Internet Worms Reality or Hype Literature Review and



![The ‘Simple’ Epidemic Model • Model assumptions [SPW 02, Bai 75]: – Homogenous population The ‘Simple’ Epidemic Model • Model assumptions [SPW 02, Bai 75]: – Homogenous population](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-7.jpg)
![Does Code Red Fit the ‘Simple’ Model? • Staniford at el. [SPW 02]: – Does Code Red Fit the ‘Simple’ Model? • Staniford at el. [SPW 02]: –](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-8.jpg)
![‘Advance’ Epidemic Model • Model assumptions [Bai 75]: – Homogenous population – Immunization: infected ‘Advance’ Epidemic Model • Model assumptions [Bai 75]: – Homogenous population – Immunization: infected](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-9.jpg)
![Do Worms Fit the ‘Advance’ Model? • • • Satorras at el. [SV 01] Do Worms Fit the ‘Advance’ Model? • • • Satorras at el. [SV 01]](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-10.jpg)
![‘Advance + Topology’ Model [SV 01] • Epidemic models do not account for the ‘Advance + Topology’ Model [SV 01] • Epidemic models do not account for the](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-11.jpg)
![‘Sophisticated’ Epidemic Model • Zou at el. [ZGT 02] objects Staniford at el. [SPW ‘Sophisticated’ Epidemic Model • Zou at el. [ZGT 02] objects Staniford at el. [SPW](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-15.jpg)

![Short Start-Up Time [SPW 01] Technique Hit List scanning (HL) Permutation scanning (PS) Warhol Short Start-Up Time [SPW 01] Technique Hit List scanning (HL) Permutation scanning (PS) Warhol](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-20.jpg)

![‘Good Guy’ Advantages • Easier to patch system than implementing a new worm [CIPART] ‘Good Guy’ Advantages • Easier to patch system than implementing a new worm [CIPART]](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-23.jpg)
![Bibliography [SPW 02] Stuart Staniford, Vern Paxson, and Nicholas Weaver. "How to 0 wn Bibliography [SPW 02] Stuart Staniford, Vern Paxson, and Nicholas Weaver. "How to 0 wn](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-28.jpg)
- Slides: 28

Internet Worms: Reality or Hype Literature Review and Comments Shai Rubin UW Madison 10/2/2020 Security Seminar Fall 2002 1

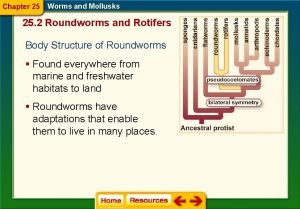
Overview • Background: – What a worm is – How a worm works • • 3 behavioral models Threat from future worms Defending against worms (Wild and Crazy) Summary 10/2/2020 Security Seminar Fall 2002 2

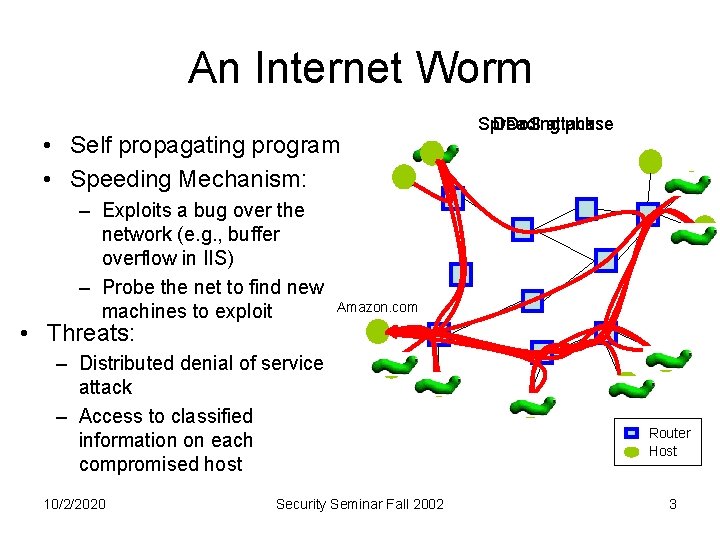
An Internet Worm • Self propagating program • Speeding Mechanism: – Exploits a bug over the network (e. g. , buffer overflow in IIS) – Probe the net to find new machines to exploit Spreading phase DDo. S attack Amazon. com • Threats: – Distributed denial of service attack – Access to classified information on each compromised host 10/2/2020 Security Seminar Fall 2002 Router Host 3

