Fundamentals of Computer Networks ECE 478578 Lecture 13



- Slides: 19

Fundamentals of Computer Networks ECE 478/578 Lecture #13: Packet Switching (2) Instructor: Loukas Lazos Dept of Electrical and Computer Engineering University of Arizona

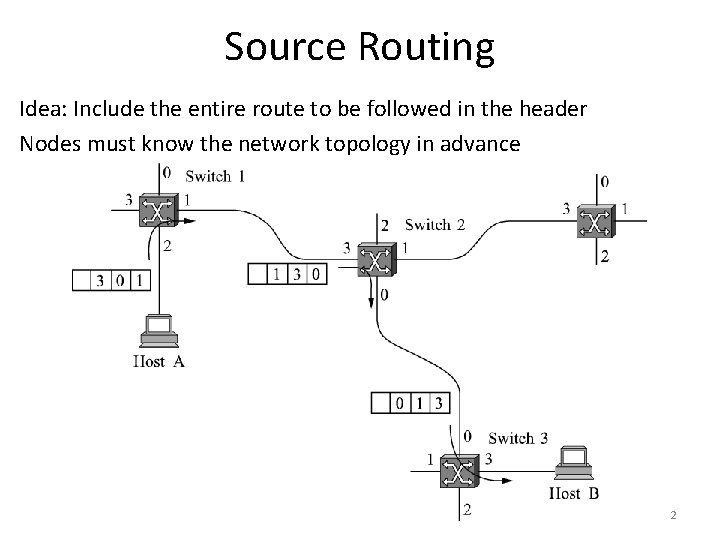
Source Routing Idea: Include the entire route to be followed in the header Nodes must know the network topology in advance 2

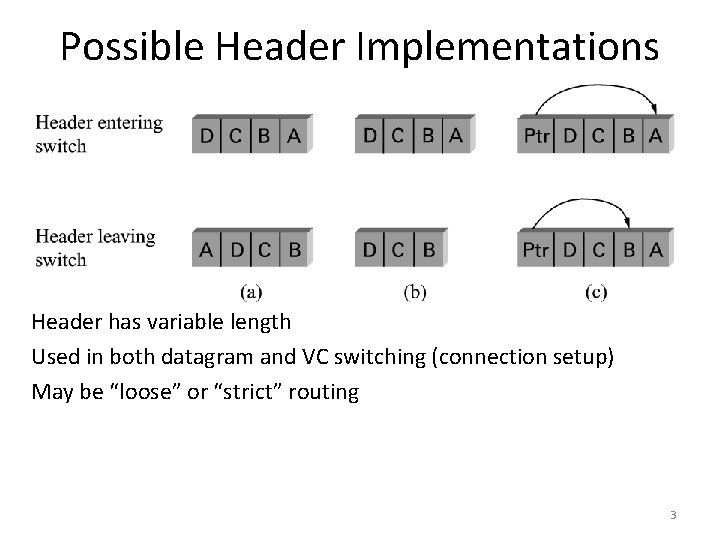
Possible Header Implementations Header has variable length Used in both datagram and VC switching (connection setup) May be “loose” or “strict” routing 3

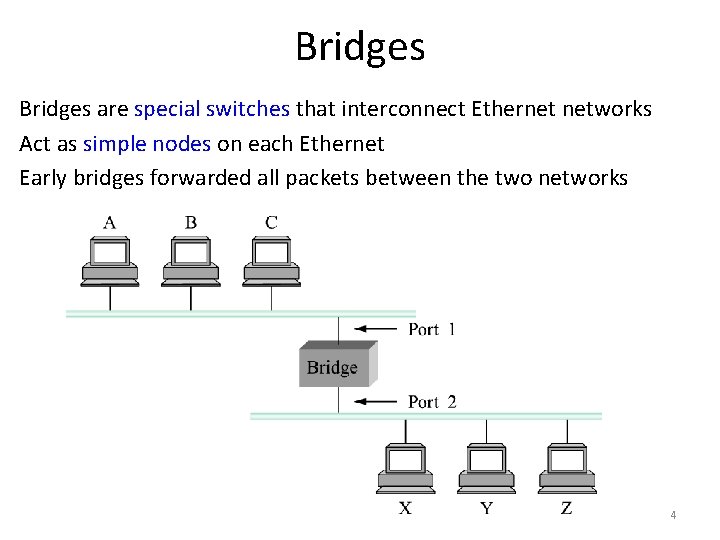
Bridges are special switches that interconnect Ethernet networks Act as simple nodes on each Ethernet Early bridges forwarded all packets between the two networks 4

