Automatic and Precise ClientSide Protection against CSRF Attacks









- Slides: 30

Automatic and Precise Client-Side Protection against CSRF Attacks Philippe De Ryck, Lieven Desmet, Wouter Joosen, Frank Piessens Philippe. De. Ryck@cs. kuleuven. be Distri. Net

Outline Cross-site Request Forgery (CSRF) Client-side Protection against CSRF Client-Side Request Filtering Policy Formal Evaluation Practical Evaluation Conclusion 18/09/2020 Distri. Net 2

Cross-Site Request Forgery 18/09/2020 Distri. Net 3

Cross-site Request Forgery can be used to … take over your blog modify your You. Tube account obtain your email address steal your money W. Zeller and E. Felten, Cross-site Request Forgeries: Distri. Net Exploitation and Prevention, Technical Report, October 2008 18/09/2020 4

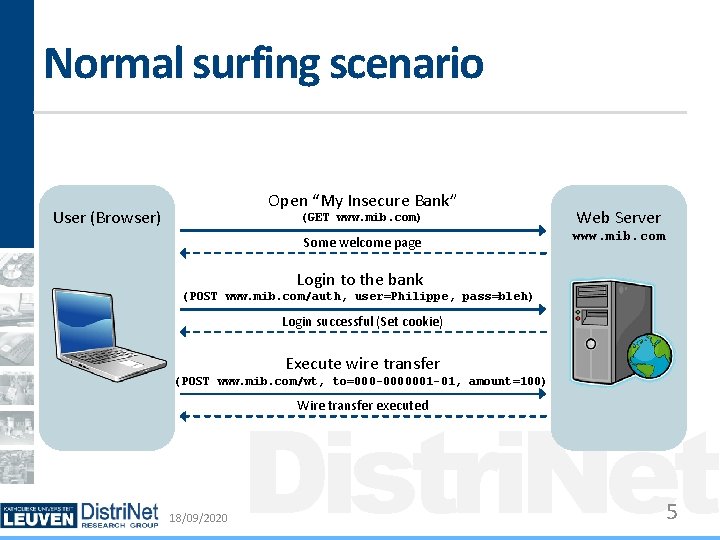
Normal surfing scenario Open “My Insecure Bank” User (Browser) (GET www. mib. com) Web Server Some welcome page www. mib. com Login to the bank (POST www. mib. com/auth, user=Philippe, pass=bleh) Login successful (Set cookie) Execute wire transfer (POST www. mib. com/wt, to=000 -0000001 -01, amount=100) Distri. Net Wire transfer executed 18/09/2020 5

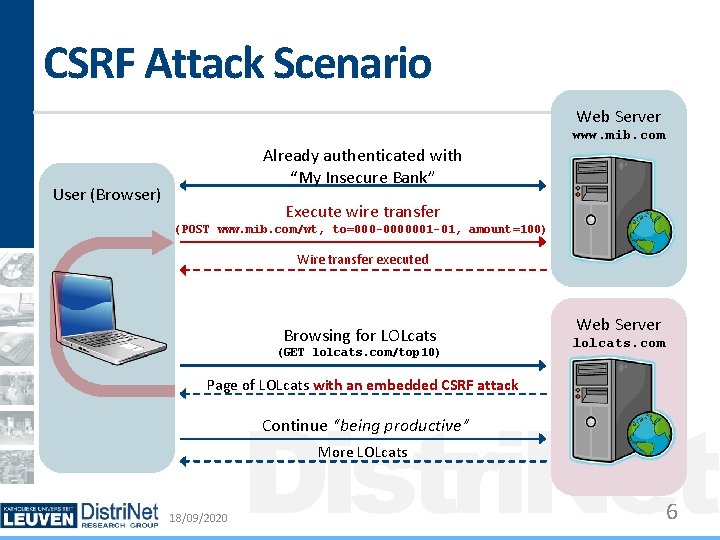
CSRF Attack Scenario Web Server www. mib. com Already authenticated with “My Insecure Bank” User (Browser) Execute wire transfer (POST www. mib. com/wt, to=000 -0000001 -01, amount=100) Wire transfer executed Browsing for LOLcats (GET lolcats. com/top 10) Web Server lolcats. com Page of LOLcats with an embedded CSRF attack Distri. Net Continue “being productive” More LOLcats 18/09/2020 6

