PIX Firewall An example of a stateful packet














- Slides: 26

PIX Firewall An example of a stateful packet filter. Can also work on higher layers of protocols (FTP, Real. Audio, etc. ) Runs on its own OS http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt

Outline • • The Adaptive Security Algorithm (ASA) Basic Features of PIX Advanced Features Case studies http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 2

Adaptive Security Algorithm • An algorithm that defines how PIX examines traffic passing through it, and applies various rules to it. Basic concept: • - Keep track of the connections being formed from the networks behind the PIX to the public network Based on info about these connections, ASA allows packets to come back into the private network through the firewall. All other traffic destined for the private network is blocked by the firewall (unless specifically allowed). http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 3

ASA • ASA defines how the state and other information is used to track the sessions passing through the PIX. • ASA keeps track of the following information: – – – Source and destination info of IP packets TCP Sequence numbers and TCP flags UDP packet flow and timers http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 4

ASA and TCP • • TCP is connection-oriented, and provides most of the information the firewall needs. The firewall keeps track of each session being formed, utilized, and terminated. ASA only allows for the packets confirming to the state of a session to go through. All other packets are dropped. However, TCP has inherent weakness, which requires ASA to perform additional work managing the sessions SYN flood, session hijacking http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 5

ASA and TCP • SYN flooding – “The SYN flood attack sends TCP connections requests faster than a machine can process them. ” (Internet Security Systems, http: //www. iss. net/security_center/advice/Exploits/TCP/SYN_flood/default. htm) – SYN flood (as fefined in the Wikipedia, http: //en. wikipedia. org/wiki/SYN_flood) – Illustration: next http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 6

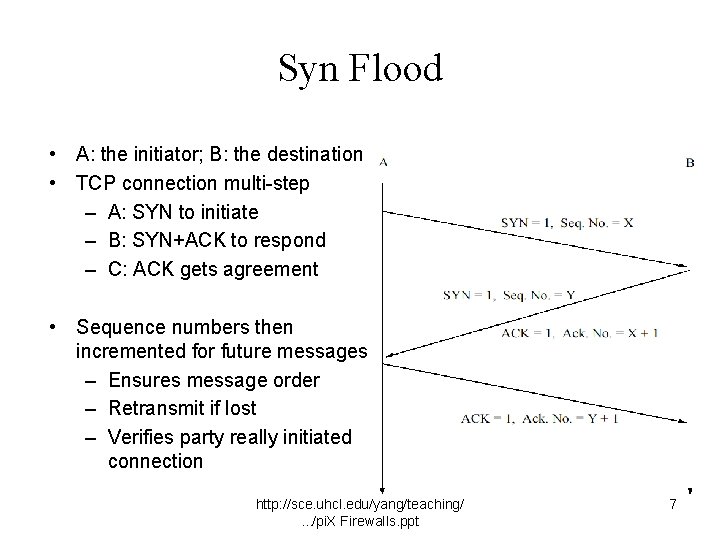
Syn Flood • A: the initiator; B: the destination • TCP connection multi-step – A: SYN to initiate – B: SYN+ACK to respond – C: ACK gets agreement • Sequence numbers then incremented for future messages – Ensures message order – Retransmit if lost – Verifies party really initiated connection http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 7

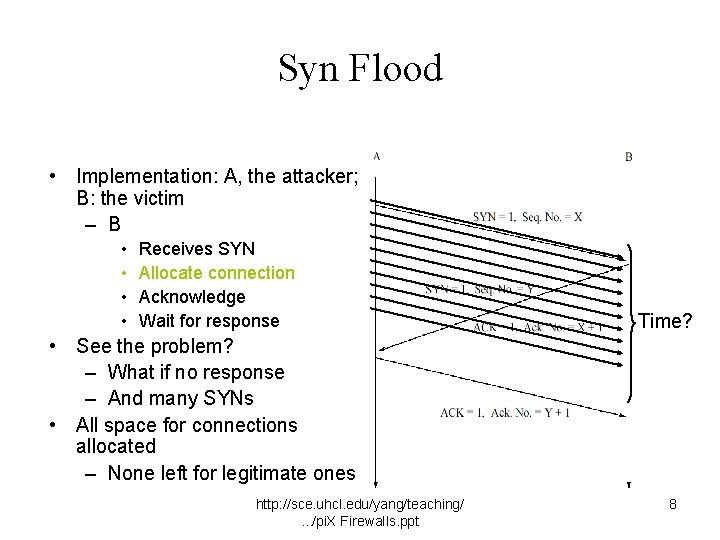
Syn Flood • Implementation: A, the attacker; B: the victim – B • • Receives SYN Allocate connection Acknowledge Wait for response Time? • See the problem? – What if no response – And many SYNs • All space for connections allocated – None left for legitimate ones http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 8

