Realization of a Vision Authentication and Authorization Infrastructure



- Slides: 22

Realization of a Vision: Authentication and Authorization Infrastructure for the Swiss Higher Education Community Copyright Martin Sutter, 2003. This work is the intellectual property of the author. Permission is granted for this material to be shared for non-commercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by permission of the author. To disseminate otherwise or to republish requires written permission from the author. 2003 © SWITCH

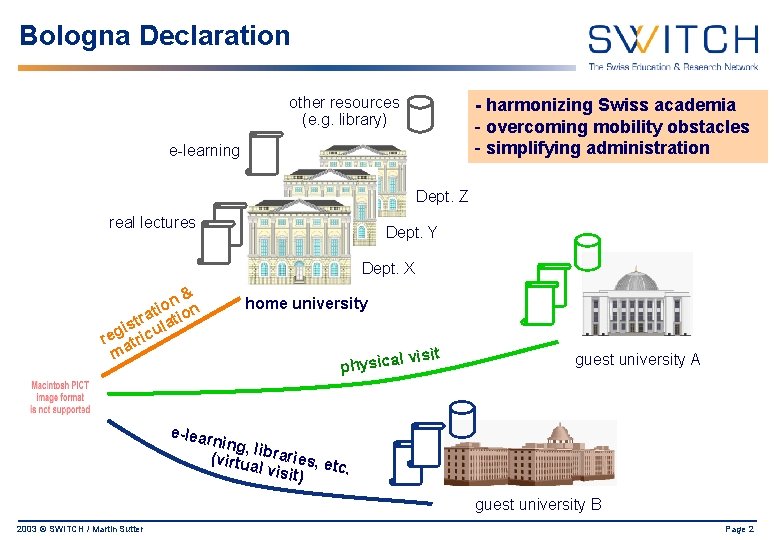
Bologna Declaration other resources (e. g. library) - harmonizing Swiss academia - overcoming mobility obstacles - simplifying administration e-learning Dept. Z real lectures Dept. Y Dept. X n& o i at tion r t is cula g e r atri m home university l visit a c i s y h p guest university A e-lear ning, l (virtu ibraries, e tc. al vis it) guest university B 2003 © SWITCH / Martin Sutter Page 2

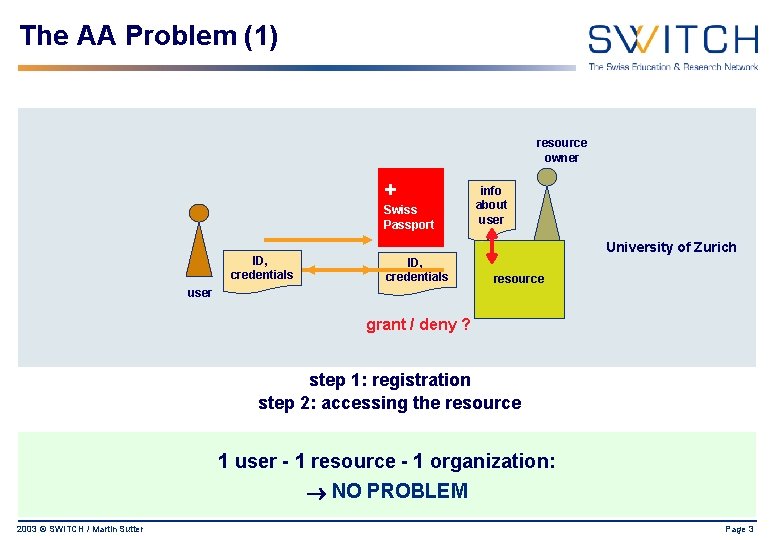
The AA Problem (1) resource owner + Swiss Passport ID, credentials info about user University of Zurich ID, credentials resource user grant / deny ? step 1: registration step 2: accessing the resource 1 user - 1 resource - 1 organization: NO PROBLEM 2003 © SWITCH / Martin Sutter Page 3

