UNIX System Protection Unix History Developed by Dennis

UNIX System Protection

Unix History • Developed by Dennis Ritchie and Ken Thompson at AT&T Bell Labs • Adapted some ideas from the Multics project in 1969

Design Features • Written in C – portable • Application program interface (API) – enabled programmers to write applications that are compatible with multiple platforms • A small base program called “kernel” with a standard interface to interact

Security • Security goal: – A common platform that could be shared by several users – Security problem becomes one of “protection” • Common mechanisms – Password storage – Protection ring – Access control lists

Kernel and Processes • A running Unix system consists of the kernel and the processes each running a program – Protection ring boundary isolates the kernel from the processes – Each process has its own address space – The concept of “file” for representing all persistent system objects

Trusted Computing Base • The set of software and data upon which the system depends for correct enforcement of system security goals • Consists of the kernel and processes running with root (superuser) privilege

Unix Protection System • What does protection mean? – An access enforcement mechanism that authorizes requests from subjects to perform operations on objects – Requests: read, write, etc. – Subjects: users, processes, etc. – Objects: files, sockets, etc.
Unix Protection System • Protection state: describes the operations that system subjects can perform on system objects • UNIX protection state specification – Subjects: process identities • Process identities: user id (UID), group id (GID), and a set of supplementary groups. – Objects: files – Access: read, write, execute – Protection state is specified by an access control list (ACL) associated with each file
Unix File • Each file is associated with: – An owner UID and an owner GID • Process with the owner UID privilege can modify the protection state – “mode bits” describe the ACL of a file • {owner bits, group bits, others bits}, where each element consists of a read bit, a write bit, and an execute bit • e. g. , rwxr--r--
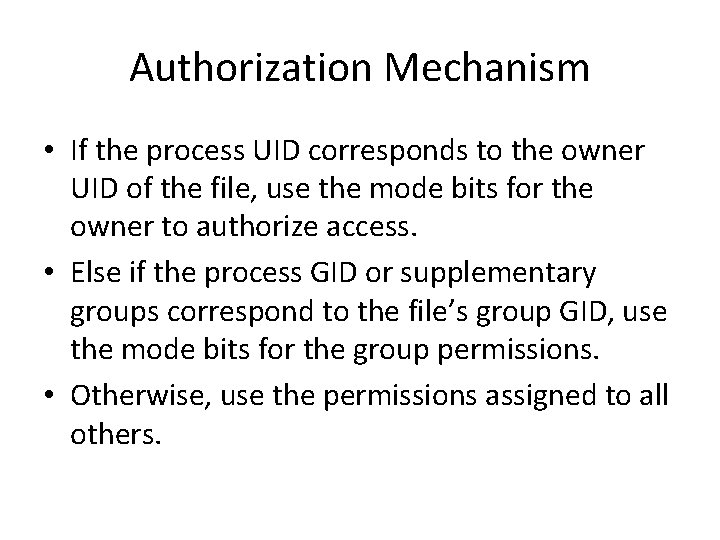
Authorization Mechanism • If the process UID corresponds to the owner UID of the file, use the mode bits for the owner to authorize access. • Else if the process GID or supplementary groups correspond to the file’s group GID, use the mode bits for the group permissions. • Otherwise, use the permissions assigned to all others.
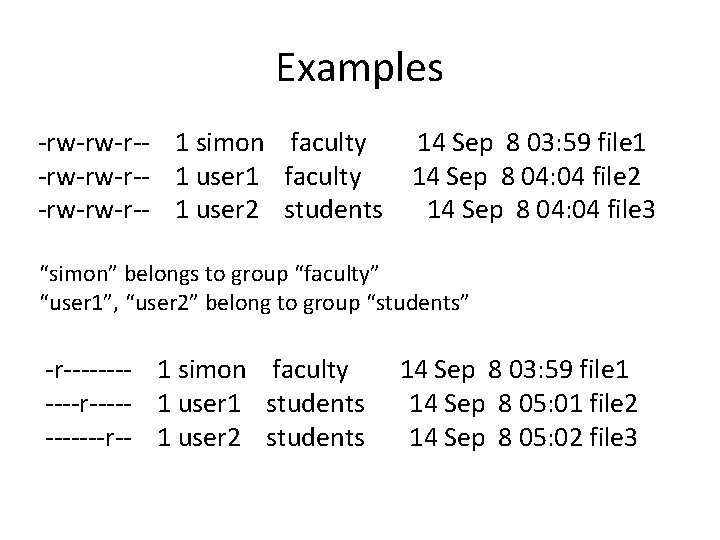
Examples -rw-rw-r-- 1 simon faculty -rw-rw-r-- 1 user 1 faculty -rw-rw-r-- 1 user 2 students 14 Sep 8 03: 59 file 1 14 Sep 8 04: 04 file 2 14 Sep 8 04: 04 file 3 “simon” belongs to group “faculty” “user 1”, “user 2” belong to group “students” -r---- 1 simon faculty ----r----- 1 user 1 students -------r-- 1 user 2 students 14 Sep 8 03: 59 file 1 14 Sep 8 05: 01 file 2 14 Sep 8 05: 02 file 3

Protection State Modification in Unix • Protection state operations: enable a protection state to be modified • In Unix, the protection state can be modified by any process that has the owner ID privilege – This is called “discretionary access control” – Essentially we have to trust all user-level processes to achieve the security goal of protection
- Slides: 12