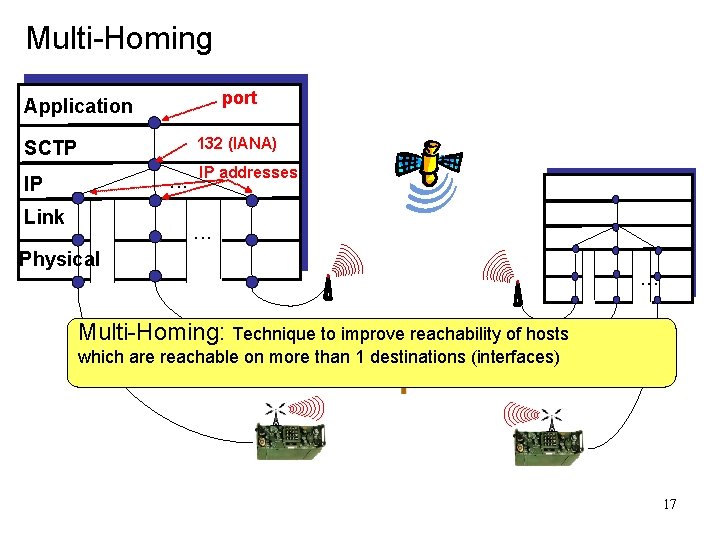
Multi-Homing port Application 132 (IANA) SCTP . . . IP Link IP addresses . . . Physical . . . Multi-Homing: Technique to improve reachability of hosts which are reachable on more than 1 destinations (interfaces) 17

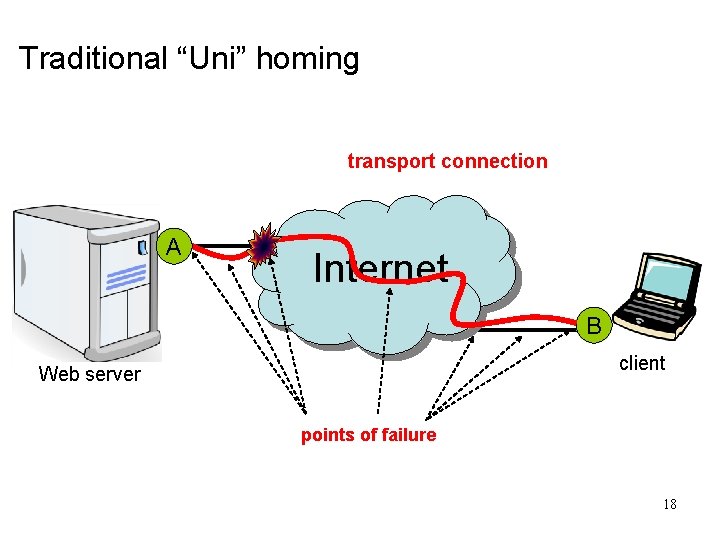
Traditional “Uni” homing transport connection A Internet B client Web server points of failure 18

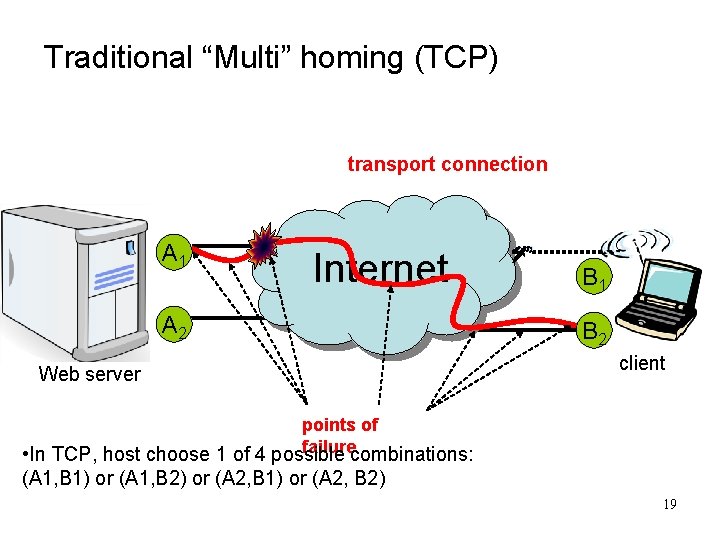
Traditional “Multi” homing (TCP) transport connection A 1 Internet A 2 Web server B 1 B 2 client points of failurecombinations: • In TCP, host choose 1 of 4 possible (A 1, B 1) or (A 1, B 2) or (A 2, B 1) or (A 2, B 2) 19

