UW Information Systems Security Policy Stephen Rondeau Institute












- Slides: 15

UW Information Systems Security Policy Stephen Rondeau Institute of Technology Computing Labs Administrator 18 Nov 2005

Agenda • • • Components Sampling of Laws Complying with the Law Consideration of Ethics Consequences References

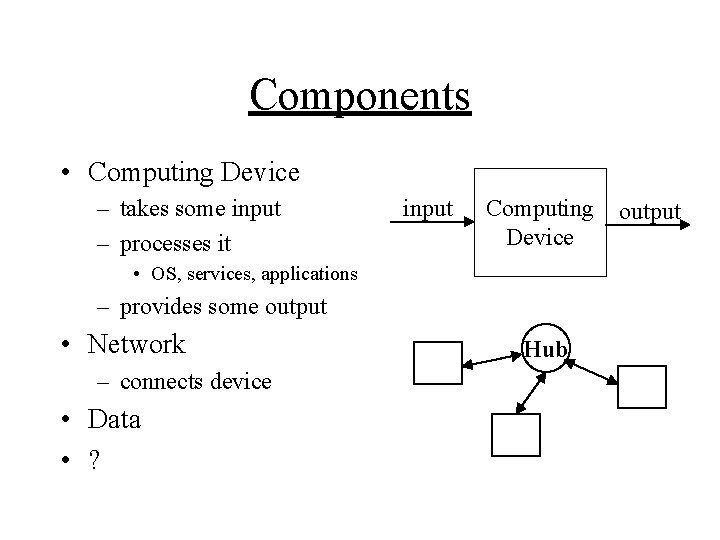
Components • Computing Device – takes some input – processes it input Computing Device • OS, services, applications – provides some output • Network – connects device • Data • ? Hub output

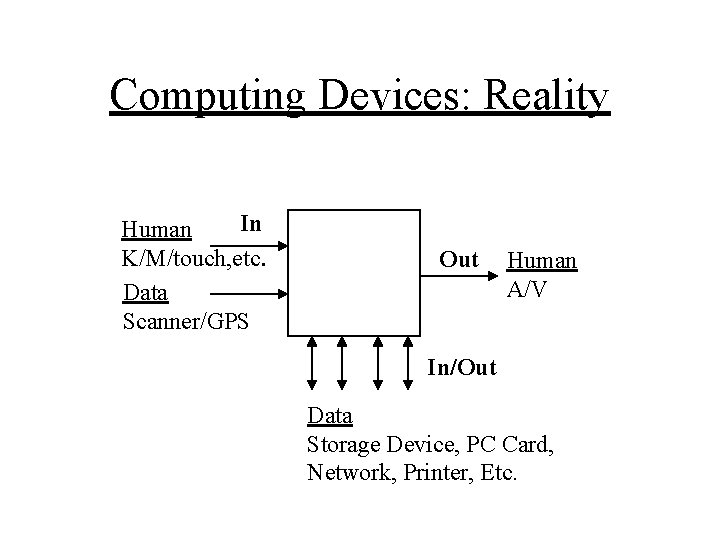
Computing Devices: Reality In Human K/M/touch, etc. Data Scanner/GPS Out Human A/V In/Out Data Storage Device, PC Card, Network, Printer, Etc.

Computing Devices: Connections • removable media – floppy, CD/DVD, flash, microdrive • PC Card • wired – serial/parallel, USB, Firewire, IDE, SCSI, twisted pair • wireless – radio (802. 11, cellular, Bluetooth) – Infrared (IR) – Ultrasound