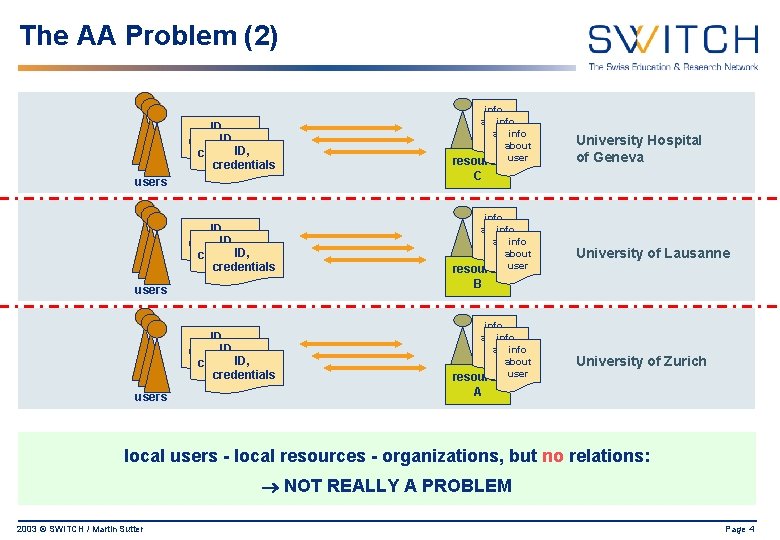
The AA Problem (2) ID, credentials info about info user about info about user resource user ID, credentials info about user info user about resource users C University of Lausanne B users ID, credentials users University Hospital of Geneva info about info user about resource user University of Zurich A local users - local resources - organizations, but no relations: NOT REALLY A PROBLEM 2003 © SWITCH / Martin Sutter Page 4

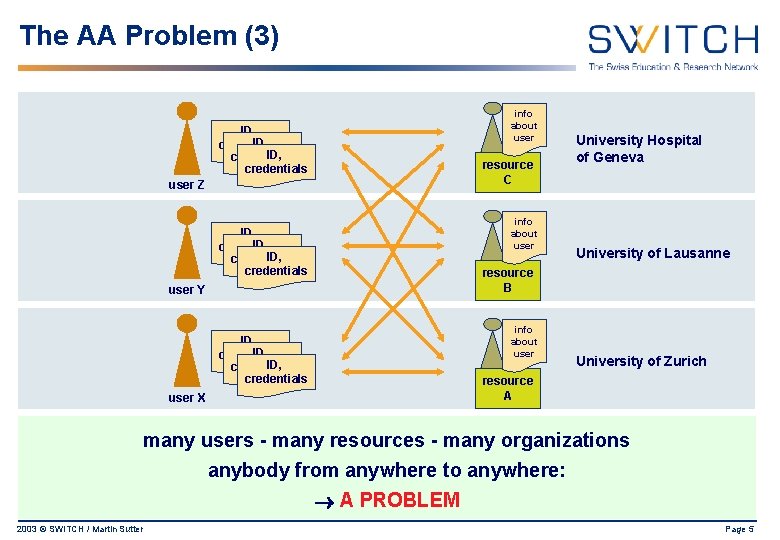
The AA Problem (3) info about user ID, credentials resource C user Z info about user ID, credentials University Hospital of Geneva University of Lausanne resource B user Y info about user ID, credentials University of Zurich resource A user X many users - many resources - many organizations anybody from anywhere to anywhere: A PROBLEM 2003 © SWITCH / Martin Sutter Page 5

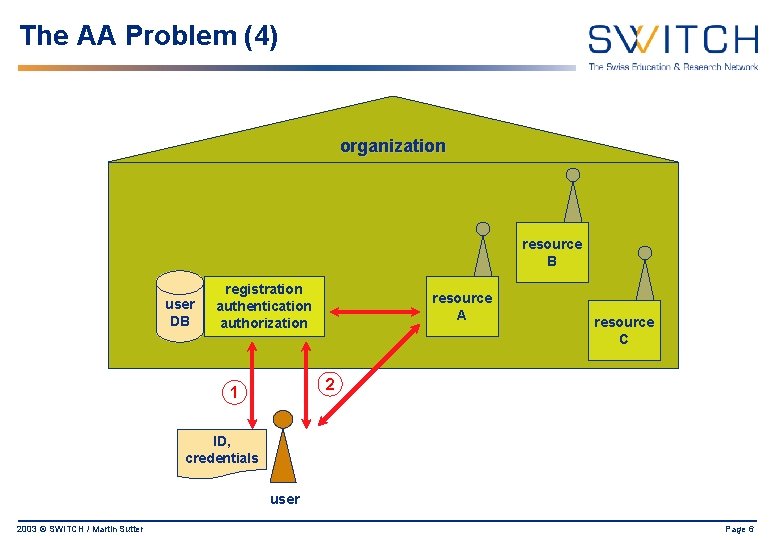
The AA Problem (4) organization resource B user DB registration authentication authorization resource A resource C 2 1 ID, credentials user 2003 © SWITCH / Martin Sutter Page 6