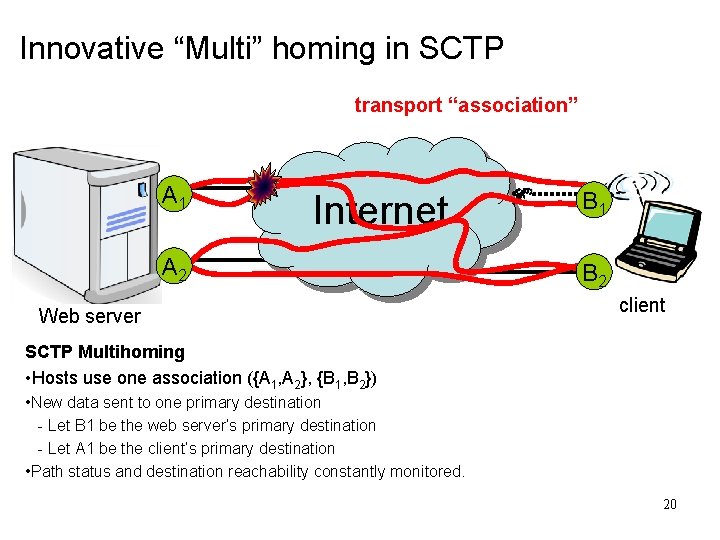
Innovative “Multi” homing in SCTP transport “association” A 1 Internet A 2 Web server B 1 B 2 client SCTP Multihoming • Hosts use one association ({A 1, A 2}, {B 1, B 2}) • New data sent to one primary destination - Let B 1 be the web server’s primary destination - Let A 1 be the client’s primary destination • Path status and destination reachability constantly monitored. 20

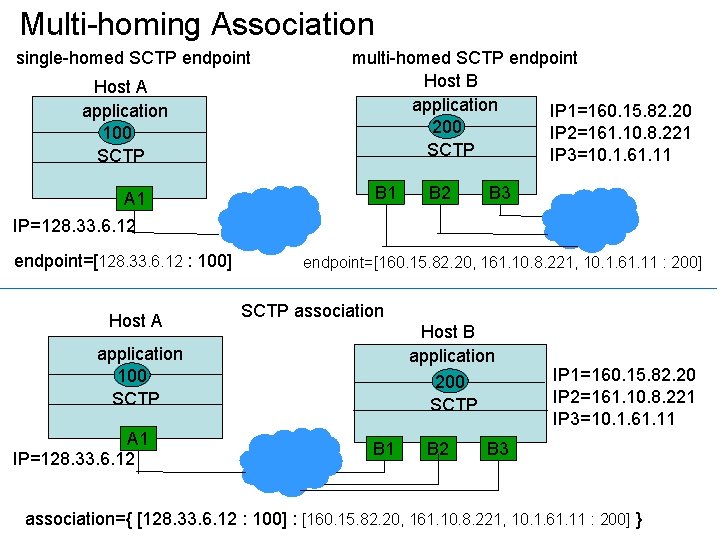
Multi-homing Association single-homed SCTP endpoint Host A application 100 SCTP A 1 IP=128. 33. 6. 12 endpoint=[128. 33. 6. 12 : 100] Host A multi-homed SCTP endpoint Host B application IP 1=160. 15. 82. 20 200 IP 2=161. 10. 8. 221 SCTP IP 3=10. 1. 61. 11 B 3 endpoint=[160. 15. 82. 20, 161. 10. 8. 221, 10. 1. 61. 11 : 200] SCTP association Host B application 200 SCTP application 100 SCTP A 1 IP=128. 33. 6. 12 B 1 B 2 IP 1=160. 15. 82. 20 IP 2=161. 10. 8. 221 IP 3=10. 1. 61. 11 B 3 association={ [128. 33. 6. 12 : 100] : [160. 15. 82. 20, 161. 10. 8. 221, 10. 1. 61. 11 : 200] }

