Safe Internet Use Mark Wheatley CSI Onsite 952












- Slides: 19

Safe Internet Use Mark Wheatley CSI Onsite 952 -928 -1788 support@csionsite. com

About Us �In business for over 15 years �Purpose & Values driven �Member in good standing with:

Safe Internet Use �What can we do to stay ahead? �What to watch out for ◦ What is a URL? ◦ What is Phishing / Spoofing? �Threat Evolution - Malware �Good Practice - 5 rules (CSI Onsite Style)

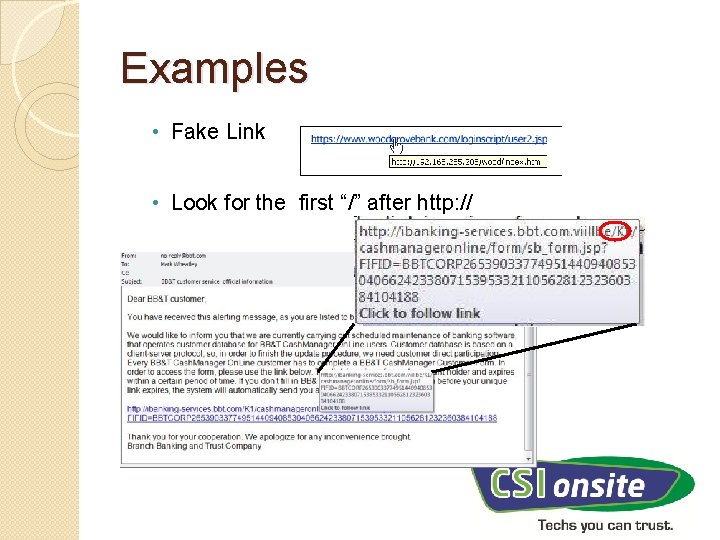
What to watch out for • URLs – Uniform Resource Locator • URL is the address to visit a web site • Domain name translates to an IP address • Can be masked to appear as something different than actual address • Web browser ignores the @ symbol in address • Besides the http: //, look for the first “/” • Words to the left of that slash, is actual domain name

What to watch out for • Hyperlinks, URLs and Redirects • Easy to spoof • Underlying address may be different than visible link • Domain names that are close to actual • www. micosoft. com • www. verify-microsoft. com • ww. mircosoft. com • Examples

Examples • Fake Link • Look for the first “/” after http: //

What to watch out for • Phishing • Get you to click on link/s with malicious or fraudulent intent • Potential for identity theft • Fake emails from company with whom you do business • Pay. Pal / EBay fraud • Fake charities • Urgent wording • Fake links with legitimate appearance http: //office. microsoft. com/en-us/outlook/HA 011400021033. aspx

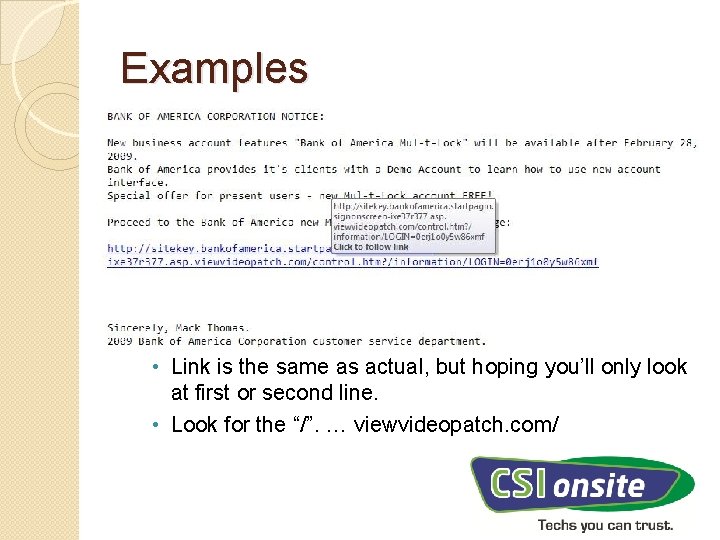
Examples • Link is the same as actual, but hoping you’ll only look at first or second line. • Look for the “/”. … viewvideopatch. com/

