Security versus Compliance STRICTLY CONFIDENTIAL 2020 Insta Med
















- Slides: 24

Security versus Compliance STRICTLY CONFIDENTIAL © 2020 Insta. Med. All rights reserved.

STRICTLY CONFIDENTIAL Security vs. Compliance Security tools, technologies and best practices that can be taken to offer layers of protection Compliance • regulatory requirements that must be met STRICTLY CONFIDENTIAL © 2016 Insta. Med. All rights reserved.

What Compliance Addresses STANDARDS MOTIVATOR BUDGET DRIVER STRICTLY CONFIDENTIAL

Attested, Validated and Certified Attestation – Self-review, affirming Validated – Reviewed by an outside group Certification – Outside group reviewing submission STRICTLY CONFIDENTIAL

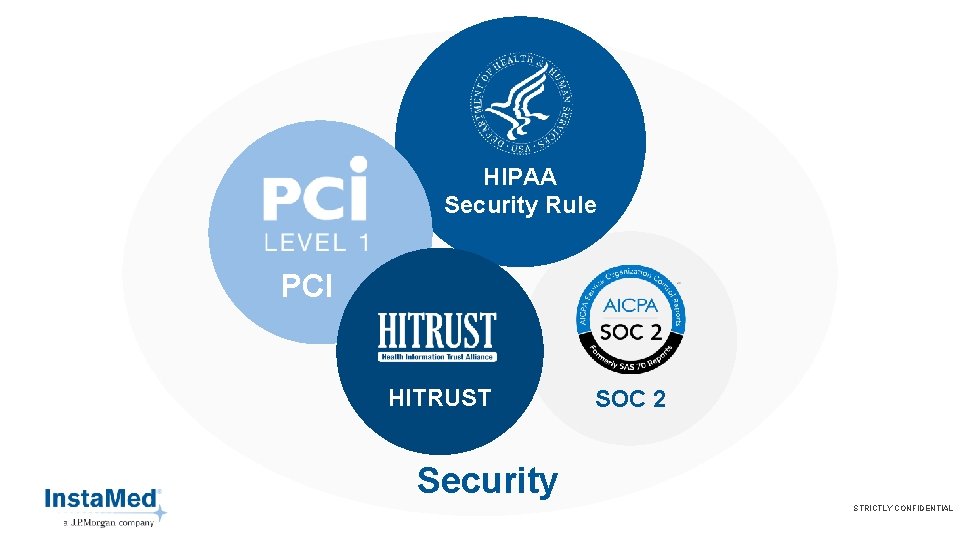
HIPAA Security Rule PCI HITRUST SOC 2 Security STRICTLY CONFIDENTIAL

Is One More Important Than the Other? PCI Compliant September 2013 October 2013 November 2013 December 2013 Hacked STRICTLY CONFIDENTIAL

What’s the Financial Risk? $7. 13 Million The average total cost of a healthcare data breach is $7. 13 million. 329 Days The average time to identify and contain a healthcare data breach is 329 days. Source: Ponemon STRICTLY CONFIDENTIAL

Overview of HIPAA STRICTLY CONFIDENTIAL © 2020 Insta. Med. All rights reserved.

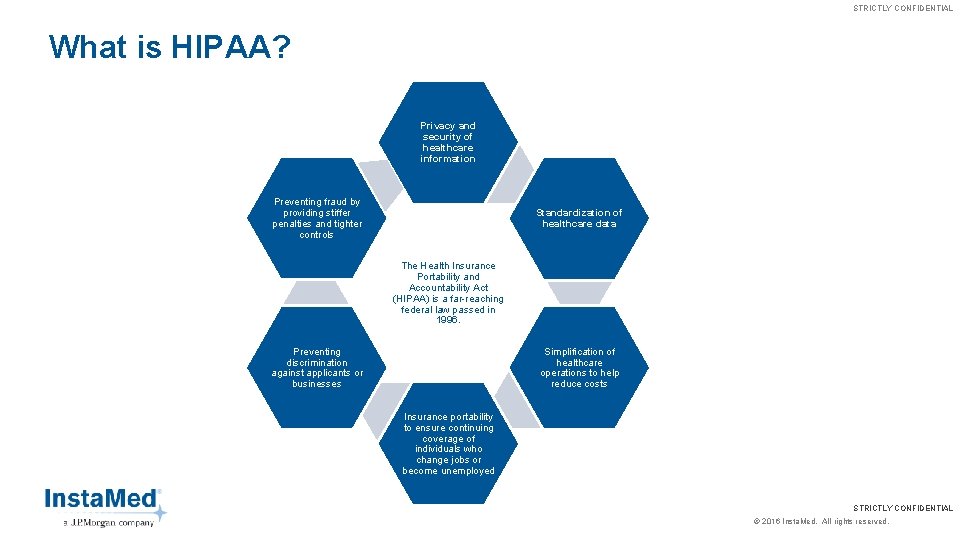
STRICTLY CONFIDENTIAL What is HIPAA? Privacy and security of healthcare information Preventing fraud by providing stiffer penalties and tighter controls Standardization of healthcare data The Health Insurance Portability and Accountability Act (HIPAA) is a far-reaching federal law passed in 1996. Simplification of healthcare operations to help reduce costs Preventing discrimination against applicants or businesses Insurance portability to ensure continuing coverage of individuals who change jobs or become unemployed STRICTLY CONFIDENTIAL © 2016 Insta. Med. All rights reserved.