Bridges Vs. Repeaters are analog amplifiers of the signal Monitor the existence of analog signal on the line Amplify and repeat the signal Physical layer function, no message parsing Bridges “repeat” frames rather than signals They forward received frames among different LANs Message parsing is performed to decide whether to fwd the packet or not 5

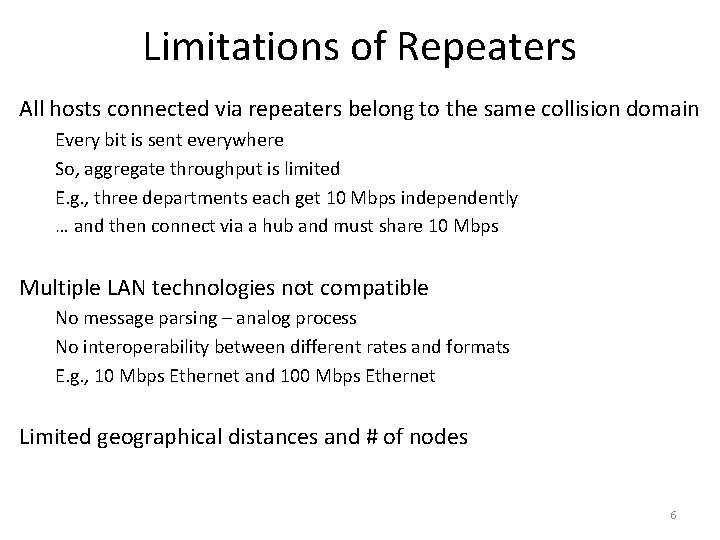
Limitations of Repeaters All hosts connected via repeaters belong to the same collision domain Every bit is sent everywhere So, aggregate throughput is limited E. g. , three departments each get 10 Mbps independently … and then connect via a hub and must share 10 Mbps Multiple LAN technologies not compatible No message parsing – analog process No interoperability between different rates and formats E. g. , 10 Mbps Ethernet and 100 Mbps Ethernet Limited geographical distances and # of nodes 6

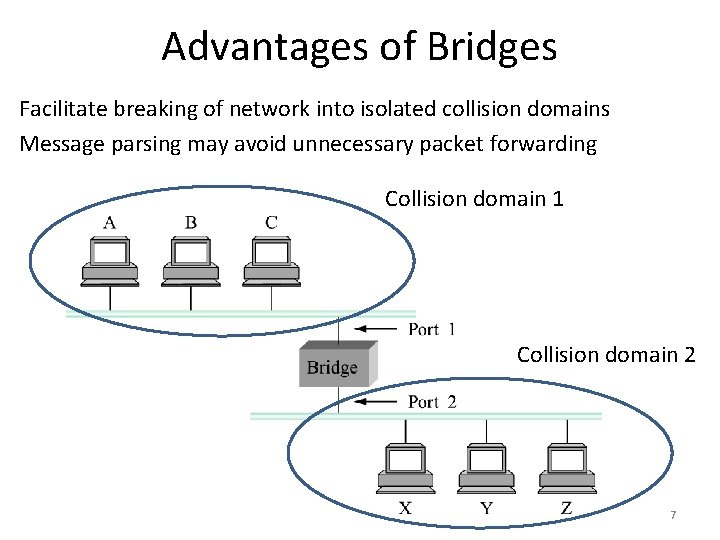
Advantages of Bridges Facilitate breaking of network into isolated collision domains Message parsing may avoid unnecessary packet forwarding Collision domain 1 Collision domain 2 7