What to watch out for • Email Spoofing • Email appearing to be from someone other than the actual sender • Spamming technique • Creates concern for recipient • Could be sent from infected computer • Open relays • Many ISPs requiring outbound e-mail authentication to keep infected computers from relaying email

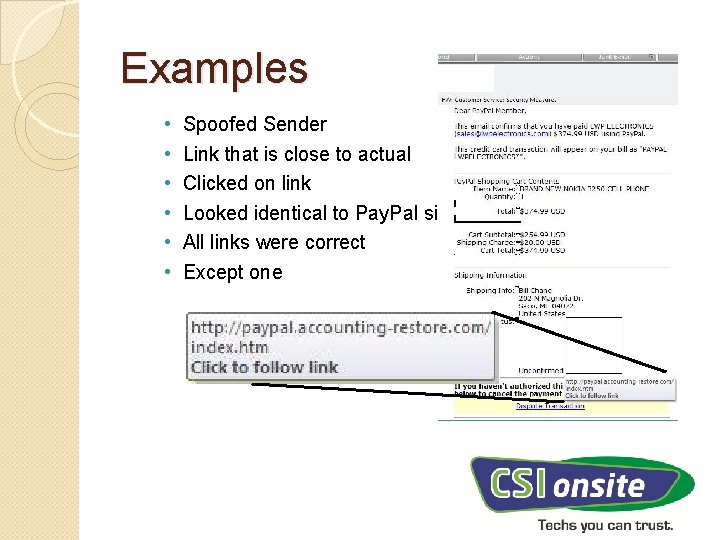
Examples • • • Spoofed Sender Link that is close to actual Clicked on link Looked identical to Pay. Pal site All links were correct Except one

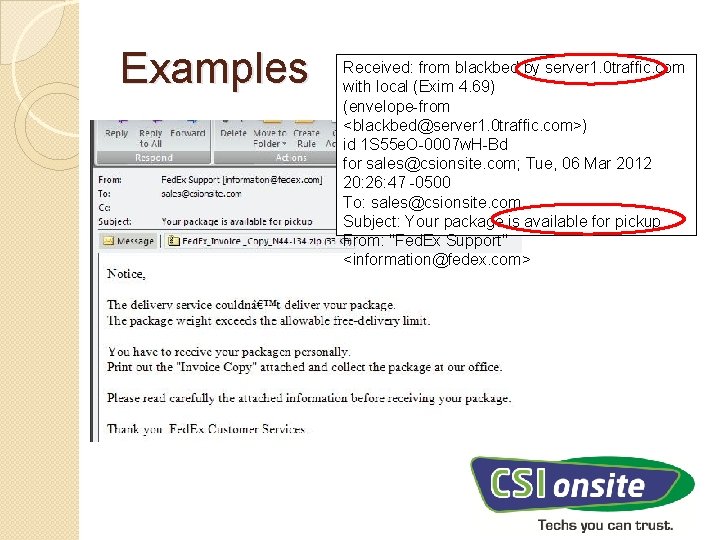
Examples Received: from blackbed by server 1. 0 traffic. com with local (Exim 4. 69) (envelope-from <blackbed@server 1. 0 traffic. com>) id 1 S 55 e. O-0007 w. H-Bd for sales@csionsite. com; Tue, 06 Mar 2012 20: 26: 47 -0500 To: sales@csionsite. com Subject: Your package is available for pickup From: "Fed. Ex Support" <information@fedex. com>

