Comp Chall Addressing Password Guessing Attacks IAS ITCC2005











- Slides: 16

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Comp. Chall: Addressing Password Guessing Attacks By Vipul Goyal OSP Global Mumbai, India Coauthors: Virendra Kumar, Mayank Singh, Ajith Abraham and Sugata Sanyal 1

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Introduction • Passwords are the most widely used means of authentication • Humans have a tendency to choose relatively short and simple passwords • Thus, passwords bring along with them, the threat of dictionary attacks 2

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Dictionary attacks • Dictionary attack means guessing the password and somehow check whether it is valid or not • If the rate of guessing and validating is reasonably high, the attacker stands a good chance of breaking the password • Two types: offline and online 3

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Offline dictionary attacks • The attacker somehow gets access to some data which allow him to test passwords without any interaction with the server • Theoretically impossible to resist w/o PKC but efficient protocols like EKE exist to resist these attacks using PKC 4

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Online dictionary attacks • For each password validation, interaction with the server is required • By attempting a login, it is always possible to test for password validity and hence, these attacks cannot be totally prevented • Common countermeasures like account locking and delayed response are not satisfactory 5

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Our protocol • Limits the rate of login attempt by asking the user to first solve a computational challenge • Uses only fast one way hash functions for efficiency • Totally stateless and thus less vulnerable to Do. S attacks 6

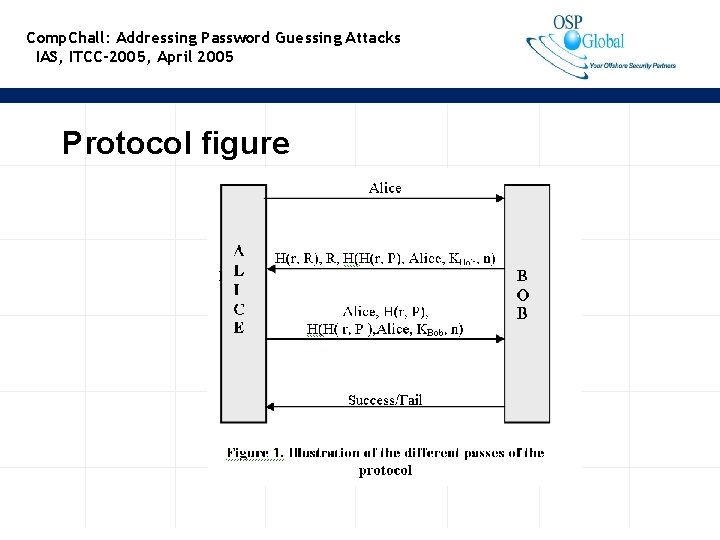
Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Protocol description • Step 1: Alice sends her user ID to Bob • This is a simple step in which Alice indicates her willingness to login 7

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Protocol description contd. . • Bob generates two random numbers r and R. r is a small (e. g. 20 bit) random number, R is a big (100 bit) random number • Bob also computes H(r, P) where P is Alice’s password and computes a MAC = H(KBob, H(r, P), Alice, n) • KBob is Bob’s secret key, n is the number of failed attempts by Alice so far • Step 2: Bob replies back with: H(r, R), R, MAC 8

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Protocol description contd. . • Alice should find out r before she can proceed with the login attempt. This is done by checking the hash values of all possible 20 bit number appended with R (and matching with H(r, R)) • R acts as a salt to prevent her from pre-computing H(r) for all possible r • This step is computationally intensive for Alice and prevents her from making a large number of login attempts per unit time. 9

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Protocol description contd. . • After finding out r, Alice computes H(r, P) • Step 3: Alice sends to Bob: Alice, H(r, P) along with the received MAC (=H(H(r, P), Alice, KBob, n)) • This step can be independently executed making the protocol stateless 10

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Protocol description contd. . • Bob hashes the received H(r, P) with its key, Alice, and n and matches the resulting quantity with the received MAC • If they match, Alice is logged in • Else n is incremented. • Bob sends the success/failure signal 11

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Protocol figure 12

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Protocol Security • The MAC H(H(r, P), Alice, KBob, n) is un-intelligible to Alice and is only meant to be returned to the server. This is to make the server stateless. • This MAC is specific for the user and the login attempt. Thus, this cannot be re-used for any other user / attempting login more than once for a single user • All this ensures that Alice did the required computation 13

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Protocol Variant 1 • A minor variation in the message sequence produces interesting results • Replace H(r, R) with H(r, P, R) in step 2 and 3 with MAC=H(H(r, P), Alice, KBob, n) • This rapidly increases the offline dictionary attack time, useful in case SSL protection is not used 14

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Protocol Variant 2 • Aimed at making the protocol secure again server compromise • Replace H(P, r) with r, H(i-1)(P) with MAC = H(r, Hi(P), Alice, KBob, n) • Relatively complex, uses Hash chains 15

Comp. Chall: Addressing Password Guessing Attacks IAS, ITCC-2005, April 2005 Thank You 16