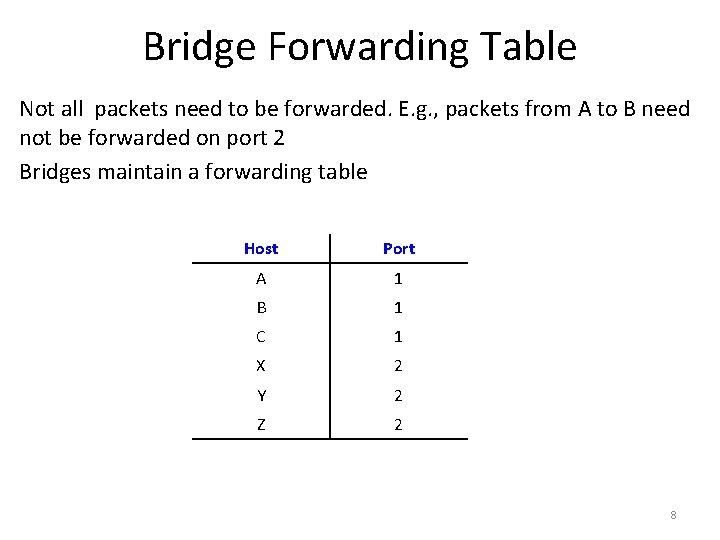
Bridge Forwarding Table Not all packets need to be forwarded. E. g. , packets from A to B need not be forwarded on port 2 Bridges maintain a forwarding table Host Port A 1 B 1 C 1 X 2 Y 2 Z 2 8

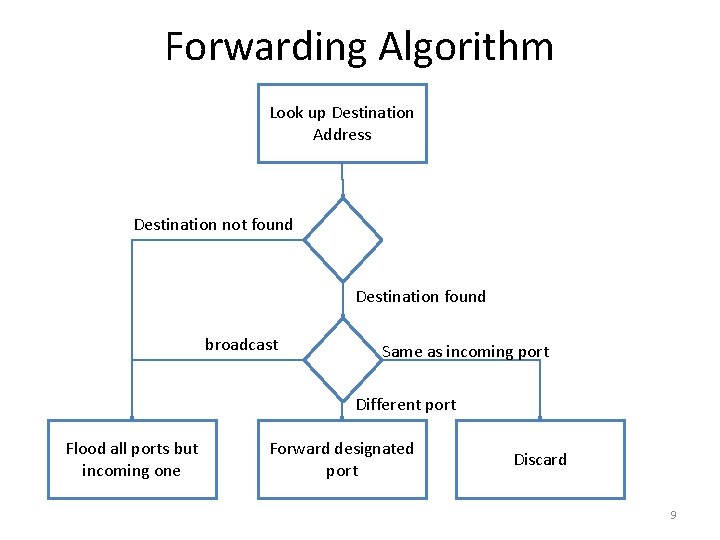
Forwarding Algorithm Look up Destination Address Destination not found Destination found broadcast Same as incoming port Different port Flood all ports but incoming one Forward designated port Discard 9