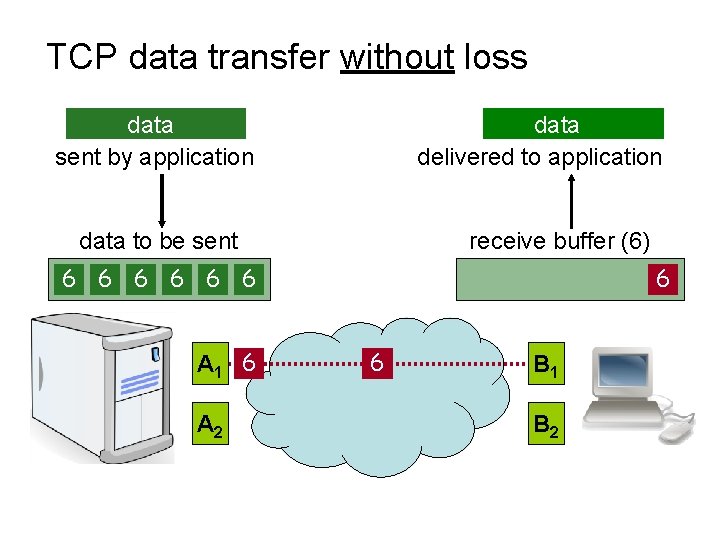
TCP data transfer without loss data sent by application data delivered to application data to be sent receive buffer (6) 6 6 5 6 4 6 5 3 6 4 5 2 6 3 4 5 2 3 4 5 1 4 3 2 5 1 A 1 6 A 2 2 3 4 5 6 1 3 2 4 5 6 1 B 2

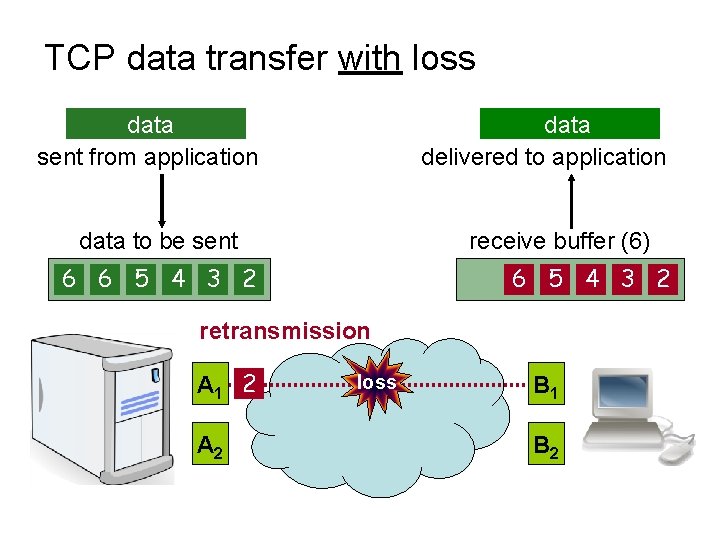
TCP data transfer with loss data delivered to application data sent from application data to be sent receive buffer (6) 6 6 5 5 4 4 3 3 2 2 1 6 5 4 3 2 1 retransmission 4 3 6 5 1 A 1 2 A 2 loss 3 2 4 5 6 1 B 2