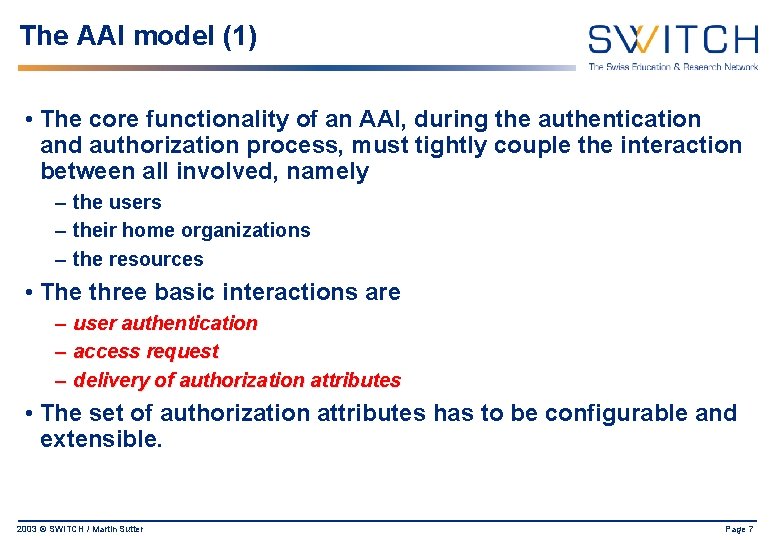
The AAI model (1) • The core functionality of an AAI, during the authentication and authorization process, must tightly couple the interaction between all involved, namely – the users – their home organizations – the resources • The three basic interactions are – user authentication – access request – delivery of authorization attributes • The set of authorization attributes has to be configurable and extensible. 2003 © SWITCH / Martin Sutter Page 7

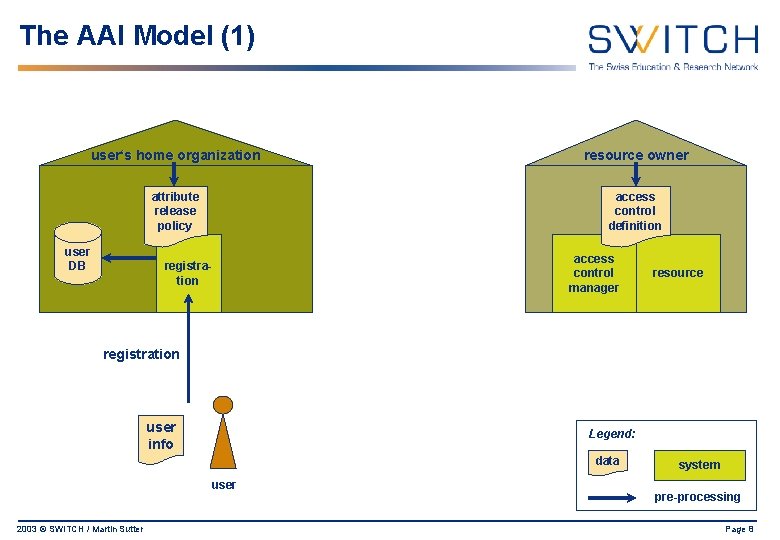
The AAI Model (1) user‘s home organization resource owner attribute release policy access control definition user DB registration access control manager resource registration user info Legend: data user 2003 © SWITCH / Martin Sutter system pre-processing Page 8

