SecurityEnhanced Linux Linux Security Module The George Washington



- Slides: 10

Security-Enhanced Linux & Linux Security Module The George Washington University CS 297 Programming Language & Security YU-HAO HU

Introduction: Why SELinux ? n n Discretionary Access Control (DAC) has not enough choices for controlling object. Mandatory Access Control (MAC) allows you to define permissions for how all processes (called subjects) interact with other parts of the system such as files, devices, sockets, ports, and other processes (called objects in SELinux).

Linux Security Module: Overview n n n SELinux motivated the creation of LSM. Separate kernel from security features in order to minimize the impact to kernel. LSM doesn’t provide any security rather it add security fields to kernel and provide interface to manage these fields for maintaining security attributes. .

Linux Security Module: Hooks n n n Hooks are a set of functions to control operations on kernel objects and security fields in kernel data structures. Management Hooks: used to manage security fields. Ex. file_alloc_security Control Hooks: used to perform access controls Ex. selinux_inode_permission

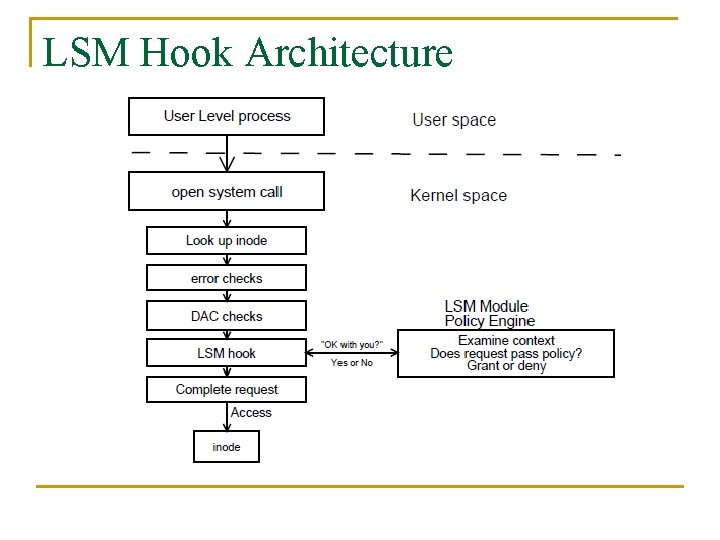
LSM Hook Architecture

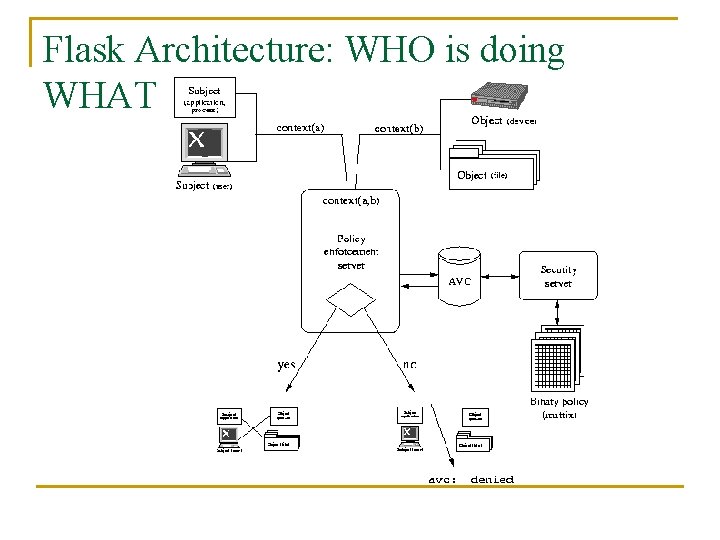
SELinux Overview n n n Implement Flask architecture. SELinux is implemented in the Linux kernel using the LSM (Linux Security Modules) framework. To support fine-grained access control, SELinux implements two technologies: Type Enforcement (TE) and Role-based Access Control (RBAC).

Flask Architecture: WHO is doing WHAT

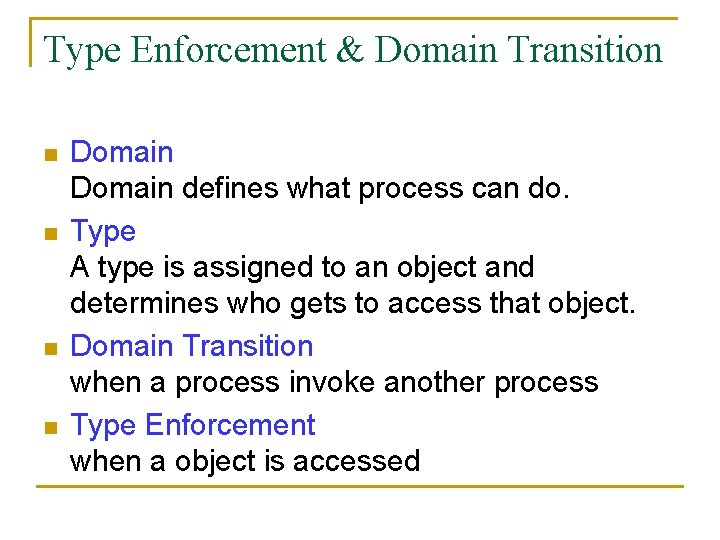
Type Enforcement & Domain Transition n n Domain defines what process can do. Type A type is assigned to an object and determines who gets to access that object. Domain Transition when a process invoke another process Type Enforcement when a object is accessed

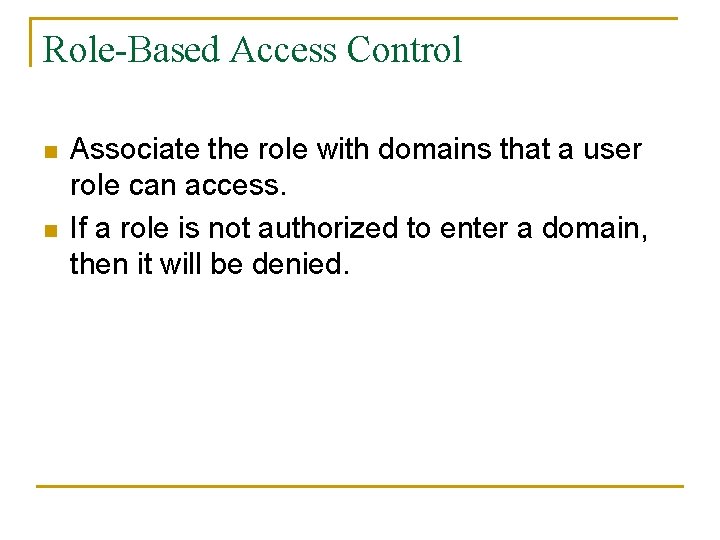
Role-Based Access Control n n Associate the role with domains that a user role can access. If a role is not authorized to enter a domain, then it will be denied.

References n Linux Security Module Framework. 2002 Ottawa Linux Symposium, Ottawa, Canada, June 2002. n n n Linux Security Modules: General Security Support for the Linux Kernel. 11 th USENIX Security Symposium, San Francisco, CA, August 2002. Red Hat SELinux Guide Configuring the SELinux Policy Stephen Smalley (NAI Labs) n Implementing SELinux as a Linux Security Module Stephen Smalley, Chris Vance, and Wayne Salamon (NAI Labs) n n Getting Started with SE Linux HOWTO: the new SE Linux Writing SE Linux Policy HOWTO Faye Coker