Security Management GEANT SIGSIM ALF MOENS SECURITY MANAGEMENT













- Slides: 22

Security Management GEANT SIG-SIM – ALF MOENS SECURITY MANAGEMENT IN NORWAY – ROLF STURE NORMANN SECURITY MANAGEMENT AT DEIC – HENRIK LARSEN Nordunet 2016 - Helsinki

SIG Information Security Management & WISE Alf Moens

Whoami Corporate security officer SURF Board member SCIPR Chair SIG-ISM Board member WISE Member Géant Community Committee ICT and security background with strong interest in privacy Board member Dutch Platform for security professionals Master Information Security Management (MISM, 2007)

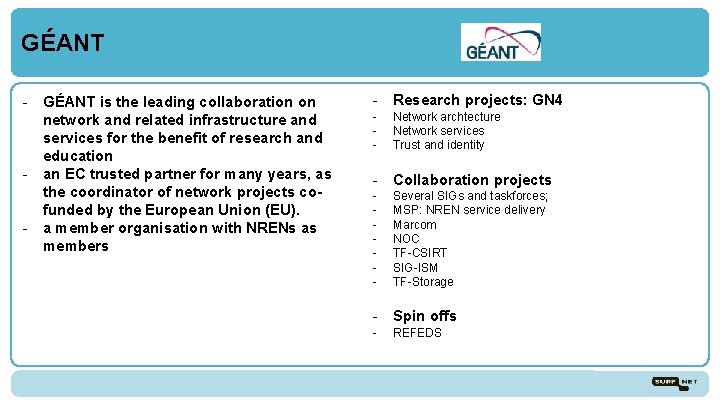
GÉANT - GÉANT is the leading collaboration on network and related infrastructure and services for the benefit of research and education - an EC trusted partner for many years, as the coordinator of network projects cofunded by the European Union (EU). - a member organisation with NRENs as members - Research projects: GN 4 - Network archtecture Network services Trust and identity - Collaboration projects - Several SIGs and taskforces; MSP: NREN service delivery Marcom NOC TF-CSIRT SIG-ISM TF-Storage - Spin offs - REFEDS

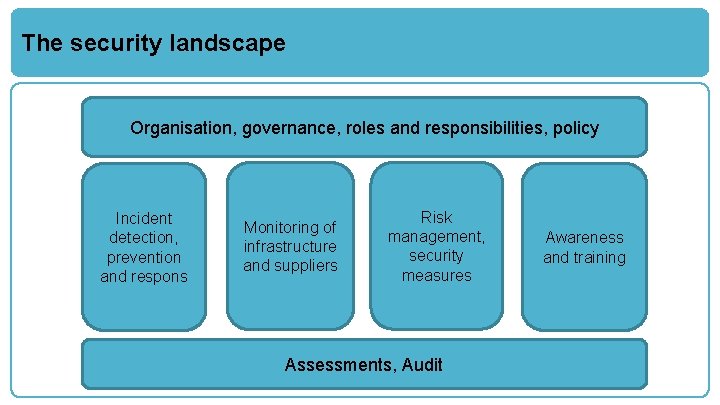
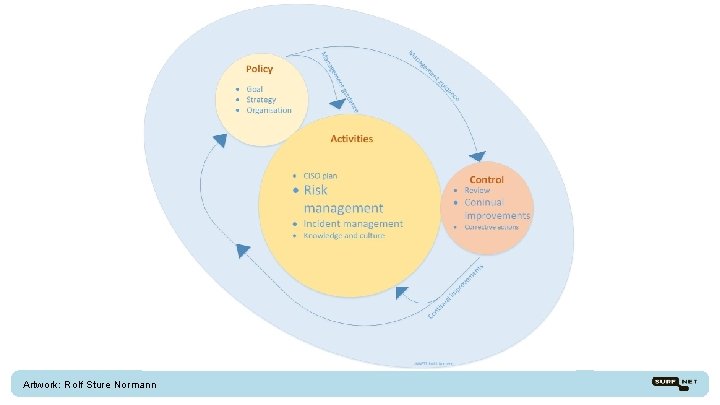
The security landscape Organisation, governance, roles and responsibilities, policy Incident detection, prevention and respons Monitoring of infrastructure and suppliers Risk management, security measures Assessments, Audit Awareness and training