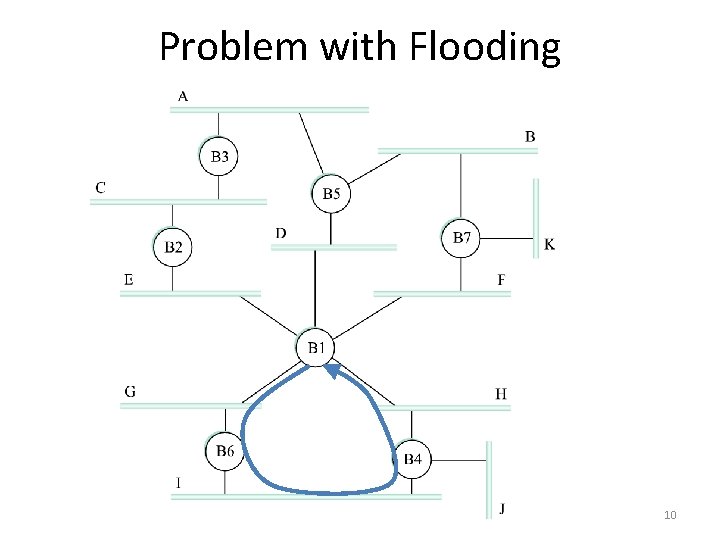
Problem with Flooding 10

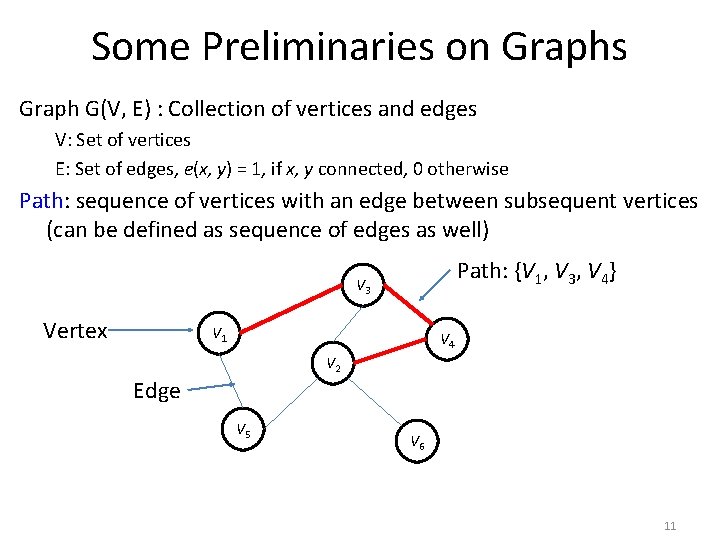
Some Preliminaries on Graphs Graph G(V, E) : Collection of vertices and edges V: Set of vertices E: Set of edges, e(x, y) = 1, if x, y connected, 0 otherwise Path: sequence of vertices with an edge between subsequent vertices (can be defined as sequence of edges as well) Path: {V 1, V 3, V 4} V 3 Vertex V 1 V 4 V 2 Edge V 5 V 6 11

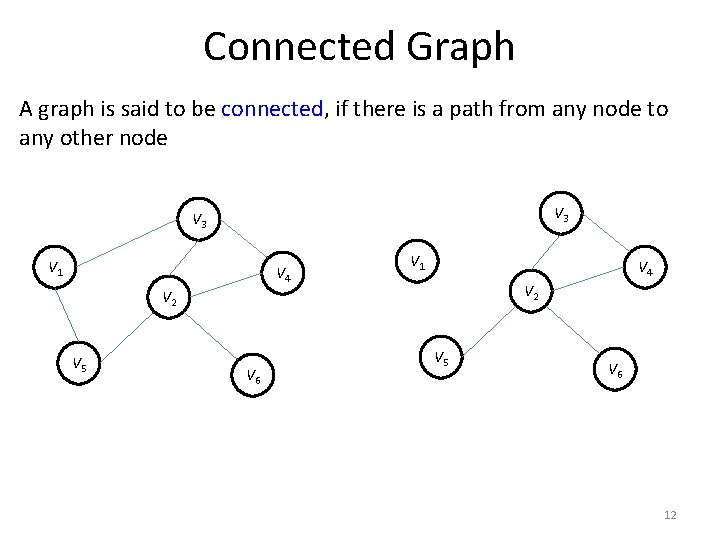
Connected Graph A graph is said to be connected, if there is a path from any node to any other node V 3 V 1 V 4 V 2 V 5 V 6 12