Code Red II • Vulnerability: buffer overflow Microsoft IIS. Code Red II Behavior [DM 02] – Vulnerability published: 19 June, 2001 • Started Spreading 19 July, 2001 • 360, 000 hosts infected in 24 hours (demo) • Damage: $1. 2 billion [USA 01] 10/2/2020 Security Seminar Fall 2002 4

Overview • Background: – What a worm is – How a worm works • Worm behavioral models: – – Why analytical models? Simple Advance Sophisticated • Threat from future worms • Defending against worms • Summary 10/2/2020 Security Seminar Fall 2002 5

Modeling Worm Behavior • Why analytical model? – In general, analytical model cheaper than simulation – Help us understand better: • Parameters that influence behavior – Use the model to explore future worm behavior – Use model define the properties of defense techniques • Starting point: human epidemic – Many similarities: infection, immunization, viruses, etc. 10/2/2020 Security Seminar Fall 2002 6
![The Simple Epidemic Model Model assumptions SPW 02 Bai 75 Homogenous population The ‘Simple’ Epidemic Model • Model assumptions [SPW 02, Bai 75]: – Homogenous population](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-7.jpg)
The ‘Simple’ Epidemic Model • Model assumptions [SPW 02, Bai 75]: – Homogenous population (each node has ~k neighbors) – no immunization – Two parameters: • n – Total population size = # of susceptible hosts • - Infection rate • Number of infected individuals: • Known as Logistic Equation 10/2/2020 Security Seminar Fall 2002 7
![Does Code Red Fit the Simple Model Staniford at el SPW 02 Does Code Red Fit the ‘Simple’ Model? • Staniford at el. [SPW 02]: –](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-8.jpg)
Does Code Red Fit the ‘Simple’ Model? • Staniford at el. [SPW 02]: – = 1. 8 – We are done • Are we really done? – A match does not entail that the model is ‘correct’ – Check other viruses/worms – Weak model assumptions (homogenous population, no immunization) – ‘Unnatural’ Code Red behavior 10/2/2020 Security Seminar Fall 2002 8
![Advance Epidemic Model Model assumptions Bai 75 Homogenous population Immunization infected ‘Advance’ Epidemic Model • Model assumptions [Bai 75]: – Homogenous population – Immunization: infected](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-9.jpg)
‘Advance’ Epidemic Model • Model assumptions [Bai 75]: – Homogenous population – Immunization: infected individuals are removed from population – Three basic parameters: • n - Total population size = # of susceptible hosts • - Infection rate = / =effective infection rate • - Removal rate • No analytical solution 1 (unlike the logistic equation for the ‘simple’ model) • Epidemic Threshold exist: – When the total number of susceptible individuals drops blow a certain threshold the epidemic ‘dies’ 10/2/2020 1 As far as I know, based on [Bai 75] Security Seminar Fall 2002 9
![Do Worms Fit the Advance Model Satorras at el SV 01 Do Worms Fit the ‘Advance’ Model? • • • Satorras at el. [SV 01]](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-10.jpg)
Do Worms Fit the ‘Advance’ Model? • • • Satorras at el. [SV 01] : No Investigate three viruses types. Why not? because computer viruses do not die. 1. Computer viruses have long lifetime (months) 2. This implies, for all computer viruses: effective spreading rate is just above the epidemic threshold 3. ‘ 2’ is very unlikely to occur • How, we can better explain this observation? 10/2/2020 Security Seminar Fall 2002 10
![Advance Topology Model SV 01 Epidemic models do not account for the ‘Advance + Topology’ Model [SV 01] • Epidemic models do not account for the](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-11.jpg)
‘Advance + Topology’ Model [SV 01] • Epidemic models do not account for the scale free topology of the Internet • Model assumptions: Scale Free Topology – Scale free topology: - P[n has K neighbors]=K (2 3) – As in the ‘advance’ model: three parameters: n, , • Intuition: individuals with higher connectivity has higher spreading rate 10/2/2020 Security Seminar Fall 2002 11

