AES Proposal Rijndael Joan Daemen Vincent Rijmen Rijndael









- Slides: 11

AES Proposal: Rijndael Joan Daemen Vincent Rijmen “Rijndael is expected, for all key and block lengths defined, to behave as good as can be expected from a block cipher with the given block and key lengths. ” Presented by Jianning TANG

Outline · · · Introduction Applications of Rijndael Design Criteria Rijndael Encryption Resistance Against Known Attacks Security goal Conclusion Question

Introduction AES: Advanced Encryption Standard published by NIST Block Cipher: An encrypting method in which each block of plain text is converted into a block of cipher text of the same length Rijndael: An iterated block cipher with a variable block length and a variable key length. The block length and the key length can be independently specified to 128, 192 or 256 bits.

Applications of Rijndael cipher is designed to be implemented efficiently on a wide range of processors and in dedicated hardware. i. e. Smart Card, ATM, HDTV, B-ISDN, Voice and Satellite (encryption). Rijndael can also be used in MAC algorithm, iterated hash function, synchronous stream cipher, pseudo-random number generator, self-synchronizing stream cipher.

Design Criteria • Resistance against all known attacks; • Speed and code compactness on a wide range of platforms; • Design simplicity.

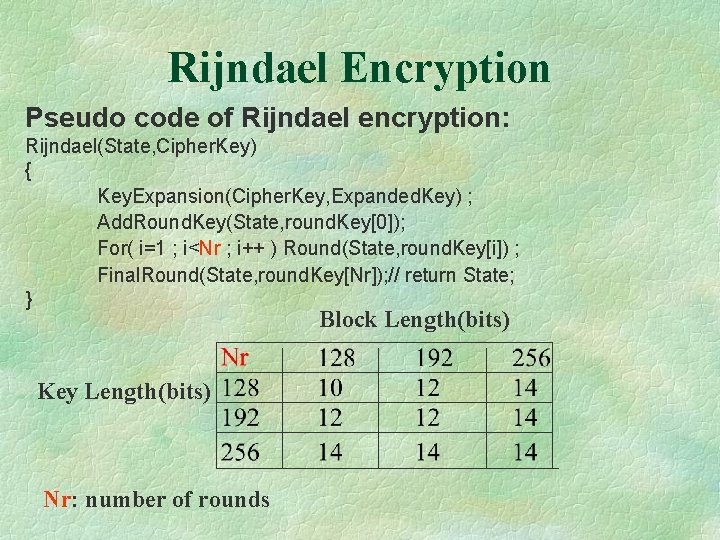
Rijndael Encryption Pseudo code of Rijndael encryption: Rijndael(State, Cipher. Key) { Key. Expansion(Cipher. Key, Expanded. Key) ; Add. Round. Key(State, round. Key[0]); For( i=1 ; i<Nr ; i++ ) Round(State, round. Key[i]) ; Final. Round(State, round. Key[Nr]); // return State; } Block Length(bits) Key Length(bits) Nr: number of rounds

Resistance Against Known Attacks Attack: If the computational time of a cryptanalysis method(to find the key) is less than the computational time of an exhausted key search, the method is said to be an effective attack. Plain Text--Cipher Text Pairs: Known to cryptanalyst. Keys: NOT known to cryptanalyst

List of known cryptanalysis methods: Symmetry properties and weak keys of the DES type Differential cryptanalysis Linear cryptanalysis Truncated differentials The Square attack Interpolation attacks Related-key attacks No attack has yet been found to be effective against Rijndael.

Security Goal 1. K-security: All possible attack strategies for Rijndael have the same expected work factor and storage requirements as for the majority of possible block ciphers with the same dimensions. 2. Hermetic: It does not have weaknesses that are not present for the majority of block ciphers with the same block and key length. Or: its internal structure cannot be exploited in any application. Rijndael is expected to achieve its security goal

Conclusion In security aspect: “Rijndael is expected, for all key and block lengths defined, to behave as good as can be expected from a block cipher with the given block and key lengths. ”

Question If a block cipher is k-security, do you think it is secure enough?

















