Proof of work to mitigate flooding attack Flooding

![References [1] From a Trickle to a Flood: Active Attacks on Several Mix Types References [1] From a Trickle to a Flood: Active Attacks on Several Mix Types](https://slidetodoc.com/presentation_image_h2/135df9218fe68867d97d407c6698f550/image-5.jpg)
- Slides: 5

Proof of work to mitigate flooding attack

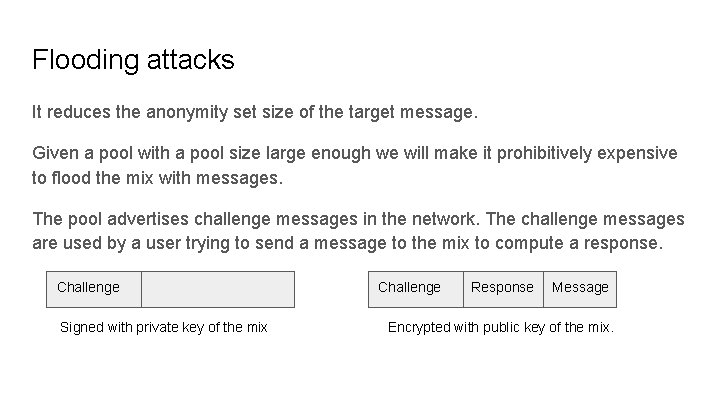
Flooding attacks It reduces the anonymity set size of the target message. Given a pool with a pool size large enough we will make it prohibitively expensive to flood the mix with messages. The pool advertises challenge messages in the network. The challenge messages are used by a user trying to send a message to the mix to compute a response. Challenge Signed with private key of the mix Challenge Response Message Encrypted with public key of the mix.

Proof of work mixes hash(challenge_token || response) = challenge_hash. We know that It is trivial for a mix to verify the proof of work but prohibitively expensive for a sender to attempt to send multiple messages to attempt a flooding attack on an honest mix. Because the mix is creating a hash challenge it is relatively very easy for the mix to create valid dummy messages. We can reduce the need for dummy messages with the exception of heartbeat messages that will ensure that the delays are not caused by an attacker delaying messages.

Resilience to attack Cryptographic hashing is a computationally heavy task which requires computational power. The implicit assumption is that the number of messages that a normal user wishes to send is far lesser than the pool size which means that it is a slight penalty for a honest user but larger overhead for an attacker. It is possible to detect an attacker blocking the messages to the mix because of the very large timeout. Mix can mark packets to be dropped at the next hop. The mix can throttle any potential attack by adjusting the computationally complexity of the challenge.
![References 1 From a Trickle to a Flood Active Attacks on Several Mix Types References [1] From a Trickle to a Flood: Active Attacks on Several Mix Types](https://slidetodoc.com/presentation_image_h2/135df9218fe68867d97d407c6698f550/image-5.jpg)
References [1] From a Trickle to a Flood: Active Attacks on Several Mix Types - Andrei Serjantov and Roger Dingledine and Paul Syverson [2] Proofs of Work and Bread pudding protocol - Markus Jakobsson [3] Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms - David Chaum [4] A Reputation System to Increase MIX-net Reliability - Roger Dingledine , Michael J. Freedman , David Hopwood , David Molnar