Hospital Automation using RFID Technology Gustavo Florentino University






- Slides: 13

Hospital Automation using RFID Technology Gustavo Florentino University of Colorado at Colorado Springs College of Engineering & Applied Science

Objectives n Speed up processes in the laboratory. n Use smart cards to store patient’s information and to perform authentication. n Use RFID tags to identify sample recipients. n Reduce faults on exams regarding to data flow in the laboratory. n Create a system which is simple for hospital employees to operate.

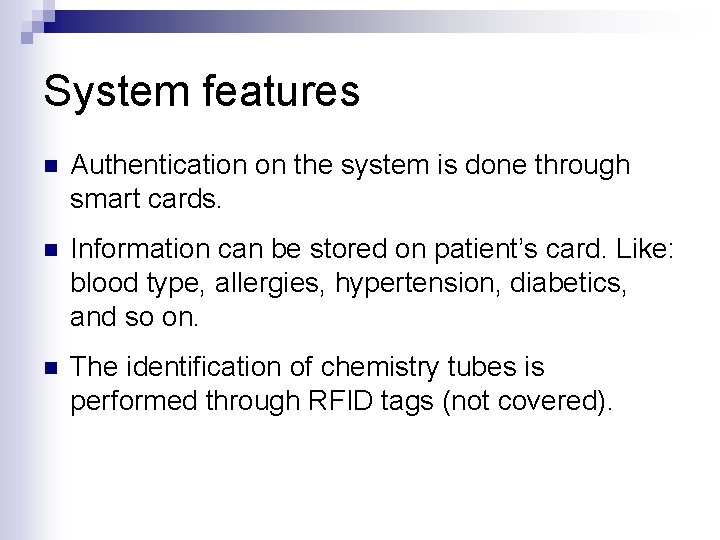
System features n Authentication on the system is done through smart cards. n Information can be stored on patient’s card. Like: blood type, allergies, hypertension, diabetics, and so on. n The identification of chemistry tubes is performed through RFID tags (not covered).

Problems n Many smartcards → low cost. n The smart card used does not have processor to process user programs. n Then, many authentication algorithms proposed in literature cannot be used. Ex: challengeresponse.

Security requirements n We have to: ¨ ¨ ¨ Avoid non-authorized people from reading the information stored on the card. Use the card as an authentication device. Ensure that the data on the card has not been tampered.

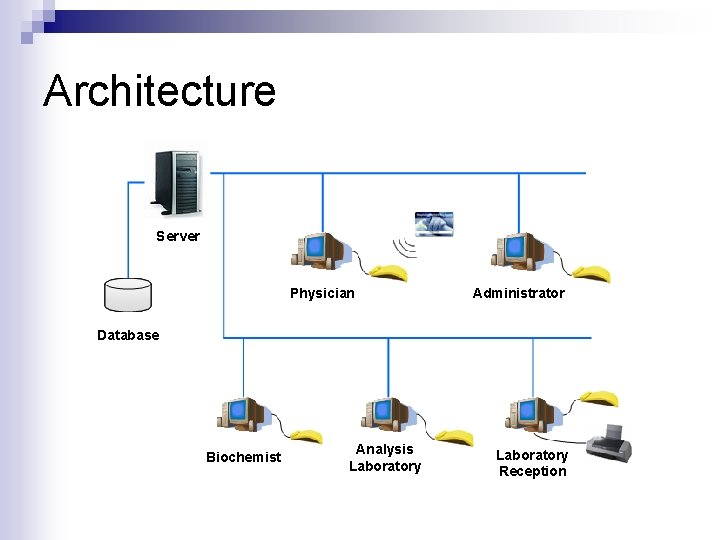
Architecture Server Physician Administrator Database Biochemist Analysis Laboratory Reception

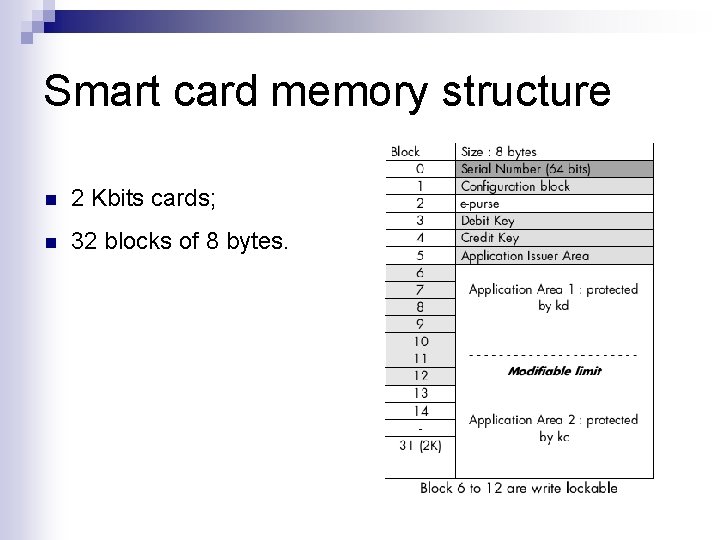
Smart card memory structure n 2 Kbits cards; n 32 blocks of 8 bytes.

