Computer Security Passwords Authentication vs Authorization Authentication n















- Slides: 18

Computer Security Passwords

Authentication vs. Authorization Authentication n n Proving you are who you say you are Tools: passwords, biometrics Authorization n n Given who you say you are, do you have privilege to do a particular action / affect a particular object? Tools: access control lists, privileges

Password Security/Policy Issues Length Required Characters (Letters, Letters plus Digits plus Special Chars, etc. Prohibited Constructs (e. g. Dictionary Words) User Changeability (Require/Prevent User From Changing) n How often? How password remembered (memory, written, on system, etc. )

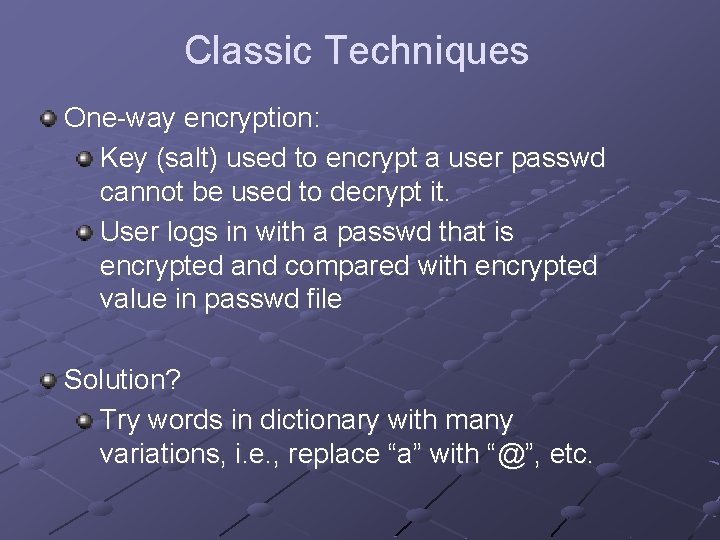
Classic Techniques – Possible but Impractical Try all possible passwords n Difficult, as most systems disconnect after small number of attempts, lock out after more Break the encryption scheme n Difficult with current one-way encryption methods

Classic Techniques One-way encryption: Key (salt) used to encrypt a user passwd cannot be used to decrypt it. User logs in with a passwd that is encrypted and compared with encrypted value in passwd file Solution? Try words in dictionary with many variations, i. e. , replace “a” with “@”, etc.

Classic Techniques – What’s Used Find password file and compare encrypted possible passwords n n Linux - /etc/passwd, world-readable, but passwords encrypted (now shadow password file /etc/shadow, with only system access, often used) Line from shadowed /etc/passwd: zatoichi: x: 2510: : /home/zatoichi: /bin/tcsh n Line from unshadowed /etc/passwd: zatoichi: 3#a. Vu 5 O 1: 2510: : /home/zatoichi: /bin/tcsh

Shadow Passwords • • • “*" token in place of one way encrypted password. Real password is located in a different file, typically called the shadow file. Different tokens used in different shadow password implementations. On many Unix systems, the password file is still located in /etc but called shadow Some systems even place the shadow in a different directory. Examples of location of the shadow, and the token. System Shadow Token AIX /etc/security/passwd * BSD /etc/master. passwd * HP-UX /. secure/etc/passwd * IRIX /etc/shadow x Linux /etc/shadow * SCO /tcb/auth/files/[first letter of username]/[username] * Solaris /etc/shadow * System V < 4. 2 /etc/shadow x System V >= 4. 2 /etc/security/* database x

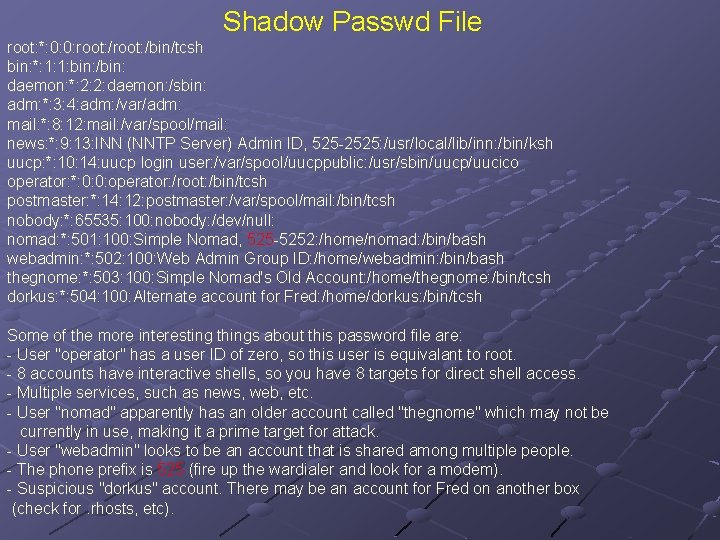
Shadow Passwd File root: *: 0: 0: root: /bin/tcsh bin: *: 1: 1: bin: /bin: daemon: *: 2: 2: daemon: /sbin: adm: *: 3: 4: adm: /var/adm: mail: *: 8: 12: mail: /var/spool/mail: news: *: 9: 13: INN (NNTP Server) Admin ID, 525 -2525: /usr/local/lib/inn: /bin/ksh uucp: *: 10: 14: uucp login user: /var/spool/uucppublic: /usr/sbin/uucp/uucico operator: *: 0: 0: operator: /root: /bin/tcsh postmaster: *: 14: 12: postmaster: /var/spool/mail: /bin/tcsh nobody: *: 65535: 100: nobody: /dev/null: nomad: *: 501: 100: Simple Nomad, 525 -5252: /home/nomad: /bin/bash webadmin: *: 502: 100: Web Admin Group ID: /home/webadmin: /bin/bash thegnome: *: 503: 100: Simple Nomad's Old Account: /home/thegnome: /bin/tcsh dorkus: *: 504: 100: Alternate account for Fred: /home/dorkus: /bin/tcsh Some of the more interesting things about this password file are: - User "operator" has a user ID of zero, so this user is equivalant to root. - 8 accounts have interactive shells, so you have 8 targets for direct shell access. - Multiple services, such as news, web, etc. - User "nomad" apparently has an older account called "thegnome" which may not be currently in use, making it a prime target for attack. - User "webadmin" looks to be an account that is shared among multiple people. - The phone prefix is 525 (fire up the wardialer and look for a modem). - Suspicious "dorkus" account. There may be an account for Fred on another box (check for. rhosts, etc).

