SIMPLE List Manipulation Semantics Markus Isomki markus isomakinokia



- Slides: 5

SIMPLE List Manipulation Semantics Markus Isomäki markus. isomaki@nokia. com IETF 55

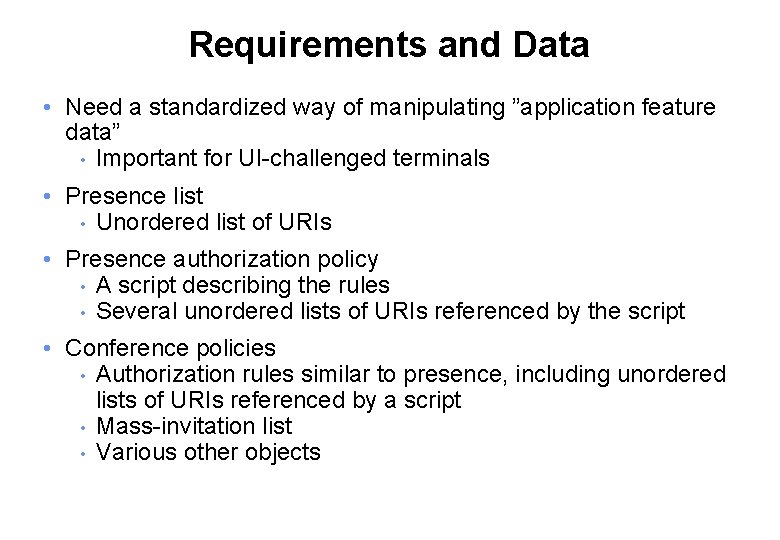
Requirements and Data • Need a standardized way of manipulating ”application feature data” • Important for UI-challenged terminals • Presence list • Unordered list of URIs • Presence authorization policy • A script describing the rules • Several unordered lists of URIs referenced by the script • Conference policies • Authorization rules similar to presence, including unordered lists of URIs referenced by a script • Mass-invitation list • Various other objects

List Manipulation • An unordered list of URIs seems to be a very common element in SIP/SIMPLE applications • Application instance has either a fixed number of lists or the number can vary • It is possible to have a list of lists • It seems very difficult to use the same list accross applications • pres: URL is OK for a presence list, but it has no meaning for a conference • Still, it would be best to do the manipulation in a uniform way across all SIP applications

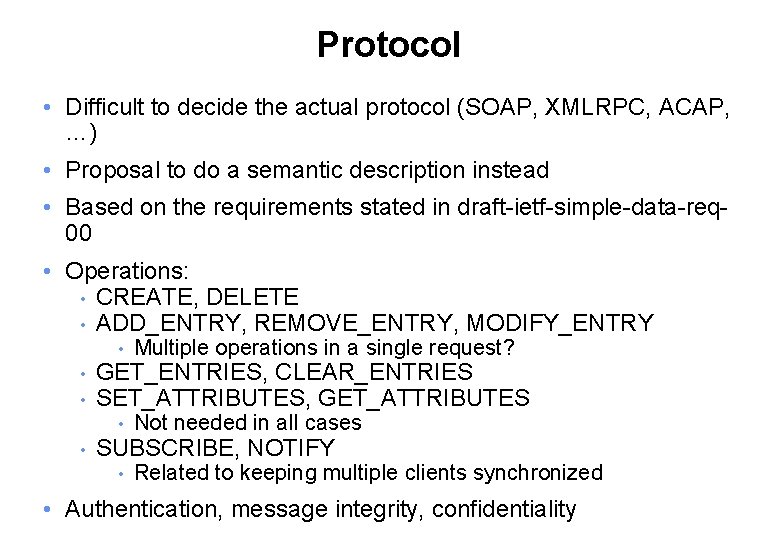
Protocol • Difficult to decide the actual protocol (SOAP, XMLRPC, ACAP, …) • Proposal to do a semantic description instead • Based on the requirements stated in draft-ietf-simple-data-req 00 • Operations: • CREATE, DELETE • ADD_ENTRY, REMOVE_ENTRY, MODIFY_ENTRY • • • GET_ENTRIES, CLEAR_ENTRIES SET_ATTRIBUTES, GET_ATTRIBUTES • • Multiple operations in a single request? Not needed in all cases SUBSCRIBE, NOTIFY • Related to keeping multiple clients synchronized • Authentication, message integrity, confidentiality

What Should Be Done Next • Decide the Scope of the solution 1. Just for presence 2. General purpose list (and authorization policy) management 3. General purpose data manipulation • • with e. g. XML and Xpath Usable also for conference policy control • Make a good plan on the documents to produce, similar to Conferencing design team • Figure out the relation to Conferencing drafts • Predict the timeline • Decide the Synchronization model • Just simple event package to inform on changes? What would be carried in NOTIFY payload? • Decide how to choose the actual protocols