Secure Composition of Untrusted Code Wrappers and Causality


![Syntax Continued l Process P – – – l P : : = n[P] Syntax Continued l Process P – – – l P : : = n[P]](https://slidetodoc.com/presentation_image_h2/948c24791e92a970eb766e526a36a7a6/image-7.jpg)
![Filtering Example l l alice[P] | !inalicex | !outalicex | !netalicex W 1(_) def Filtering Example l l alice[P] | !inalicex | !outalicex | !netalicex W 1(_) def](https://slidetodoc.com/presentation_image_h2/948c24791e92a970eb766e526a36a7a6/image-9.jpg)
![Filtering Example Continued l l l l inalicey | alice [P | W 1(Q)] Filtering Example Continued l l l l inalicey | alice [P | W 1(Q)]](https://slidetodoc.com/presentation_image_h2/948c24791e92a970eb766e526a36a7a6/image-10.jpg)



- Slides: 15

Secure Composition of Untrusted Code: Wrappers and Causality Types Kyle Taylor

Introduction

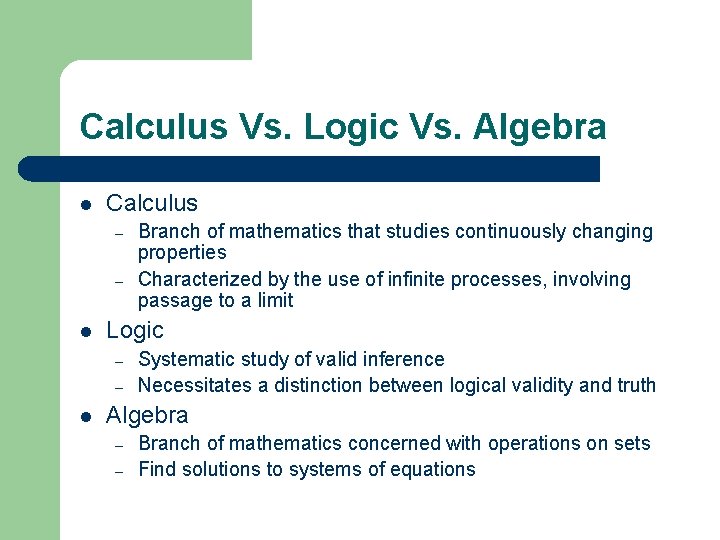
Calculus Vs. Logic Vs. Algebra l Calculus – – l Logic – – l Branch of mathematics that studies continuously changing properties Characterized by the use of infinite processes, involving passage to a limit Systematic study of valid inference Necessitates a distinction between logical validity and truth Algebra – – Branch of mathematics concerned with operations on sets Find solutions to systems of equations

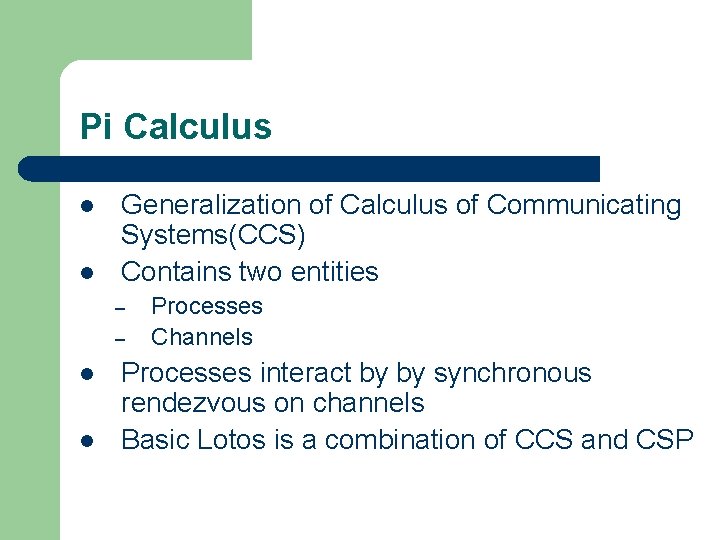
Pi Calculus l l Generalization of Calculus of Communicating Systems(CCS) Contains two entities – – l l Processes Channels Processes interact by by synchronous rendezvous on channels Basic Lotos is a combination of CCS and CSP

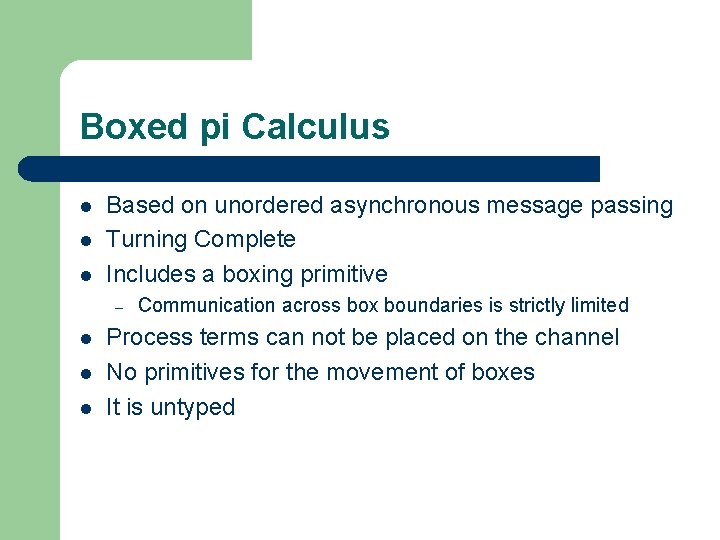
Boxed pi Calculus l l l Based on unordered asynchronous message passing Turning Complete Includes a boxing primitive – l l l Communication across box boundaries is strictly limited Process terms can not be placed on the channel No primitives for the movement of boxes It is untyped

