Higher Order Universal OneWay Hash Functions Deukjo Hong






![Extension of UOWHF(r) Then, TRt[H]: UOWHF for t l … HK … HK … Extension of UOWHF(r) Then, TRt[H]: UOWHF for t l … HK … HK …](https://slidetodoc.com/presentation_image_h2/5fea1e2f815cde18abfa07ea4b4f2283/image-12.jpg)
- Slides: 17

Higher Order Universal One-Way Hash Functions Deukjo Hong Graduate School of Information Security, Center for Information Security Technologies, Korea University

Contents § § Security Notions of Hash Functions Extension of UOWHF of order r Construction of UOWHF of order r Conclusion

Security Notions of Hash Functions § F: D R is a function. § For x, x D, (x, x ) is a collision under F. x x and F(x) = F(x ).

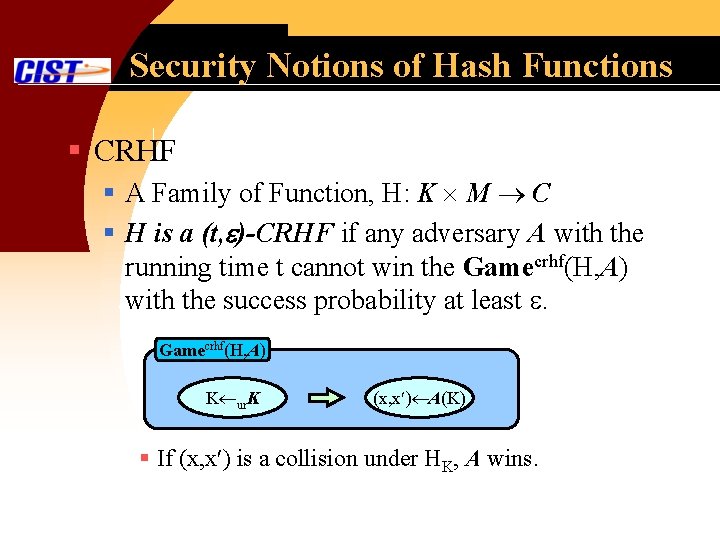
Security Notions of Hash Functions § CRHF § A Family of Function, H: K M C § H is a (t, )-CRHF if any adversary A with the running time t cannot win the Gamecrhf(H, A) with the success probability at least . Gamecrhf(H, A) K ur. K (x, x ) A(K) § If (x, x ) is a collision under HK, A wins.

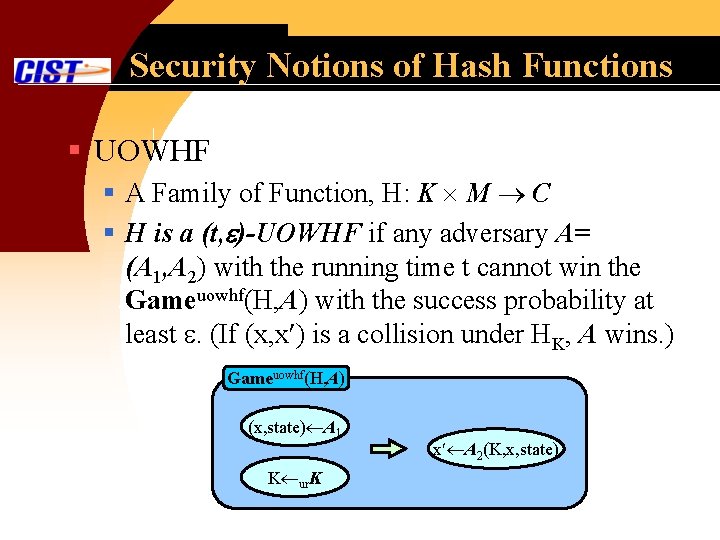
Security Notions of Hash Functions § UOWHF § A Family of Function, H: K M C § H is a (t, )-UOWHF if any adversary A= (A 1, A 2) with the running time t cannot win the Gameuowhf(H, A) with the success probability at least . (If (x, x ) is a collision under HK, A wins. ) Gameuowhf(H, A) (x, state) A 1 K ur. K x A 2(K, x, state)

Security Notions of Hash Functions § A UOWHF has some advantages compared to a CRHF. § § Security bound is 2 n when the output length is n. A UOWHF is weaker than a CRHF. A UOWHF is easier to design than a CRHF. “Ask less of a hash function and it is less likely to disappoint!”

