Firewalls n Types of Firewalls n Inspection Methods


- Slides: 12

Firewalls n Types of Firewalls n Inspection Methods ¡ ¡ Static Packet Inspection Stateful Packet Inspection NAT Application Firewalls n Firewall Architecture n Configuring, Testing, and Maintenance 1

Figure 5 -8: Stateful Inspection Firewalls n State of Connection: Open or Closed ¡ State: Order of packet within a dialog ¡ Often simply whether the packet is part of an open connection 2

Figure 5 -8: Stateful Inspection Firewalls n Stateful Firewall Operation ¡ For TCP, record two IP addresses and port numbers in state table as OK (open) (Figure 5 -9) ¡ By default, permit connections from internal clients (on trusted network) to external servers (on untrusted network) n ¡ This default behavior can be changed with an ACL Accept future packets between these hosts and ports with little or no inspection 3

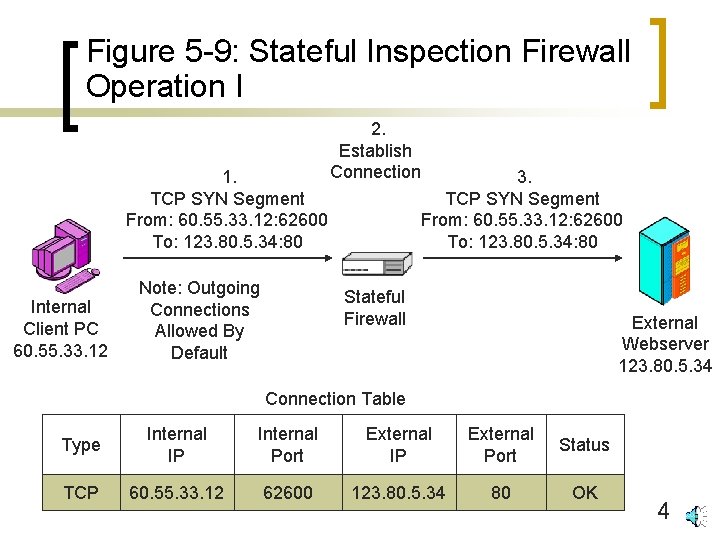
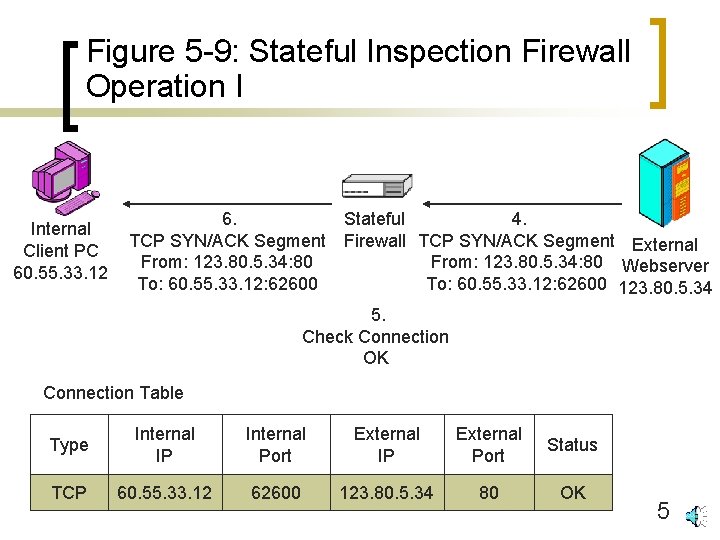
Figure 5 -9: Stateful Inspection Firewall Operation I 1. TCP SYN Segment From: 60. 55. 33. 12: 62600 To: 123. 80. 5. 34: 80 Internal Client PC 60. 55. 33. 12 Note: Outgoing Connections Allowed By Default 2. Establish Connection 3. TCP SYN Segment From: 60. 55. 33. 12: 62600 To: 123. 80. 5. 34: 80 Stateful Firewall External Webserver 123. 80. 5. 34 Connection Table Type Internal IP Internal Port External IP External Port Status TCP 60. 55. 33. 12 62600 123. 80. 5. 34 80 OK 4

Figure 5 -9: Stateful Inspection Firewall Operation I Internal Client PC 60. 55. 33. 12 6. TCP SYN/ACK Segment From: 123. 80. 5. 34: 80 To: 60. 55. 33. 12: 62600 Stateful 4. Firewall TCP SYN/ACK Segment External From: 123. 80. 5. 34: 80 Webserver To: 60. 55. 33. 12: 62600 123. 80. 5. 34 5. Check Connection OK Connection Table Type Internal IP Internal Port External IP External Port Status TCP 60. 55. 33. 12 62600 123. 80. 5. 34 80 OK 5