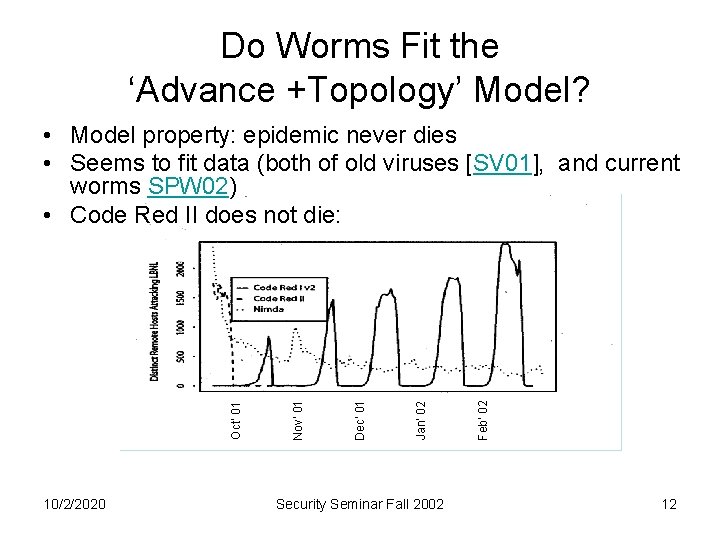
Do Worms Fit the ‘Advance +Topology’ Model? 10/2/2020 Security Seminar Fall 2002 Feb’ 02 Jan’ 02 Dec’ 01 Nov’ 01 Oct’ 01 • Model property: epidemic never dies • Seems to fit data (both of old viruses [SV 01], and current worms SPW 02) • Code Red II does not die: 12

The But of ‘Advance + Topology’ • Is the assumption (scale free topology) valid? – Viruses/worms attack ‘end’ machines (servers/hosts) – Routers are the ‘highly connected’ individuals, but they are not susceptible (usually) – Hence, we should consider a fully connected graph of susceptible individuals 10/2/2020 Security Seminar Fall 2002 13

Current Models Summary Topology Infection/ Removal rate Analytical solution Evidence that fits data 10/2/2020 Simple Advanced + Topology K-connected Scale Free Constant infection rate (no removal rate) Constant Rates Yes Approximation Yes Security Seminar Fall 2002 14
![Sophisticated Epidemic Model Zou at el ZGT 02 objects Staniford at el SPW ‘Sophisticated’ Epidemic Model • Zou at el. [ZGT 02] objects Staniford at el. [SPW](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-15.jpg)
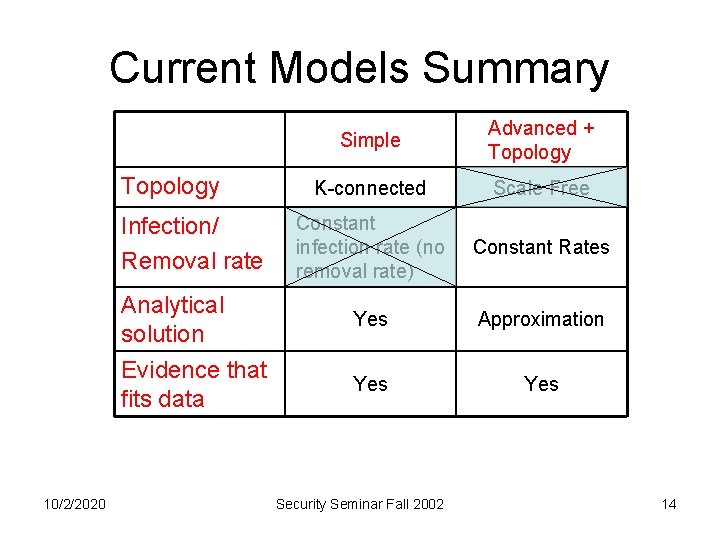
‘Sophisticated’ Epidemic Model • Zou at el. [ZGT 02] objects Staniford at el. [SPW 02]: – No removal process – Model was artificially fitted. Code Red II artificially stopped spreading after 24 hours – Furthermore, infection/removal rate not constant. Real population: 490, 000 • Infection rate decreased (due to high network traffic) • Removal rate increased 10/2/2020 Security Seminar Fall 2002 15

