Firewalls n Types of Firewalls n Inspection Methods





- Slides: 8

Firewalls n Types of Firewalls n Inspection Methods n Firewall Architecture n Configuring, Testing, and Maintenance 1

Figure 5 -22: Configuring, Testing, and Maintaining Firewalls n Firewall Misconfiguration is a Serious Problem ¡ ACL rules must be executed in series ¡ Easy to make misordering problems ¡ Easy to make syntax errors 2

Figure 5 -22: Configuring, Testing, and Maintaining Firewalls n Create Policies Before ACLs ¡ Policies are easier to read than ACLs ¡ Can be reviewed by others more easily than ACLs ¡ Policies drive ACL development ¡ Policies also drive testing 3

Figure 5 -22: Configuring, Testing, and Maintaining Firewalls n n Must test Firewalls with Security Audits ¡ Only way to tell if policies are being supported ¡ Must be driven by policies Maintaining Firewalls ¡ New threats appear constantly ¡ ACLs must be updated constantly if firewall is to be effective 4

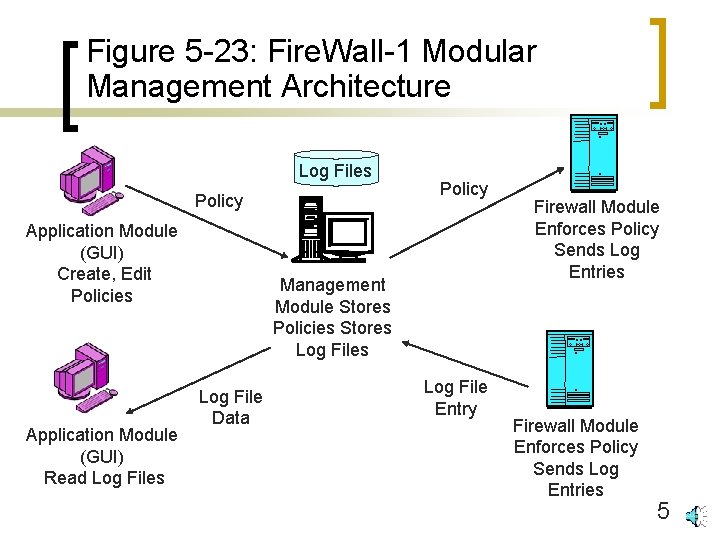
Figure 5 -23: Fire. Wall-1 Modular Management Architecture Log Files Policy Application Module (GUI) Create, Edit Policies Application Module (GUI) Read Log Files Policy Management Module Stores Policies Stores Log File Data Log File Entry Firewall Module Enforces Policy Sends Log Entries 5

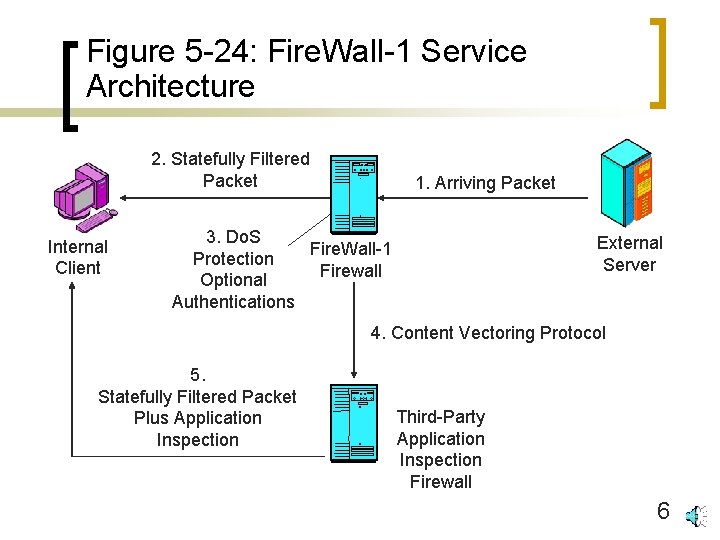
Figure 5 -24: Fire. Wall-1 Service Architecture 2. Statefully Filtered Packet Internal Client 1. Arriving Packet 3. Do. S Fire. Wall-1 Protection Firewall Optional Authentications External Server 4. Content Vectoring Protocol 5. Statefully Filtered Packet Plus Application Inspection Third-Party Application Inspection Firewall 6

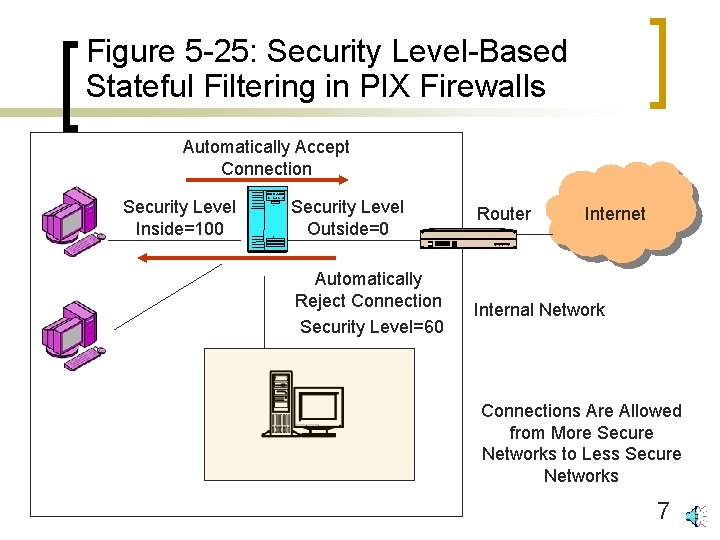
Figure 5 -25: Security Level-Based Stateful Filtering in PIX Firewalls Automatically Accept Connection Security Level Inside=100 Security Level Outside=0 Router Automatically Reject Connection Security Level=60 Internal Network Internet Connections Are Allowed from More Secure Networks to Less Secure Networks 7

Figure 5 -21: Other Security Architecture Issues n Host and Application Security (Chapters 6 and 9) n Antivirus Protection (Chapter 4) n Intrusion Detection Systems (Chapter 10) n Virtual Private Networks (Chapter 8) n Policy Enforcement System 8