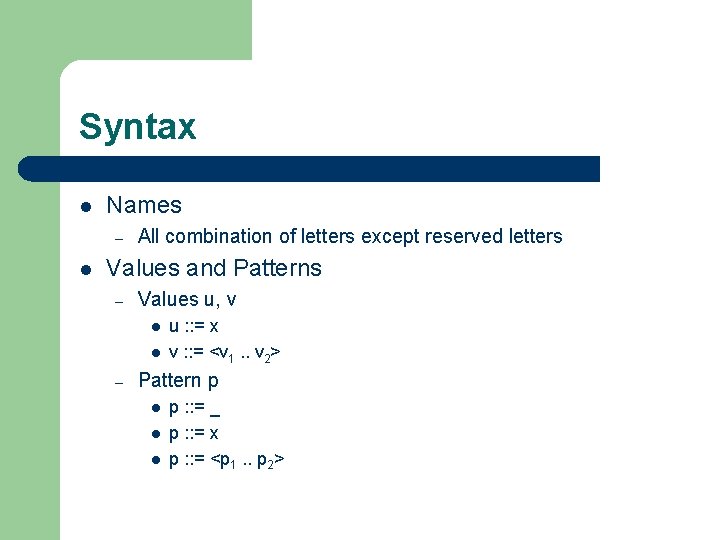
Syntax l Names – l All combination of letters except reserved letters Values and Patterns – Values u, v l l – u : : = x v : : = <v 1. . v 2> Pattern p l l l p : : = _ p : : = x p : : = <p 1. . p 2>
![Syntax Continued l Process P l P nP Syntax Continued l Process P – – – l P : : = n[P]](https://slidetodoc.com/presentation_image_h2/948c24791e92a970eb766e526a36a7a6/image-7.jpg)
Syntax Continued l Process P – – – l P : : = n[P] P : : = P | P’ P : : = xov P : : = xip. P P : : = !xip. P P : : = (v x) P Input tag i and output tag o can be *, , n

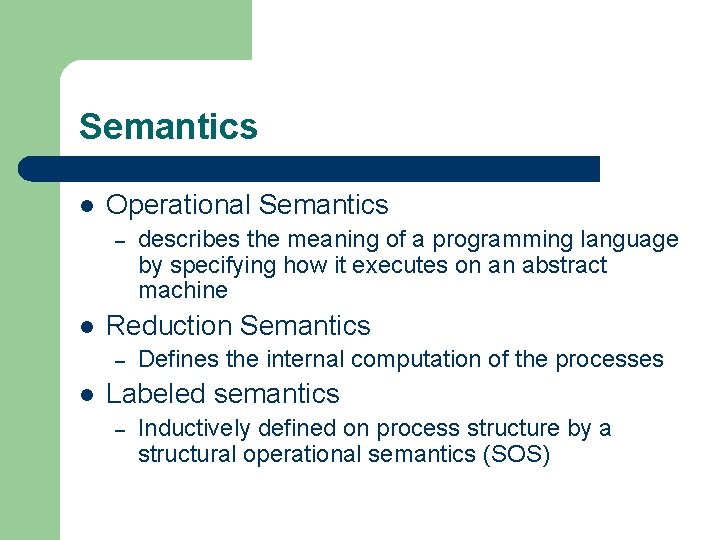
Semantics l Operational Semantics – l Reduction Semantics – l describes the meaning of a programming language by specifying how it executes on an abstract machine Defines the internal computation of the processes Labeled semantics – Inductively defined on process structure by a structural operational semantics (SOS)
![Filtering Example l l aliceP inalicex outalicex netalicex W 1 def Filtering Example l l alice[P] | !inalicex | !outalicex | !netalicex W 1(_) def](https://slidetodoc.com/presentation_image_h2/948c24791e92a970eb766e526a36a7a6/image-9.jpg)
Filtering Example l l alice[P] | !inalicex | !outalicex | !netalicex W 1(_) def = (v a)( a[_] | B ) – l l B =!in x. inax | !outax. out x W 1 prevents Q from accessing the network Assumes P=0 and Q=in x. net x
![Filtering Example Continued l l l l inalicey alice P W 1Q Filtering Example Continued l l l l inalicey | alice [P | W 1(Q)]](https://slidetodoc.com/presentation_image_h2/948c24791e92a970eb766e526a36a7a6/image-10.jpg)
Filtering Example Continued l l l l inalicey | alice [P | W 1(Q)] inalicey | alice[(v a)(a[Q] | B)] alice[in y | (v a)(a[Q] | B)] alice[(v a)(in y | a[Q] | B)] alice[(v a)(inay | a[Q] | B)] alice[(v a)(a[in y | Q] | B)] alice[(v a)(a[net y] | B)] alice[(v a)(netay | a[0] | B)]

Unidirectional-flow Wrapper l l l Provides ordered asynchronous communication Eliminates the awkwardness of only using only unordered asynchronous communication while ensuring casual independence Necessitates the maintaining of an unbounded buffer

Colouring and Causal Flow l l The box pi calculus is extended to handle coloring Output processes are annotated with the sets of colours that record their histories – l The sets of principles that have effected them in the past Very simple colouring that only captures a limited amount of causality information

Causality Types l l The type system statically captures causal flows A wrapper can be shown to satisfy the causal flow property simply by checking that it is welltyped

Discussion l l Wrappers impose security policies on components for which it is impractical to analyze the internal structure Alternative policies – – Java style sand boxing Code signing

Conclusions l Provided techniques for proving that software wrappers enforce user specified flow constraints l Security is solely a function of causality