ITEC 810 Project Unit Trustworthy Sensor Networks Daniel



- Slides: 15

ITEC 810 – Project Unit Trustworthy Sensor Networks Daniel Aegerter, 41542053 Supervisor: Rajan Shankaran

Agenda t Problem Statement t Wireless Sensor Networks t Notion of Trust in Wireless Sensor Networks t Comparative Analysis t Recommendations 1

Problem t Security is critical in many applications of Wireless Sensor Networks (WSNs) Battlefield surveillance — Patient monitoring — Environment monitoring — t Security mechanisms assume trustworthiness of participating nodes t What happens if nodes get compromised? Access key material — Change content of messages — Drop messages — t Lives and livelihoods might depend on the correctness of the data 2

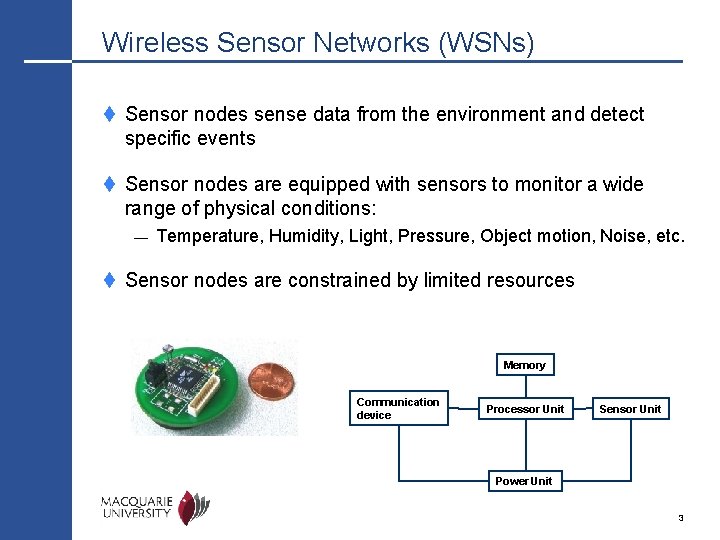
Wireless Sensor Networks (WSNs) t Sensor nodes sense data from the environment and detect specific events t Sensor nodes are equipped with sensors to monitor a wide range of physical conditions: — Temperature, Humidity, Light, Pressure, Object motion, Noise, etc. t Sensor nodes are constrained by limited resources Memory Communication device Processor Unit Sensor Unit Power Unit 3

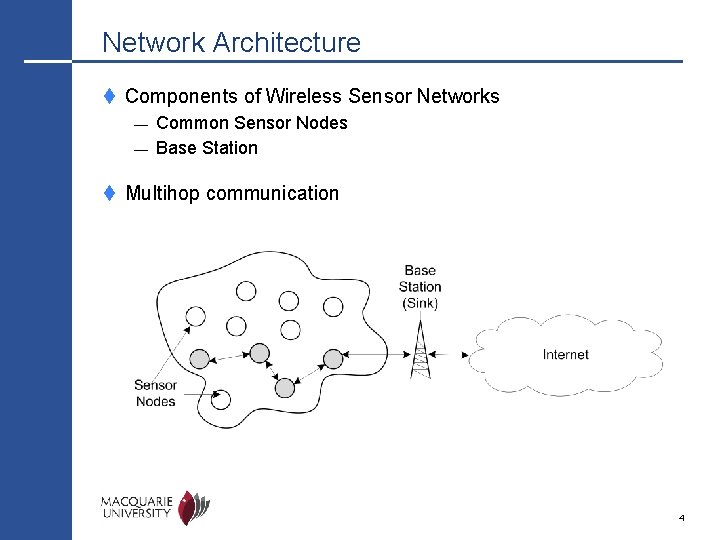
Network Architecture t Components of Wireless Sensor Networks — — Common Sensor Nodes Base Station t Multihop communication 4