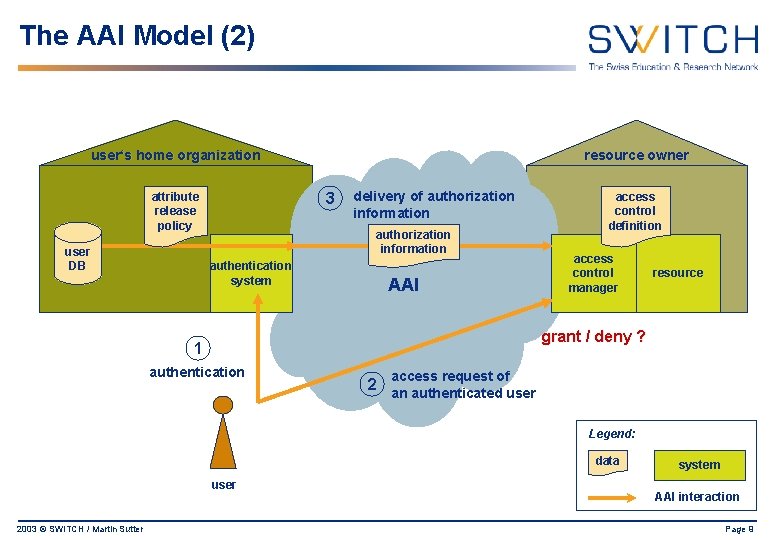
The AAI Model (2) user‘s home organization 3 attribute release policy user DB resource owner delivery of authorization information authentication system AAI access control definition access control manager resource grant / deny ? 1 authentication access request of 2 an authenticated user Legend: data user 2003 © SWITCH / Martin Sutter system AAI interaction Page 9

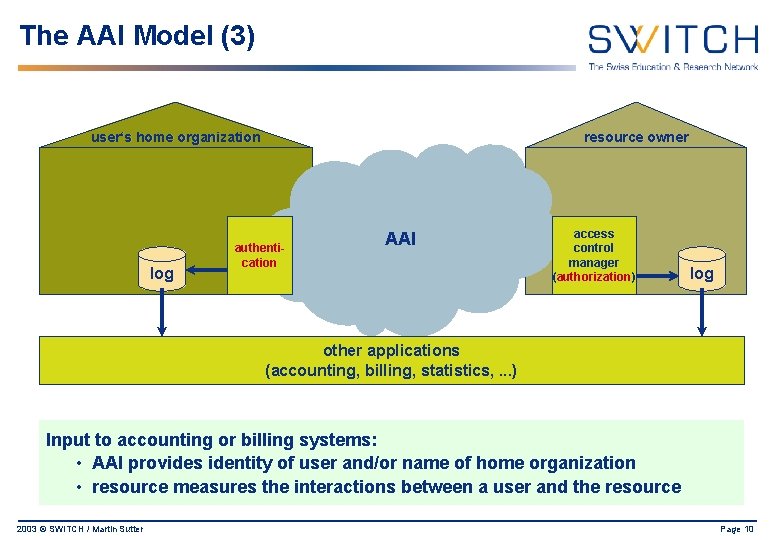
The AAI Model (3) user‘s home organization log resource owner authentication AAI access control manager (authorization) log other applications (accounting, billing, statistics, . . . ) Input to accounting or billing systems: • AAI provides identity of user and/or name of home organization • resource measures the interactions between a user and the resource 2003 © SWITCH / Martin Sutter Page 10

Connecting Campuses • In practice, everything is not so simple… • connecting resources to the AAI faces problems • • campus history commercial products financial considerations … 2003 © SWITCH / Martin Sutter Page 11

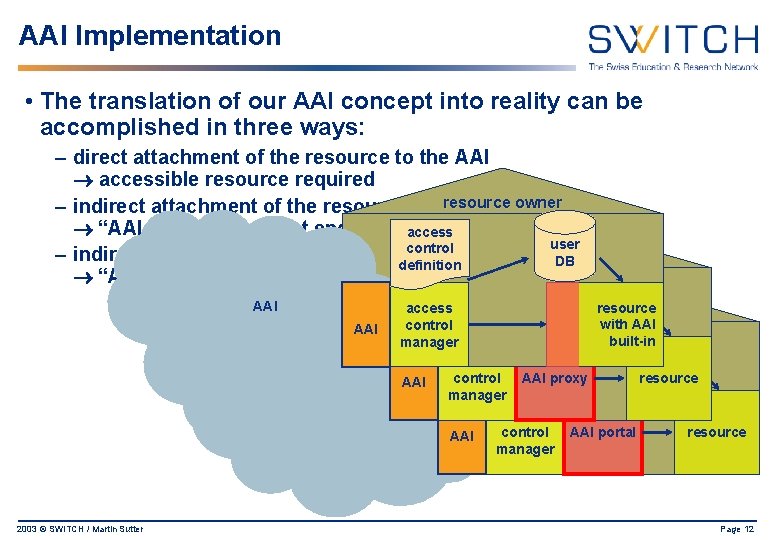
AAI Implementation • The translation of our AAI concept into reality can be accomplished in three ways: – direct attachment of the resource to the AAI accessible resource required resource – indirect attachment of the resource to the AAI, owner method I “AAI proxy” as a front end to theaccess resource user control – indirect attachment of the resourcedefinition to the AAI, method resource owner. II DB “AAI portal” AAI AAI 2003 © SWITCH / Martin Sutter access user resource access control resource owner DB definition with AAI control built-in manager access user access control DB controldefinition AAI proxy resource AAI manager access control AAI portal resource AAI manager Page 12

