Efficient Protection Against Inherent IT Risks Targeted Attacks



- Slides: 13

Efficient Protection Against Inherent IT Risks & Targeted Attacks Insert Speaker Name Insert Speaker Title Symantec Protection Center Overview 1

Disclaimer “This information is about pre-release software. Any unreleased update to the product or other planned modification is subject to ongoing evaluation by Symantec and therefore subject to change. This information is provided without warranty of any kind, express or implied. Customers who purchase Symantec products should make their purchase decision based upon features that are currently available. ” Symantec Protection Center Overview 2

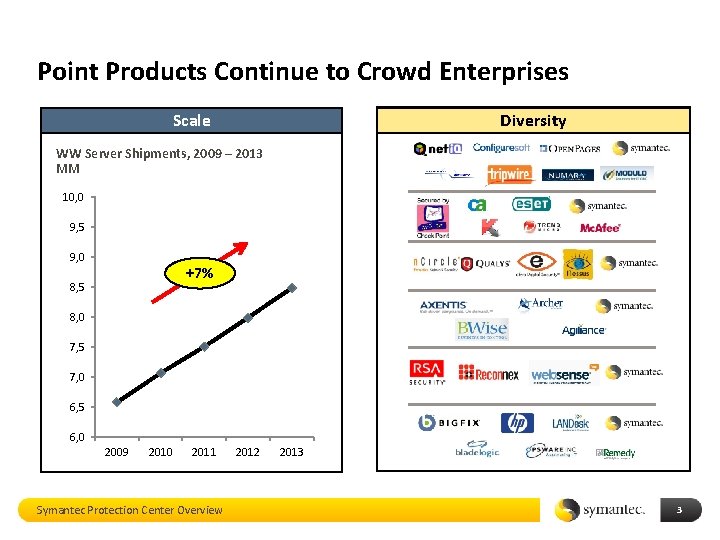
Point Products Continue to Crowd Enterprises Scale Diversity WW Server Shipments, 2009 – 2013 MM 10, 0 9, 5 9, 0 +7% 8, 5 8, 0 7, 5 7, 0 6, 5 6, 0 2009 2010 2011 Symantec Protection Center Overview 2012 2013 3

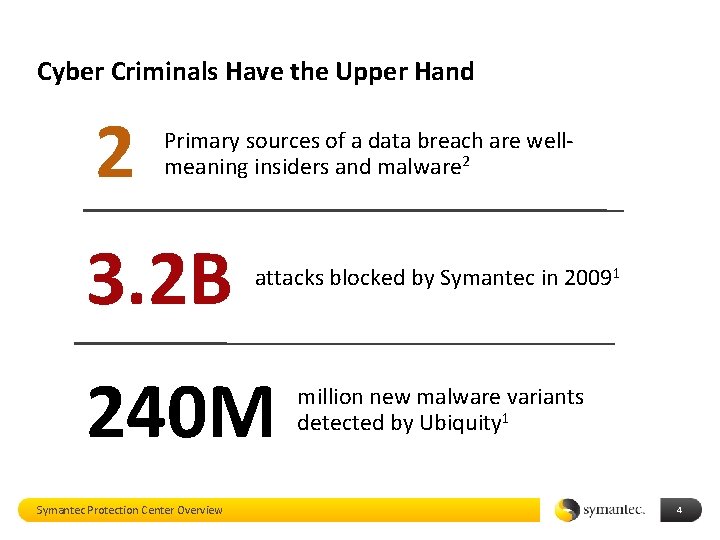
Cyber Criminals Have the Upper Hand 2 Primary sources of a data breach are wellmeaning insiders and malware 2 3. 2 B attacks blocked by Symantec in 20091 240 M Symantec Protection Center Overview million new malware variants detected by Ubiquity 1 4