Covered Entities Organizations such as hospitals, insurance companies, self-insured employers, and small physician practices are considered covered entities under HIPAA. Covered Entities include: Health Plans Healthcare Providers Clearing House STRICTLY CONFIDENTIAL

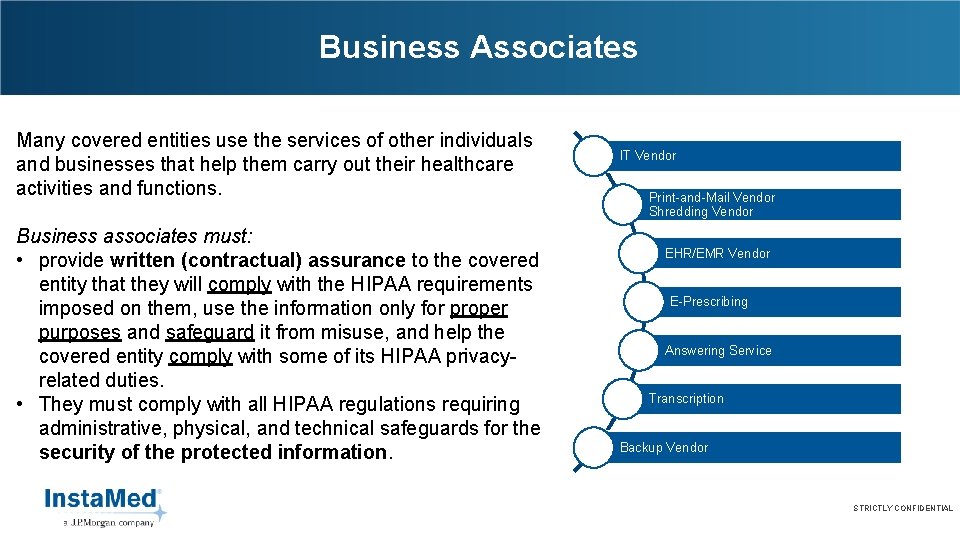
Business Associates Many covered entities use the services of other individuals and businesses that help them carry out their healthcare activities and functions. Business associates must: • provide written (contractual) assurance to the covered entity that they will comply with the HIPAA requirements imposed on them, use the information only for proper purposes and safeguard it from misuse, and help the covered entity comply with some of its HIPAA privacyrelated duties. • They must comply with all HIPAA regulations requiring administrative, physical, and technical safeguards for the security of the protected information. IT Vendor Print-and-Mail Vendor Shredding Vendor EHR/EMR Vendor E-Prescribing Answering Service Transcription Backup Vendor STRICTLY CONFIDENTIAL

STRICTLY CONFIDENTIAL Penalties Failure to comply with HIPAA can lead to significant financial and other penalties, such as the following: Civil fines range from $100 to $50, 000 for each violation up to $1. 5 million per year. Criminal penalties for a basic offense may include a fine of up to $50, 000 and/or imprisonment for up to one year. Criminal penalties for an offense committed under false pretenses may include a fine of up to $100, 000 and/or imprisonment for up to five years. Criminal penalties for an offense committed with the intent to use PHI for one's commercial advantage may include a fine of up to $250, 000 and/or imprisonment for up to ten years. STRICTLY CONFIDENTIAL © 2016 Insta. Med. All rights reserved.

