IEEE 802 15 13 0006 00 004 N


- Slides: 14

IEEE 802. 15 -13 -0006 -00 -004 N Project: IEEE P 802. 15 Working Group for Wireless Personal Area Networks (WPANs) Submission Title: Adaptive timeslot allocation scheme for WBAN Date Submitted: Sept 10, 2012 Source: Wei-Xia Zou, BUPT ; Jin Shuai, BUPT ; Liang Li, Vinno; Suite 202, Building D, No. 2 Xinxi Lu, Beijing, China, Voice: 1 -914 -333 -9687, FAX: 1 -914 -332 -0615, E-Mail: liangli@vinnotech. com Abstract: Opening report for TG 4 n(MBAN) Task Group Purpose: Outline accomplishments from the March 2012 meeting and planned tasks for this meeting. Notice: This document has been prepared to assist the IEEE P 802. 15. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) reserve(s) the right to add, amend or withdraw material contained herein. Release: The contributor acknowledges and accepts that this contribution becomes the property of IEEE and may be made publicly available by P 802. 15. Submission Slide 1 Liang Li Vinno

IEEE 802. 15 -13 -0006 -00 -004 N Informative Abstract • • • General View Data Priority Classification Priority timeslot allocation scheme Data transmission procedure Conclusion Submission Slide 2 Liang Li Vinno

IEEE 802. 15 -13 -0006 -00 -004 N General View • How to support diverse Qo. S requirements of various applications is one features of WBAN MAC operation. In this proposal, we classify the traffics in WBAN scenarios into several priorities. And then, based on the data priority classification, the adaptive timeslot allocation scheme is proposed. At last, we will discuss the process of the data transfer procedure. Submission Slide 3 Liang Li Vinno

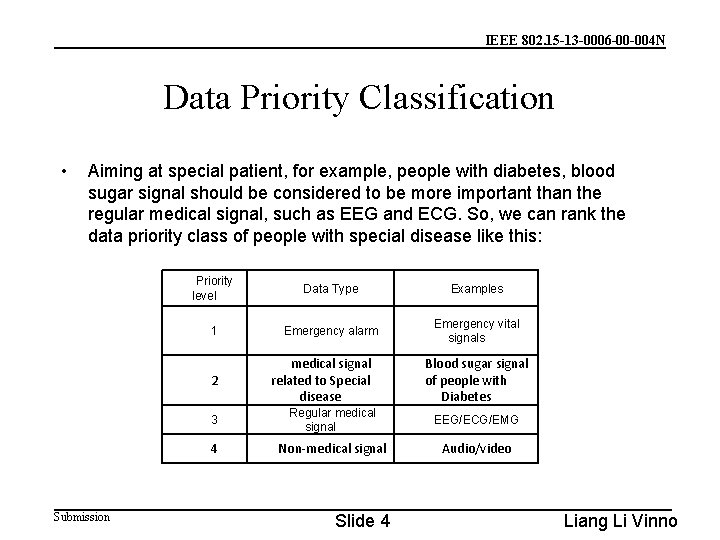
IEEE 802. 15 -13 -0006 -00 -004 N Data Priority Classification • Aiming at special patient, for example, people with diabetes, blood sugar signal should be considered to be more important than the regular medical signal, such as EEG and ECG. So, we can rank the data priority class of people with special disease like this: Priority level Data Type Examples 1 Emergency alarm Emergency vital signals 2 Submission medical signal related to Special disease Blood sugar signal of people with Diabetes 3 Regular medical signal EEG/ECG/EMG 4 Non-medical signal Audio/video Slide 4 Liang Li Vinno