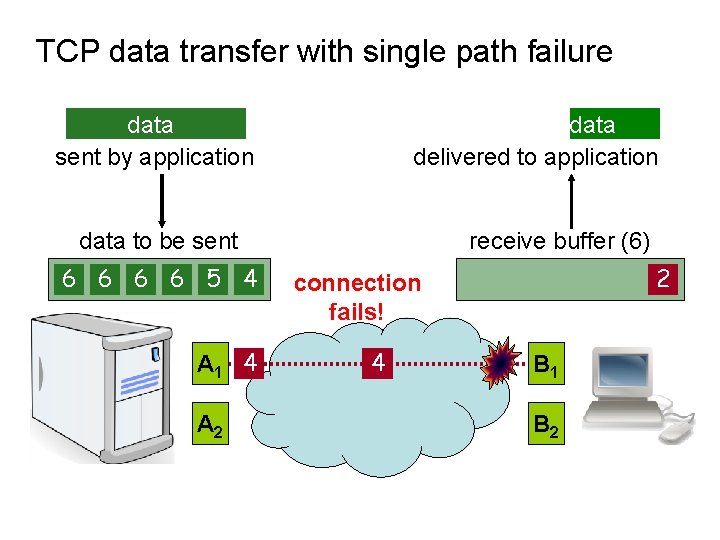
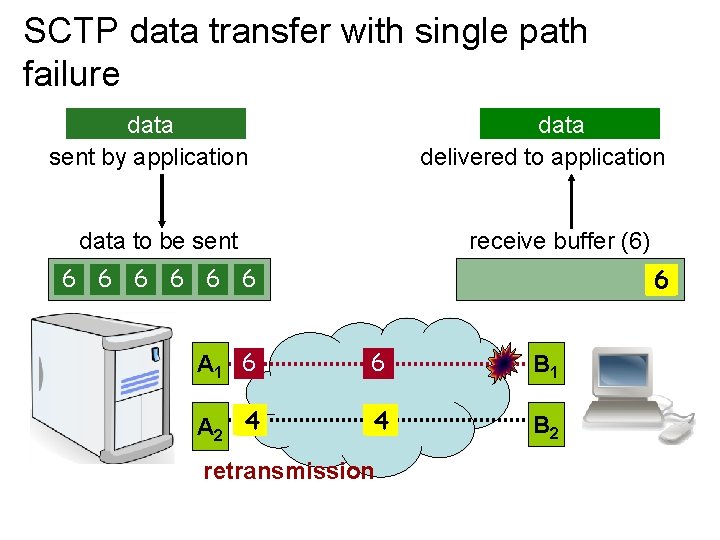
TCP data transfer with single path failure data delivered to application data sent by application data to be sent 6 6 5 6 4 6 5 3 5 4 5 2 4 3 4 2 3 1 3 2 6 5 1 A 1 4 A 2 receive buffer (6) 2 3 1 connection fails! 6 5 4 3 2 1 B 2

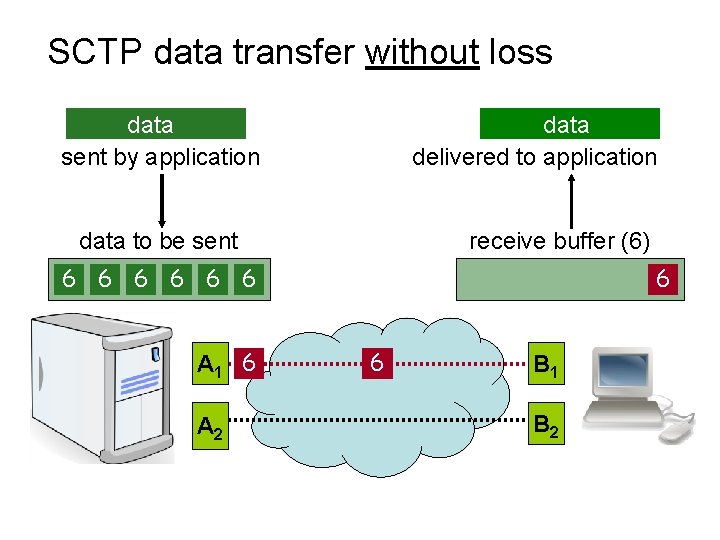
SCTP data transfer without loss data delivered to application data sent by application data to be sent receive buffer (6) 6 6 5 6 4 6 5 3 6 4 5 2 6 3 4 5 2 3 4 5 1 4 3 2 5 1 A 1 6 A 2 2 3 4 5 6 1 3 2 4 5 6 1 B 2

