doc IEEE 802 22 080083 r 01 Month

- Slides: 17

doc. : IEEE 802. 22 -08/0083 r 01 Month Year Security and the Protocol Reference Model Enhancements in IEEE 802. 22 Authors: IEEE P 802. 22 Wireless RANs Date: 2008 -05 -09 Notice: This document has been prepared to assist IEEE 802. 22. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) reserve(s) the right to add, amend or withdraw material contained herein. Release: The contributor grants a free, irrevocable license to the IEEE to incorporate material contained in this contribution, and any modifications thereof, in the creation of an IEEE Standards publication; to copyright in the IEEE’s name any IEEE Standards publication even though it may include portions of this contribution; and at the IEEE’s sole discretion to permit others to reproduce in whole or in part the resulting IEEE Standards publication. The contributor also acknowledges and accepts that this contribution may be made public by IEEE 802. 22. Patent Policy and Procedures: The contributor is familiar with the IEEE 802 Patent Policy and Procedures http: //standards. ieee. org/guides/bylaws/sb-bylaws. pdf including the statement "IEEE standards may include the known use of patent(s), including patent applications, provided the IEEE receives assurance from the patent holder or applicant with respect to patents essential for compliance with both mandatory and optional portions of the standard. " Early disclosure to the Working Group of patent information that might be relevant to the standard is essential to reduce the possibility for delays in the development process and increase the likelihood that the draft publication will be approved for publication. Please notify the Chair Carl R. Stevenson as early as possible, in written or electronic form, if patented technology (or technology under patent application) might be incorporated into a draft standard being developed within the IEEE 802. 22 Working Group. If you have questions, contact the IEEE Patent Committee Administrator at patcom@iee. org. Submission 1 John Doe, Some Company

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Abstract • This presentation focuses on Protocol Reference Model (PRM) and Security enhancements in 802. 22 • The Spectrum Manager in the current PRM (802. 22_Draftv 1. 0) resides in the MLME. However, the MLME falls outside the scope of the standard and as a result so does the Spectrum Manager • The current 802. 22 draft does not specify where the Security Sublayer resides and what its functions should be. Also, no security mechanisms are provided to authenticate the sensing and geolocation information as well as the information coming from the incumbent database. • Inadequate security features may expose wireless networks to be misused by anti-social elements and terrorists, resulting in Denial of Service attacks and Information Operations. • IEEE 802. 22 based networks are even more susceptible since they are likely to operate in un-licensed bands with cognitive radio techniques. • Hence, in order to overcome the shortfalls mentioned above, we propose a Modification to the PRM which separates the Cognitive Plane from the Data, Control and Management planes, allowing functionality specific attributes to be defined for each plane. • The Data/ Control and Management Plane functionality remains unchanged. • The Cognitive Plane consists of the Spectrum Sensing Function, the Geolocation function and the Spectrum Manager / Spectrum Automaton. • We suggest security feature enhancements for the Cognitive Plane, as well as some additional features which are based on the new 802. 16 m SDD call for proposals Submission 2 Apurva N. Mody, BAE Systems

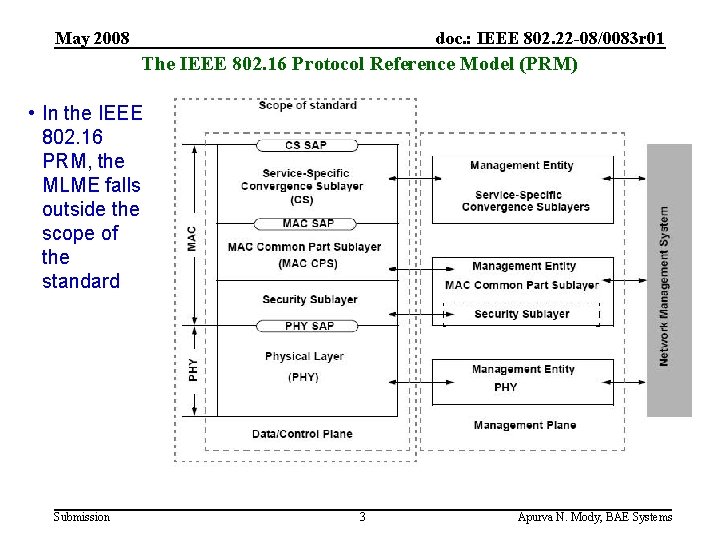
May 2008 doc. : IEEE 802. 22 -08/0083 r 01 The IEEE 802. 16 Protocol Reference Model (PRM) • In the IEEE 802. 16 PRM, the MLME falls outside the scope of the standard Submission 3 Apurva N. Mody, BAE Systems