‘Sophisticated’ Epidemic Model So, which parameters should we take into account? 10/2/2020 Security Seminar Fall 2002 16

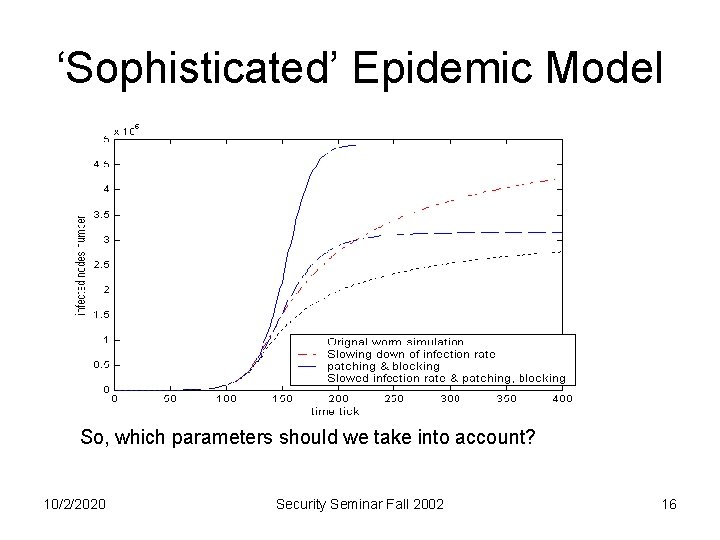
Models Summary Topology Infection/ Removal rate Limitations Analytical solution Evidence that fits data Common 10/2/2020 Simple Advanced + Topology Sophisticated K-connected Scale Free K-Connected Constant infection rate (no removal rate) Constant Rates Time dependent rates Naive Questionable topology Complex Yes Approximation No? Yes Highly virulence Security Seminar Fall 2002 17

Overview • Background: – What a worm is – How a worm works • Worm behavior models: – Simple – Advance – Sophisticated • Threat from future worms • Defending against worms – The defender advantage – Defense techniques • Summary 10/2/2020 Security Seminar Fall 2002 18

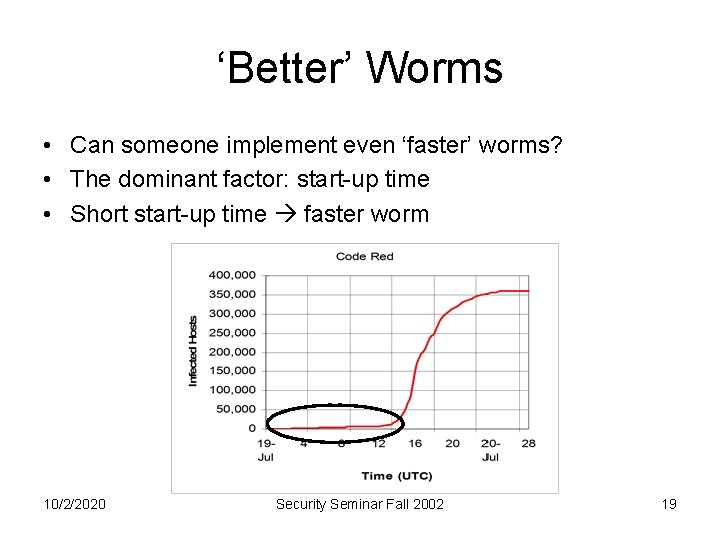
‘Better’ Worms • Can someone implement even ‘faster’ worms? • The dominant factor: start-up time • Short start-up time faster worm 10/2/2020 Security Seminar Fall 2002 19
![Short StartUp Time SPW 01 Technique Hit List scanning HL Permutation scanning PS Warhol Short Start-Up Time [SPW 01] Technique Hit List scanning (HL) Permutation scanning (PS) Warhol](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-20.jpg)
Short Start-Up Time [SPW 01] Technique Hit List scanning (HL) Permutation scanning (PS) Warhol (HL+PS) 10/2/2020 Creator prepares a list of potential susceptible machines. Worm splits the list into sub-lists as it propagates. Problem: infection rate drops after list is exhausted. Each copy of the worm scans different range of addresses. Problem: sill long start up time Initially use HL. Continue with PS. Problem: ? ? ? Security Seminar Fall 2002 20