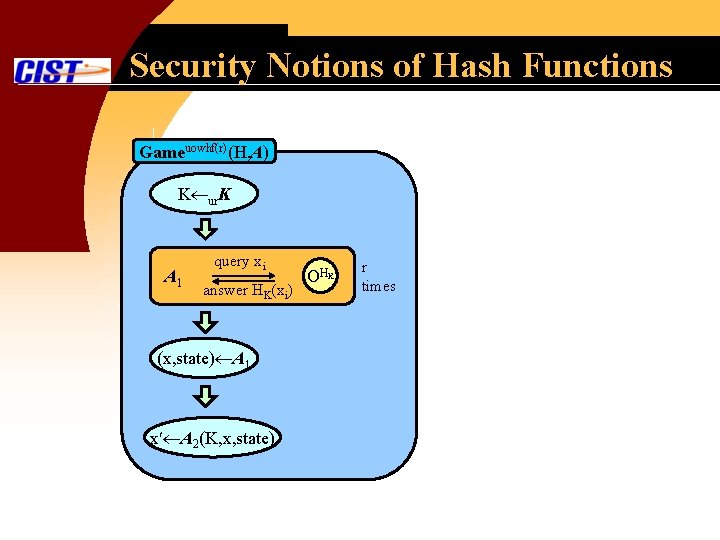
Security Notions of Hash Functions § UOWHF(r): UOHWF of order r § A Family of Function, H: K M C § H is a (t, )-UOWHF(r) if any adversary A= (A 1, A 2) with the running time t cannot win the Gameuowhf(r)(H, A) with the success probability at least . (If (x, x ) is a collision under HK, A wins. )

Security Notions of Hash Functions Gameuowhf(r)(H, A) K ur. K A 1 query xi answer HK(xi) (x, state) A 1 x A 2(K, x, state) OH K r times

Security Notions of Hash Functions § Relationship among the notions § § Let H: K M C be a family of hash functions. H: UOWHF(0). H: UOWHF(r+1) H: UOWHF(r). H: CRHF H: UOWHF(r)

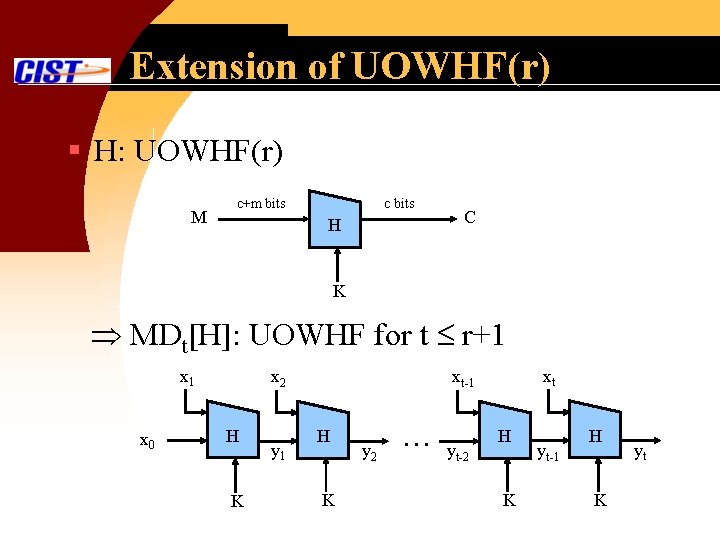
Extension of UOWHF(r) § H: UOWHF(r) M c+m bits c bits H C K MDt[H]: UOWHF for t r+1 x 0 x 2 H K y 1 xt xt-1 H K y 2 … yt-2 H K yt-1 H K yt

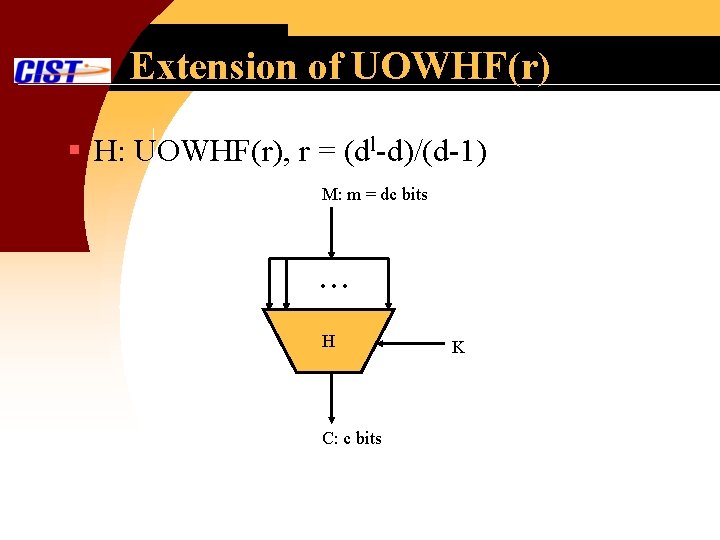
Extension of UOWHF(r) § H: UOWHF(r), r = (dl-d)/(d-1) M: m = dc bits … H C: c bits K
![Extension of UOWHFr Then TRtH UOWHF for t l HK HK Extension of UOWHF(r) Then, TRt[H]: UOWHF for t l … HK … HK …](https://slidetodoc.com/presentation_image_h2/5fea1e2f815cde18abfa07ea4b4f2283/image-12.jpg)
Extension of UOWHF(r) Then, TRt[H]: UOWHF for t l … HK … HK … … … … … HK