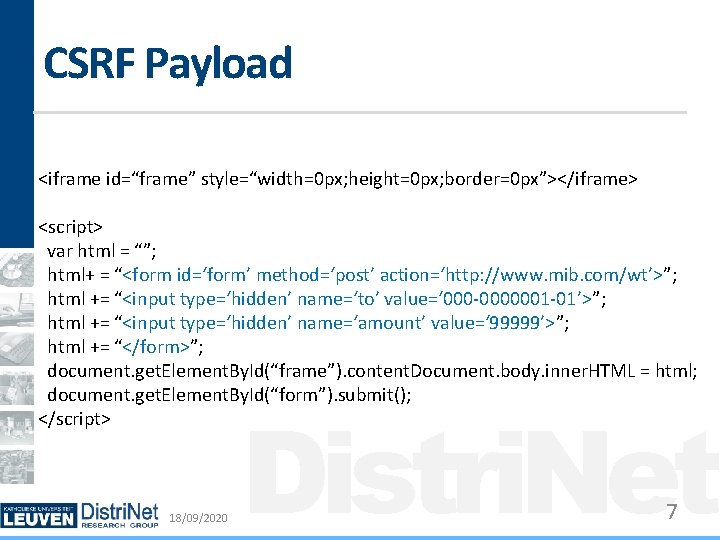
CSRF Payload <iframe id=“frame” style=“width=0 px; height=0 px; border=0 px”></iframe> <script> var html = “”; html+ = “<form id=‘form’ method=‘post’ action=‘http: //www. mib. com/wt’>”; html += “<input type=‘hidden’ name=‘to’ value=‘ 000 -0000001 -01’>”; html += “<input type=‘hidden’ name=‘amount’ value=‘ 99999’>”; html += “</form>”; document. get. Element. By. Id(“frame”). content. Document. body. inner. HTML = html; document. get. Element. By. Id(“form”). submit(); </script> 18/09/2020 Distri. Net 7

Client-Side Protection against CSRF 18/09/2020 Distri. Net 8

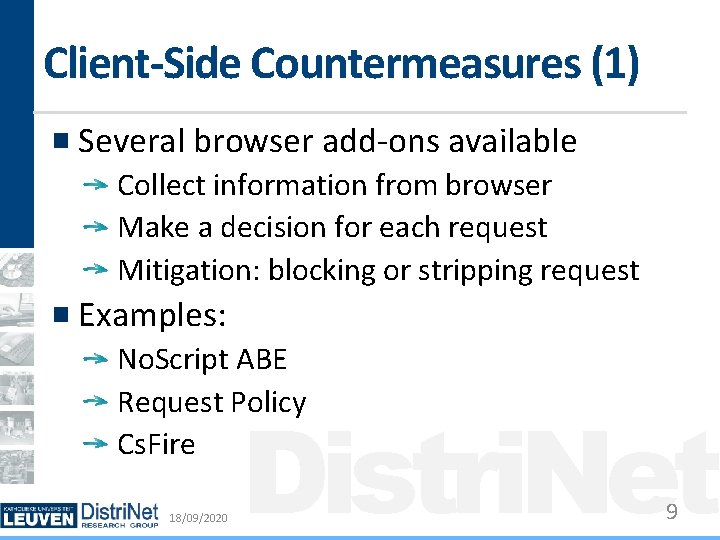
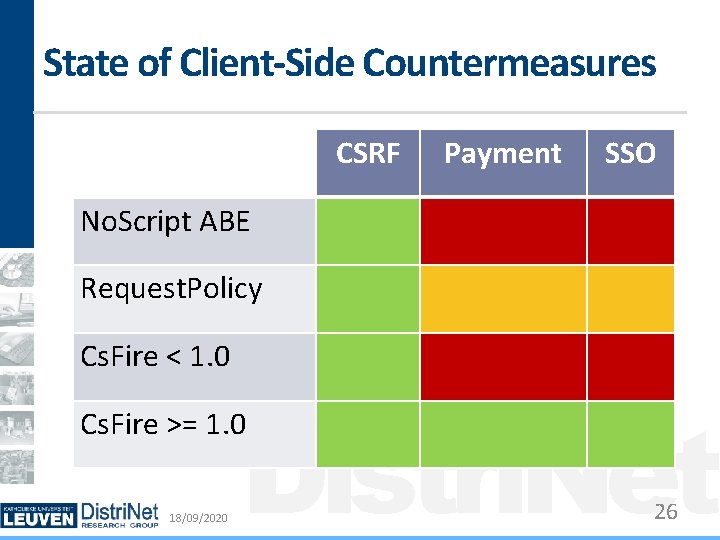
Client-Side Countermeasures (1) Several browser add-ons available Collect information from browser Make a decision for each request Mitigation: blocking or stripping request Examples: No. Script ABE Request Policy Cs. Fire 18/09/2020 Distri. Net 9