Cyber Security & Healthcare The Johns Hopkins Academic Medical Center Approach

Managing the Patients Information • Use of Epic EHR – electronic medical record system • Role based access • Integrated automation for patient treatment • Improved functionality for availability & downtime handling • Medical Device Security • Health data replicated in real time & offline • Patient information used in medical research is tightly managed • Use of Business Associates Agreements when involving third parties

Separating Clinical & Academic environments • Cultural differences of data and systems availability • Clinical – data is extremely private (HIPAA) and the dependency on systems availability is critical to patient care and safety • Academic – Open access, free exchange of idea and data, availability less critical • As a result the larger Hopkins technical environment is broken down at the network level to ensure the appropriate level of protection and redundancy for the individual Hopkins Communities i. e. Clinical/Research/Academic/Financial

What tools are applied to protect Johns Hopkins ? • Network Segmentation • Advanced Next Generation Firewalls • Intrusion Detection & Prevention • Access Control & Authentication • Multifactor Authorization • Anti-phisihing tools • Ongoing Pen testing (internal & external) • Logging & Log management • Privileged Account Management • Specific Incident Monitoring ^ Management (NOC) • Data backup & Redundancy

There’s still risk ! • FBI issued an alert on 10/28/20 of an increased and imminent threat to healthcare organizations for ransomware attacks • Four healthcare institutions have been reported hit by ransomware so far this week, three belonging to the St. Lawrence County Health System in upstate New York and the Sky Lakes Medical Center in Klamath Falls, Oregon. AP- 10/29/20 • A total of 59 U. S. healthcare providers/systems have been impacted by ransomware in 2020, disrupting patient care at up to 510 facilities, Callow said. Cybersecurity firm Emisoft 10/2020 • Universal Health System Ransomware attack Sept 2020 • Nebraska Medicine Sept. 2020 • Johns Hopkins has well over 50, 000 employees and in excess of 150, 000 devices accessing the network, each represents a point of risk. • Hundreds of active 3 rd parties involved in delivery of our services, their risks can become ours if not managed appropriately

Vendor Management STRICTLY CONFIDENTIAL © 2020 Insta. Med. All rights reserved.

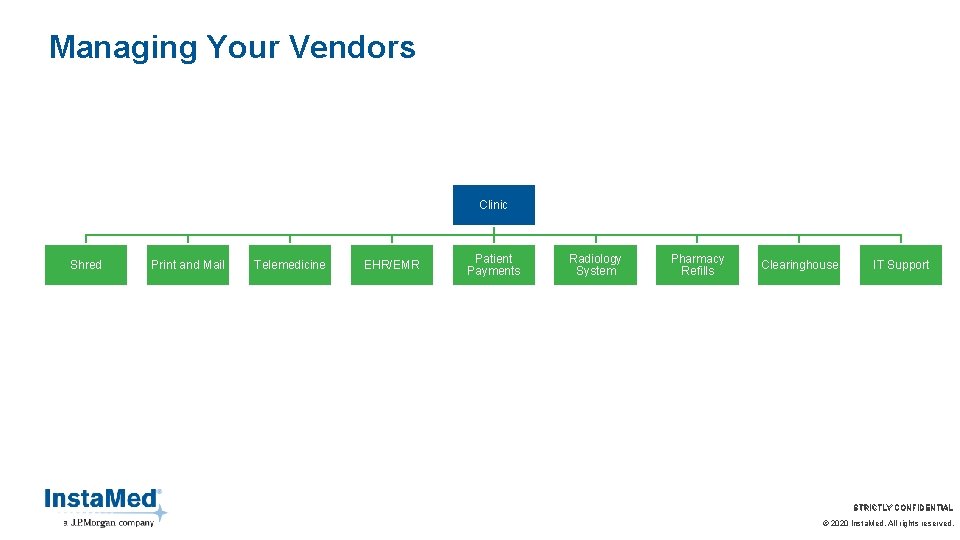
Managing Your Vendors Clinic Shred Print and Mail Telemedicine EHR/EMR Patient Payments Radiology System Pharmacy Refills Clearinghouse IT Support STRICTLY CONFIDENTIAL © 2020 Insta. Med. All rights reserved.