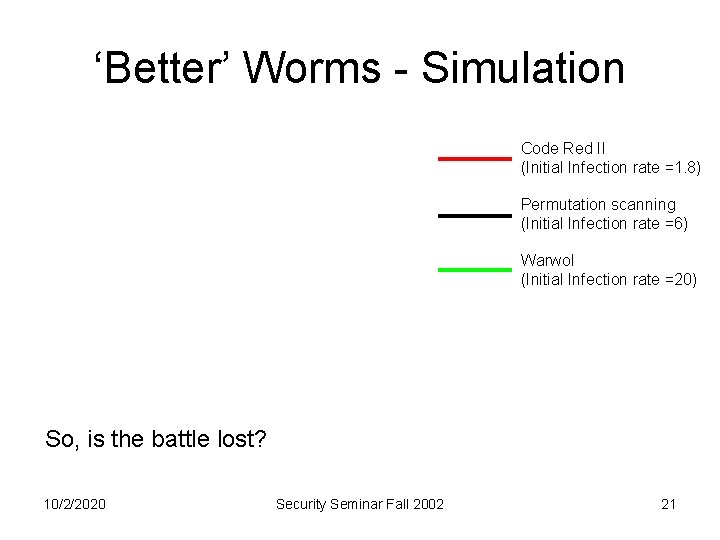
‘Better’ Worms - Simulation Code Red II (Initial Infection rate =1. 8) Permutation scanning (Initial Infection rate =6) Warwol (Initial Infection rate =20) So, is the battle lost? 10/2/2020 Security Seminar Fall 2002 21

Overview • Background: – What a worm is – How a worm works • 3 behavioral models: – Simple – Advance – Sophisticated • Threat from future worms • Defending against worms – ‘Good guy’ advantages – Defense techniques • Summary 10/2/2020 Security Seminar Fall 2002 22
![Good Guy Advantages Easier to patch system than implementing a new worm CIPART ‘Good Guy’ Advantages • Easier to patch system than implementing a new worm [CIPART]](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-23.jpg)
‘Good Guy’ Advantages • Easier to patch system than implementing a new worm [CIPART] • Good guys have more resources – Use resources the identify/fight worms – Diversify resources • Models suggest: easier to slow active worm than making it faster • Other? 10/2/2020 Security Seminar Fall 2002 23

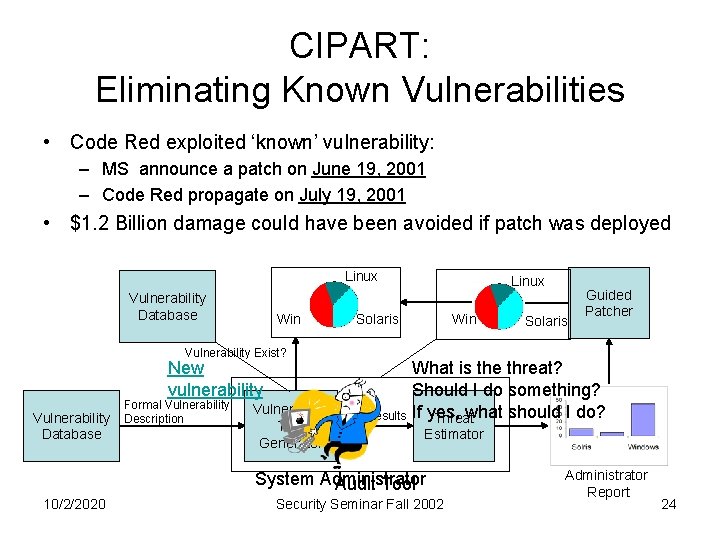
CIPART: Eliminating Known Vulnerabilities • Code Red exploited ‘known’ vulnerability: – MS announce a patch on June 19, 2001 – Code Red propagate on July 19, 2001 • $1. 2 Billion damage could have been avoided if patch was deployed Linux Vulnerability Database Win Solaris Vulnerability Exist? New vulnerability Vulnerability Database Formal Vulnerability Description Vulnerability Test Generator Linux Test results Win What is the threat? Should I do something? If yes, what should I do? Threat Estimator System Administrator Audit Tool 10/2/2020 Solaris Guided Patcher Security Seminar Fall 2002 Administrator Report 24