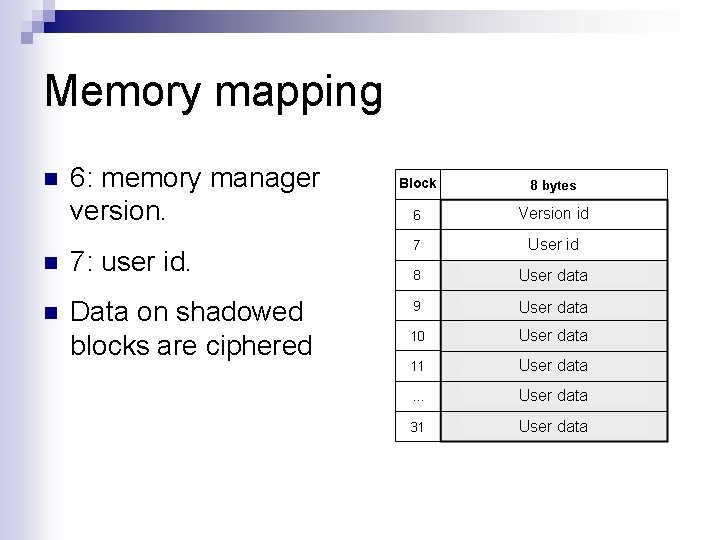
Memory mapping n 6: memory manager version. n 7: user id. n Data on shadowed blocks are ciphered Block Version id User data User data

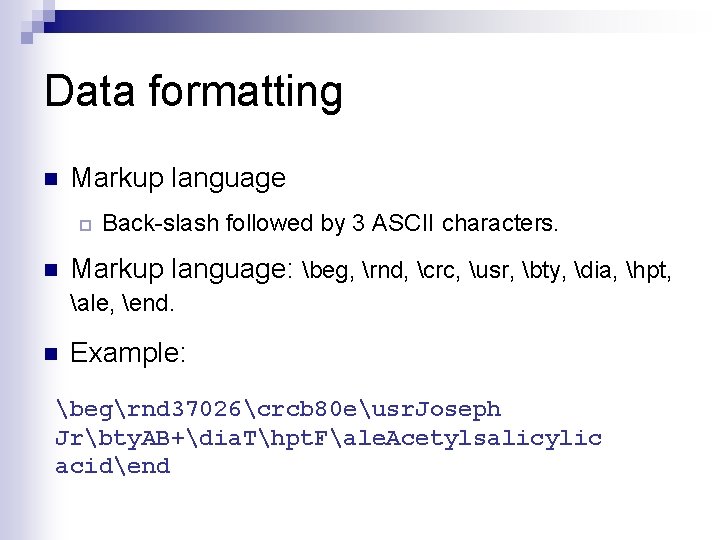
Data formatting n Markup language ¨ Back-slash followed by 3 ASCII characters. n Markup language: beg, rnd, crc, usr, bty, dia, hpt, ale, end. n Example: begrnd 37026crcb 80 eusr. Joseph Jrbty. AB+dia. Thpt. Fale. Acetylsalicylic acidend

Security n Symmetric key cryptography: AES ¨ ¨ Faster than an asymmetric algorithm. At first, only the system is capable of reading and writing on the card. n One key is used for each card. n System security doesn’t rely on manufacturer’s specific mechanisms. So we can easily change the reader and card model or manufacturer if necessary.

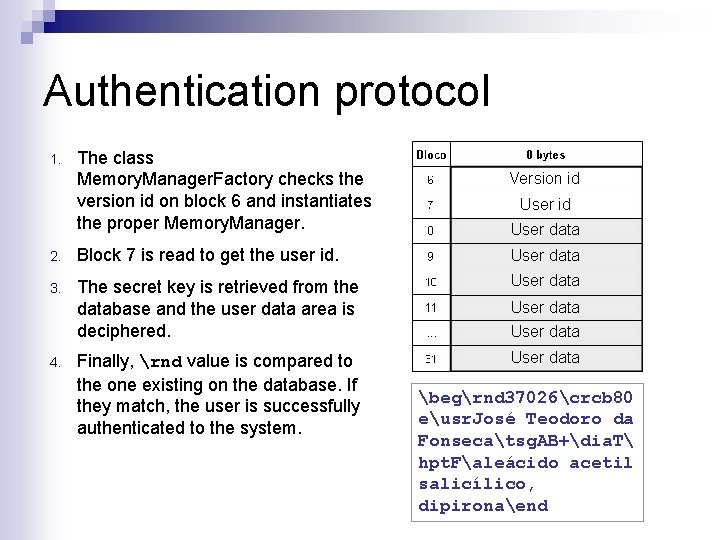
Authentication protocol 1. The class Memory. Manager. Factory checks the version id on block 6 and instantiates the proper Memory. Manager. Version id User data 2. Block 7 is read to get the user id. User data 3. The secret key is retrieved from the database and the user data area is deciphered. User data Finally, rnd value is compared to the one existing on the database. If they match, the user is successfully authenticated to the system. User data 4. User data begrnd 37026crcb 80 eusr. José Teodoro da Fonsecatsg. AB+dia. T hpt. Faleácido acetil salicílico, dipironaend

Data integrity n A cyclic redundancy check code is used to verify integrity of the data contained on the card. n Stronger message digests weren’t employed due to memory constraints. n While data is read from the card, it’s checked if the CRC calculated matches the one read from the card. n This procedure avoids changes of the data on the card by malicious users.

Conclusions n Due to severe memory and processing constraints, many techniques found on the literature cannot be applied to this system. n The solution was to make use of digital signature concepts.
 Library automation using rfid project
Library automation using rfid project Rfid in library automation
Rfid in library automation Florentino ulibarri poemas
Florentino ulibarri poemas Florentino collantes
Florentino collantes Florentino paredes
Florentino paredes Ruiz de galarreta
Ruiz de galarreta Catalina florentino
Catalina florentino Rfid technology overview
Rfid technology overview Rfid
Rfid Rfid technology seminar
Rfid technology seminar Pyautogui web browser
Pyautogui web browser Industrial automation using plc
Industrial automation using plc Conclusion for home automation
Conclusion for home automation Problem statement for home automation using arduino
Problem statement for home automation using arduino