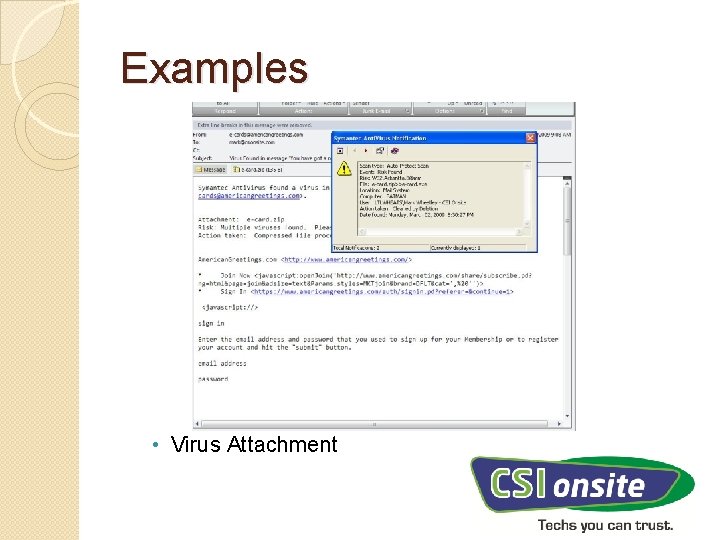
Threat Evolution • What is Malware? • Short for Malicious Software • Disrupt computer operation, gather information or exploit system or data, without consent • Hostile, intrusive or annoying software • Delivered to system via: • Email attachment • Web site re-direct • Infected system, flash drive, software install

Examples • Virus Attachment

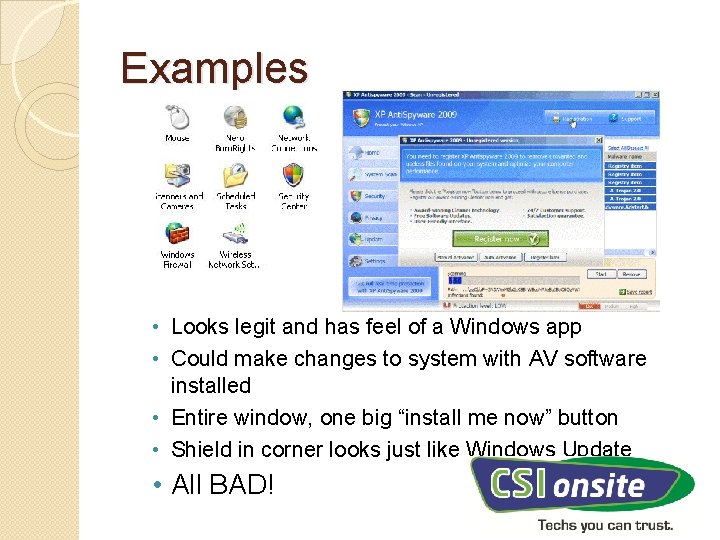
Threat Evolution • Can look like legitimate software • Hold your system ransom • Lock system down so even skilled technicians may choose to reload computer operating system, or restore from backup rather than try to find or undo changes • Capture credit card information, leading to identity theft

Examples • Looks legit and has feel of a Windows app • Could make changes to system with AV software installed • Entire window, one big “install me now” button • Shield in corner looks just like Windows Update • All BAD!

Threat Evolution • Malicious intent – take down company web presence • Organized crime • Fraud • Financial gain • 1% of 1 million emails = 10, 000 • X $40 = a lot of money to be had….

What can we do to stay ahead • • • Education, education Software can’t always protect you Be suspicious of Internet content Operate computer with lesser privileges Watch for drive-by downloads, or piggy-backing Verify the software you do install, is legitimate and has good intentions • Email settings / spam filters • Create regular backups and system restore points

5 Basic Rules � Keep your antivirus software installed and definitions up to date � Careful where you browse… � Be careful when opening emails from people you do AND don’t know � Microsoft does not typically send updates or patches via email and neither do most software manufacturers � Check your hyperlinks and URLs before clicking

Questions… Give us a call and we will help you out.