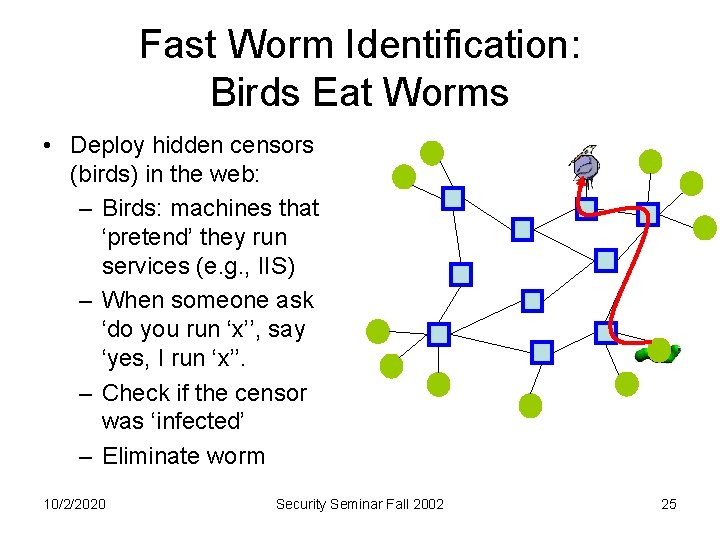
Fast Worm Identification: Birds Eat Worms • Deploy hidden censors (birds) in the web: – Birds: machines that ‘pretend’ they run services (e. g. , IIS) – When someone ask ‘do you run ‘x’’, say ‘yes, I run ‘x’’. – Check if the censor was ‘infected’ – Eliminate worm 10/2/2020 Security Seminar Fall 2002 25

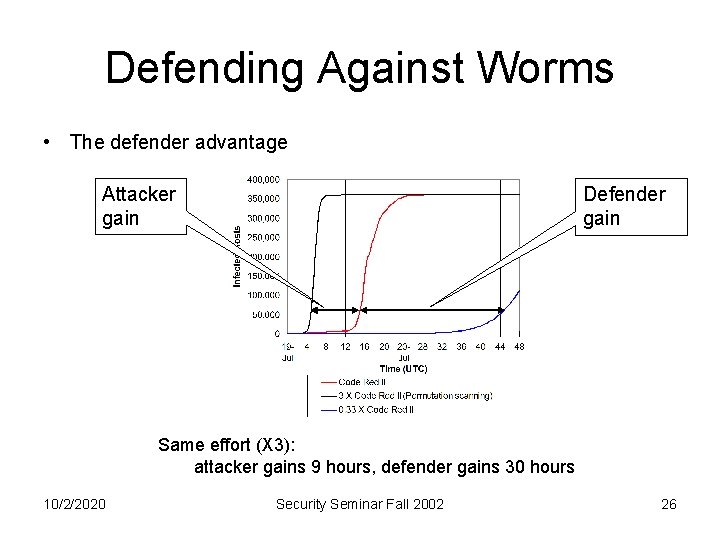
Defending Against Worms • The defender advantage Attacker gain Defender gain Same effort (X 3): attacker gains 9 hours, defender gains 30 hours 10/2/2020 Security Seminar Fall 2002 26