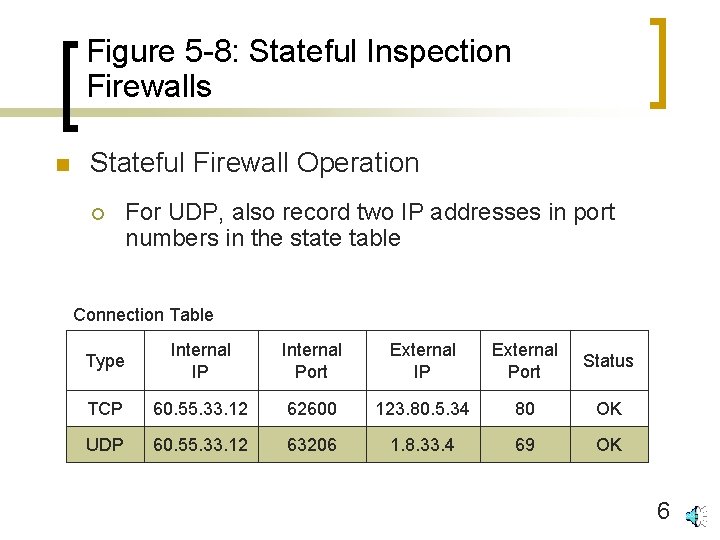
Figure 5 -8: Stateful Inspection Firewalls n Stateful Firewall Operation ¡ For UDP, also record two IP addresses in port numbers in the state table Connection Table Type Internal IP Internal Port External IP External Port Status TCP 60. 55. 33. 12 62600 123. 80. 5. 34 80 OK UDP 60. 55. 33. 12 63206 1. 8. 33. 4 69 OK 6

Figure 5 -8: Stateful Inspection Firewalls n Static Packet Filter Firewalls are Stateless ¡ Filter one packet at a time, in isolation ¡ If a TCP SYN/ACK segment is sent, cannot tell if there was a previous SYN to open a connection ¡ But stateful firewalls can (Figure 5 -10) 7

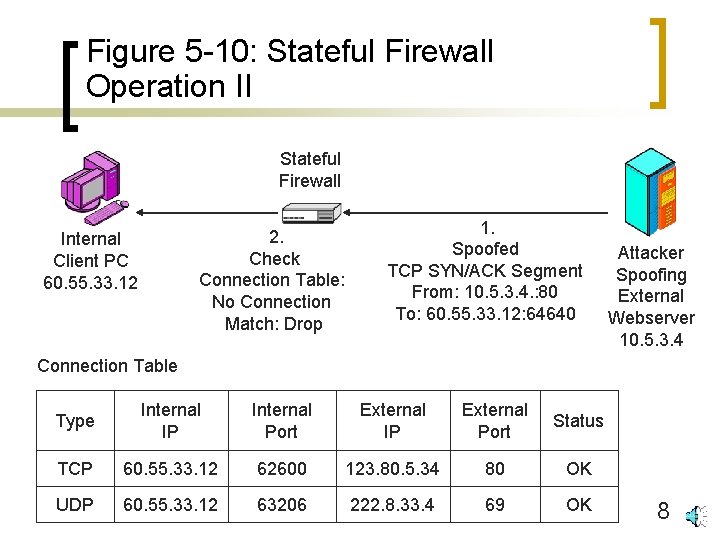
Figure 5 -10: Stateful Firewall Operation II Stateful Firewall 2. Check Connection Table: No Connection Match: Drop Internal Client PC 60. 55. 33. 12 1. Spoofed TCP SYN/ACK Segment From: 10. 5. 3. 4. : 80 To: 60. 55. 33. 12: 64640 Attacker Spoofing External Webserver 10. 5. 3. 4 Connection Table Type Internal IP Internal Port External IP External Port Status TCP 60. 55. 33. 12 62600 123. 80. 5. 34 80 OK UDP 60. 55. 33. 12 63206 222. 8. 33. 4 69 OK 8