Client-Side Countermeasures (2) Current client-side countermeasures Affect each cross-origin request Very secure Negative impact on usability Experience from Cs. Fire (33, 000+ downloads) Limited impact on usability A few cross-origin scenarios break Currently addressed by central/local policies 18/09/2020 Distri. Net 10

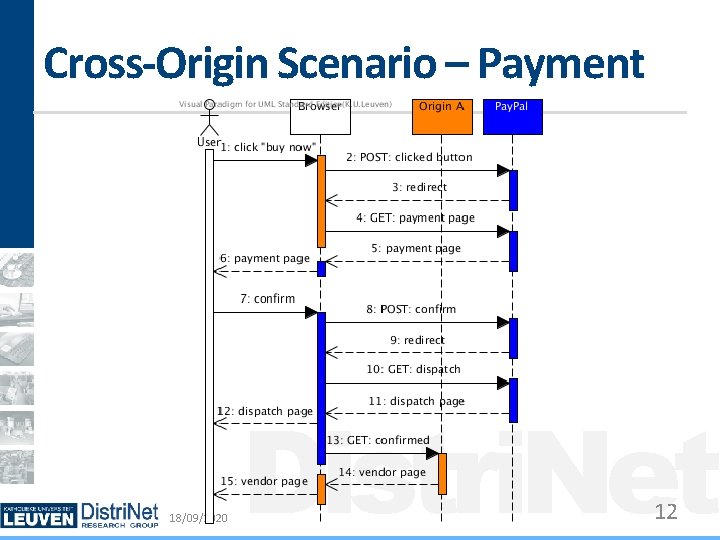
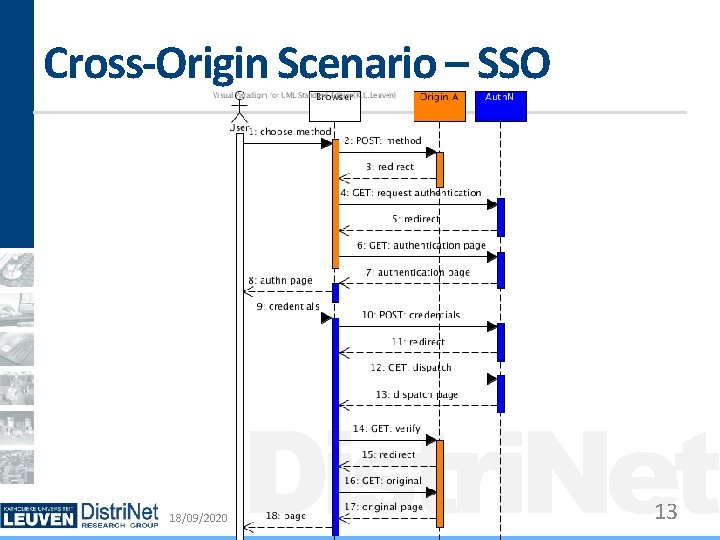
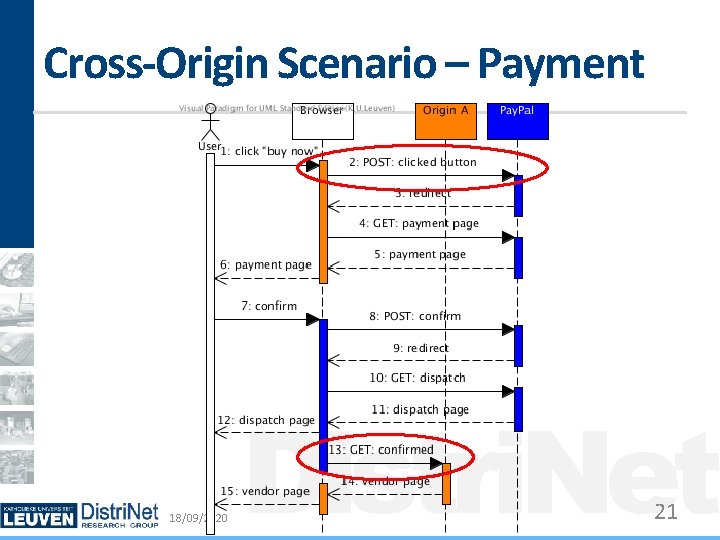
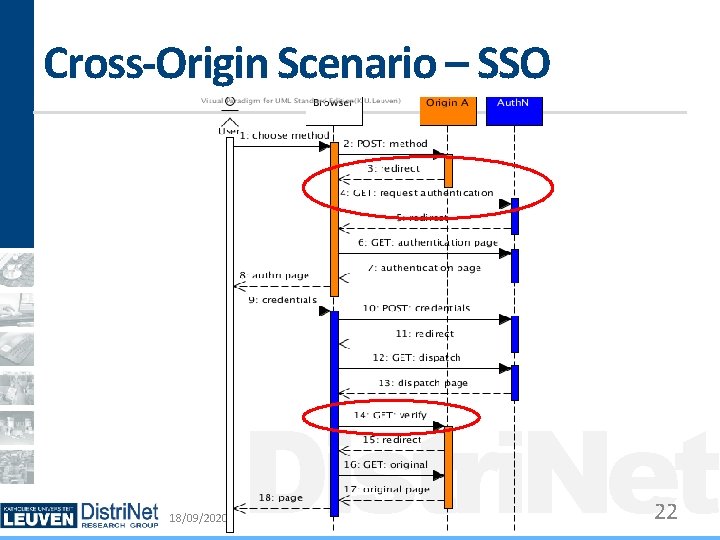
Cross-Origin Scenarios Examples: Payment Providers, Single sign-on Hard to distinguish Often look like CSRF attacks Intention of user/site is unknown Current status Broken by all client-side countermeasures Can be addressed using specific policy rules 18/09/2020 Distri. Net 11

