Providing Realtime Security Support for Multilevel Adhoc Networks

- Slides: 10

Providing Real-time Security Support for Multi-level Ad-hoc Networks Jiejun Kong, Mario Gerla Computer Science Department University of California, Los Angeles {jkong, gerla}@cs. ucla. edu

Real-time Security Support: Characteristics Capable of processing vast amount of data in short period n n Raises performance concerns on mobile devices This work studies performance aspects of security solutions in mobile ad hoc networks Delay sensitive n Packets that incur an extra end-to-end delay are essentially useless Loss-tolerant (nearly solved) n n Occasional data loss/corruption only causes insignificant glitches Solutions: TESLA, IPsec/ESP

Mobile Real-time Applications Mobile real-time data collector n n Useful in tactical environments, paramedic emergency, news report, personal communications On-device encoding and encryption Mobile client of multimedia streaming § Pocket TV broadcasting § On-device decryption and decoding

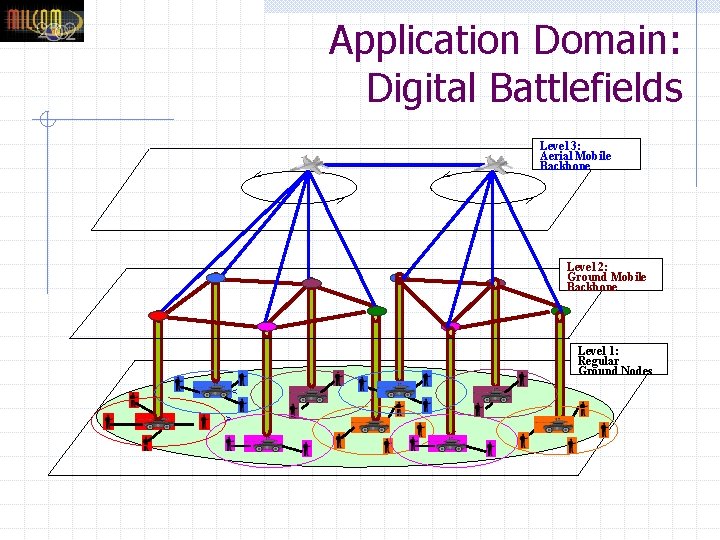
Application Domain: Digital Battlefields Level 3: Aerial Mobile Backbone Level 2: Ground Mobile Backbone Level 1: Regular Ground Nodes < >

Multi-level Heterogeneous Ad-hoc Networks Problem of homogeneous mobile ad-hoc networks n Network capacity approaches 0 when network scale increases Multi-level heterogeneous ad-hoc network provides scalability and throughput guarantees n n n Regular ground nodes Ground mobile backbone (MBN nodes) Aerial mobile backbone structure (UAV nodes) Network capacity approaches the bottleneck link capacity n E. g. , 11 Mbps in 802. 11 b, 54 Mbps in 802. 11 a

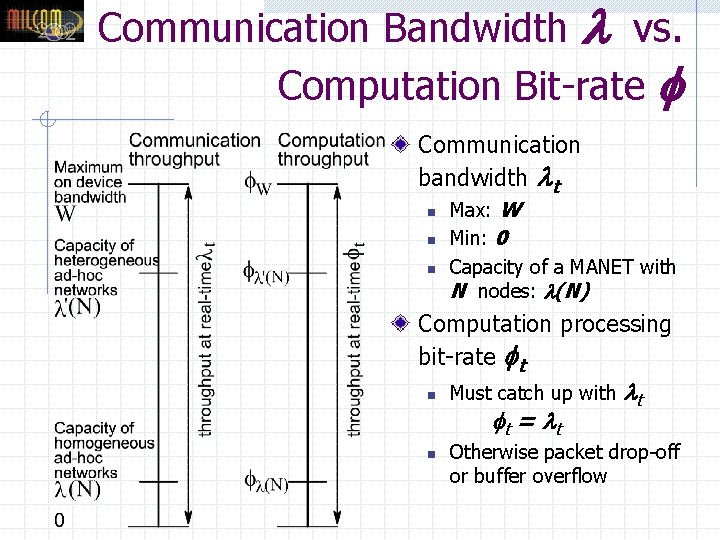
Communication Bandwidth vs. Computation Bit-rate Communication bandwidth t n n n Max: W Min: 0 Capacity of a MANET with N nodes: (N) Computation processing bit-rate t n Must catch up with t t = t n Otherwise packet drop-off or buffer overflow

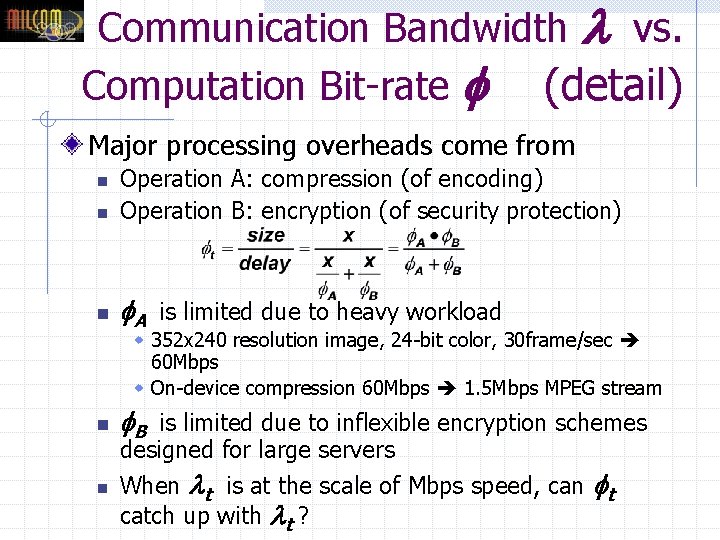
Communication Bandwidth vs. Computation Bit-rate (detail) Major processing overheads come from n Operation A: compression (of encoding) Operation B: encryption (of security protection) n A is limited due to heavy workload n w 352 x 240 resolution image, 24 -bit color, 30 frame/sec 60 Mbps w On-device compression 60 Mbps 1. 5 Mbps MPEG stream n n B is limited due to inflexible encryption schemes designed for large servers When t is at the scale of Mbps speed, can t catch up with t ?