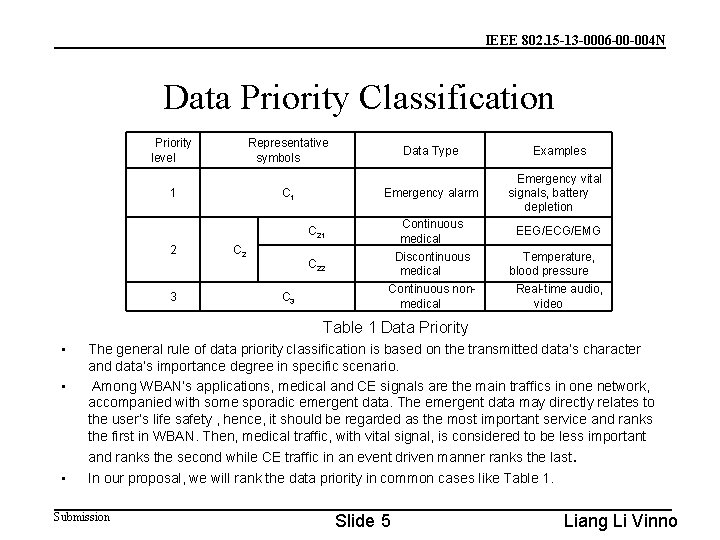
IEEE 802. 15 -13 -0006 -00 -004 N Data Priority Classification Priority level Representative symbols 1 2 3 C 1 C 2 C 3 Data Type Emergency alarm C 21 Continuous medical C 22 Discontinuous medical Continuous nonmedical Examples Emergency vital signals, battery depletion EEG/ECG/EMG Temperature, blood pressure Real-time audio, video Table 1 Data Priority • • • The general rule of data priority classification is based on the transmitted data’s character and data’s importance degree in specific scenario. Among WBAN‘s applications, medical and CE signals are the main traffics in one network, accompanied with some sporadic emergent data. The emergent data may directly relates to the user’s life safety , hence, it should be regarded as the most important service and ranks the first in WBAN. Then, medical traffic, with vital signal, is considered to be less important and ranks the second while CE traffic in an event driven manner ranks the last. In our proposal, we will rank the data priority in common cases like Table 1. Submission Slide 5 Liang Li Vinno

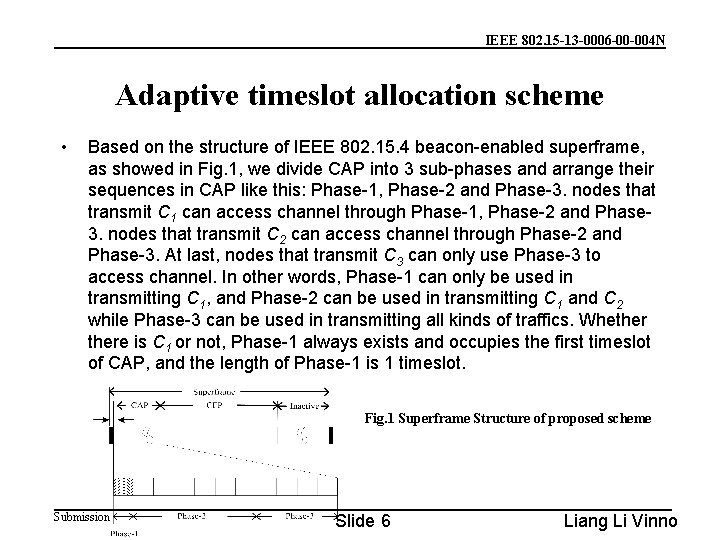
IEEE 802. 15 -13 -0006 -00 -004 N Adaptive timeslot allocation scheme • Based on the structure of IEEE 802. 15. 4 beacon-enabled superframe, as showed in Fig. 1, we divide CAP into 3 sub-phases and arrange their sequences in CAP like this: Phase-1, Phase-2 and Phase-3. nodes that transmit C 1 can access channel through Phase-1, Phase-2 and Phase 3. nodes that transmit C 2 can access channel through Phase-2 and Phase-3. At last, nodes that transmit C 3 can only use Phase-3 to access channel. In other words, Phase-1 can only be used in transmitting C 1, and Phase-2 can be used in transmitting C 1 and C 2 while Phase-3 can be used in transmitting all kinds of traffics. Whethere is C 1 or not, Phase-1 always exists and occupies the first timeslot of CAP, and the length of Phase-1 is 1 timeslot. Fig. 1 Superframe Structure of proposed scheme Submission Slide 6 Liang Li Vinno

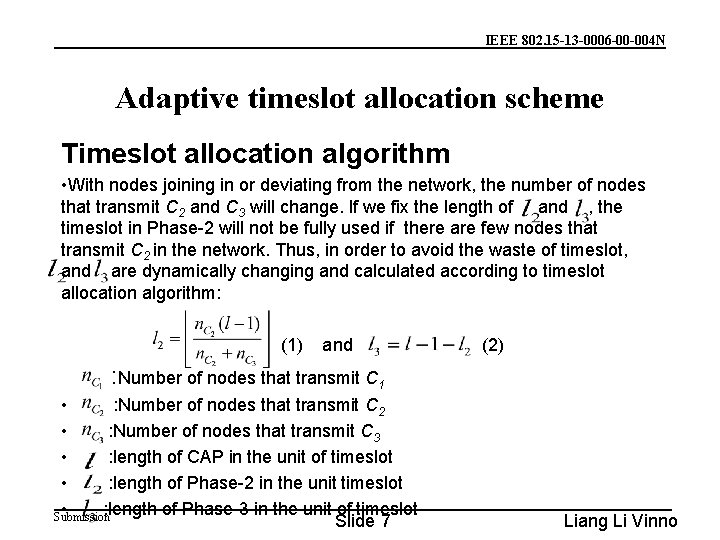
IEEE 802. 15 -13 -0006 -00 -004 N Adaptive timeslot allocation scheme Timeslot allocation algorithm • With nodes joining in or deviating from the network, the number of nodes that transmit C 2 and C 3 will change. If we fix the length of and , the timeslot in Phase-2 will not be fully used if there are few nodes that transmit C 2 in the network. Thus, in order to avoid the waste of timeslot, and are dynamically changing and calculated according to timeslot allocation algorithm: (1) and (2) : Number of nodes that transmit C 1 • : Number of nodes that transmit C 2 • : Number of nodes that transmit C 3 • : length of CAP in the unit of timeslot • : length of Phase-2 in the unit timeslot • : length of Phase-3 in the unit of timeslot Submission Slide 7 Liang Li Vinno