Cross-Origin Scenario – Payment 18/09/2020 Distri. Net 12

Cross-Origin Scenario – SSO 18/09/2020 Distri. Net 13

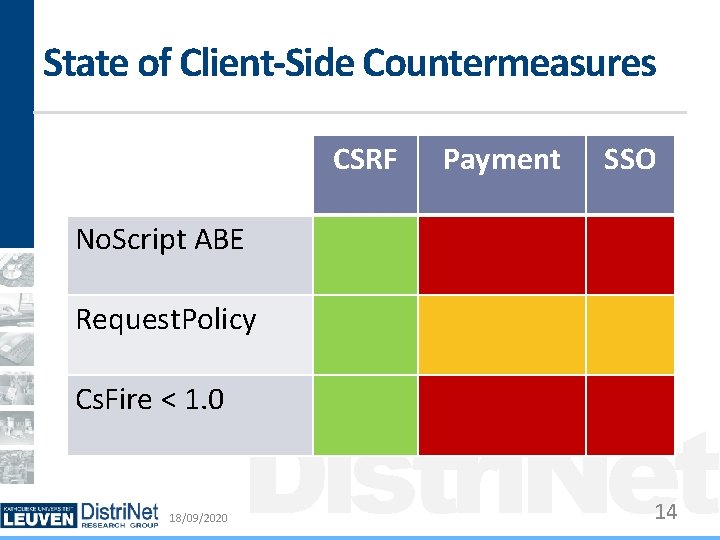
State of Client-Side Countermeasures CSRF Payment SSO No. Script ABE Request. Policy Cs. Fire < 1. 0 18/09/2020 Distri. Net 14

Client-side Request Filtering 18/09/2020 Distri. Net 15

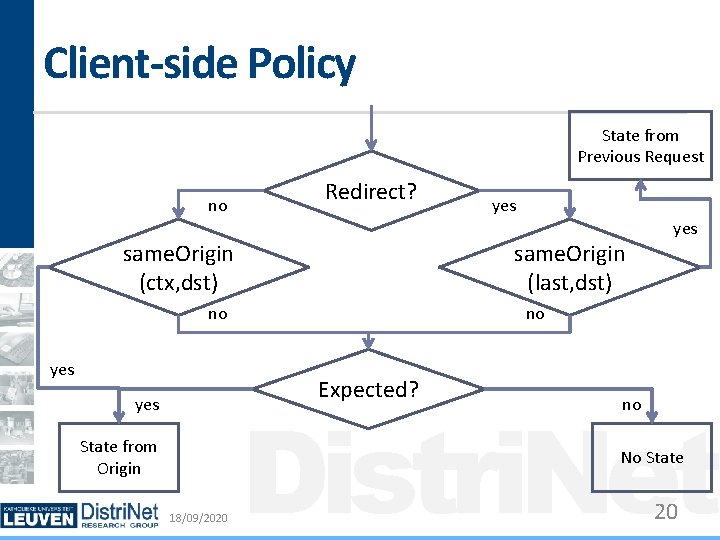
Idea behind the Client-side Policy Site A can delegate control to site B E. g. when B is a payment provider When B is finished, control is transferred back to A E. g. when the payment is complete and A needs to complete the transaction Distri. Net Detect delegation to B and allow B to return to A 18/09/2020 16