ASA vs Syn Flood • (Beginning in version 5. 2 and later) – When the number of incomplete connections through the PIX reaches a pre-configured limit (the limit on embryonic connections), ASA turns the PIX into a proxy for connection attempts (SYNs) to servers or other resources sitting behind it. • • – PIX responds to SYN requests with SYN ACKs and continues proxying the connection until the three-way TCP handshake is complete. Only when the three-way handshake is complete would the PIX allow the connection through to the server or resource on the private or DMZ network. Benefit: Limits the exposure of the servers behind the PIX to SYN floods http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 9

ASA and TCP • Problem with the ISN: The initial sequence number (ISN) of TCP is not really random! possible TCP session hijacking attack case study: Kevin Metnick’s attack on Tsutomu Shimomura’s computers in 1994 -1995 Six steps (pp. 421 -422): 1. an initial reconnaissance attack: gather info about the victim 2. a SYN flood attack: disable the login server; a DOS attack 3. A reconnaissance attack: determine how one of the x-term generated its TCP sequence numbers 4. Spoof the server’s identity, and establish a session with the x-term (using the sequence number the x-term must have sent) result: a one-way connection to the x-term 5. modify the x-term’s. rhosts file to trust every host 6. Gain root access to the x-term http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 10

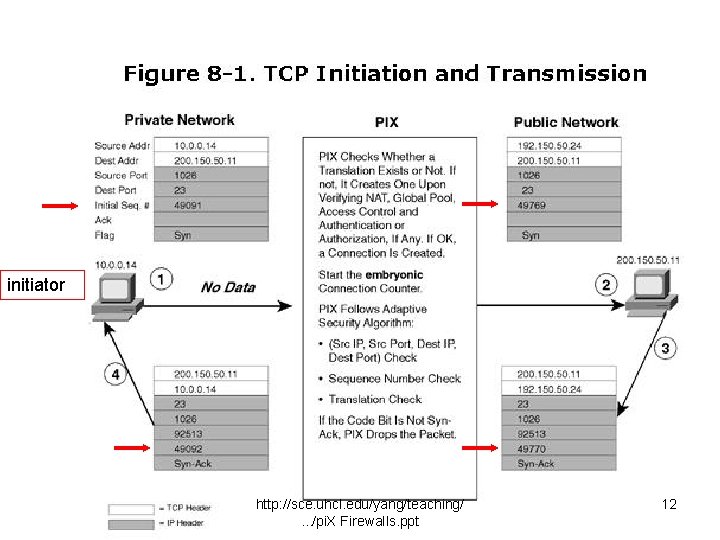
ASA and TCP • TCP session hijacking attack (cont. ) ASA’s solution “proxy” the sequence number in an outgoing packet a. b. create a new, more random sequence number; use the new number as the sequence number in the outgoing packet, and store the difference between the new and the original number; When return traffic for that packet is received, ASA restores the sequence number before forwarding the packet to the destination on the inside network. Illustration: Figures 8 -1 (initialization) and 8 -2 (termination) http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 11

initiator http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 12

PIX: Basic Features • • ASA’s stateful inspection of traffic Assigning varying security levels to interfaces ACL Extensive logging Basic routing capability (including RIP) NAT Failover and redundancy Traffic authentication http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 13

