Remote Control and Advanced Techniques Remote Control Software


- Slides: 4

Remote Control and Advanced Techniques

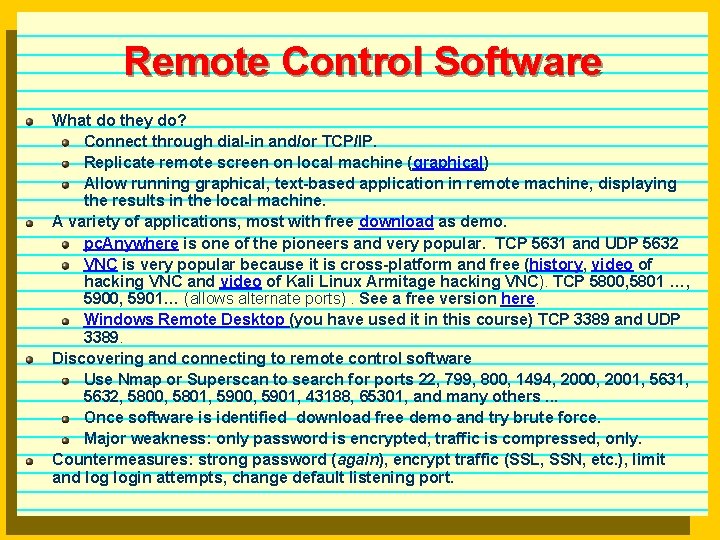
Remote Control Software What do they do? Connect through dial-in and/or TCP/IP. Replicate remote screen on local machine (graphical) Allow running graphical, text-based application in remote machine, displaying the results in the local machine. A variety of applications, most with free download as demo. pc. Anywhere is one of the pioneers and very popular. TCP 5631 and UDP 5632 VNC is very popular because it is cross-platform and free (history, video of hacking VNC and video of Kali Linux Armitage hacking VNC). TCP 5800, 5801 …, 5900, 5901… (allows alternate ports). See a free version here. Windows Remote Desktop (you have used it in this course) TCP 3389 and UDP 3389. Discovering and connecting to remote control software Use Nmap or Superscan to search for ports 22, 799, 800, 1494, 2000, 2001, 5632, 5800, 5801, 5900, 5901, 43188, 65301, and many others. . . Once software is identified download free demo and try brute force. Major weakness: only password is encrypted, traffic is compressed, only. Countermeasures: strong password (again), encrypt traffic (SSL, SSN, etc. ), limit and login attempts, change default listening port.

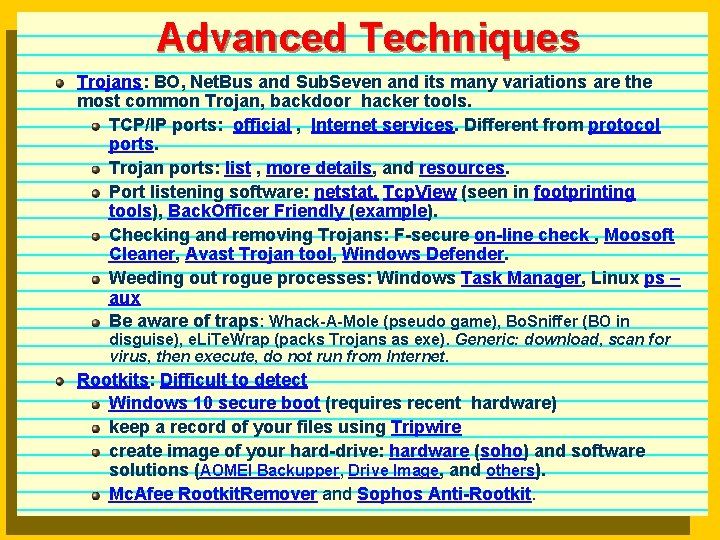
Advanced Techniques Trojans: BO, Net. Bus and Sub. Seven and its many variations are the most common Trojan, backdoor hacker tools. TCP/IP ports: official , Internet services. Different from protocol ports. Trojan ports: list , more details, and resources. Port listening software: netstat, Tcp. View (seen in footprinting tools), Back. Officer Friendly (example). Checking and removing Trojans: F-secure on-line check , Moosoft Cleaner, Avast Trojan tool, Windows Defender. Weeding out rogue processes: Windows Task Manager, Linux ps – aux Be aware of traps: Whack-A-Mole (pseudo game), Bo. Sniffer (BO in disguise), e. Li. Te. Wrap (packs Trojans as exe). Generic: download, scan for virus, then execute, do not run from Internet. Rootkits: Difficult to detect Windows 10 secure boot (requires recent hardware) keep a record of your files using Tripwire create image of your hard-drive: hardware (soho) and software solutions (AOMEI Backupper, Drive Image, and others). Mc. Afee Rootkit. Remover and Sophos Anti-Rootkit.

Other Techniques TCP hijacking Juggernaut: spy on a TCP connection and issue commands as the logged user. Hunt: spy on a TCP connection (works with shared and switched networks). Countermeasures: encrypted protocols such as IPSec, SSH. TFTP: Trivial File Transfer Protocol. Used by routers, and there are free servers for Windows. Available client in Windows : tftp. exe Prevent its use by Nimda (mostly obsolete) or similar: 1) Edit the services file: %systemroot%/system 32/drivers/etc/services 2) Find this line: tftp 69/udp 3) Replace it with: tftp 0/udp Social Engineering Help desk information: on the Web, e-mail, voice User information: on the Web, e-mail, voice Social Engineering in Kali Linux (SET): a tutorial.