MSP 432 MCUs Training Part 7 Security AES



- Slides: 8

MSP 432™ MCUs Training Part 7: Security AES 256 JTAG/SWD Lock IP Protection Firmware Update 1

Security | AES 256 Benefits Applications include Securing of communication channels like RF • Hardware acceleration for AES (Advanced Encryption Standard – links, UART communications, etc. FIPS PUB 197) • Accelerates AES en- and decryption by one to two orders of magnitude (compared to software) • Lower power (compared to software) • Off-loads CPU Performance • 128 -bit of data are en- or decrypted with a 128 -bit key within 167 MCLK cycles, 256 bit encryption in 234 cycles Features • supporting 128 -, 192 -, and 256 -bit key lengths • On-the-fly key expansion • Off-line key generation for decryption • Shadow registers for initial key • 128 bit truly random seed to generate the random key • Block mode with DMA: OFB, ECB, etc. 2

Security | Device Security Overview • Full chip security: JTAG Protection – Device is fully secure from debug accesses. • Regional security: IP Protection – Up to 4 regional secure zones of memories can be configured in flash – These zones are non-intrusive to debug (JTAG/debugger) and code outside this region. – Regular debug allowed outside these regional secure zones. • Combination of regional and full-chip security – This is a combination of the above two where: • Debug accesses are blocked for the entire device • Code/Data access restrictions and protections apply for the secure regions. 3

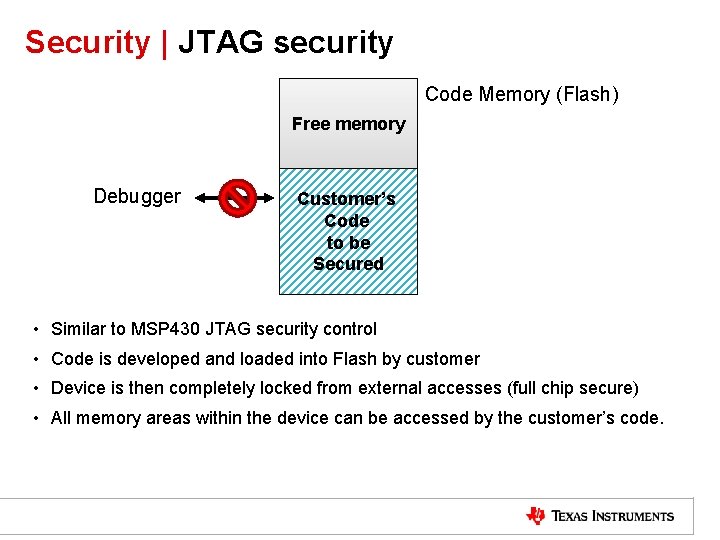
Security | JTAG security Code Memory (Flash) Free memory Debugger Customer’s Code to be Secured • Similar to MSP 430 JTAG security control • Code is developed and loaded into Flash by customer • Device is then completely locked from external accesses (full chip secure) • All memory areas within the device can be accessed by the customer’s code.

Security | IP Protection • Configure up to 4 regionally secured zones to protect IP from read/write access • Facilitate securing protected IP code from vendors • Prevent access during IP code execution by stalling JTAG until end of code execution • Regionally secured zones can be updated via BSL • Ease of use: Use CCS & other IDEs to configure and secure zones 5

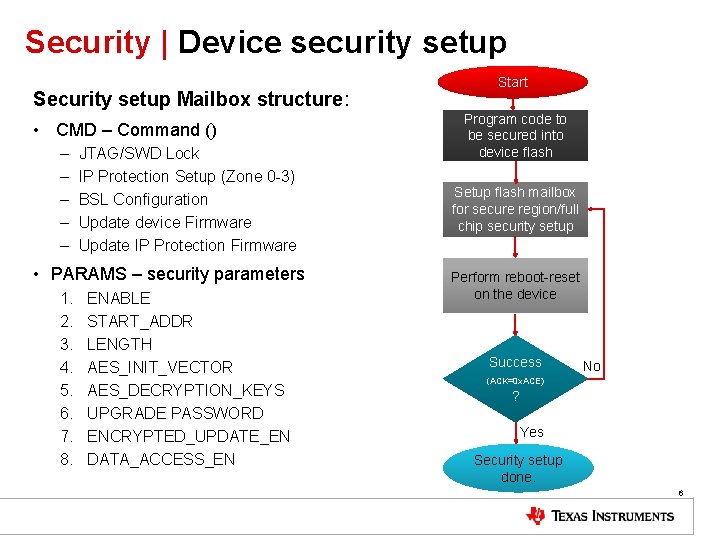
Security | Device security setup Security setup Mailbox structure: • CMD – Command () – – – JTAG/SWD Lock IP Protection Setup (Zone 0 -3) BSL Configuration Update device Firmware Update IP Protection Firmware • PARAMS – security parameters 1. 2. 3. 4. 5. 6. 7. 8. ENABLE START_ADDR LENGTH AES_INIT_VECTOR AES_DECRYPTION_KEYS UPGRADE PASSWORD ENCRYPTED_UPDATE_EN DATA_ACCESS_EN Start Program code to be secured into device flash Setup flash mailbox for secure region/full chip security setup Perform reboot-reset on the device Success No (ACK=0 x. ACE) ? Yes Security setup done. 6

Security | Device firmware update • Password-protected BSL can be used to update a device’s firmware • When locking JTAG/SWD, option to provide an encryption key – Key is only shared at the time of initial firmware programming – During field-update, BSL payload can be encrypted with the same key – Invoke boot override to decrypt the payload and program the new firmware • IP Protection also requires an encryption key – Key is only shared at the time of IP protected zone programming – BSL payload is encrypted with the same key – No-one other than original IP provide has access to the key 7

Security | More Resources Application Notes & SW examples • Software IP Protection • Configuring Security features Available in MSPWare 8