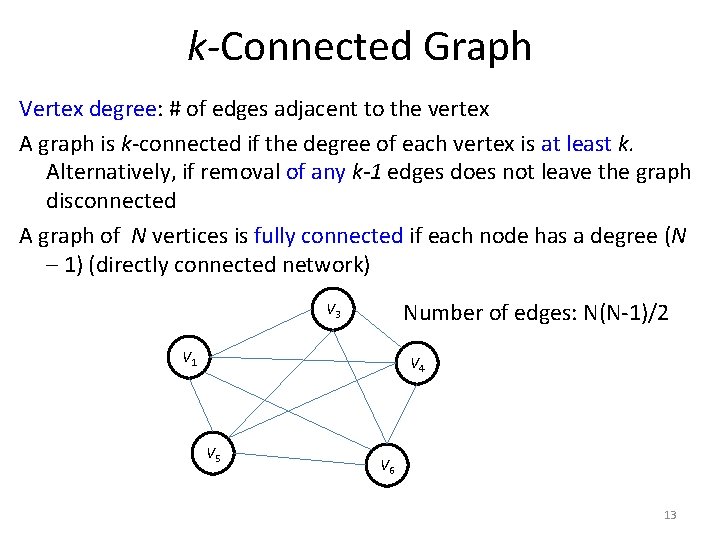
k-Connected Graph Vertex degree: # of edges adjacent to the vertex A graph is k-connected if the degree of each vertex is at least k. Alternatively, if removal of any k-1 edges does not leave the graph disconnected A graph of N vertices is fully connected if each node has a degree (N – 1) (directly connected network) Number of edges: N(N-1)/2 V 3 V 1 V 4 V 5 V 6 13

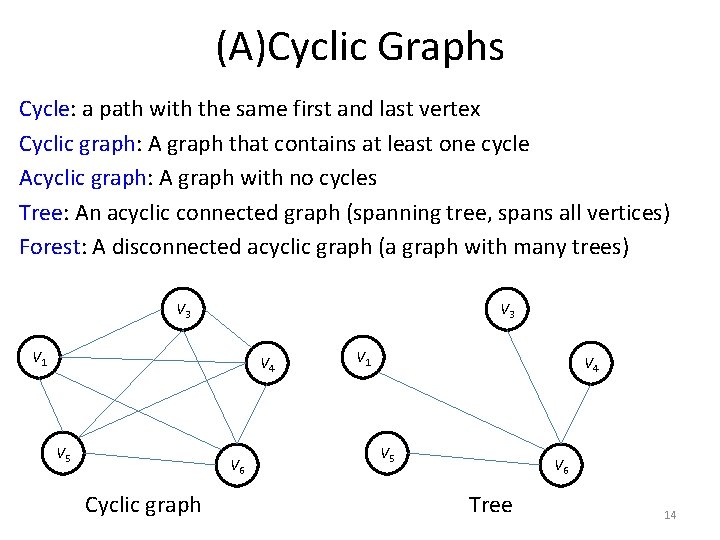
(A)Cyclic Graphs Cycle: a path with the same first and last vertex Cyclic graph: A graph that contains at least one cycle Acyclic graph: A graph with no cycles Tree: An acyclic connected graph (spanning tree, spans all vertices) Forest: A disconnected acyclic graph (a graph with many trees) V 3 V 1 V 4 V 5 V 6 Cyclic graph V 1 V 4 V 5 V 6 Tree 14