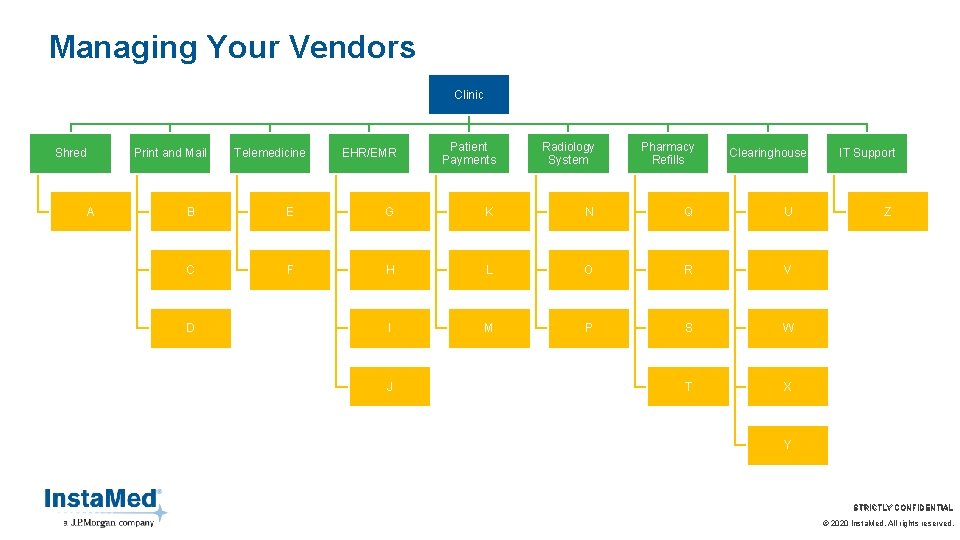
Managing Your Vendors Clinic Shred Print and Mail A Telemedicine EHR/EMR Patient Payments Radiology System Pharmacy Refills Clearinghouse B E G K N Q U C F H L O R V I M P S W T X D J IT Support Z Y STRICTLY CONFIDENTIAL © 2020 Insta. Med. All rights reserved.

Managing Your Vendors Clinic Print and Mail Shred A B C 1 3 2 4 Telemedicin e D 5 E 6 Patient Payments EHR/EMR F G H I J K 7 10 12 15 18 22 8 11 13 16 19 23 14 17 20 9 21 L 24 Radiology System M N O Pharmacy Refills P Q R Clearinghou se S T U V W IT Support X 25 27 30 34 40 43 49 53 55 58 62 67 26 28 31 35 41 44 50 54 56 59 63 68 29 32 36 42 45 51 57 60 64 69 33 37 46 52 61 65 38 47 39 48 Y 70 Z 71 73 72 74 75 66 STRICTLY CONFIDENTIAL © 2020 Insta. Med. All rights reserved.

Pay. Pal – 600 3 rd Parties STRICTLY CONFIDENTIAL https: //www. paypal. com/va/webapps/mpp/ua/third-parties-list

Vendor Example - Lockbox Not all lockboxes are the same Some Questions To Ask Your Lockbox Vendor • Are their employees trained on HIPAA? • What employee screening is done? (ex: OIG, OFAC, etc. ) • Are they willing to complete a Business Associate Agreement (BAA)? • What is their business resiliency plan in the event a site has to be closed? • Do they physically segregate processing of healthcare lockboxes (PHI) from the non-healthcare lockboxes? • What employee screening is done? (ex: OIG, OFAC, etc. ) • What security controls do they have in place? • How and where does the vendor store images and the data they process? • How does the vendor limit the number of people accessing the lockbox? • Does your lockbox vendor encourage online payments? 7 STRICTLY CONFIDENTIAL

Disclaimer Slide STRICTLY CONFIDENTIAL
 Not for onward distribution
Not for onward distribution Confidential not for circulation
Confidential not for circulation Strictly private & confidential
Strictly private & confidential Strictly private & confidential
Strictly private & confidential Strictly private and confidential
Strictly private and confidential Strictly private & confidential
Strictly private & confidential Confidential
Confidential Strictly private and confidential
Strictly private and confidential Strictly private and confidential
Strictly private and confidential Suranne jones strictly confidential
Suranne jones strictly confidential Strictly confidential not for distribution
Strictly confidential not for distribution Private secuirty
Private secuirty Due diligence sjekkliste
Due diligence sjekkliste Revm arapça tanımı
Revm arapça tanımı Insta trac
Insta trac Milena lutovac insta
Milena lutovac insta Insta grap
Insta grap Habibmetro car finance
Habibmetro car finance Instavu
Instavu Nmi laboratory
Nmi laboratory Insta line
Insta line Insta book
Insta book Hvad er insta 800
Hvad er insta 800 Security compliance monitoring
Security compliance monitoring Microsoft from back doors gov active
Microsoft from back doors gov active











