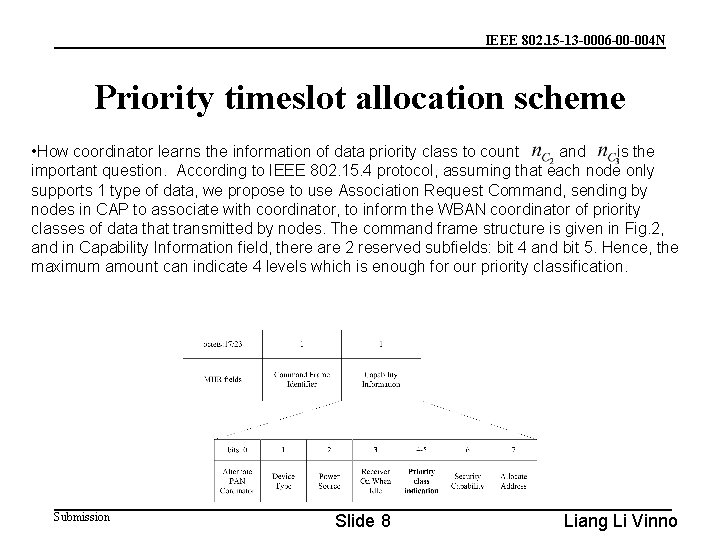
IEEE 802. 15 -13 -0006 -00 -004 N Priority timeslot allocation scheme • How coordinator learns the information of data priority class to count and is the important question. According to IEEE 802. 15. 4 protocol, assuming that each node only supports 1 type of data, we propose to use Association Request Command, sending by nodes in CAP to associate with coordinator, to inform the WBAN coordinator of priority classes of data that transmitted by nodes. The command frame structure is given in Fig. 2, and in Capability Information field, there are 2 reserved subfields: bit 4 and bit 5. Hence, the maximum amount can indicate 4 levels which is enough for our priority classification. Submission Slide 8 Liang Li Vinno

IEEE 802. 15 -13 -0006 -00 -004 N Data transmission procedure • In the superframe structure of IEEE 802. 15. 4, CAP is suitable for the transfer of short data and command message, while CFP is design for continual message transfer. – C 1: Appears in the form of short and sporadic message, the nodes transmit C 1 immediately once successfully accesses channel in CAP. – C 21: Appears in the form of large periodic and continual message. The node uniformly sends GTS request command frame in CAP to apply for GTS allocation, and transmit C 21 in allocated GTS of next superframe. – C 22: Appears in the form of small periodic and discrete message. The nodes transmit C 22 immediately once successfully accesses channel in CAP – C 3: Appears in the form of burst and large continual message. The node uniformly sends GTS request command frame in CAP to apply for GTS allocation, and transmits C 3 in allocated GTS of next superframe. Submission Slide 9 Liang Li Vinno

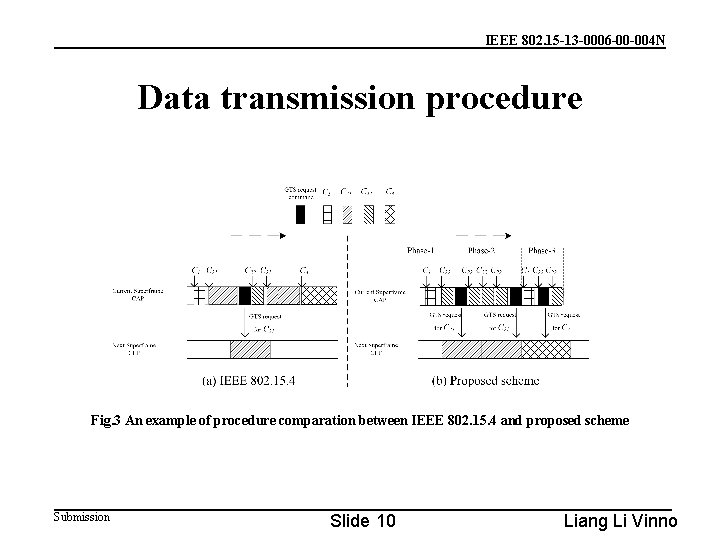
IEEE 802. 15 -13 -0006 -00 -004 N Data transmission procedure Fig. 3 An example of procedure comparation between IEEE 802. 15. 4 and proposed scheme Submission Slide 10 Liang Li Vinno