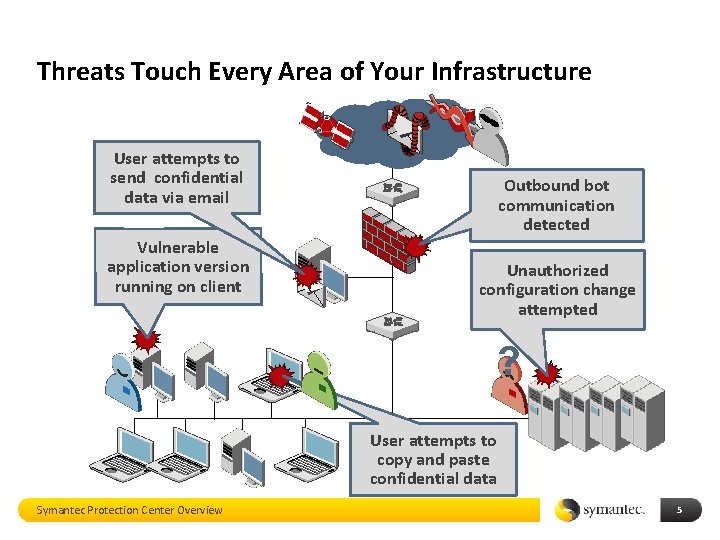
Threats Touch Every Area of Your Infrastructure User attempts to send confidential data via email Vulnerable application version running on client Outbound bot communication detected Unauthorized configuration change attempted ? User attempts to copy and paste confidential data Symantec Protection Center Overview 5

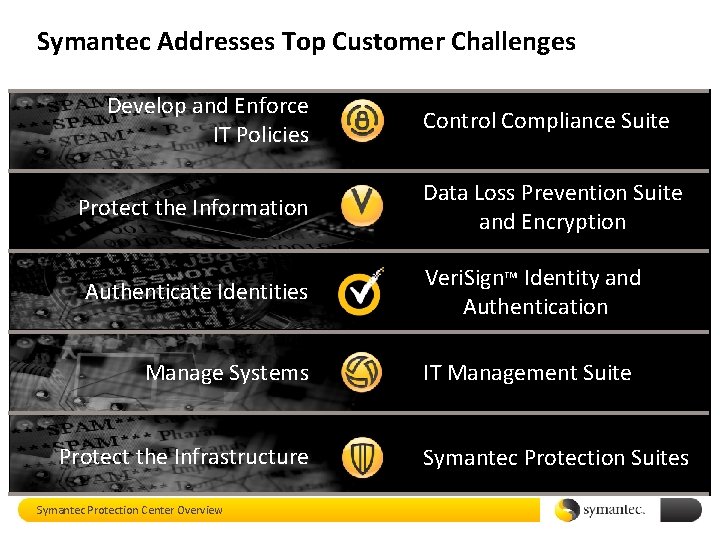
Symantec Addresses Top Customer Challenges Develop and Enforce IT Policies Protect the Information Authenticate Identities Manage Systems Protect the Infrastructure Symantec Protection Center Overview Control Compliance Suite Data Loss Prevention Suite and Encryption Veri. Sign™ Identity and Authentication IT Management Suite Symantec Protection Suites

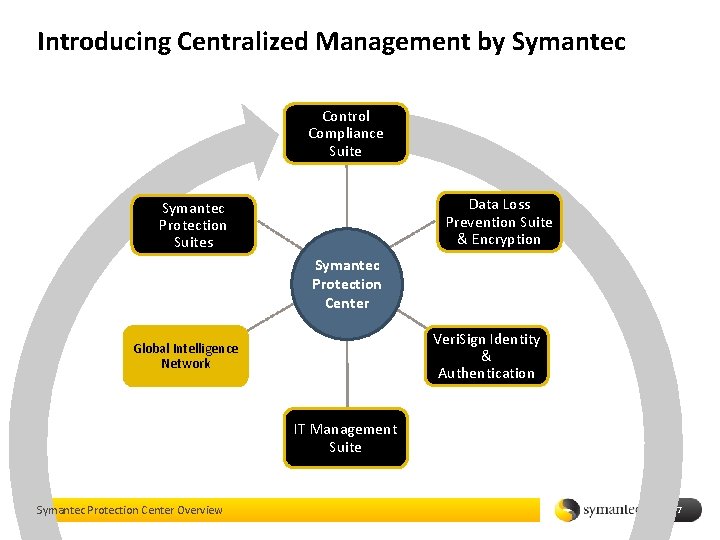
Introducing Centralized Management by Symantec Control Compliance Suite Data Loss Prevention Suite & Encryption Symantec Protection Suites Symantec Protection Center Veri. Sign Identity & Authentication Global Intelligence Network IT Management Suite Symantec Protection Center Overview 7

