Unix network Services Configuring a network interface In








- Slides: 13

Unix network Services

Configuring a network interface In Unix there are essentially two commands that are used to enable TCP/IP. ifconfig route

How Unix processes network Requests When a Unix system receives a TCP/IP packet. The headers of these packets contain the IP address and port address of the service being requested. The port address is located in the transport layer header. (TCP or UDP)

The Portmapper The portmapper is a program that examines all off the incoming/outgoing packets. The portmapper will then consult the /etc/services file to determine which (if any) program should be passed the packet.

Sample services file ftp ssh telnet smtp http pop 3 https 21/tcp #File Transfer [Control] 22/tcp #Secure Shell Login 23/tcp 25/tcp # mail 80/tcp www-http 110/tcp #Post Office Protocol -V 3 443/tcp #secure http

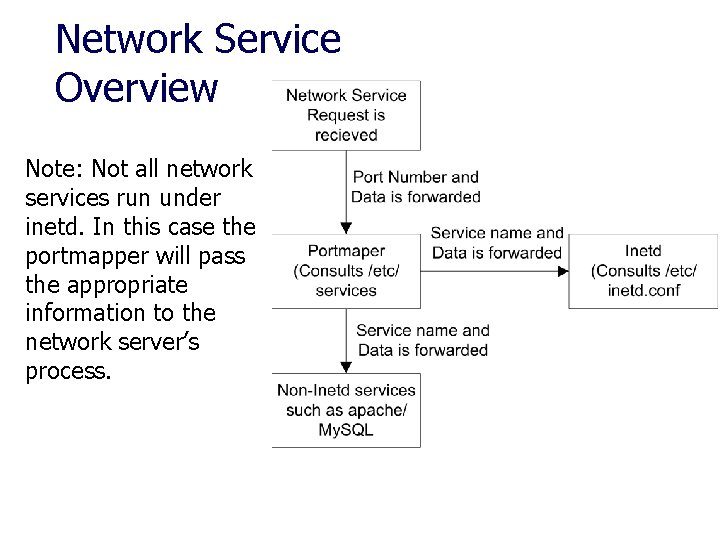
Network Service Overview Note: Not all network services run under inetd. In this case the portmapper will pass the appropriate information to the network server’s process.

Inetd is consider the master networking daemon. This program controls many network functions. Such as email, ftp, telnet and sometimes web and ssh. The role of inetd is to start up the appropriate process to service a request. The rationale is that only one process will be running, then when additional processes are required they will started by the one. The net result is a savings in overall system resources.

/etc/inetd. conf This is the configuration file for inetd. This file contains a list of which programs respond to which service requests, as well as how they respond. The general syntax for the inetd. con file is; service_name-sock_type-proto-flags-user-server_path-args

Sample inetd. conf ftp stream tcp nowait root /usr/sbin/tcpd proftpd telnet stream tcp nowait root /usr/sbin/tcpd in. telnetd pop 3 stream tcp nowait root /usr/sbin/tcpd /usr/sbin/popa 3 d /usr/sbin/tcpd is a service wrapper that provides an additional layer of protection, by not starting the service using the root user.

Removing services To prevent a service from running one may comment out the entry in the services file or inetd. conf.

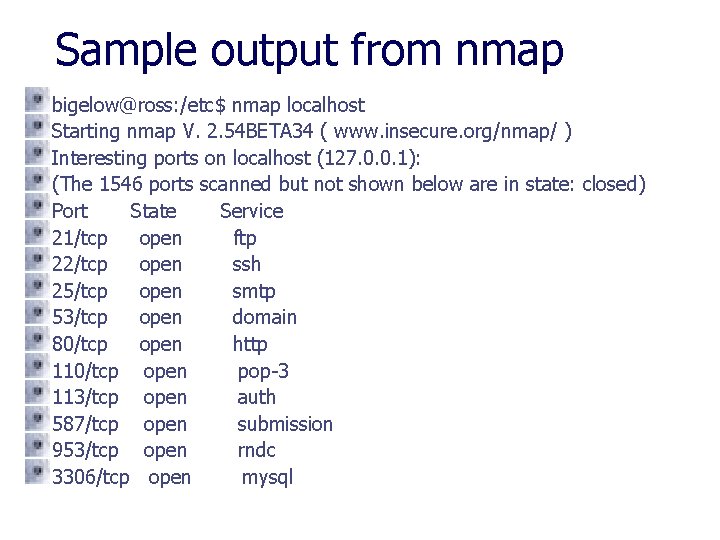
Finding out which services are running To determine which network services are running one could use a port scanner such as nmap. The nmap command will port scan a system and inform you which ports are open.

Sample output from nmap bigelow@ross: /etc$ nmap localhost Starting nmap V. 2. 54 BETA 34 ( www. insecure. org/nmap/ ) Interesting ports on localhost (127. 0. 0. 1): (The 1546 ports scanned but not shown below are in state: closed) Port State Service 21/tcp open ftp 22/tcp open ssh 25/tcp open smtp 53/tcp open domain 80/tcp open http 110/tcp open pop-3 113/tcp open auth 587/tcp open submission 953/tcp open rndc 3306/tcp open mysql

Closing open ports The first rule of security is if you don’t need something disable it. Every open port is another “door” into your system. Therefore is if you have 4 services running there are 4 possible programs that may be exploited, and you are 4 times as likely to have a system compromise then a system that is running only 1 service.