Secure Credit Card Transactions on an Untrusted Channel







- Slides: 11

Secure Credit Card Transactions on an Untrusted Channel Source: Information Sciences in review Presenter: Tsuei-Hung Sun (孫翠鴻) Date: 2010/9/24 1

Outline • • Introduction Motivation Scheme Security analysis Performance evaluation Advantage vs. weakness Comment 2

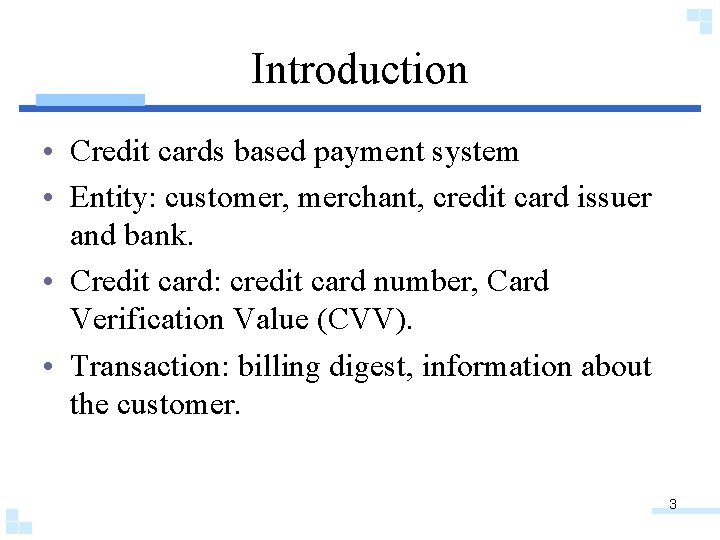
Introduction • Credit cards based payment system • Entity: customer, merchant, credit card issuer and bank. • Credit card: credit card number, Card Verification Value (CVV). • Transaction: billing digest, information about the customer. 3

Introduction • Secure Socket Layer (SSL) – Establish a trusted connection between two parties. • HTTPS (Secure HTTP) – Send messages securely using SSL. • Both two need public keys and certificates, besides, the operations process are complex. 4

Motivation • SSL and HTTPS are complex because they involve key-management, user credentials and certificates. • Smart cards require extra infrastructure like smart card reader and middleware. • This paper want to let the transaction become more simpler and easy to achieve security. 5

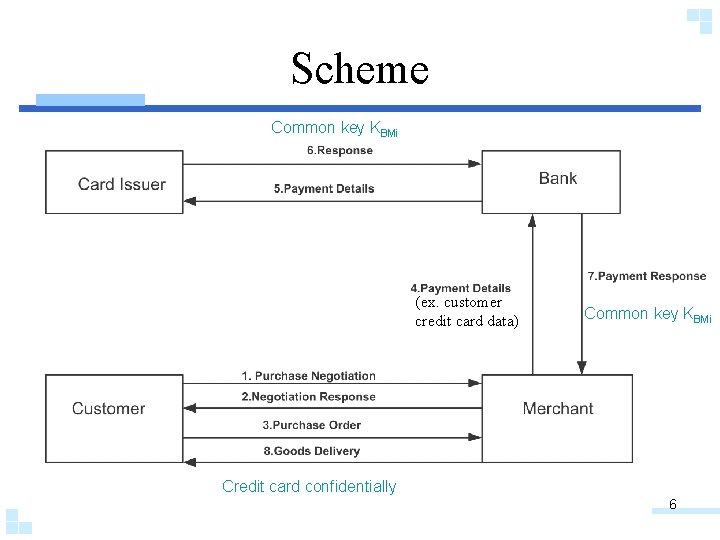
Scheme Common key KBMi (ex. customer credit card data) Common key KBMi Credit card confidentially 6

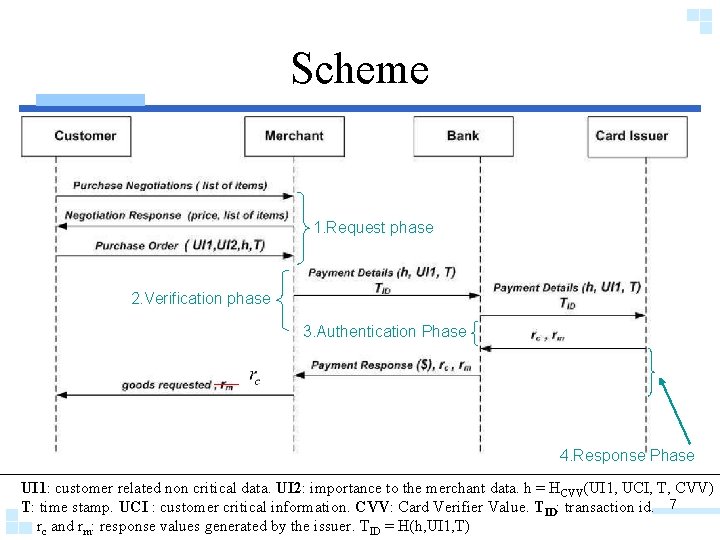
Scheme 1. Request phase 2. Verification phase 3. Authentication Phase 4. Response Phase UI 1: customer related non critical data. UI 2: importance to the merchant data. h = HCVV(UI 1, UCI, T, CVV) T: time stamp. UCI : customer critical information. CVV: Card Verifier Value. TID: transaction id. 7 rc and rm: response values generated by the issuer. TID = H(h, UI 1, T)

Scheme • Authentication Phase – Issuer has a database containing customer credit card data. A 1 Retrieve CVV and UCI from database. A 2 Compute hash value h 1. A 3 Comparing h and h 1 consistency. A 4 Generate response values Accept: Reject: A 5 Send acknowledgement to bank. 8 : common key between the bank and the merchant i.

Security analysis • • Replay Attack Forgery Attack Man-in-the-Middle Attack Guessing Attack 9

Performance evaluation • Complexity Comparison Request phase: exor operation, hash operation (bank). Verification phase: hash operation (merchant), intersection operation (issuer). Authentication phase: exor operations (issuer). 10

Advantage vs. weakness • Advantage – Can resist 4 type important attack. – No need complex computing. – No need extra overhead like smart card, reader and middleware. – Just use hash function and a common key. – just use a one round protocol. • Weakness – Common key may be weak. 11
 Debit cards advantages and disadvantages
Debit cards advantages and disadvantages Checking account and debit card simulation
Checking account and debit card simulation Ssl decryption explained
Ssl decryption explained Secure electronic payment
Secure electronic payment Part two analyzing the effect of transactions
Part two analyzing the effect of transactions Remote side-channel attacks on anonymous transactions
Remote side-channel attacks on anonymous transactions Secure communication channel
Secure communication channel This can be avoided by giving credit where credit is due.
This can be avoided by giving credit where credit is due. Credit channel example
Credit channel example Single channel marketing
Single channel marketing Conversion of continuous awgn channel to vector channel
Conversion of continuous awgn channel to vector channel Jfet self bias configuration
Jfet self bias configuration