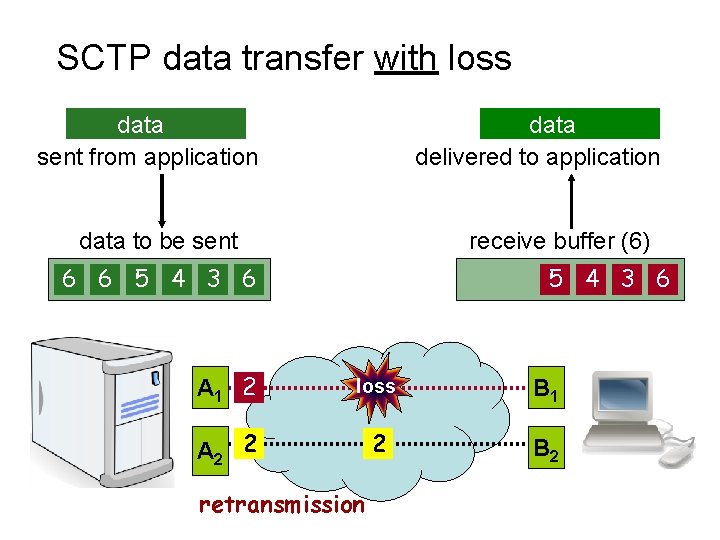
SCTP data transfer with loss data delivered to application data sent from application data to be sent receive buffer (6) 6 6 5 5 4 4 3 3 2 6 2 1 5 4 3 6 2 1 4 3 6 5 1 A 1 2 loss 6 5 4 3 1 B 1 A 2 2 2 B 2 retransmission

SCTP data transfer with single path failure data delivered to application data sent by application data to be sent receive buffer (6) 6 6 5 6 4 6 5 3 6 4 5 2 6 3 4 5 2 3 4 5 1 5 3 2 4 1 6 2 6 3 4 1 A 1 5 5 4 3 2 6 1 B 1 4 A 2 65 64 5 B 2 retransmission

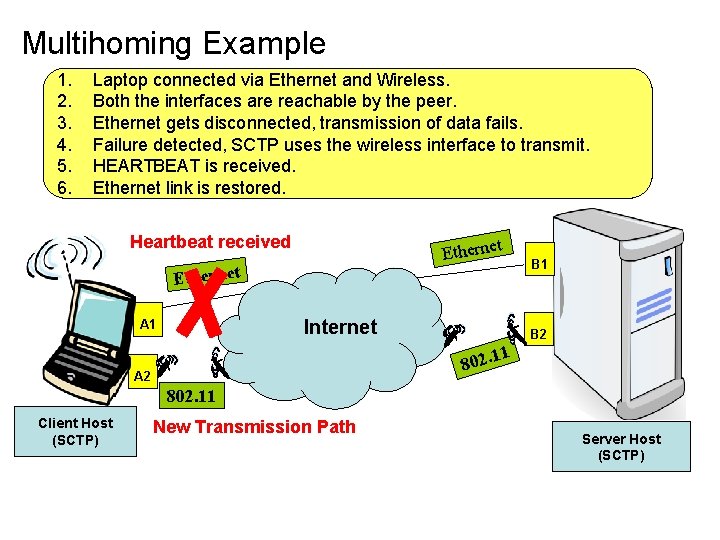
Multihoming Example 1. 2. 3. 4. 5. 6. Laptop connected via Ethernet and Wireless. Both the interfaces are reachable by the peer. Ethernet gets disconnected, transmission of data fails. Failure detected, SCTP uses the wireless interface to transmit. HEARTBEAT is received. Ethernet link is restored. Heartbeat received Ethernet t Internet A 1 B 2 11 802. A 2 802. 11 Client Host (SCTP) New Transmission Path Server Host (SCTP)

