ACM Code of Ethics Ethical Considerations 1 The





- Slides: 10

ACM Code of Ethics Ethical Considerations 1 The ACM Code of Ethics expresses the conscience of the computing profession, and it a�rms an obligation of computing professionals both individually and collectively to use their skills for the benefit of society. Computing professionals' actions change the world. To act responsibly, they should reflect upon the wider impacts of their work, consistently supporting the public good. The Code is designed to inspire and guide the ethical conduct of all computing professionals, including current and aspiring practitioners, instructors, students, influencers, and anyone who uses computing technology in an impactful way. www. acm. org/code-of-ethics CS@VT Data Structures & Algorithms © 2000 -2020 Mc. Quain

ACM Code of Ethics Ethical Considerations 2 General Principles A computing professional should: 1. 1 Contribute to society and to human well-being, acknowledging that all people are stakeholders in computing. 1. 2 Avoid harm. 1. 3 Be honest and trustworthy. 1. 4 Be fair and take action not to discriminate. 1. 5 Respect the work required to produce new ideas, inventions, creative works, and computing artifacts. 1. 6 Respect privacy. 1. 7 Honor confidentiality. www. acm. org/code-of-ethics CS@VT Data Structures & Algorithms © 2000 -2020 Mc. Quain

ACM Code of Ethics Ethical Considerations 3 Professional Responsibilities A computing professional should: 2. 1 Strive to achieve high quality in both the processes and products of professional work. 2. 2 Maintain high standards of professional competence, conduct, and ethical practice. 2. 3 Know and respect existing rules pertaining to professional work. 2. 4 Accept and provide appropriate professional review. 2. 5 Give comprehensive and thorough evaluations of computer systems and their impacts, including analysis of possible risks. 2. 6 Perform work only in areas of competence. 2. 7 Foster public awareness and understanding of computing, related technologies, and their consequences. 2. 8 Access computing and communication resources only when authorized or when compelled by the public good. 2. 9 Design and implement systems that are robustly and usably secure. www. acm. org/code-of-ethics CS@VT Data Structures & Algorithms © 2000 -2020 Mc. Quain

Sobering Truths about Design Ethical Considerations 4 Is design important? 75%-80% of system errors are created in the analysis and design phases. Analysis and design phases account for about only 10% of the overall system cost. Only about 25% of software projects result in working systems. (Perhaps you get what you pay for. ) Let's consider which ACM guidelines may have been violated in these actual cases: Therac-25 Medical Linear Accelerator (1985 -1987, >= 2 deaths) Patriot Anti-missile Timing Bug (1991, 28 deaths, 98 wounded) WWMCCS network (Nov 9, 1979, possible global thermonuclear war) CS@VT Data Structures & Algorithms © 2000 -2020 Mc. Quain

Questionable Features Ethical Considerations 5 Try an experiment: Google your name (or the name of a parent) Are you disturbed by the availability of any of the resulting pieces of information? If so, does this suggest anything that the ACM Code might have prevented? CS@VT Data Structures & Algorithms © 2000 -2020 Mc. Quain

Case: Federal GIS Database Ethical Considerations 6 Following the attacks on Sept 11, 2001: - The availability of information on the Internet was considered. - Precise location data for some sensitive features were removed from public files. - Eventually, that data was restored or obfuscated. Does this suggest anything about the application of the ACM Code? CS@VT Data Structures & Algorithms © 2000 -2020 Mc. Quain

Case: Facial Recognition Software Ethical Considerations 7 What are the issues? - Privacy concerns: the right to be left alone. - Privacy concerns: confidentiality and retention of data. - Accuracy of results: less so for women and people of color. Does this suggest anything about the application of the ACM Code? Where else have we seen comparable issues? - general medical records - medical studies related to common illnesses, drug effectiveness, etc. CS@VT Data Structures & Algorithms © 2000 -2020 Mc. Quain

Case: Asimov's 3 Laws of Robotics Ethical Considerations 8 First Law A robot may not injure a human being or, through inaction, allow a human being to come to harm. Second Law A robot must obey the orders given it by human beings except where such orders would conflict with the First Law. Third Law A robot must protect its own existence as long as such protection does not conflict with the First or Second Law. Loopholes? Unintended consequences? Permutations? Isaac Asimov, Runaround, 1942 CS@VT Data Structures & Algorithms © 2000 -2020 Mc. Quain

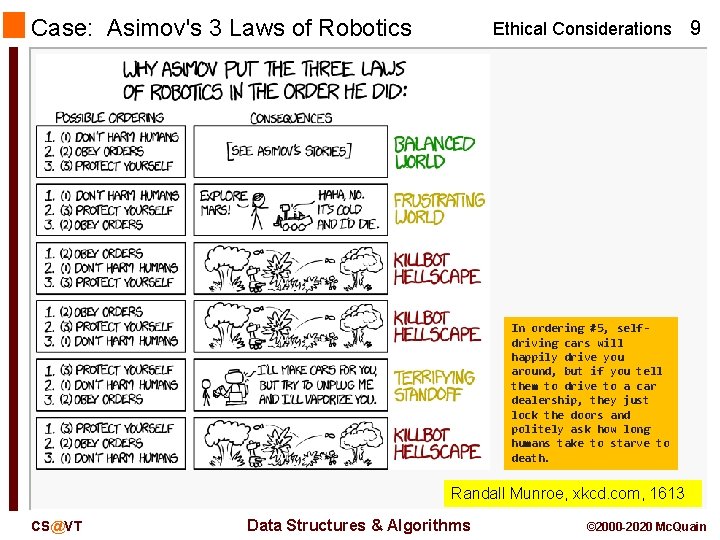
Case: Asimov's 3 Laws of Robotics Ethical Considerations 9 In ordering #5, selfdriving cars will happily drive you around, but if you tell them to drive to a car dealership, they just lock the doors and politely ask how long humans take to starve to death. Randall Munroe, xkcd. com, 1613 CS@VT Data Structures & Algorithms © 2000 -2020 Mc. Quain

References Ethical Considerations 10 An Investigation of the Therac-25 Accidents N Leveson & C Turner, IEEE Computer, July 1993 Patriot Missile Defense: Software Problem Led to System failure at Dharan, Saudia Arabia Report to Committee on Science, Space, and Technology, House of Representatives, February 1992 Close Calls with Nuclear Weapons Union of Concerned Scientists, April 2015 Command control: nuclear weapons, the Damascus accident, and the illusion of safety E Schlosser, 2013 CS@VT Data Structures & Algorithms © 2000 -2020 Mc. Quain