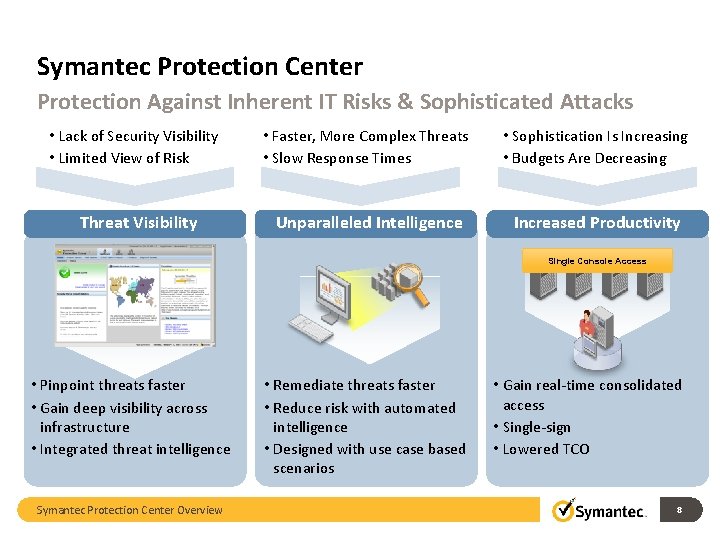
Symantec Protection Center Protection Against Inherent IT Risks & Sophisticated Attacks • Lack of Security Visibility • Limited View of Risk Threat Visibility • Faster, More Complex Threats • Slow Response Times • Sophistication Is Increasing • Budgets Are Decreasing Unparalleled Intelligence Increased Productivity Single Console Access • Pinpoint threats faster • Gain deep visibility across infrastructure • Integrated threat intelligence Symantec Protection Center Overview • Remediate threats faster • Reduce risk with automated intelligence • Designed with use case based scenarios • Gain real-time consolidated access • Single-sign • Lowered TCO 8

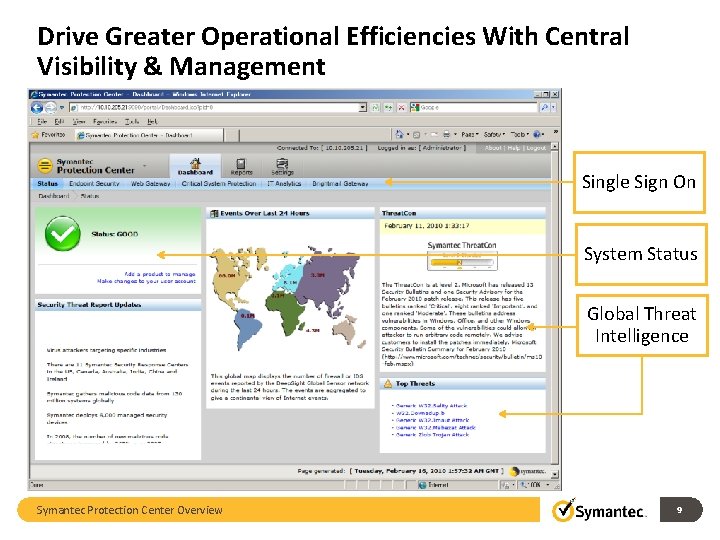
Drive Greater Operational Efficiencies With Central Visibility & Management Single Sign On System Status Global Threat Intelligence Symantec Protection Center Overview 9

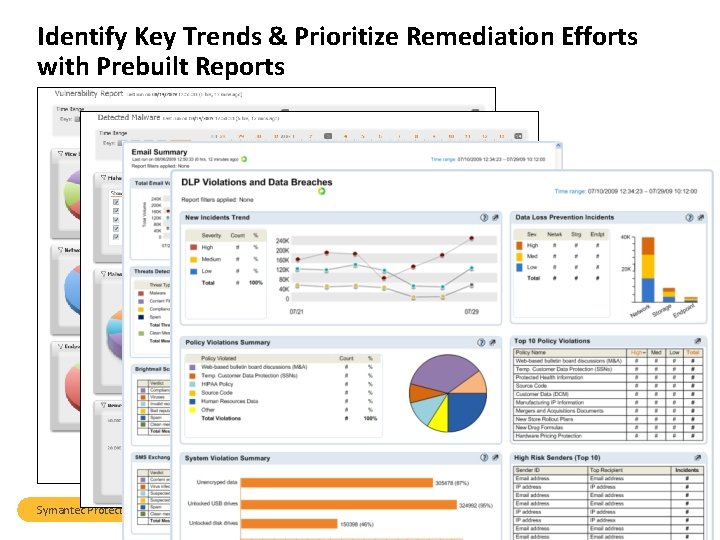
Identify Key Trends & Prioritize Remediation Efforts with Prebuilt Reports Symantec Protection Center Overview 10