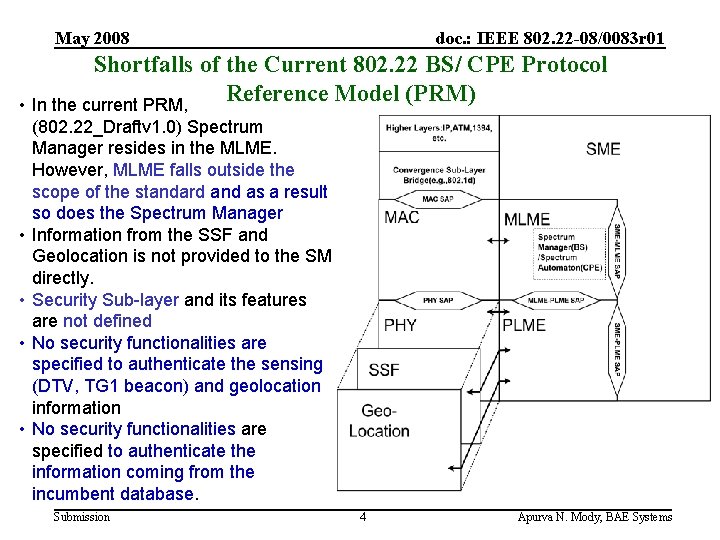
May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Shortfalls of the Current 802. 22 BS/ CPE Protocol Reference Model (PRM) • In the current PRM, • • (802. 22_Draftv 1. 0) Spectrum Manager resides in the MLME. However, MLME falls outside the scope of the standard and as a result so does the Spectrum Manager Information from the SSF and Geolocation is not provided to the SM directly. Security Sub-layer and its features are not defined No security functionalities are specified to authenticate the sensing (DTV, TG 1 beacon) and geolocation information No security functionalities are specified to authenticate the information coming from the incumbent database. Submission 4 Apurva N. Mody, BAE Systems

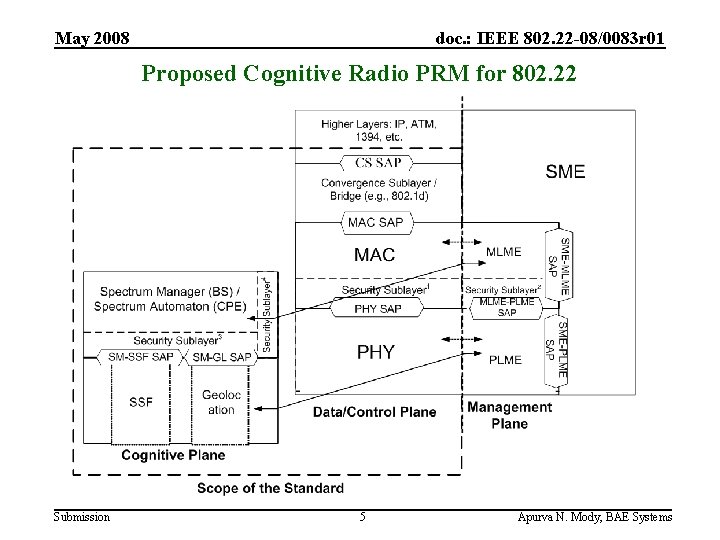
May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Proposed Cognitive Radio PRM for 802. 22 Submission 5 Apurva N. Mody, BAE Systems

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Features of the Proposed Cognitive Radio PRM for 802. 22 • Separates the Cognitive Plane from the Data, Control and Management planes, allowing functionality specific attributes to be defined for each plane. • The Data/ Control and Management Plane functionality remains unchanged. • The Cognitive Plane consists of the Spectrum Sensing Function, the Geolocation function and the Spectrum Manager / Spectrum Automaton. • Spectrum Manager resides in the Cognitive Plane at the same layer as the MAC in the Data/ Control Plane. • Spectrum manager interfaces directly with the Spectrum Sensing and the Geolocation functions. • Modular security features may be added to protect the data, authenticate the sensing and geo-location information, as well as authenticate the information coming from the incumbent database. Submission 6 Apurva N. Mody, BAE Systems

