Reflections on Trusting Trust Ken Thompson Overview n










- Slides: 16

Reflections on Trusting Trust Ken Thompson

Overview n n Introduction “Cutest Program” Stage 1 n Stage 2 n Stage 3 n n n Moral Conclusion

Introduction n n The author’s acknowledgement UNIX Background Presentation

“Cutest Program” n Stage 1 Shortest self-reproducing program n Write a source program that will produce an exact copy of its source n n Figure 1 Produces a self-reproducing program n Can be easily written by another program n Can contain baggage that will be reproduced along with main algorithm n Source Code next slide n

Source Code

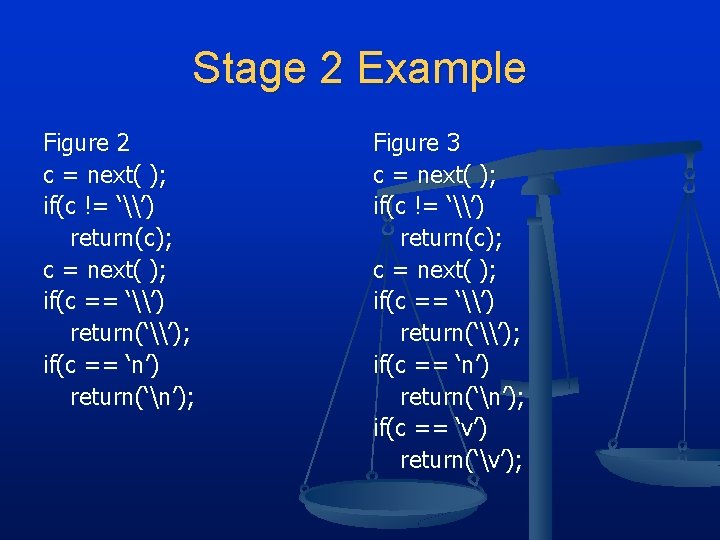
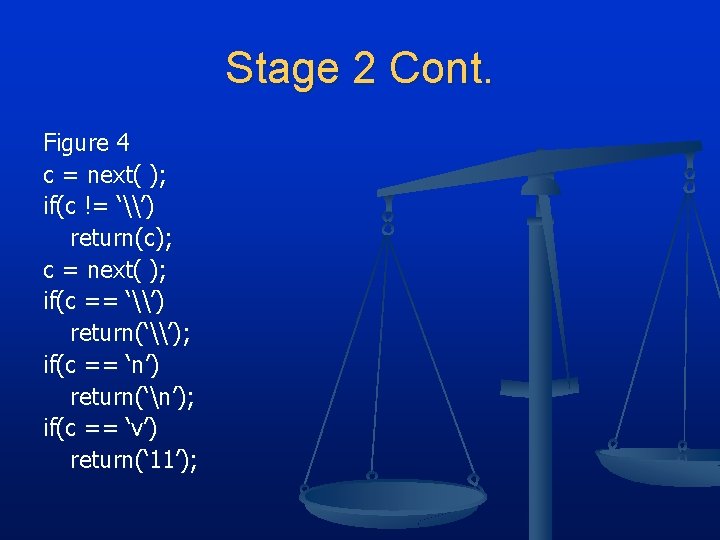
“Cutest Program” n Stage 2 n n C Compiler written in C “Chicken and egg” problem n n n Example from C compiler Figure 2 n n Compilers written in their own language C compiler interprets the character escape sequence Figure 3 and 4 n n Figure 3 adds vertical tab “v” Binary version does not know about “v” add ASCII value if(c == ‘v’) return(‘ 11’)

Stage 2 Example Figure 2 c = next( ); if(c != ‘\’) return(c); c = next( ); if(c == ‘\’) return(‘\’); if(c == ‘n’) return(‘n’); Figure 3 c = next( ); if(c != ‘\’) return(c); c = next( ); if(c == ‘\’) return(‘\’); if(c == ‘n’) return(‘n’); if(c == ‘v’) return(‘v’);

Stage 2 Cont. Figure 4 c = next( ); if(c != ‘\’) return(c); c = next( ); if(c == ‘\’) return(‘\’); if(c == ‘n’) return(‘n’); if(c == ‘v’) return(‘ 11’);

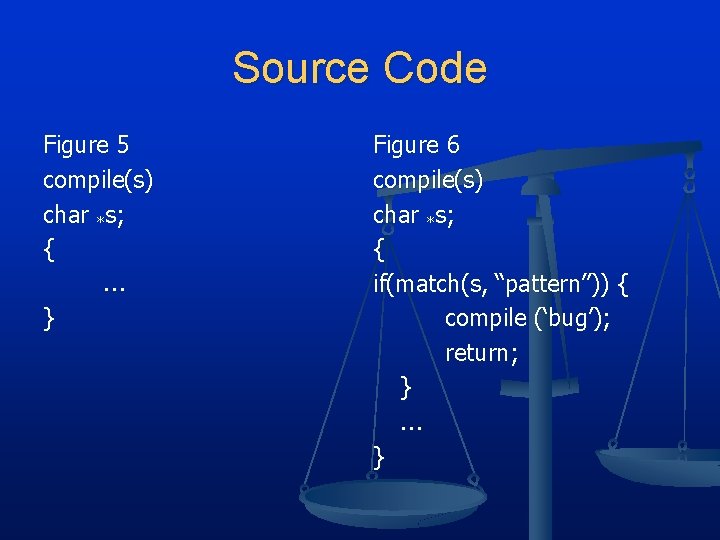
Stage 3 n n Takes the code and modifies it Figure 5 n n n High level control of the C compiler “compile” is called to compile next line of code Figure 6 n n Modified to mis-compile source when a pattern is matched Not deliberate would be a “bug”. Since deliberate should be called “Trojan horse”.

Source Code Figure 5 compile(s) char *s; { } Figure 6 compile(s) char *s; { if(match(s, “pattern”)) { compile (‘bug’); return; } }

Results of Code n n The bug planted would match code in UNIX “login” command Replacement code will miscompile login command n Giving access to login Accepting the intended encrypted password OR n Accepting a particular known password n

Source Code Figure 7 compile(s) char *s; { if(match(s, “pattern 1”)) { compile (‘bug 1’); return; } if(match(s, “pattern 2”)) { compile (‘bug 2’); return; } }

Stage 3 Cont. n Figure 7 adds a second Trojan horse. n n n Figure 7 shows the use of stage 1 by applying self-reproducing program This is done by compiling modified source with the C compiler n n n Aimed for the C compiler Produces bugged binary The binary is installed as the official C Remove the bugs from the compiler n New binary will reinsert the bugs whenever compiled

Moral n n n Can’t trust code you didn’t write Source level verification will not protect us from using untrusted code Could be done with any program-handling program n n Assembler Loaders Hardware microcode Level of program gets lower bugs will be harder to detect

Moral Cont. n n n Criticizes press on handling of hackers Author states these acts by kids are “vandalism t best” States inadequacy of law that saves hackers from real prosecution Companies are pressing to update criminal code 2 major issues n n Press, TV, and etc. call these hackers “whiz kids” The acts performed will be sending them to jail for many years

Conclusion n n Creating bugs and viruses can be simple There is a cultural gap n n Kids have no idea these are serious acts Social Stigma n Breaking into computers should be the same as breaking into homes Questions ?