IEEE 802. 15 -13 -0006 -00 -004 N Data transmission procedure • As showed in Fig. 3, each kind of traffic follows the rule to be transmitted. On one hand, continual traffic no longer tries to be sent in CAP directly, hence, there are more chances for short message and GTS request command to be successfully delivered to coordinator in CAP. On the other hand, with the growth of successfully GTS request command delivery probability, continual traffic can be delivered with less latency in CFP. At last, compared to C 3, GTS request command for C 21 owns a higher probability to be delivered in CAP with the help of priority timeslot allocation scheme, and consequently, it is easier for C 21 to obtain GTS in the next superframe, so priority scheme also affects the continual traffic transmission in CFP. Submission Slide 11 Liang Li Vinno

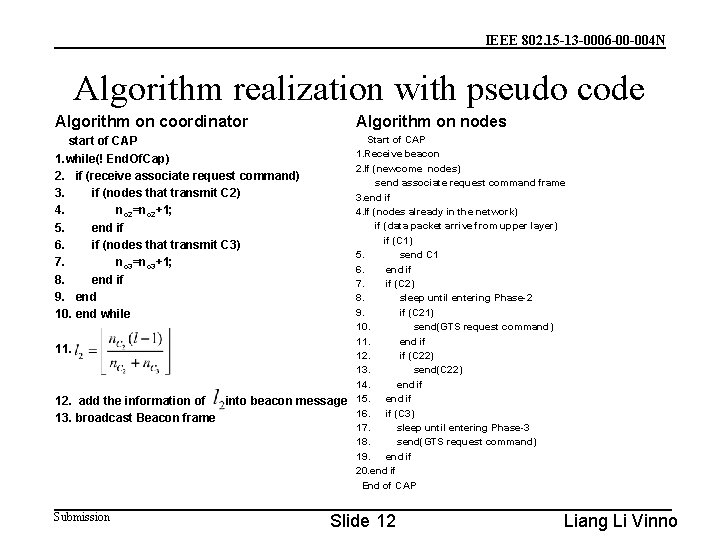
IEEE 802. 15 -13 -0006 -00 -004 N Algorithm realization with pseudo code Algorithm on coordinator Algorithm on nodes start of CAP 1. while(! End. Of. Cap) 2. if (receive associate request command) 3. if (nodes that transmit C 2) 4. n c 2=nc 2+1; 5. end if 6. if (nodes that transmit C 3) 7. n c 3=nc 3+1; 8. end if 9. end 10. end while Start of CAP 1. Receive beacon 2. If (newcome nodes) send associate request command frame 3. end if 4. If (nodes already in the network) if (data packet arrive from upper layer) if (C 1) 5. send C 1 6. end if 7. if (C 2) 8. sleep until entering Phase-2 9. if (C 21) 10. send(GTS request command) 11. end if 12. if (C 22) 13. send(C 22) 14. end if 15. end if 16. if (C 3) 17. sleep until entering Phase-3 18. send(GTS request command) 19. end if 20. end if End of CAP 11. 12. add the information of into beacon message 13. broadcast Beacon frame Submission Slide 12 Liang Li Vinno

IEEE 802. 15 -13 -0006 -00 -004 N Advantages of proposal • Differentiate Qo. S requirements of wireless body area network data: the higher the data’s priority class is, the higher the probability of access channel and the smaller the corresponding transmission delay. • Nodes, in each priority class, try to access channel in the specific phase and go to sleep in the rest of the time, so it is an efficient way for nodes’ energy saving. • Data transmission procedure helps to alleviate the data transmission collision in CAP, so, it increases the probability for successful transmission of discontinuous data and GTS request command frame. Submission Slide 13 Liang Li Vinno

IEEE 802. 15 -13 -0006 -00 -004 N Summary • General View • Data Priority Classification • Priority timeslot allocation scheme • Timeslot allocation algorithm • Algorithm realization in IEEE 802. 15. 4 • Data transmission procedure • Conclusion Submission Slide 14 Liang Li (Vinno)