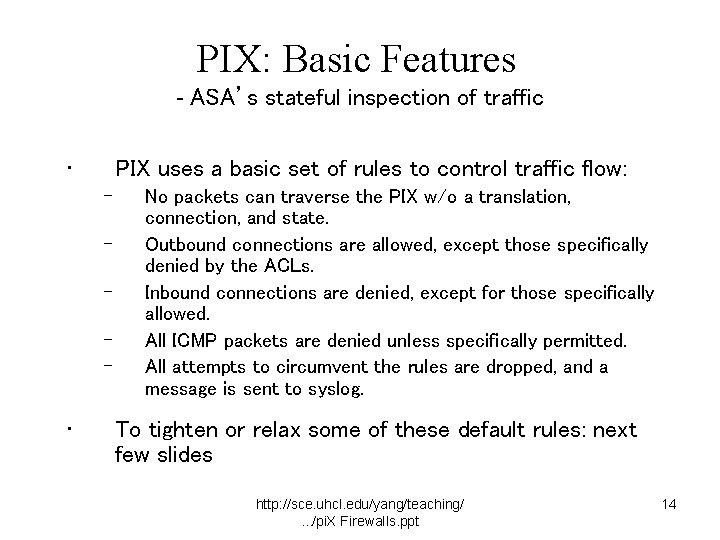
PIX: Basic Features - ASA’s stateful inspection of traffic • PIX uses a basic set of rules to control traffic flow: – – – • No packets can traverse the PIX w/o a translation, connection, and state. Outbound connections are allowed, except those specifically denied by the ACLs. Inbound connections are denied, except for those specifically allowed. All ICMP packets are denied unless specifically permitted. All attempts to circumvent the rules are dropped, and a message is sent to syslog. To tighten or relax some of these default rules: next few slides http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 14

PIX: Basic Features • Assigning varying security levels to interfaces – – PIX allows varying security levels to be assigned to its various interfaces, creating the so called security zones. A PIX may have 2 to 10 interfaces. Each i/f can be assigned a level from 0 (least secure, usually the Internet) to 100 (most secure, usually the internal private network). Default rules: o o Traffic from a higher security zone can enter a lower security zone. PIX keeps track of the connections for this traffic and allows the return traffic through. Traffic from a lower security zone is not allowed to enter a higher security zone, unless explicitly permitted (such as using ACLs). http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 15

PIX: Basic Features • ACL – Mainly used to allow traffic from a less-secure portion of the network to enter a more-secure portion of the network. – Information used in ACLs: Source address Destination address Protocol numbers Port numbers – Examples: To allow connections to be made to web or mail servers sitting on the DMZ of the PIX from the public network To allow a machine on a DMZ network to access the private network behind the DMZ – Use of ACLs must be governed by the network security policy. (Only use them when necessary) http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 16

PIX: Basic Features • Extensive logging – – System logs are sent and recorded in a central location (for example, the syslog server). PIX records the following types of syslog messages: Connection events, AAA events, Failover events, FTP/URL events, Mail Guard/SNMP events, PIX Firewall management events, Routing errors – 8 syslog logging levels: 0 (emergency), 1 (alert), 2 (critical condition), …, 7 (debug message, log FTP command, etc. ) – – – A subset of the syslog messages may be displayed on the PIX console or a Telnet session screen. 3 rd party s/w (e. g. , Private Eye) may be used to generate extensive reporting from the syslog messages. Info in the syslog may be used by PIX to help intrusion detection. http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 17

PIX: Basic Features • Basic routing capability – PIX supports some basic routing, including the use of default routes, static routes, and Routing Information Protocol (RIP) – However, routing functionality in PIX is limited. http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 18

PIX: Basic Features • NAT – – – PIX can perform NAT for packets traversing any two of its interfaces. By default, NAT must be set up for a connection state to be created. Examples: • • – The most common use of NAT is sit between the private network behind the PIX (using an RFC 1918 space) and the Internet translate and keep track of the addresses NAT may also be used between two interfaces on the PIX, neither of which is on the public network. dynamic NAT vs static NAT: next http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 19

PIX: Basic Features • static NAT – • A type of NAT in which a private IP address is mapped to a public IP address, where the public address is always the same IP address (i. e. , it has a static address). This allows an internal host, such as a Web server, to have an unregistered (private) IP address and still be reachable over the Internet. dynamic NAT – • A type of NAT in which a private IP address is mapped to a public IP address drawing from a pool of registered (public) IP addresses. Typically, the NAT router in a network will keep a table of registered IP addresses, and when a private IP address requests access to the Internet, the router chooses an IP address from the table that is not at the time being used by another private IP address. Configuring NAT in PIX: http: //www. cisco. com/warp/public/556/9. html – With dynamic NAT, translations do not exist in the NAT table until the router receives traffic that requires translation. Dynamic translations have a timeout period after which they are purged from the translation table. – With static NAT, translations exist in the NAT translation table as soon as you configure static NAT command(s), and they remain in the translation table until you delete the static NAT command(s). http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 20

