Protecting Childrens Personal Information Using Contextual Integrity Theory








- Slides: 13

Protecting Children’s Personal Information: Using Contextual Integrity Theory to Examine Information Boundary on Mobile Devices Ying Chen*, Sencun Zhu*, Yilu Zhou+, Heng Xu* *The Pennsylvania State University +Fordham University

Children’s Privacy Risk with Mobile Use • 25% of toddlers used their parents’ smartphones in 2011 • 48% of American children aged between 6 and 12 want i. Pad for Christmas gift • Nearly 10% children get first mobile phone by the age 5

Children’s Privacy Risk with Mobile Use • Children’s personal information (CPI) can be easily leaked via mobile use • Sharing CIP on mobile devices to third-parties exposes children to risks such as cyber-solicitation • Only 13% of mobile apps have privacy policies regarding collection and distribution of children’s personal information

Parents Unaware of Privacy Risks

Let strangers know these information is dangerous for children • Where are you at this moment? • How can I bond with you?

Contextual Integrity Theory as a Theoretical Framework • We use the contextual integrity theory to examine information boundaries on mobile platforms • We aim at developing quantitative measures of privacy risks on children’s mobile apps • We propose context-based mobile privacy controls, and perform a case study to examine the information boundaries among the top 49 coloring apps

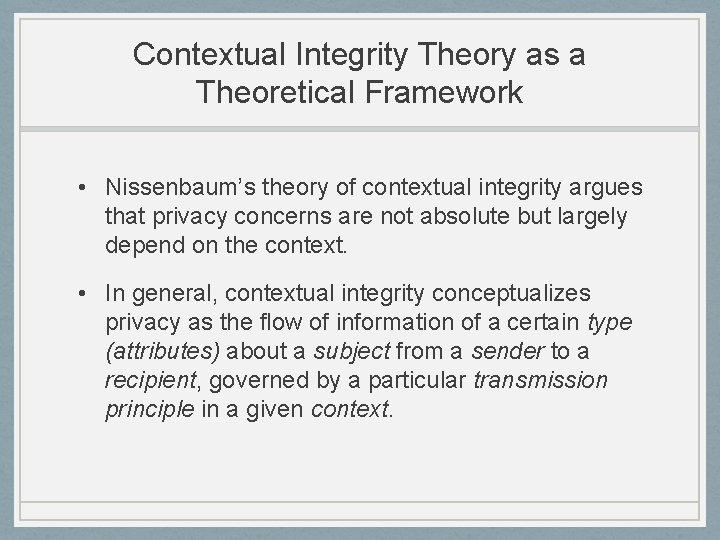
Contextual Integrity Theory as a Theoretical Framework • Nissenbaum’s theory of contextual integrity argues that privacy concerns are not absolute but largely depend on the context. • In general, contextual integrity conceptualizes privacy as the flow of information of a certain type (attributes) about a subject from a sender to a recipient, governed by a particular transmission principle in a given context.

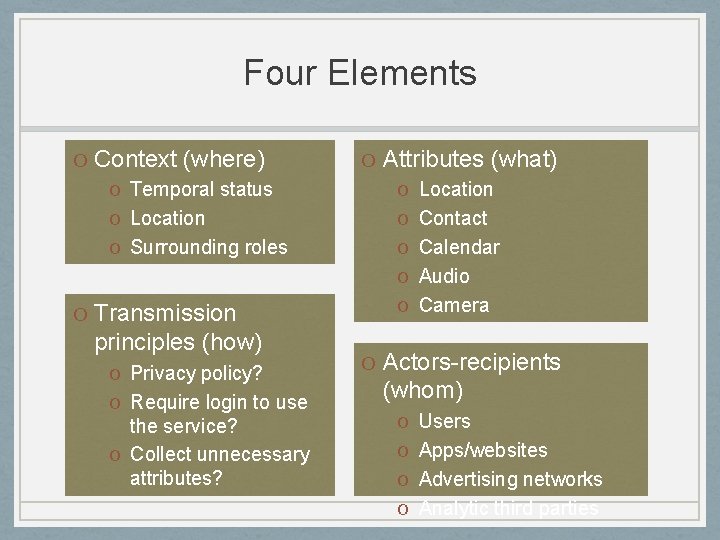
Four Elements O Context (where) O Temporal status O Location O Surrounding roles O Transmission principles (how) O Privacy policy? O Require login to use the service? O Collect unnecessary attributes? O Attributes (what) O Location O Contact O Calendar O Audio O Camera O Actors-recipients (whom) O Users O Apps/websites O Advertising networks O Analytic third parties

Case Study • Exploiting contextual integrity theory to • Establish a context-based access control mechanism on mobile platforms • Quantitatively measure privacy risks of children’s mobile apps

Context-based Access Control on Mobile Platforms • The safety level of disclosing CPI on mobile devices highly depends on the context • When children use mobile devices in risky times, unprotected locations, or without guardians’ companion, mobile platforms should automatically limit the disclosure of CPI • Rules can be designed on mobile platforms to limit disclosure of certain types of CPI under certain context

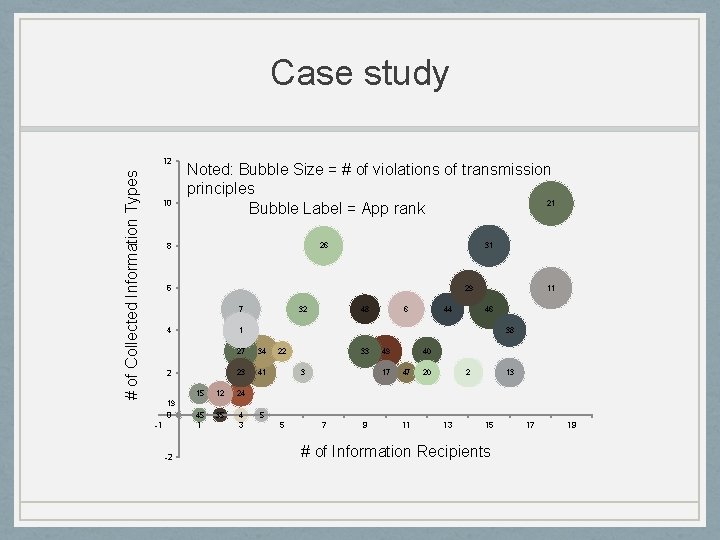
Quantitative Privacy Risk Measures on Mobile Apps • Measure the privacy risk levels of mobile apps with three dimensions in contextual integrity: 1. actors, 2. attributes, and 3. transmission principles • We conducted an experiment to show the proposed method can effectively measure apps’ privacy risks and help parents choose safe apps for their children.

Case study # of Collected Information Types 12 10 Noted: Bubble Size = # of violations of transmission principles 21 Bubble Label = App rank 8 26 31 6 29 7 4 32 48 6 44 11 46 1 2 15 12 45 35 38 27 34 23 41 22 33 3 49 17 40 47 20 2 13 24 19 0 -1 1 -2 4 3 5 5 7 9 11 13 15 # of Information Recipients 17 19

Thanks! Protecting Children’s Personal Information: Using Contextual Integrity Theory to Examine Information Boundary on Mobile Devices Ying Chen, Sencun Zhu, Yilu Zhou, Heng Xu