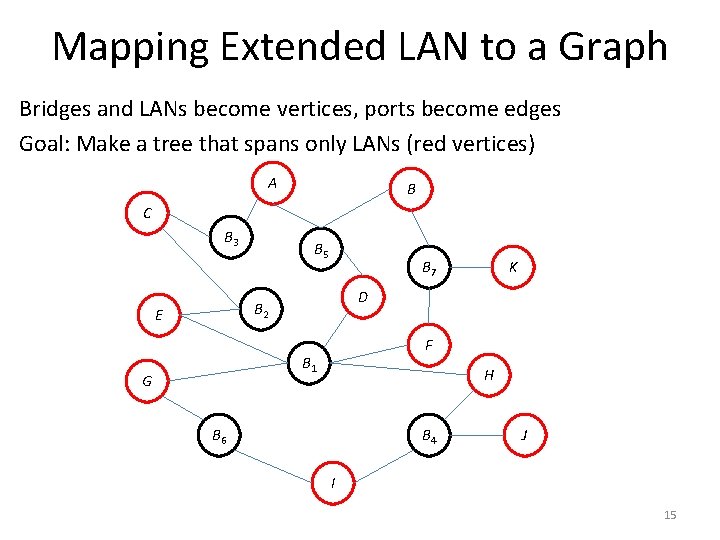
Mapping Extended LAN to a Graph Bridges and LANs become vertices, ports become edges Goal: Make a tree that spans only LANs (red vertices) A B C B 3 B 5 B 7 D B 2 E F B 1 G K H B 6 B 4 J I 15

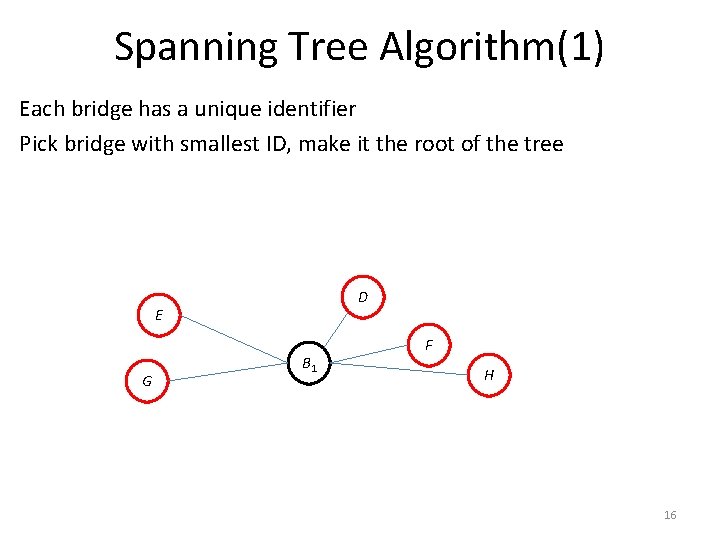
Spanning Tree Algorithm(1) Each bridge has a unique identifier Pick bridge with smallest ID, make it the root of the tree D E G B 1 F H 16

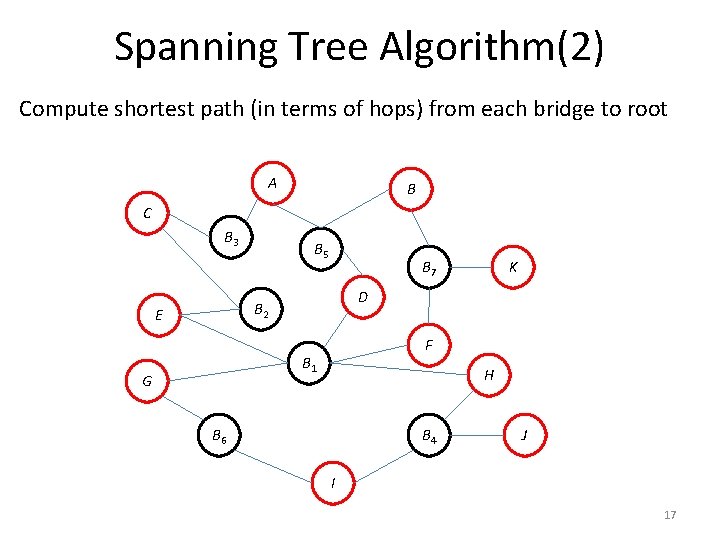
Spanning Tree Algorithm(2) Compute shortest path (in terms of hops) from each bridge to root A B C B 3 B 5 B 7 D B 2 E F B 1 G K H B 6 B 4 J I 17