Idea behind the Client-side Policy (2) Strip all cross-origin requests unless it is an expected request A request from B to A is expected if A previously delegated to B Delegation from A to B occurs if A issues a POST request to B or if A redirects to B using a parametrized URI 18/09/2020 Distri. Net 17

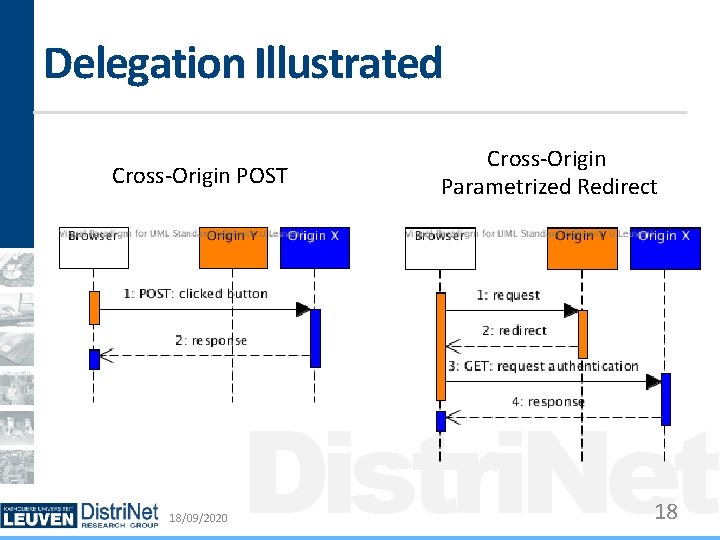
Delegation Illustrated Cross-Origin POST 18/09/2020 Cross-Origin Parametrized Redirect Distri. Net 18

Assumption of Delegation Can an attacker delegate control? POST request • By form submission or using XHR • Requires script injection (which trumps CSRF) Parametrized Redirect • By injecting server-side code (total compromise) • Using an open redirect (direct attack possible, so no Distri. Net point in using a delegation and expected request) Limit expected requests to single GET 18/09/2020 19

Client-side Policy State from Previous Request no Redirect? same. Origin (ctx, dst) same. Origin (last, dst) no yes State from Origin yes no Expected? yes Distri. Net no No State 18/09/2020 20

Cross-Origin Scenario – Payment 18/09/2020 Distri. Net 21

Cross-Origin Scenario – SSO 18/09/2020 Distri. Net 22

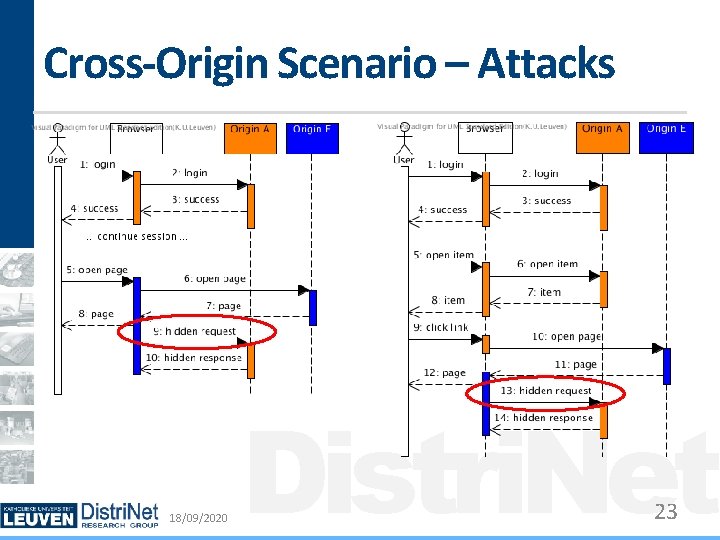
Cross-Origin Scenario – Attacks 18/09/2020 Distri. Net 23