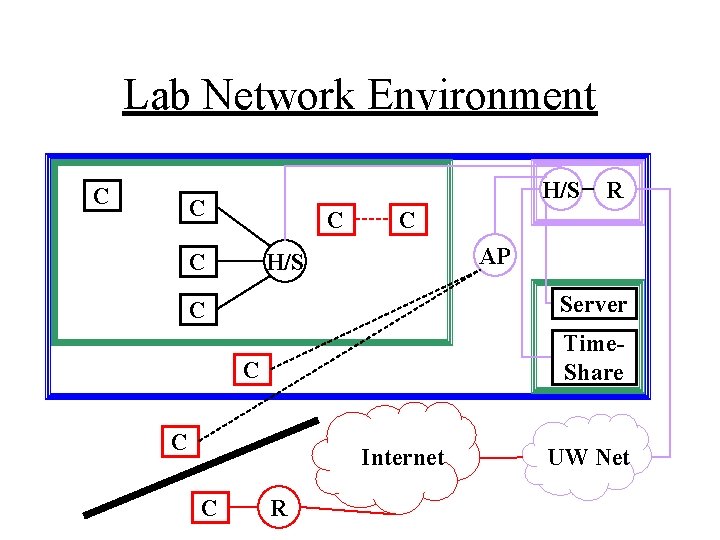
Lab Network Environment C H/S C C AP H/S Server C Time. Share C C Internet C R R UW Net

Data Issues • Sensitivity: public or confidential – confidential • minimal, more sensitive, most sensitive • owned by someone • specific statements for access, distribution, storage, disposal and penalties for disclosure • Criticality: how important to function

Key Security Concepts • Must protect: – Services/Use • Functionality: perform function or use device • Availability: device or data is ready for use on demand at operational speed and capacity – Data • Confidentiality: prevent disclosure to unauthorized people • Integrity: unaltered, intact

Sampling of Laws • International, federal, state, UW – statutes and regulations • Federal – privacy, wiretapping, fraud, disclosure, surveillance, counterterrorism – grant-related policy • WA State – privacy, malicious mischief, public records, spam, disclosure • UW Administrative Code – student and general conduct, records access

Complying with the Laws • • Comply: take action to conform Law => Policies + Standards + Guidelines Policies state what needs to be done Standards define how to implement the policy (via procedures) • Guidelines are strongly-recommended practices to assist in adhering to standards

Roles and Responsibilities • System owners and operators • comply with laws, policies, guidelines • maintain confidentiality of sensitive data • grant access based on “least privilege” and “separation of duties” principles • report security incidents and perform incident response • Data Custodians • Users

Policies • May monitor user accounts, files and access • Understand nature of data on systems, and manage it appropriately • Provide logical and physical access control and logging commensurate with sensitivity and criticality of computing devices, networks and data • Document procedures for issuing, altering and revoking access privileges • Implement minimum computer and network measures and practices

Consideration of Ethics • Ethics are the principles of conduct that are harmonious with society – arguably higher than policy – notable examples • whistleblowing • preventing conflicts of interest • protecting life • Use of university resources; data sensitivity

Consequences • • • Worm/Virus authoring and release Trojans Unauthorized wireless access Keylogging Botnets

References • UW Information Systems Security – http: //www. washington. edu/admin/rules/APS/02. 01 TO C. html • UW Minimum Computing Security Standards – http: //www. washington. edu/computing/security/pass/M in. Comp. Sec. html • UW Electronic Information Privacy Policy – http: //www. washington. edu/computing/rules/privacypol icy. html • SANS Institute Policy Templates – http: //www. sans. org/resources/policies/
 Stephen rondeau
Stephen rondeau E commerce security policy
E commerce security policy Security private
Security private Xkcd specifications
Xkcd specifications Explain about visa international security mode
Explain about visa international security mode Information security
Information security Securing information systems summary
Securing information systems summary Le printemps charles d'orléans
Le printemps charles d'orléans Diamante poem structure
Diamante poem structure Acrostic poem using catalyst
Acrostic poem using catalyst Ciel, air et vents, plains et monts découverts analyse
Ciel, air et vents, plains et monts découverts analyse Institute for urban policy research
Institute for urban policy research Pensions commission ireland
Pensions commission ireland Pensions policy institute
Pensions policy institute Quantum information stephen m. barnett
Quantum information stephen m. barnett Homeland security institute
Homeland security institute




