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Cognitive Radio Interface Diagram with Security Sub. Layer Modularization • A cognitive communications device must include security and authentication features for the Cognitive Plane, in addition to the Data and Control / Management Planes • A Cognitive Plane consists of the Spectrum Sensing Function, the Geolocation Function and the Spectrum Manager • The proposed PRM creates Four Security Sub-layers with dedicated and modular security functionality. The detailed functionality of each of the layers needs to be defined (Security Ad-Hoc) Submission 7 Apurva N. Mody, BAE Systems

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Suggested Security and Authentication Features for Spectrum Sensing – Authenticating the TV Signals • NTSC, ATSC DTV and DVB-T signals must be authenticated to avoid unwanted Denial of Service (Do. S) attacks • Authentication of the NTSC, ATSC DTV and DVB-T signals may be carried out using • Multiple sources for confirmation such as sensing and the incumbent database, and / or • Sensing using multiple cognitive devices and / or • Sensing for a long continuous period of time to ensure that the signal is indeed originating from a valid source. Submission 8 Apurva N. Mody, BAE Systems

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Suggested Security and Authentication Features for Spectrum Sensing – Authenticating Wireless Microphones and TG 1 Beacons • Signals originating Wireless Microphones and TG 1 Beacons must be authenticated to avoid unwanted Denial of Service (Do. S) attacks • Authentication of the SPDs such as wireless microphone signals may be carried out • At the Security Sub-layer in the Cognitive Plane using the security features embedded in the TG 1 beaconing signal • Multiple sources such as beacon sensing and the incumbent database, and / or • Beacon sensing using multiple cognitive devices and / or • Control information handshake between the cognitive device and the PPD / SPD / NPD. Submission 9 Apurva N. Mody, BAE Systems

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Suggested Security and Authentication Features for Spectrum Sensing – Authenticating WRAN Discovery • WRAN discovery must be authenticated using • Capture of a valid Superframe Control Header (SCH) • Three-way confirmation handshake with the WRAN that is currently occupying the current channel • Periodic updates and refresh to ensure continued usage • Local (country dependent) database Submission 10 Apurva N. Mody, BAE Systems

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Suggested Security and Authentication Features for Geolocation – Authenticating Geolocation Info. • The geolocation information must be authenticated for its validity. • The geolocation authentication may be device and / or algorithm dependent • The underlying signals used as a reference for geolocation must be authenticated. • Authentication features for both the Global Positioning System (GPS) based geolocation as well as other soft algorithms should be clearly defined in the standard. Submission 11 Apurva N. Mody, BAE Systems

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Suggested Security and Authentication Features between the Spectrum Manager – MAC Common Part Sublayer Interface • The interface diagram shows a modular format with the data / control plane and the cognitive plane. • The information provided to the SM from the incumbent database must be authenticated • The information provided by the spectrum manager to the MAC Common Part Sublayer must be authenticated and protected through various security and privacy features. • The sensing and geolocation information transmitted to various other devices in the network must be encrypted. Submission 12 Apurva N. Mody, BAE Systems

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Other Security, Authentication and Privacy Features Recommended for 802. 22 • Management message protection (encryption and integrity protection) • MAC header protection (encryption and integrity protection) • Key management enhancement with secure and efficient key establishments and distribution • Certificate revocation enhancement • Mitigations of network attacks including authentication attacks (BS and SS impersonations and passive eaves dropping attack), replay attacks (key reuse attack), denial of service (packet forgery), weak key attack, and manin-the-middle-attack Submission 13 Apurva N. Mody, BAE Systems

