Open Source Intelligence Offensive Security Open Source Intelligence







![Google/Bing/[Search Engine] • If no pre-existing information is given, start by searching All the Google/Bing/[Search Engine] • If no pre-existing information is given, start by searching All the](https://slidetodoc.com/presentation_image_h2/b1a95953528ac7ffe06bfc234e13c773/image-9.jpg)






- Slides: 20

Open Source Intelligence Offensive Security

Open Source Intelligence • Used to gather data from public sources • Generally very passive • Never touching the target • Public information may reveal a lot about an organization • Sources may not always be true Offensive Security Media, newspapers Business documents, publications Internet… 2

Where does OSINT fit in Penetration Testing/Red Teaming? • Methodologies PTES OWASP OSSTMM NIST SP 800 -115 Output of OSINT is input to the next step Threat modeling/vulnerability analysis/exploitation Offensive Security • 3

Why OSINT? • One of the most important parts of an assessment Foundational work Helps to build plan of attack Social Engineering Useful information using during assessment OSINT information in a report is value added Offensive Security • 4

Targets of OSINT • Based on scope and goals of test • Different end goals might require different intel • Creating plan of attack based on this information Offensive Security Business User Network 5

Types of Information – Business • Organizational Information Who they are What they do Relationships with other companies Comes in the form of Physical location, Size, Partners, Records, Organization structure Product Information, Patents Technology in use, Employees Job openings Affiliations Public document metadata Org Chart Offensive Security • 6

Types of Information – User • Employee Information • Who they are • What they do • Organizational chart • Username/password • Job/Role, Previous Jobs • Email addresses Offensive Security Found in various places 7

Types of Information – Network • Addressing Flat network vs Separated • Technologies • Remote access • Defenses Network based Host based Offensive Security VPN Email 8
![GoogleBingSearch Engine If no preexisting information is given start by searching All the Google/Bing/[Search Engine] • If no pre-existing information is given, start by searching All the](https://slidetodoc.com/presentation_image_h2/b1a95953528ac7ffe06bfc234e13c773/image-9.jpg)
Google/Bing/[Search Engine] • If no pre-existing information is given, start by searching All the information mentioned previously Search operators Intitle: Type: Site: Info: Loc: Offensive Security • 9

Google Cache/Wayback Machine Services caching data on the internet Offensive Security • 10