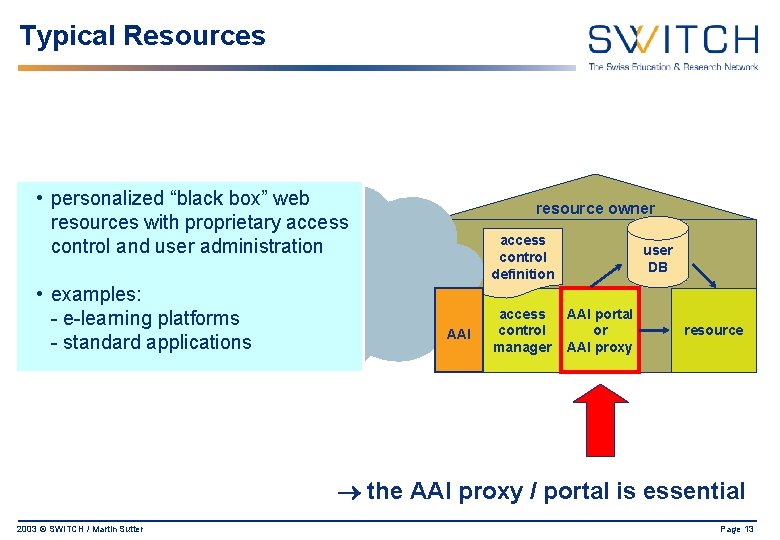
Typical Resources • personalized “black box” web resources with proprietary access control and user administration • examples: - e-learning platforms - standard applications resource owner access control definition AAI access control manager user DB AAI portal or AAI proxy resource the AAI proxy / portal is essential 2003 © SWITCH / Martin Sutter Page 13

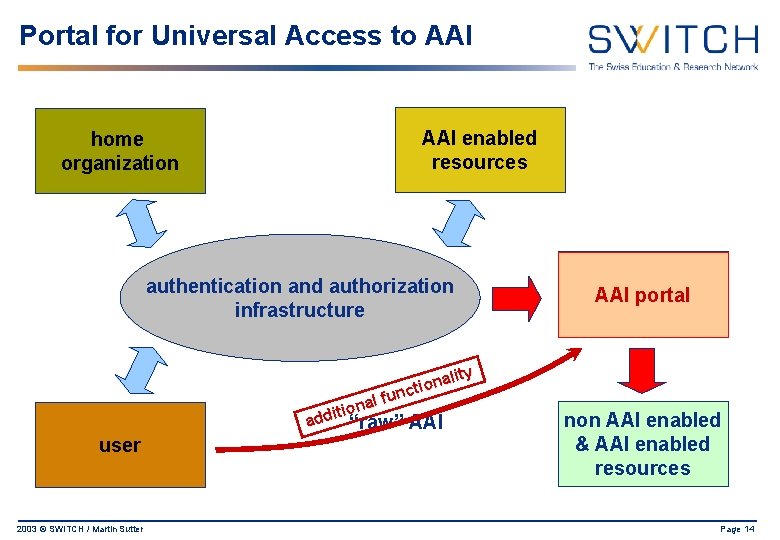
Portal for Universal Access to AAI home organization AAI enabled resources authentication and authorization infrastructure lity a n o ncti u f l iona t i d ad “raw” AAI user 2003 © SWITCH / Martin Sutter proxy AAI portal non AAI enabled & AAI enabled resources Page 14