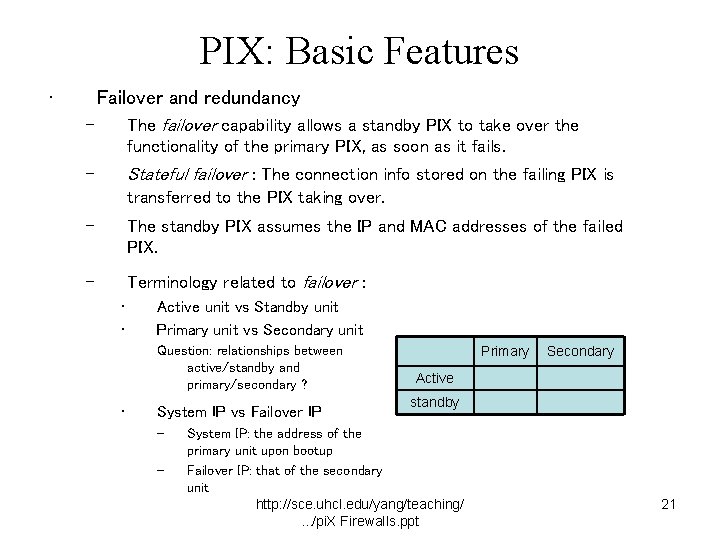
PIX: Basic Features • Failover and redundancy – The failover capability allows a standby PIX to take over the functionality of the primary PIX, as soon as it fails. Stateful failover : The connection info stored on the failing PIX is – transferred to the PIX taking over. – The standby PIX assumes the IP and MAC addresses of the failed PIX. – Terminology related to failover : • • Active unit vs Standby unit Primary unit vs Secondary unit Question: relationships between active/standby and primary/secondary ? • System IP vs Failover IP – – Primary Secondary Active standby System IP: the address of the primary unit upon bootup Failover IP: that of the secondary unit http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 21

PIX: Basic Features - Failover and redundancy How does failover work? • – – A failover cable (RS-232 serial) connects the primary unit and the secondary unit, allowing the secondary unit to detect the primary unit’s power status, and failover communication in between. (In the case of stateful failover) The state info is transferred via an Ethernet cable connecting the primary unit and the secondary unit. Every 15 seconds, special failover hello packets are sent in between the two units for synchronization. Requirements: The h/w, s/w, and configurations on the two PIXes must be identical. http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 22

PIX: Basic Features - Failover and redundancy Limitations of CISCO PIX failover ? • – Some info are not replicated between the two units: • • – User authentication table ISAKMP and IPsec SA table ARP table Routing info The secondary unit must rebuild the info to perform the functions of the failed unit. http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 23

PIX: Basic Features • Traffic authentication on PIX: Cut-through proxy authentication – • • • – Only when the authentication occurring during the establishment of a given connection succeeds would PIX allows the data flow to be established through it. A successfully authenticated connection is entered the ASA as a valid state. As soon as an authenticated connection is established, PIX lets the rest of the packets belong to that connection go through without further authentication. PIX supports both TACACS+ and Radius as the AAA servers. http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 24

Advanced Features of PIX • Aliasing – – • x Guards – • • NAT on the destination addresses “DNS doctoring (modification)” of a DNS server’s address flood guard, frag guard, mail guard, & DNS guard Advanced filtering Multimedia support Spoof detection (via URPF) Protocol fixup sysopt commands Multicast support Fragment handling http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 25

Case studies • • • PIX with 3 interfaces, running a web server on the DMZ PIX setup for failover to a secondary device PIX setup to use the alias command for a server sitting on the DMZ (a case of NAT on the destination address) PIX setup for cut-through proxy authentication and authorization Scaling PIX configurations using object groups and turbo ACLs http: //sce. uhcl. edu/yang/teaching/. . . /pi. X Firewalls. ppt 26