Possible Password Sources Regular dictionary Special cracker dictionary n Common phrases, names, bands, slang, etc. Combinations of relevant numbers and constructs from above sources Knowledge about user

Comparison re: Length/Content 6 chars, Letters (52 upper and lower) n n 52^6 = 19. 7 billion possibilities Easier to crack 8 chars, Letters plus Digits plus Special (approximately 82 characters) n n 82^8 = 2 quadrillion possibilities 100, 000 times harder to crack

Enforcing Password Policies - Linux System utilities n n n passwd npasswd (replacement for passwd) File: /etc/login. defs 3 rd party tools

Enforcing Password Policies Windows System – Group Policy Editor n Start/Run: gpedit. msc Computer Configuration Windows Settings Security Settings Account Policies Password Policy n Items to control: keep password history, min and max age, min and max length, complexity requirement, encryption

Password Encryption Techniques and Tools - Linux Crypt – tool for encrypting many passwords under Unix/Linux n Based on DES PAM – Pluggable Authentication Modules n Supports dynamic configuration of authentication for multiple applications

Password Encryption Techniques and Tools - Windows Passwords stored in protected part of registry (SAM file) rdisk command – can back up SAM Can analyze this backup file Other tools can directly access SAM file n E. g. , SAMInside

Defensive Issues Weakest Link Theory n n One weak password on system jeopardizes other users, system Security officer should check all passwords periodically to make sure there aren’t potential problems What to do if find problems? n n Notify users Lock out accounts

Authentication Across The System Many applications need authentication n Directory services Database management systems Web-based applications Goals n n Unified point of authentication Customized authorization Example n http: //www. yale. edu/tp/auth/cas 10. html

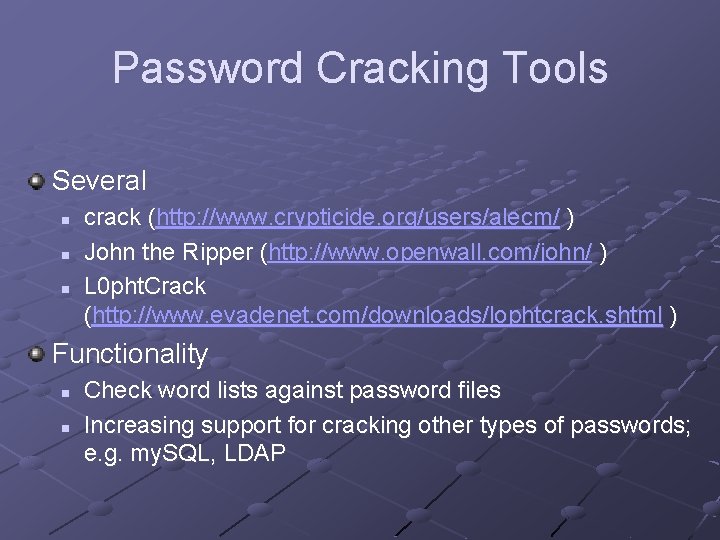
Password Cracking Tools Several n n n crack (http: //www. crypticide. org/users/alecm/ ) John the Ripper (http: //www. openwall. com/john/ ) L 0 pht. Crack (http: //www. evadenet. com/downloads/lophtcrack. shtml ) Functionality n n Check word lists against password files Increasing support for cracking other types of passwords; e. g. my. SQL, LDAP

Account Management Related issue Need to monitor accounts n n If no longer needed, remove them Periodically check for unused accounts, remove them Need policy for abuse of accounts (e. g. not maintaining password secrecy)