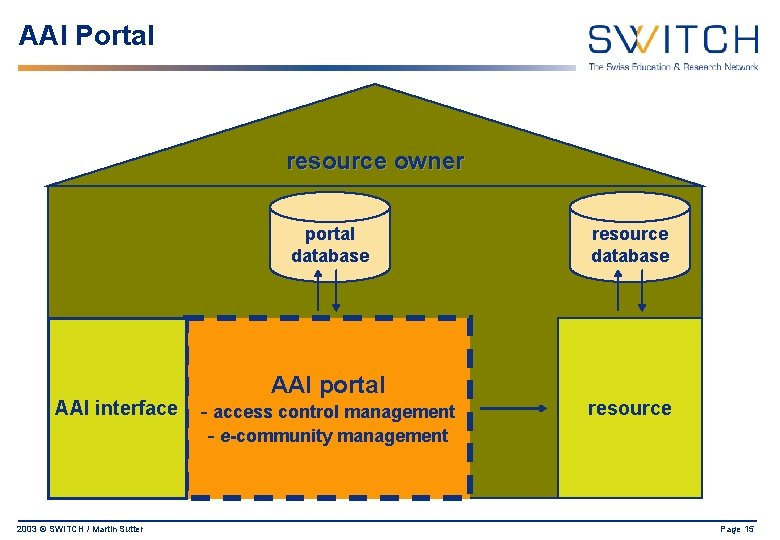
AAI Portal resource owner portal database AAI interface 2003 © SWITCH / Martin Sutter AAI portal - access control management - e-community management resource database resource Page 15

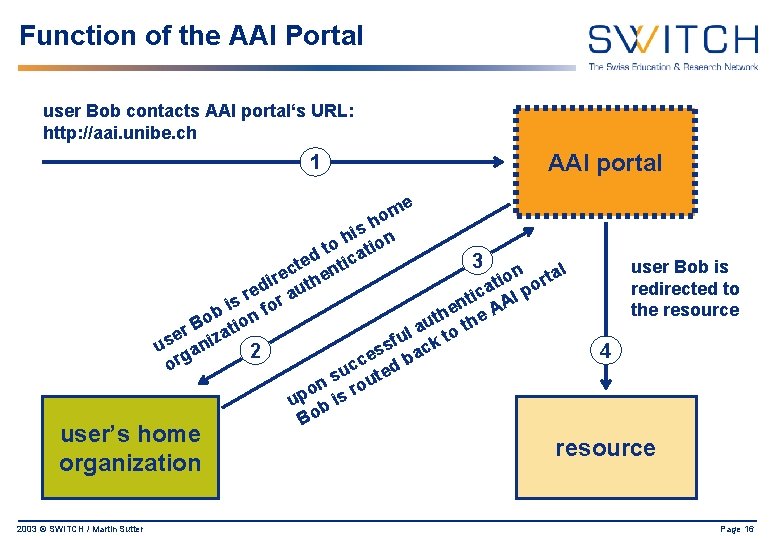
Function of the AAI Portal user Bob contacts AAI portal‘s URL: http: //aai. unibe. ch 1 AAI portal me o h s i o h ation t d tic 3 e t c n n rtal e he o r i i at I po ed aut c r i nt AA is for e b th the o ion u B a t l er iza to u s f k s u an 2 es bac g r c o uc ted s n rou o up b is Bo user’s home organization 2003 © SWITCH / Martin Sutter user Bob is redirected to the resource 4 resource Page 16

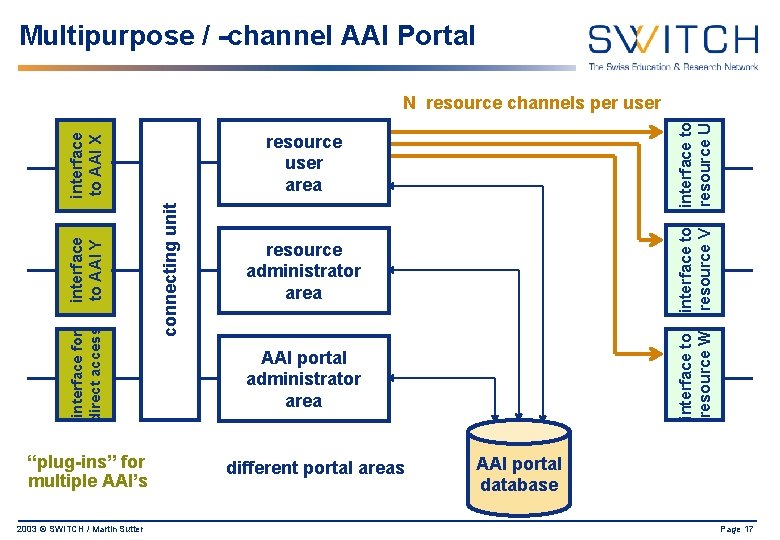
Multipurpose / -channel AAI Portal 2003 © SWITCH / Martin Sutter resource administrator area interface to resource W connecting unit interface to resource V resource user area interface to AAI X interface to AAI Y interface for direct access “plug-ins” for multiple AAI’s interface to resource U N resource channels per user AAI portal administrator area different portal areas AAI portal database Page 17