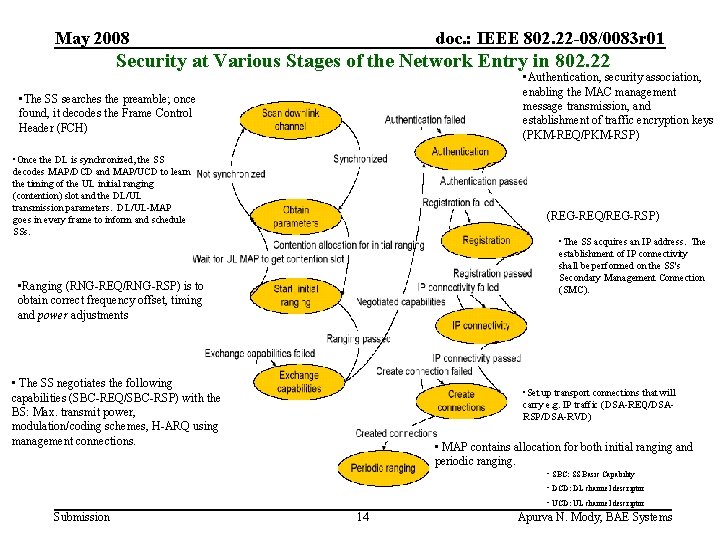
May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Security at Various Stages of the Network Entry in 802. 22 • Authentication, security association, enabling the MAC management message transmission, and establishment of traffic encryption keys (PKM-REQ/PKM-RSP) • The SS searches the preamble; once found, it decodes the Frame Control Header (FCH) • Once the DL is synchronized, the SS decodes MAP/DCD and MAP/UCD to learn the timing of the UL initial ranging (contention) slot and the DL/UL transmission parameters. DL/UL-MAP goes in every frame to inform and schedule SSs. (REG-REQ/REG-RSP) • The SS acquires an IP address. The establishment of IP connectivity shall be performed on the SS's Secondary Management Connection (SMC). • Ranging (RNG-REQ/RNG-RSP) is to obtain correct frequency offset, timing and power adjustments • The SS negotiates the following capabilities (SBC-REQ/SBC-RSP) with the BS: Max. transmit power, modulation/coding schemes, H-ARQ using management connections. • Set up transport connections that will carry e. g. IP traffic (DSA-REQ/DSARSP/DSA-RVD) • MAP contains allocation for both initial ranging and periodic ranging. • SBC: SS Basic Capability • DCD: DL channel descriptor • UCD: UL channel descriptor Submission 14 Apurva N. Mody, BAE Systems

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Security at Various Stages of the Network Entry in 802. 22 • MAP and FCH can be protected • This is optional • Use the pre-shared key (via vendor or user certificate) • Once the pre-shared key is installed, the user is able to scan the DL • If you do not do this step initially, follow 802. 22 default. • No need to protect RNG-REQ - Signatures may be used to protect malicious flooding attack • Need to protect RNG-RSP since the basic CID and primary management uniquely identify the station • No need to protect SBC-REQ - Signatures may be used to protect malicious flooding attack • Need to protect SBC-RSP since it carries basic CID • No change for authentication since the contents of PKM are protected • No change for registration since the contents of REG are protected • DSA messages are required for path set up and admission control • DSA messages can be protected • This is optional • The 802. 22 MAC header has only CRC – MAC headers need to be protected • Periodic ranging needs to be protected in the same manner as the initial ranging Submission 15 Apurva N. Mody, BAE Systems

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 Conclusions • This presentation focused on Protocol Reference Model (PRM) and Security enhancements in 802. 22 • The Spectrum Manager in the current PRM (802. 22_Draftv 1. 0) resides in the MLME. However, the MLME falls outside the scope of the standard and as a result so does the Spectrum Manager • The current 802. 22 draft does not specify where the Security Sublayer resides and what its functions should be. Also, no security mechanisms are provided to authenticate the sensing and geolocation information as well as the information coming from the incumbent database. • Inadequate security features may expose wireless networks to be misused by anti-social elements and terrorists, resulting in Denial of Service attacks and Information Operations. • IEEE 802. 22 based networks are even more susceptible since they are likely to operate in un -licensed bands with cognitive radio techniques. • Hence, in order to overcome the shortfalls mentioned above, we proposed a Modification to the PRM which separated the Cognitive Plane from the Data, Control and Management planes, allowing functionality specific attributes to be defined for each of the planes. • The Data/ Control and Management Plane functionality remained unchanged. • The Cognitive Plane consisted of the Spectrum Sensing Function, the Geolocation function and the Spectrum Manager / Spectrum Automaton. • We suggested security feature enhancements for the Cognitive Plane, as well as some additional features which are based on the new 802. 16 m SDD call for proposals Submission 16 Apurva N. Mody, BAE Systems

May 2008 doc. : IEEE 802. 22 -08/0083 r 01 References • WRAN Protocol Reference Model – Contribution 22 -07 -0523 -030000_WRAN_PRM. ppt • Security Enhancement for 802. 16 e - A SDD Proposal for 802. 16 m www. wirelessman. org/tgm/contrib/C 80216 m-08_046. doc Submission 17 Apurva N. Mody, BAE Systems