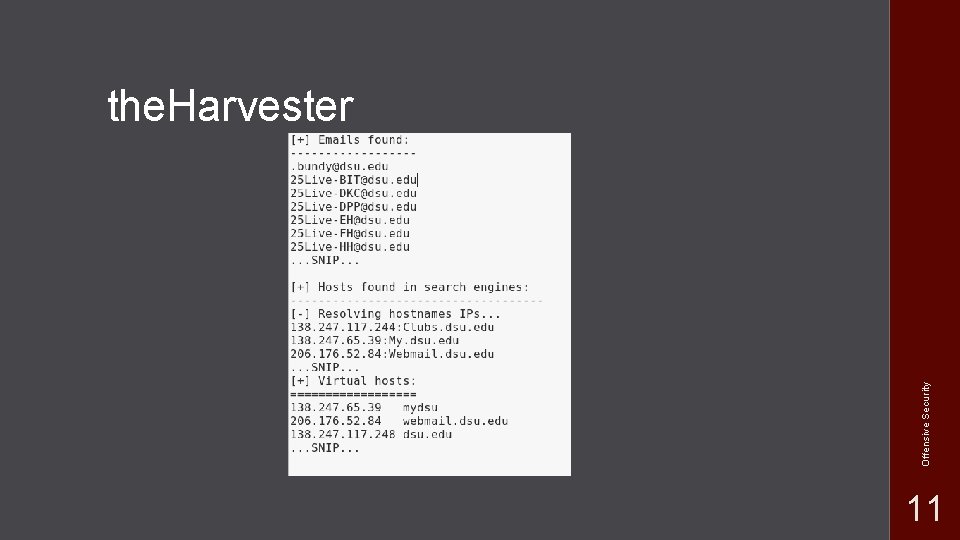
Offensive Security the. Harvester 11

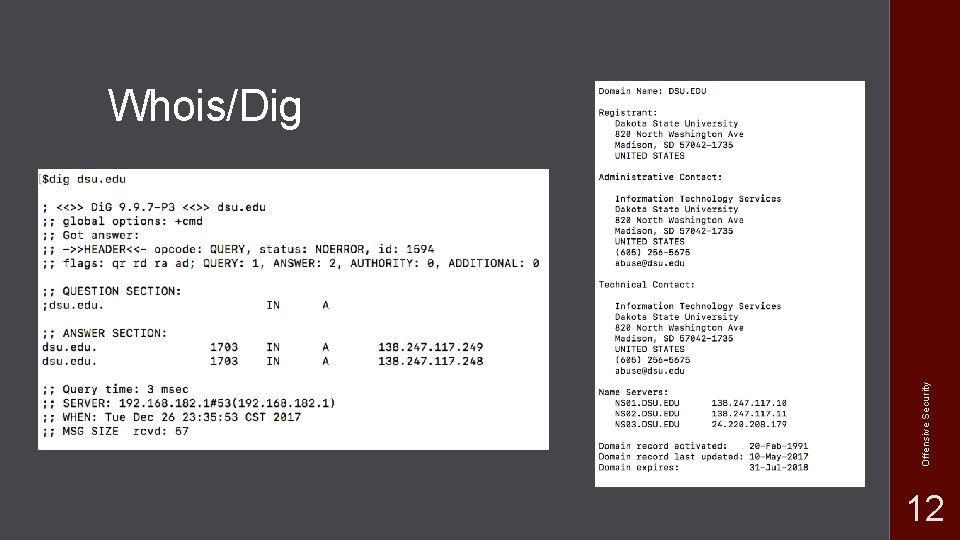
Offensive Security Whois/Dig 12

Offensive Security DNS 13

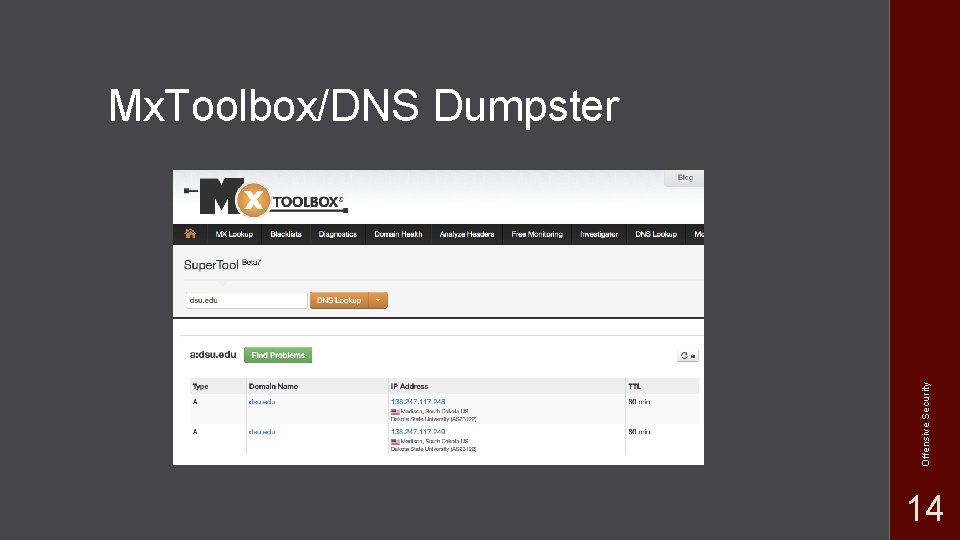
Offensive Security Mx. Toolbox/DNS Dumpster 14

• https: //github. com/leebaird/discover • Recon • Scanning • Web • Misc Offensive Security Discover Scripts 15

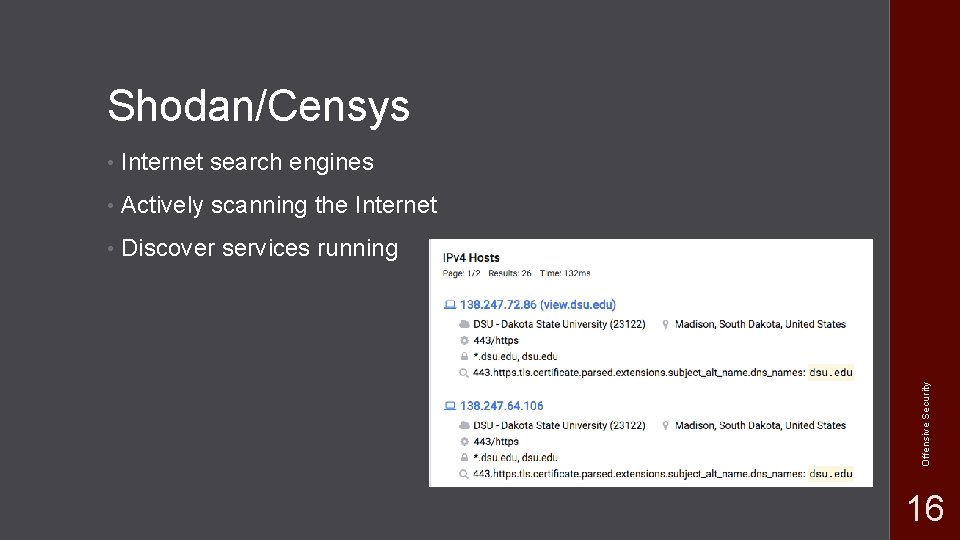
• Internet search engines • Actively scanning the Internet • Discover services running Offensive Security Shodan/Censys 16

Employee Information • Setting the stage for phishing • Knowing about them gives information about an organization • Social Media • Other Search Engines Offensive Security Spokeo 17

• Linked. In • Facebook • Twitter • Etc. Offensive Security Social Media 18

Offensive Security Recon-ng Demo 19

• OSINT Framework • Metagoofil • Maltego • Etc… Offensive Security Other Tools 20