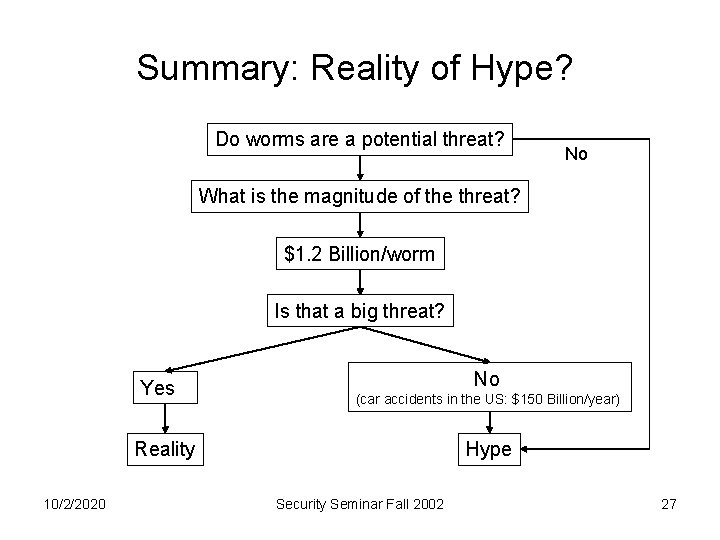
Summary: Reality of Hype? Do worms are a potential threat? No What is the magnitude of the threat? $1. 2 Billion/worm Is that a big threat? Yes No (car accidents in the US: $150 Billion/year) Reality 10/2/2020 Hype Security Seminar Fall 2002 27
![Bibliography SPW 02 Stuart Staniford Vern Paxson and Nicholas Weaver How to 0 wn Bibliography [SPW 02] Stuart Staniford, Vern Paxson, and Nicholas Weaver. "How to 0 wn](https://slidetodoc.com/presentation_image/cd429289cc8377a5af1b8a79ba9868c1/image-28.jpg)
Bibliography [SPW 02] Stuart Staniford, Vern Paxson, and Nicholas Weaver. "How to 0 wn the Internet in Your Spare Time". In the Proceedings of the 11 th USENIX Security Symposium, 2002. [SV 01] Romualdo Pastor-Satorras and Alessandro Vespignani. "Epidemic Spreading in Scale-Free Networks". Physical Review Letters Vol 86(14), 2001. [ZGT 02] Changchun Zou, Weibo Gong, and Don Towsley. "Code Red Worm Propagation Modeling and Analysis". 9 th ACM Conference on Computer and Communications Security, 2002. [DM 02] David Moore. “The Spread of the Code-Red Worm”. Cooperative Association for Internet Data Analysis (CAIDA), http: //www. caida. org/analysis/security/code-red/coderedv 2_analysis. xml, 2002. [USA 01] USA Today 08/01/01. http: //www. usatoday. com/life/cyber/tech/2001 -0801 -code-red-costs. htm#more [Bai 75] Norman T. J. Bailey. “The mathematical theory of infectious diseases and its applications”, 1975. 10/2/2020 Security Seminar Fall 2002 28
 Dawn dude rugs
Dawn dude rugs Computing hype problem
Computing hype problem No hype
No hype Hype driven development
Hype driven development Gartner hype cycle 2009
Gartner hype cycle 2009 Auteur theory
Auteur theory I hate hype
I hate hype I hate hype
I hate hype Gartner group hype cycle
Gartner group hype cycle Hype driven development
Hype driven development Cyber hype
Cyber hype Hype nn
Hype nn Internet or internet
Internet or internet Literature review dalam penelitian
Literature review dalam penelitian Difference between literature review and introduction
Difference between literature review and introduction Types of literature review
Types of literature review Chapter 27 mollusks and segmented worms
Chapter 27 mollusks and segmented worms Chapter 25 section 3 mollusks
Chapter 25 section 3 mollusks Sponges cnidarians and worms
Sponges cnidarians and worms Worm characteristics
Worm characteristics Fat worms waiting on a dawn bright lawn
Fat worms waiting on a dawn bright lawn Pseudocoelomate flatworm
Pseudocoelomate flatworm Sponges cnidarians and worms
Sponges cnidarians and worms 5 advanced characteristics shared by cephalopods
5 advanced characteristics shared by cephalopods Trojan horses spyware and worms are all forms of
Trojan horses spyware and worms are all forms of Section 27-3 annelids
Section 27-3 annelids The most active mollusks are the
The most active mollusks are the Chapter review motion part a vocabulary review answer key
Chapter review motion part a vocabulary review answer key Uncontrollable spending ap gov
Uncontrollable spending ap gov