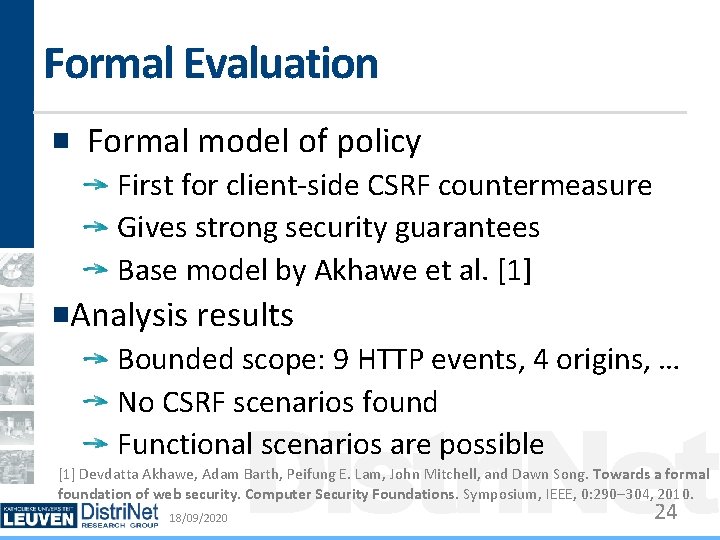
Formal Evaluation Formal model of policy First for client-side CSRF countermeasure Gives strong security guarantees Base model by Akhawe et al. [1] Analysis results Bounded scope: 9 HTTP events, 4 origins, … No CSRF scenarios found Functional scenarios are possible Distri. Net [1] Devdatta Akhawe, Adam Barth, Peifung E. Lam, John Mitchell, and Dawn Song. Towards a formal foundation of web security. Computer Security Foundations. Symposium, IEEE, 0: 290– 304, 2010. 18/09/2020 24

Practical Evaluation Implementation as extension of Cs. Fire Tested against benchmark of CSRF scenarios • Different attack vectors: HTML, CSS, JS, redirect, … Tested on real-life functional scenarios 18/09/2020 Distri. Net 25

State of Client-Side Countermeasures CSRF Payment SSO No. Script ABE Request. Policy Cs. Fire < 1. 0 Distri. Net Cs. Fire >= 1. 0 18/09/2020 26

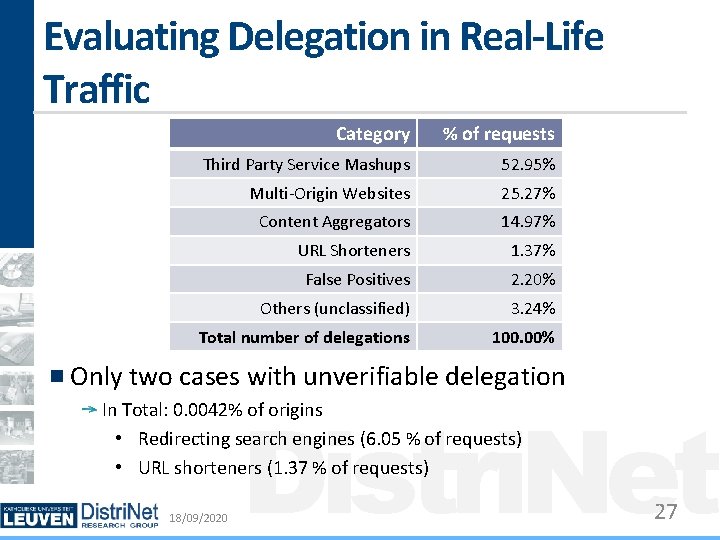
Evaluating Delegation in Real-Life Traffic Category % of requests Third Party Service Mashups 52. 95% Multi-Origin Websites 25. 27% Content Aggregators 14. 97% URL Shorteners 1. 37% False Positives 2. 20% Others (unclassified) 3. 24% Total number of delegations 100. 00% Only two cases with unverifiable delegation Distri. Net In Total: 0. 0042% of origins • Redirecting search engines (6. 05 % of requests) • URL shorteners (1. 37 % of requests) 18/09/2020 27

Conclusion 18/09/2020 Distri. Net 28

Conclusion Client-side CSRF countermeasure Improved balance usability and security Support for cross-origin collaborations Formal evaluation of the policy Delegation between sites Experimentally evaluated Minor compromise on security 18/09/2020 Distri. Net 29

Cs. Fire – Mozilla Add-Ons 18/09/2020 Distri. Net 30