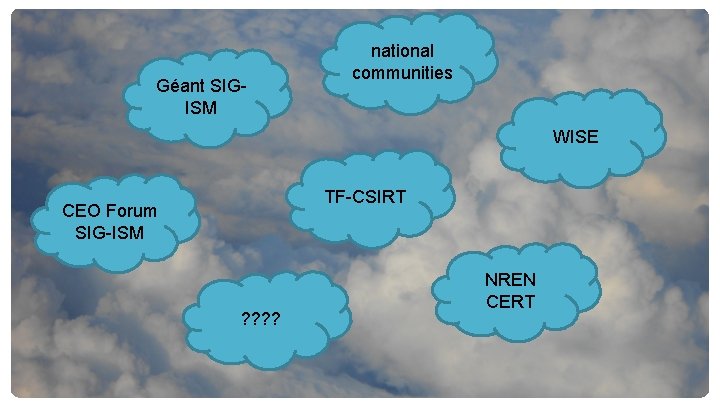
Who is doing what in the security landscape?

Géant SIGISM national communities WISE TF-CSIRT CEO Forum SIG-ISM ? ? NREN CERT

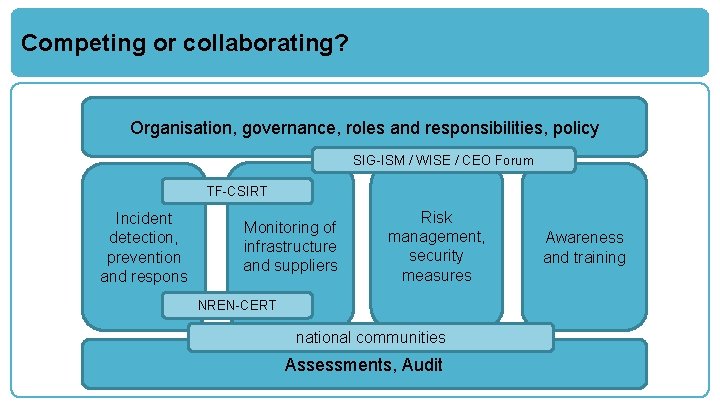
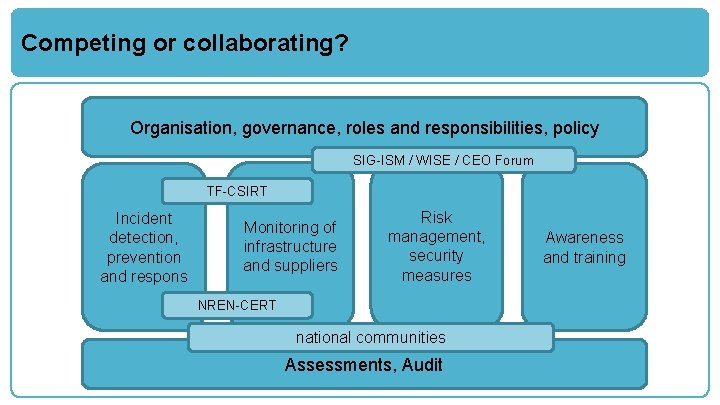
Competing or collaborating? Organisation, governance, roles and responsibilities, policy SIG-ISM / WISE / CEO Forum TF-CSIRT Incident detection, prevention and respons Monitoring of infrastructure and suppliers Risk management, security measures NREN-CERT national communities Assessments, Audit Awareness and training

WISE – security for e-infrastructures WISE is for the e-infrastructures, globally, both networking and super- and gridcomputing infrastructures. WISE was initiated by Géant SIG-ISM and SCI. SIG-ISM: Information Security Management SCI: Security for Collaboration among Infrastructures “Launching” e-infrastructures: Géant (European research and education networks) EGI (European Grid Infrastructure) EUDAT (research data services) PRACE (high performance computing) Participating communities NRENs, HEP/CERN, the Human Brain Project, XSEDE, NCSA, CTSC, LIGO and others Kick off meeting at BSC, Barcelona, oktober 2015, 49 participants Workshops at XSEDE and DI 4 R in 2016

WISE working program 2016 • Updating the SCI-framework: an operational security framework with guidance for incident response, changes, user management • Security Training and Awareness: what training do you need, what is available • Risk Assessment: Looking at the major risks on information security for an e-infrastructure • Security Review and Audit: Can we set up a program of peer reviewing? What should you audit and when? • Security in Big and Open Data: Identifying the security needs for big and open data