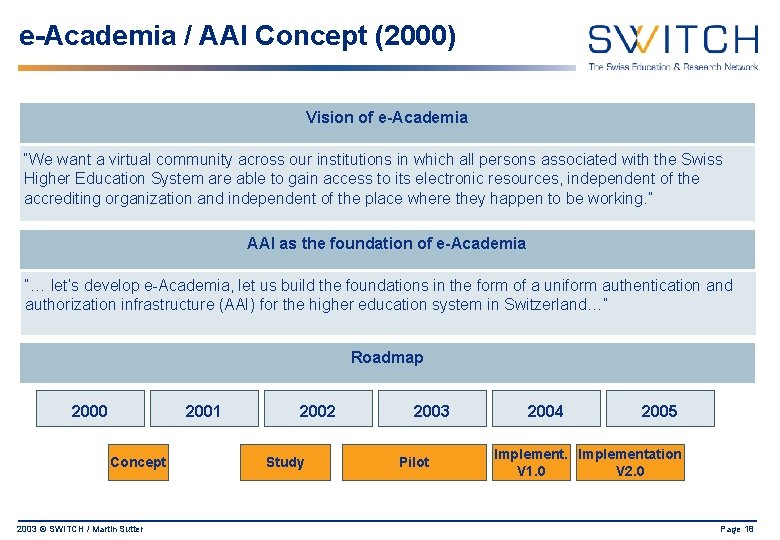
e-Academia / AAI Concept (2000) Vision of e-Academia “We want a virtual community across our institutions in which all persons associated with the Swiss Higher Education System are able to gain access to its electronic resources, independent of the accrediting organization and independent of the place where they happen to be working. ” AAI as the foundation of e-Academia “… let’s develop e-Academia, let us build the foundations in the form of a uniform authentication and authorization infrastructure (AAI) for the higher education system in Switzerland…” Roadmap 2000 2001 Concept 2003 © SWITCH / Martin Sutter 2002 Study 2003 Pilot 2004 2005 Implementation V 1. 0 V 2. 0 Page 18

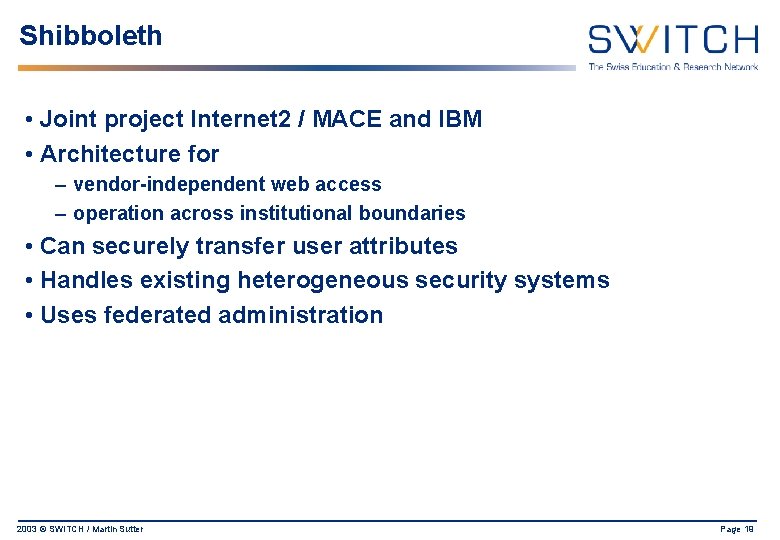
Shibboleth • Joint project Internet 2 / MACE and IBM • Architecture for – vendor-independent web access – operation across institutional boundaries • Can securely transfer user attributes • Handles existing heterogeneous security systems • Uses federated administration 2003 © SWITCH / Martin Sutter Page 19