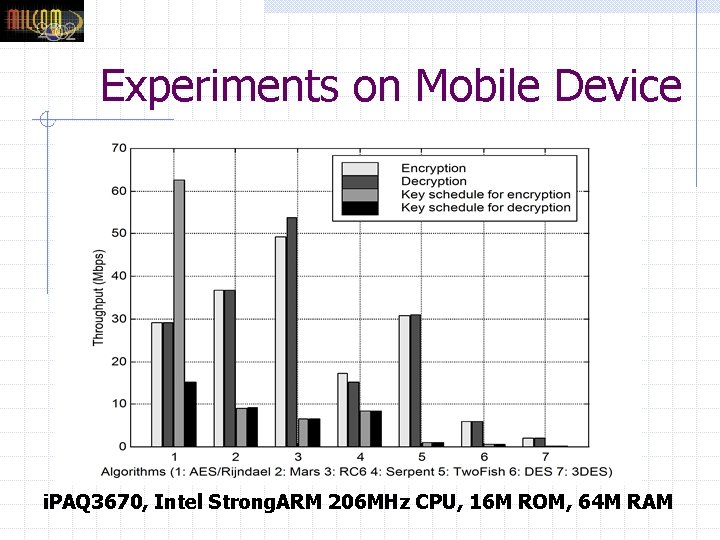
Experiments on Mobile Device i. PAQ 3670, Intel Strong. ARM 206 MHz CPU, 16 M ROM, 64 M RAM

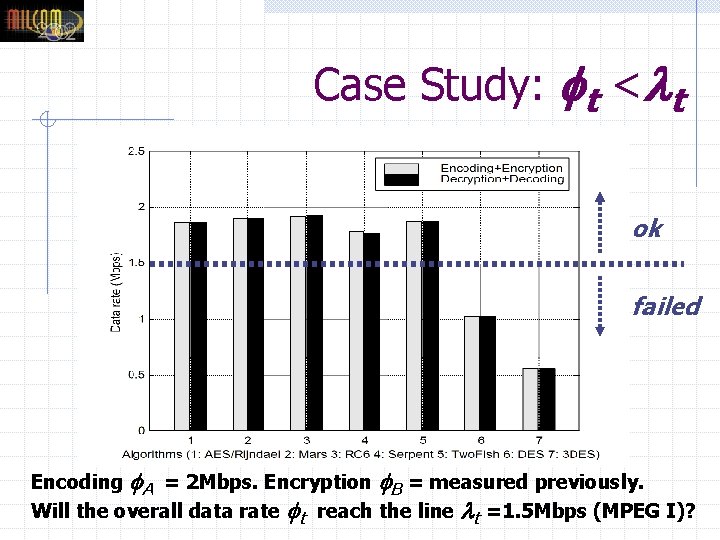
Case Study: t < t ok failed Encoding A = 2 Mbps. Encryption B = measured previously. Will the overall data rate t reach the line t =1. 5 Mbps (MPEG I)?

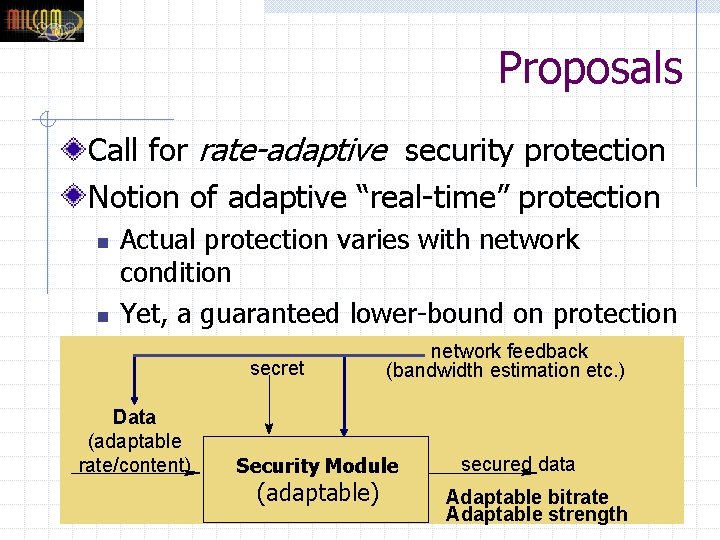
Proposals Call for rate-adaptive security protection Notion of adaptive “real-time” protection n n Actual protection varies with network condition Yet, a guaranteed lower-bound on protection secret Data (adaptable rate/content) network feedback (bandwidth estimation etc. ) Security Module (adaptable) secured data Adaptable bitrate Adaptable strength