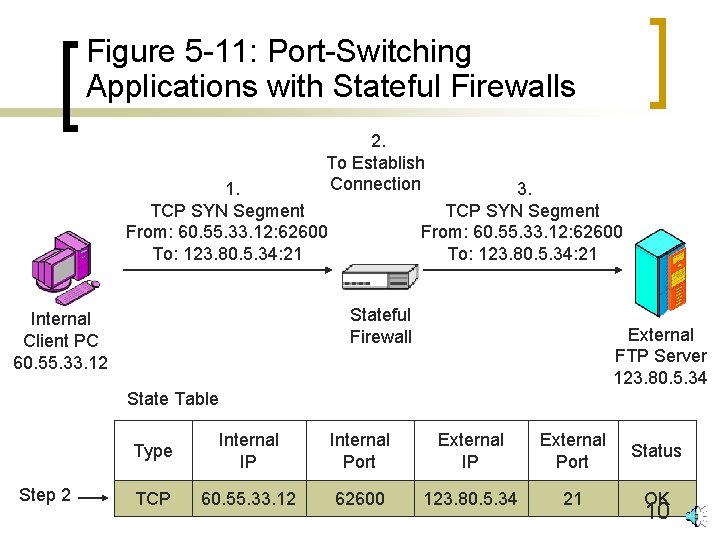
Figure 5 -8: Stateful Inspection Firewalls n Static Packet Filter Firewalls are Stateless ¡ Filter one packet at a time, in isolation ¡ Cannot deal with port-switching applications ¡ But stateful firewalls can (Figure 5 -11) 9

Figure 5 -11: Port-Switching Applications with Stateful Firewalls 2. To Establish Connection 1. TCP SYN Segment From: 60. 55. 33. 12: 62600 To: 123. 80. 5. 34: 21 3. TCP SYN Segment From: 60. 55. 33. 12: 62600 To: 123. 80. 5. 34: 21 Stateful Firewall Internal Client PC 60. 55. 33. 12 External FTP Server 123. 80. 5. 34 State Table Step 2 Type Internal IP Internal Port External IP External Port Status TCP 60. 55. 33. 12 62600 123. 80. 5. 34 21 OK 10

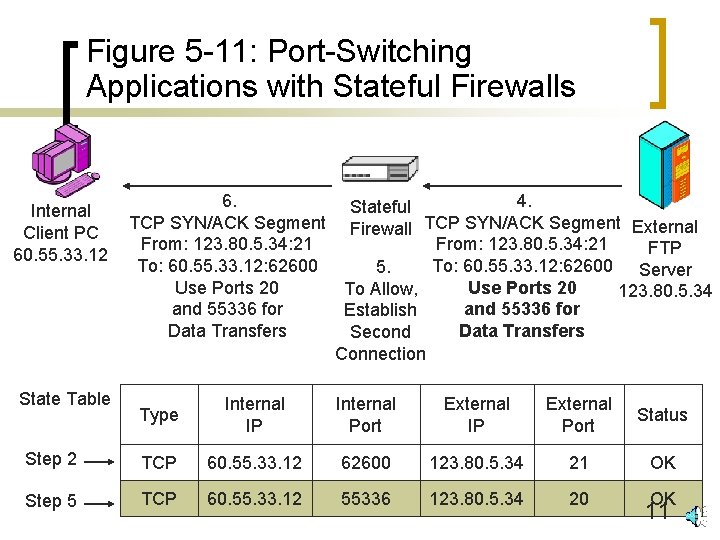
Figure 5 -11: Port-Switching Applications with Stateful Firewalls Internal Client PC 60. 55. 33. 12 State Table 6. TCP SYN/ACK Segment From: 123. 80. 5. 34: 21 To: 60. 55. 33. 12: 62600 Use Ports 20 and 55336 for Data Transfers 4. Stateful Firewall TCP SYN/ACK Segment External From: 123. 80. 5. 34: 21 FTP To: 60. 55. 33. 12: 62600 Server 5. Use Ports 20 To Allow, 123. 80. 5. 34 and 55336 for Establish Data Transfers Second Connection Type Internal IP Internal Port External IP External Port Status Step 2 TCP 60. 55. 33. 12 62600 123. 80. 5. 34 21 OK Step 5 TCP 60. 55. 33. 12 55336 123. 80. 5. 34 20 11 OK

Figure 5 -8: Stateful Inspection Firewalls n Stateful Inspection Access Control Lists (ACLs) ¡ Primary allow or deny applications ¡ Simple because probing attacks that are not part of conversations do not need specific rules because they are dropped automatically ¡ In integrated firewalls, ACL rules can specify that messages using a particular application protocol or server be authenticated or passed to an application firewall for inspection 12
 Types of firewalls ppt
Types of firewalls ppt Usability inspection methods
Usability inspection methods History of firewalls
History of firewalls Introduction to firewall
Introduction to firewall Screened subnet firewall adalah
Screened subnet firewall adalah List the design goals of firewalls
List the design goals of firewalls Linux firewalls
Linux firewalls Firewalls and intrusion detection systems
Firewalls and intrusion detection systems Firewalls are used for what security principle
Firewalls are used for what security principle Open source firewalls
Open source firewalls Dynamic firewalls
Dynamic firewalls Perimeter firewalls are the simplest type of firewall
Perimeter firewalls are the simplest type of firewall Auditing firewalls
Auditing firewalls