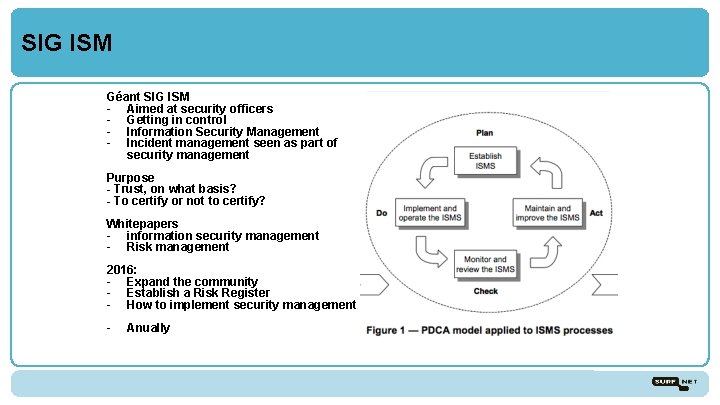
SIG ISM Géant SIG ISM - Aimed at security officers - Getting in control - Information Security Management - Incident management seen as part of security management Purpose - Trust, on what basis? - To certify or not to certify? Whitepapers - information security management - Risk management 2016: - Expand the community - Establish a Risk Register - How to implement security management - Anually

Artwork: Rolf Sture Normann

SIG ISM is looking at NREN needs Strong CERTs/CSIRTs Trust Some are ISO 27001 certified or are working on it: - Because they are a tld registry - Because they deliver services to government - Internal motivation: goals for quality management With SIG-ISM we are joining forces on the subject of trust Strong CERTs/CSIRTs

Whitepaper on Security Management High level paper on how to organise information security in you organisation - Role and responsibilities - Selecting standards Full paper at: https: //wiki. geant. org/display/SIGISM/SIG+ISM +white+paper+security+management

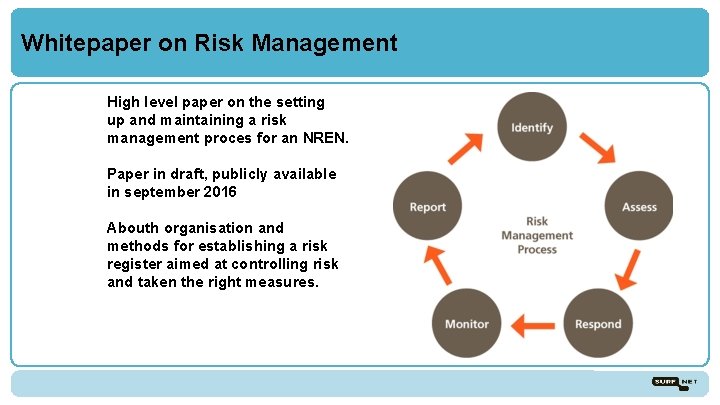
Whitepaper on Risk Management High level paper on the setting up and maintaining a risk management proces for an NREN. Paper in draft, publicly available in september 2016 Abouth organisation and methods for establishing a risk register aimed at controlling risk and taken the right measures.

Designing the Risk Matrix • SIG ISM worked on 3 subjects of the Risk Matrix in her february workshop in Copenhagen • Risks concerning hosted services • Risks concerning People • Risks concerning federated identity management systems • First steps to a comprehensive risk matrix for an NREN • Cooperate with WISE WG-SRA

Outcome Copenhagen Workshop (work in progress) Hosted Services People • infrastructure complexity • • insecure software or • infrastructures • • supplier • • incident detection • • trust/over-delegation • Economical loss/reputation Sickness Leaving staff Segregation of duties Policies Screening (lack of) Federations • Declining (implicit) trust in growing federations • Federation operator procedures and responsibilities • Users cannot log in • Cannot identify abuser/intruder • Leak/abuse of personal information • SP Data/Attribute profiles appropriate • Protocol implementation vulnerabilities

Results of the September 2016 Trondheim Workshop • • Write up success stories: What works, what doesn’t work Business case for security management: when is security a success? Share information and documentation Expand the risk register Tooling for security and risk management, and for secure sharing of information Set up a directory of key people with a short description (2 -pager) of what they are doing and how Set up a FAQ Survey on ISM Trondheim

Competing or collaborating? Organisation, governance, roles and responsibilities, policy SIG-ISM / WISE / CEO Forum TF-CSIRT Incident detection, prevention and respons Monitoring of infrastructure and suppliers Risk management, security measures NREN-CERT national communities Assessments, Audit Awareness and training

Allways be prepared For your next incident

From incident handling to security management Key Largo

Alf Moens Alf. moens@surfnet. nl www. surfnet. nl Foto’s: Alf Moens