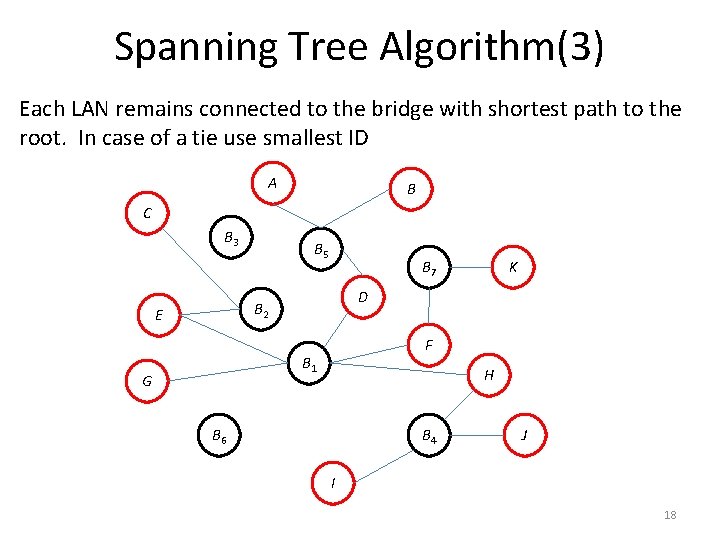
Spanning Tree Algorithm(3) Each LAN remains connected to the bridge with shortest path to the root. In case of a tie use smallest ID A B C B 3 B 5 B 7 D B 2 E F B 1 G K H B 6 B 4 J I 18

Message Exchange Initially, all bridges consider themselves as roots Broadcast on all ports ID, root bridge, and distance to root If bridge hears a message from another bridge with smaller ID it adjusts root/distance, and forwards Ex. , Let (Y, d, X) denote (root, distance, bridge ID) B 3 receives (B 2, 0, B 2) B 3 accepts B 2 as root B 3 adds one on its distance to B 2, and fwds to B 5 (B 2, 1, B 3) B 2 accepts B 1 as root and updates B 3 with (B 1, 1, B 2) B 5 accepts B 1 as root and updates B 3 with (B 1, 1, B 3) B 3 accepts B 1 as root, and note that both B 2, B 5 are closer to root in both ports. Hence, B 3 blocks all ports 19
 A switch in a datagram network uses a
A switch in a datagram network uses a Basestore iptv
Basestore iptv 01:640:244 lecture notes - lecture 15: plat, idah, farad
01:640:244 lecture notes - lecture 15: plat, idah, farad Logic and computer design fundamentals
Logic and computer design fundamentals Logic and computer design fundamentals
Logic and computer design fundamentals Logic and computer design fundamentals
Logic and computer design fundamentals Logic and computer design fundamentals
Logic and computer design fundamentals Orthogonal projection in computer graphics
Orthogonal projection in computer graphics Sierpinski gasket in computer graphics
Sierpinski gasket in computer graphics Computer fundamentals chapter 1
Computer fundamentals chapter 1 Fundamentals of computer design
Fundamentals of computer design Computer fundamentals anita goel
Computer fundamentals anita goel Fundamentals of computer design
Fundamentals of computer design Computer security fundamentals 4th edition
Computer security fundamentals 4th edition Programming fundamentals 1
Programming fundamentals 1 Logic & computer design fundamentals
Logic & computer design fundamentals Fundamentals of cpu in advanced computer architecture
Fundamentals of cpu in advanced computer architecture Chapter 23 computer system fundamentals
Chapter 23 computer system fundamentals Computer security 161 cryptocurrency lecture
Computer security 161 cryptocurrency lecture Computer aided drug design lecture notes
Computer aided drug design lecture notes