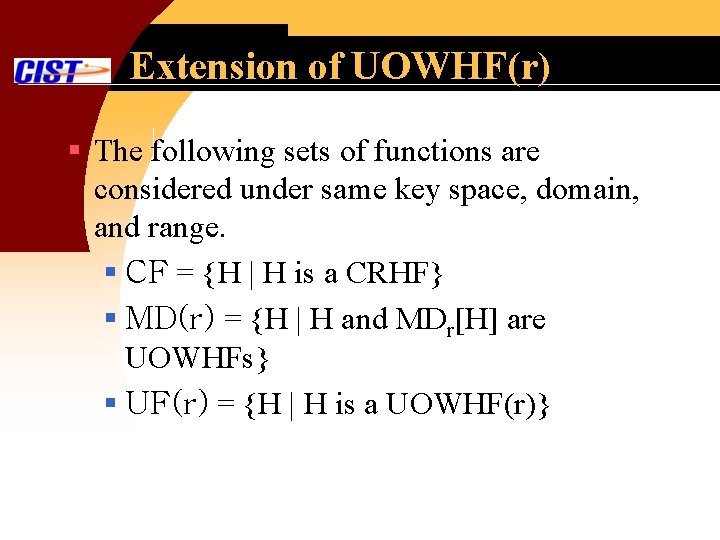
Extension of UOWHF(r) § The following sets of functions are considered under same key space, domain, and range. § CF = {H | H is a CRHF} § MD(r) = {H | H and MDr[H] are UOWHFs} § UF(r) = {H | H is a UOWHF(r)}

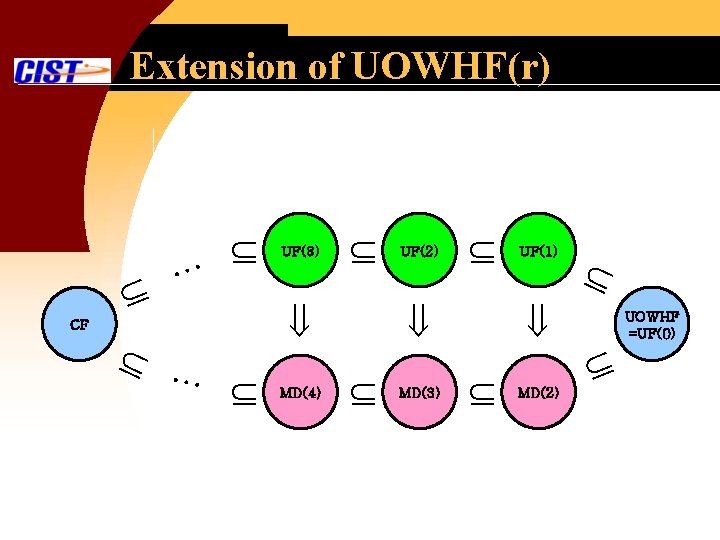
Extension of UOWHF(r) … CF … UF(3) MD(4) UF(2) MD(3) UF(1) MD(2) UOWHF =UF(0)

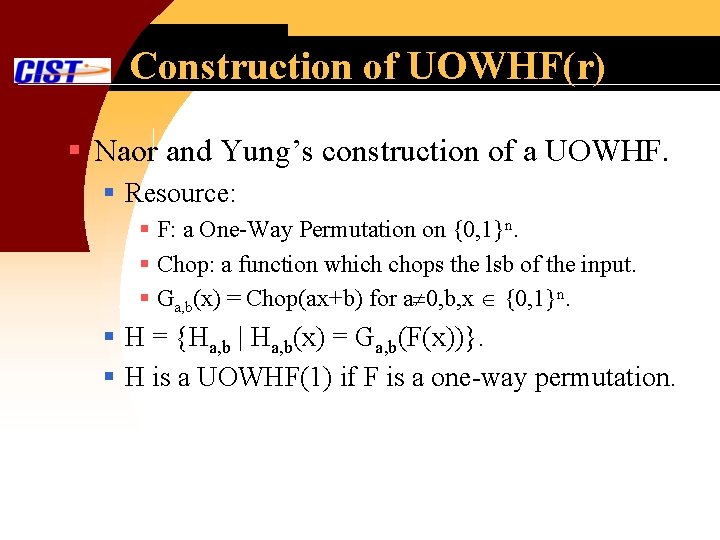
Construction of UOWHF(r) § Naor and Yung’s construction of a UOWHF. § Resource: § F: a One-Way Permutation on {0, 1}n. § Chop: a function which chops the lsb of the input. § Ga, b(x) = Chop(ax+b) for a 0, b, x {0, 1}n. § H = {Ha, b | Ha, b(x) = Ga, b(F(x))}. § H is a UOWHF(1) if F is a one-way permutation.

Construction of UOWHF(r) § Generalization: § Gar, …, a 0(x) = Chop(arxr+…+a 1 x+a 0). § H = {Har, …, a 0 | Har, …, a 0(x) = Gar, …a 0(F(x))}. § H is a UOWHF(r) if F is a one-way permutation.

Conclusion § The existing extensions for UOWHFs require random key values whose total length increase with message length. § The notion of UOWHF with order is helpful for reducing total key length of existing extensions for UOWHFs. § UOWHF of order r can be constructed to be provably secure from a one-way permutation.