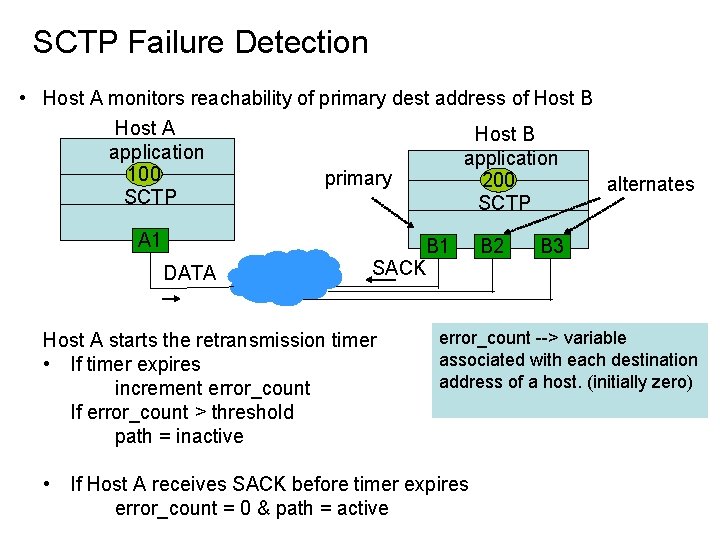
SCTP Failure Detection • Host A monitors reachability of primary dest address of Host B Host A Host B application 100 primary 200 alternates SCTP A 1 DATA B 1 SACK Host A starts the retransmission timer • If timer expires increment error_count If error_count > threshold path = inactive B 2 B 3 error_count --> variable associated with each destination address of a host. (initially zero) • If Host A receives SACK before timer expires error_count = 0 & path = active

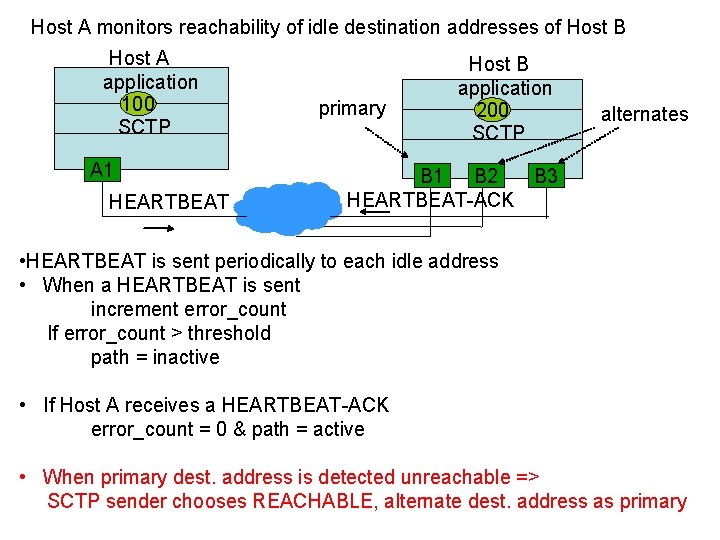
Host A monitors reachability of idle destination addresses of Host B Host A application 100 SCTP A 1 HEARTBEAT primary Host B application 200 SCTP alternates B 1 B 2 B 3 HEARTBEAT-ACK • HEARTBEAT is sent periodically to each idle address • When a HEARTBEAT is sent increment error_count If error_count > threshold path = inactive • If Host A receives a HEARTBEAT-ACK error_count = 0 & path = active • When primary dest. address is detected unreachable => SCTP sender chooses REACHABLE, alternate dest. address as primary

HEARTBEAT? • HEARTBEAT is a chunk that an endpoint sends to its peer endpoints to probe the reachability of a particular destination transport address. • In our case, the HEARTBEAT is sent to a destination address which has been idle for a long time to check for its reachability. • HEARTBEAT ACK is a chunk which an endpoint sends to its peer endpoints as a response to a HEARBEAT chunk. 31

Summary of SCTP • SCTP used for applications which require data reliability and rigid timing. • SCTP provides security against DOS attacks by using cookies during association • SCTP association can bind multiple IP addresses at each endpoint • SCTP provides multi-homing for applications that require high degree of fault tolerance. 32

Reference Material Textbooks Stream Control Transmission Protocol (SCTP) Randall Stewart, Qiaobing Xie, Addison Wesley, 2002 TCP/IP Protocol Suite – Chapter 13 Behrouz Forouzan RFC’s • RFC 2960 - Stream Control Transmission Protocol • RFC 3286 - An Introduction to SCTP • RFC 4460 - SCTP Specification Errata and Issues 33

Thank You!!!! 34