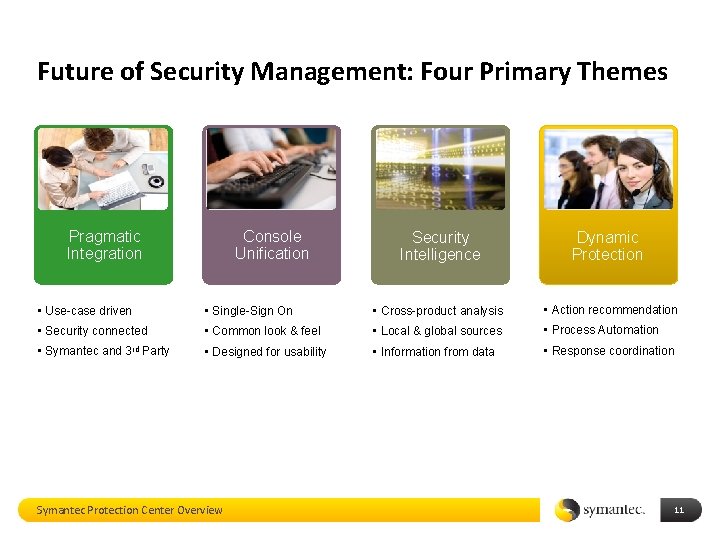
Future of Security Management: Four Primary Themes Console Unification Pragmatic Integration Security Intelligence Dynamic Protection • Use-case driven • Single-Sign On • Cross-product analysis • Action recommendation • Security connected • Common look & feel • Local & global sources • Process Automation • Symantec and 3 rd Party • Designed for usability • Information from data • Response coordination Symantec Protection Center Overview 11

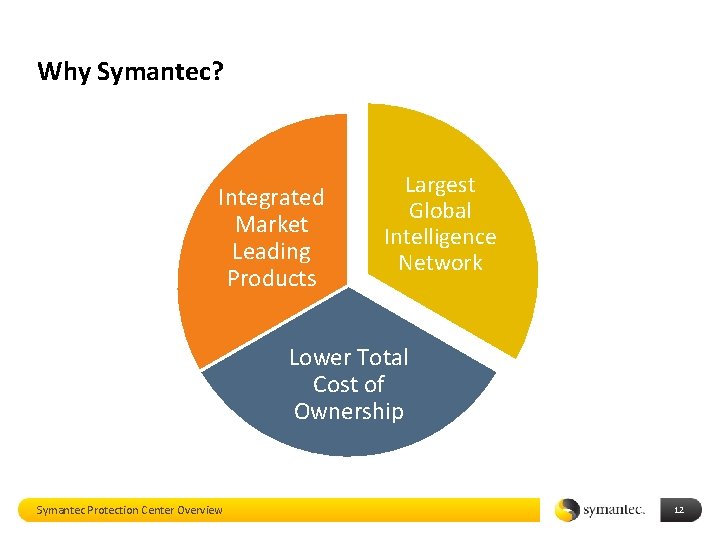
Why Symantec? Integrated Market Leading Products Largest Global Intelligence Network Lower Total Cost of Ownership Symantec Protection Center Overview 12

Thank you! Insert Speaker Name Copyright © 2010 Symantec Corporation. All rights reserved. Symantec and the Symantec Logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U. S. and other countries. Other names may be trademarks of their respective owners. This document is provided for informational purposes only and is not intended as advertising. All warranties relating to the information in this document, either express or implied, are disclaimed to the maximum extent allowed by law. The information in this document is subject to change without notice. Symantec Protection Center Overview 13