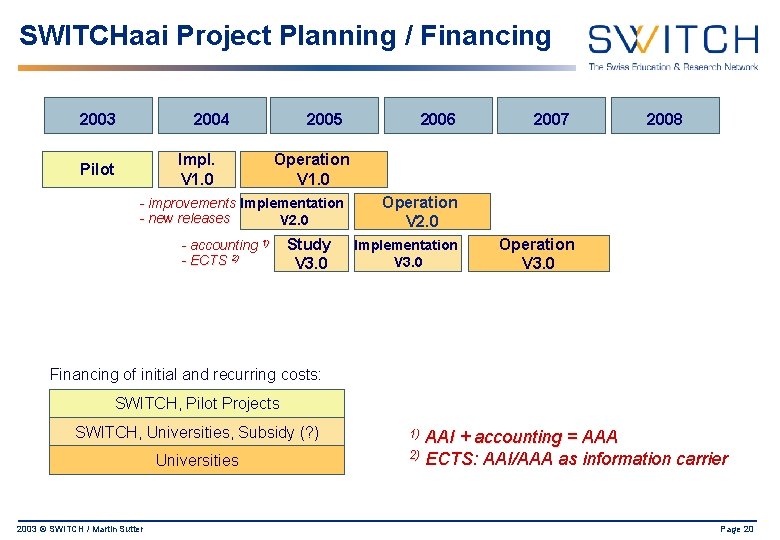
SWITCHaai Project Planning / Financing 2003 2004 Impl. V 1. 0 Pilot 2005 2006 2007 2008 Operation V 1. 0 - improvements Implementation - new releases V 2. 0 - accounting 1) - ECTS 2) Study V 3. 0 Operation V 2. 0 Implementation V 3. 0 Operation V 3. 0 Financing of initial and recurring costs: SWITCH, Pilot Projects SWITCH, Universities, Subsidy (? ) Universities 2003 © SWITCH / Martin Sutter AAI + accounting = AAA 2) ECTS: AAI/AAA as information carrier 1) Page 20

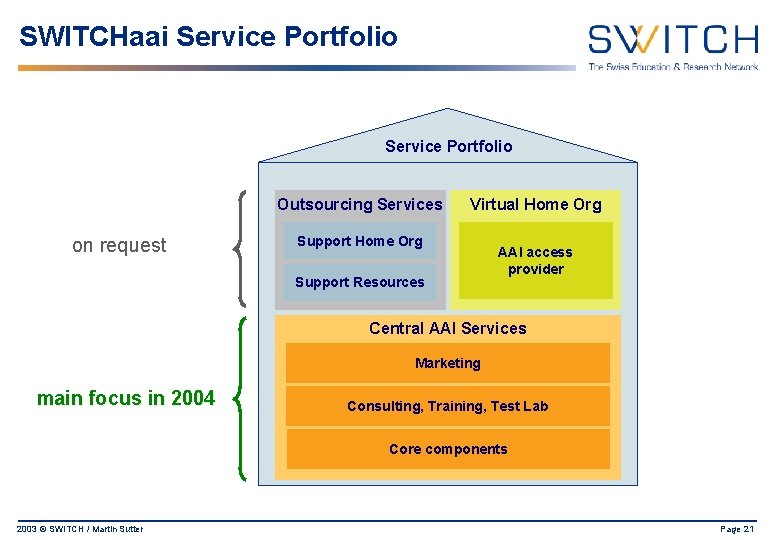
SWITCHaai Service Portfolio Outsourcing Services on request Virtual Home Org Support Resources AAI access provider Central AAI Services Marketing main focus in 2004 Consulting, Training, Test Lab Core components 2003 © SWITCH / Martin Sutter Page 21

Conclusion and Outlook • The AAI for the higher education community in Switzerland is becoming a concrete matter – conceptual questions are solved – prototype projects are running – the infrastructure is being implemented • First results are very promising • For a fully established AAI continuing joint effort is required • In a more distant future the Swiss AAI should be connected to other AAI’s in other countries Q&A 2003 © SWITCH / Martin Sutter Page 22