Steganography Then and Now John Hally May 2012










- Slides: 15

Steganography Then and Now John Hally May 2012 GIAC GSEC, GCIA, GCIH, GCFA, GCWN, GPEN SANS Technology Institute - Candidate for Master of Science Degree 1 1

Steganography • What it is: Hidden Writing – From Greek words “steganos” (covered) and “graphie” (writing). – The goal is to hide that communication is taking place. • What it is not: Cryptography – The goal of Cryptography is to make data unreadable by third party. • Commonly combined together SANS Technology Institute - Candidate for Master of Science Degree 2

Uses – Then • Digital watermarking/copyright protection • Corporate espionage • Anti-forensics • Terrorist cell covert communications SANS Technology Institute - Candidate for Master of Science Degree 3

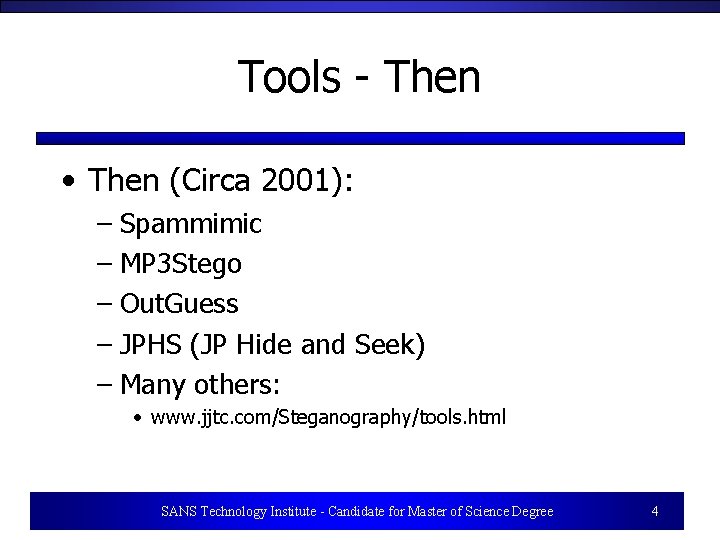
Tools - Then • Then (Circa 2001): – Spammimic – MP 3 Stego – Out. Guess – JPHS (JP Hide and Seek) – Many others: • www. jjtc. com/Steganography/tools. html SANS Technology Institute - Candidate for Master of Science Degree 4

Detection - Then • Direct comparison using original (visual, statistical) • Targeted Detection tools – target popular steganography tools • Steg. Detect • General framework - Statistical analysis SANS Technology Institute - Candidate for Master of Science Degree 5

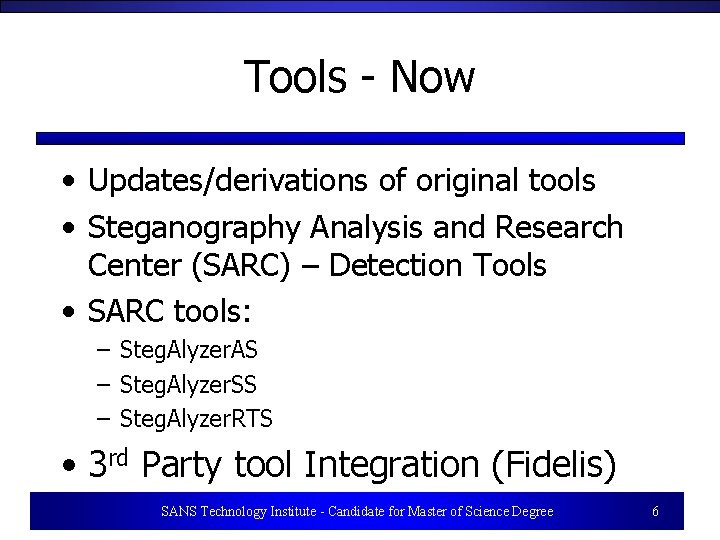
Tools - Now • Updates/derivations of original tools • Steganography Analysis and Research Center (SARC) – Detection Tools • SARC tools: – Steg. Alyzer. AS – Steg. Alyzer. SS – Steg. Alyzer. RTS • 3 rd Party tool Integration (Fidelis) SANS Technology Institute - Candidate for Master of Science Degree 6

Detection - Now • • Signature-based solutions are prevalent Anti. Virus/Anti. Malware similarities Original Methodologies still relevant Forensic expert consensus – not typically included in investigations SANS Technology Institute - Candidate for Master of Science Degree 7

In Use Today • Command Control • Operation Shady Rat • Espionage • Russian Intelligence “Illegals Program” • Terrorism? SANS Technology Institute - Candidate for Master of Science Degree 8

Operation Shady Rat • A multi-year targeted operation by one ‘actor’ in order to extrude sensitive information from its targets. – 71 compromised organizations identified: • 21 Government Organizations - including 6 US Federal, 5 State, 3 County • 6 Industrial Organizations - Construction/heavy industry, Steel, Solar, Energy • 13 Technology-based Organizations – including 2 Security organizations • 13 Defense Contractors, many others. – 3 Stage targeted attack: • Spear Phishing • Command Control (C&C) • Information Exfiltration SANS Technology Institute - Candidate for Master of Science Degree 9

Shady Rat C & C • Trojan exploit code used steganography • Commands embedded in HTML and image files • HTML files used encryption and encoding for obfuscation • Impregnated commands in images SANS Technology Institute - Candidate for Master of Science Degree 10

Examples of Steganographic Files SANS Technology Institute - Candidate for Master of Science Degree 11

Espionage • United States vs. Anna Chapman and Mikhail Semenko • Illegals Program – Investigation of Russian ‘sleeper’ agents operating in the U. S. • Main goal was to infiltrate the United States policy making circles. • Agents were to hide connections between themselves and the Russian Intelligence Federation SANS Technology Institute - Candidate for Master of Science Degree 12

Espionage: Covert Communications • Investigation revealed the use of steganography for communications back to Russia • Custom steganography program used to embed data in images • Communications also took place via “wireless drive-by” • Additional physical steganograhic methods were used SANS Technology Institute - Candidate for Master of Science Degree 13

Enterprise Defenses • Know your data • Know your traffic • Know your people • Education • Vigilance SANS Technology Institute - Candidate for Master of Science Degree 14

Summary • Steganography • Art of hiding messages in files for covert communications • Tools – Hundreds of tools available, many use the same methods • Detection – Detection methods for well known tools – Statistical analysis required for ‘custom’ tools – Not commonly searched for in typical forensic analysis • Uses – Command Control – Shady Rat – Russian Espionage – “Illegals Program” • Defenses – Know your data, traffic, people – Education and vigilance SANS Technology Institute - Candidate for Master of Science Degree 15
 201 cmr 17
201 cmr 17 Steganography
Steganography Sociology: then and now
Sociology: then and now Sociology: then and now practice
Sociology: then and now practice Seaside holidays now and then
Seaside holidays now and then Seaside then and now
Seaside then and now John purdy inventor
John purdy inventor Dubai now and then
Dubai now and then Agriculture now and then
Agriculture now and then Child labor then and now venn diagram
Child labor then and now venn diagram Seaside now and then
Seaside now and then Physical education now and then
Physical education now and then Then and now grammar
Then and now grammar What is the official salute of the ffa organization
What is the official salute of the ffa organization Jerusalem then and now
Jerusalem then and now Victorian seaside holidays
Victorian seaside holidays




