Notion of Trust t “Trust is the subjective probability by which an individual, A, expects that another individual, B, performs a given action on which its welfare depends” (Gambetta, 1988) In the context of WSNs t Trustworthy sensor nodes don’t: Manipulate gathered information — Alter information received from neighbouring nodes — Flood the network with bogus routing information — Drop messages received from other nodes — 5

Challenges in Evaluating Trust for WSNs t Limited processing, storage, and energy resources Existing protocols and mechanisms are not applicable — Minimise communication overhead — t Trusted authority not present in WSNs — Public key mechanisms and certificates not suitable t Adoption of architectural network changes Dynamic nature of WSNs — Nodes may become faulty or compromised Trust re-evaluation is essential — 6

Concept of Reputation-Based Trust Systems t Trust is based on a node’s behaviour Does the node behave in a correct manner? — Network events and correctness of gathered information — t Trust evaluation through first and second-hand information Direct observations — Recommendations from peers — t Building blocks Watchdog mechanism collects evidence — Reputation system evaluates and maintains trust — 7

Comparative Analysis t Compares five reviewed reputation-based frameworks 1. 2. 3. 4. 5. Reputation-based framework for high integrity sensor network (RFSN) Gaussian trust model and reputation system (GRSSN) Lightweight group based trust management scheme (GTMS) Trust-based cluster head election Certificate and behaviour-based approach t Determines characteristics and constraints of each framework t Proposes categories to conduct the comparative analysis Trust management — Node and network requirement — Trust evaluation — 8

Comparative Analysis – Some Criteria t Evidence — Network events vs. correctness of sensed data t Pre-established trust relationships — Do sensor nodes trust each other at time of deployment? t Storage complexity — Tables, keys, certificates t Revocation — What happens with non-cooperative sensor nodes? 9

Comparative Analysis – Outcomes t All frameworks have some design problems — Difficult to take all characteristics and constraints of WSNs into account t Frameworks are application specific Different assumptions — Different requirements (e. g. supernodes, keys, certificates) — t Sophisticated frameworks are more complex Economical issues — Management issues — t Evidence analysis — Network events or also correctness of sensed data? 10

Recommendations t Collaborative reputation-based approach for establishing trust t Behaviour of nodes is observed by a subset of sensor nodes Other nodes do not have to monitor network events — Guardian nodes — t Guardian nodes evaluate collaborative trustworthiness of nodes All sensor nodes are directly observable by guardian nodes — Guardian node evaluate whether a node is cooperative — Opinions are shared among guardian nodes — t Blacklist entry has to be confirmed by other guardians — Sensor node keep list with non-cooperative nodes 11

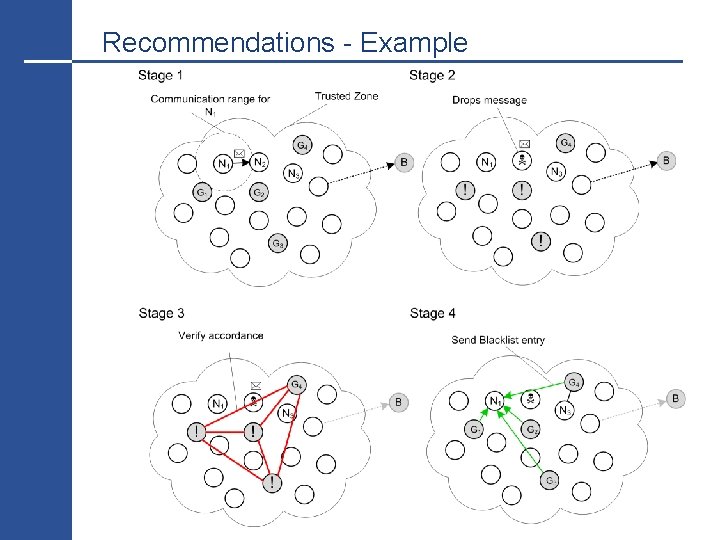
Recommendations - Example 12

Future Research Directions t Analyse correctness of sensed data not only network events t Trust evaluation for different roles that sensor node can perform Forward messages — Aggregate data — Sense information — Thank you 13

Questions 14