PIV 1 Ketan Mehta Ketan mehtanist gov May


- Slides: 9

PIV 1 Ketan Mehta Ketan. mehta@nist. gov May 5, 2005

PIV 1 • What does it mean to agencies • Role-based vs System-based Models • Moving forward

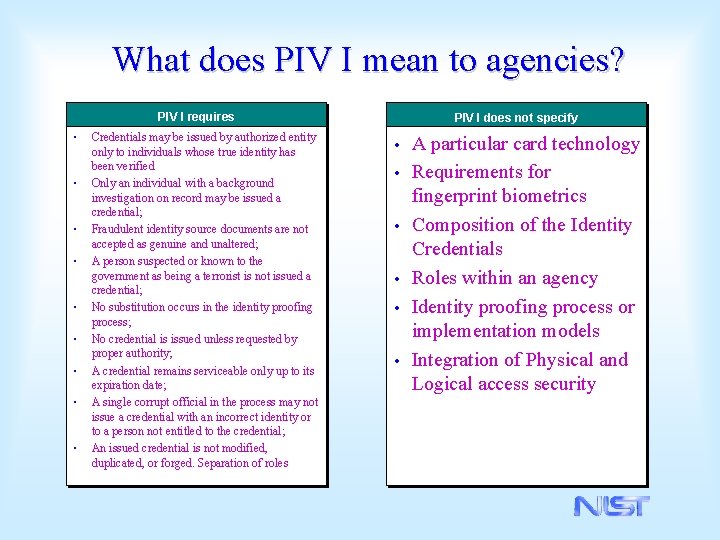
What does PIV I mean to agencies? PIV I requires • • • Credentials may be issued by authorized entity only to individuals whose true identity has been verified Only an individual with a background investigation on record may be issued a credential; Fraudulent identity source documents are not accepted as genuine and unaltered; A person suspected or known to the government as being a terrorist is not issued a credential; No substitution occurs in the identity proofing process; No credential is issued unless requested by proper authority; A credential remains serviceable only up to its expiration date; A single corrupt official in the process may not issue a credential with an incorrect identity or to a person not entitled to the credential; An issued credential is not modified, duplicated, or forged. Separation of roles PIV I does not specify • • • A particular card technology Requirements for fingerprint biometrics Composition of the Identity Credentials Roles within an agency Identity proofing process or implementation models Integration of Physical and Logical access security

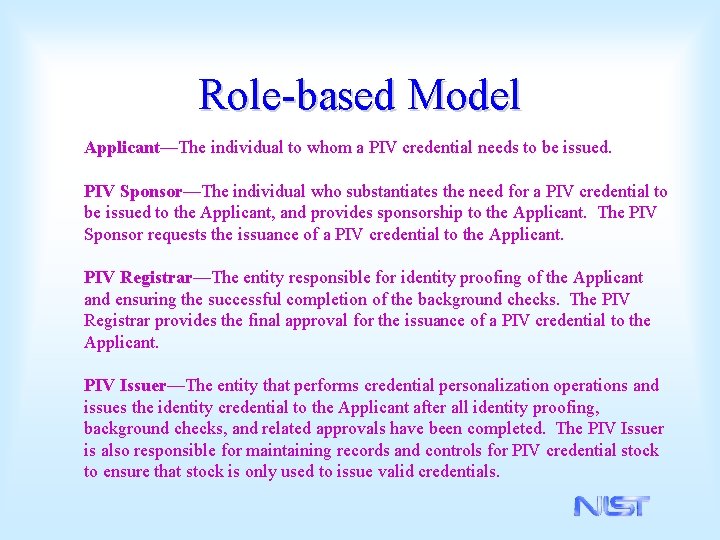
Role-based Model Applicant—The individual to whom a PIV credential needs to be issued. PIV Sponsor—The individual who substantiates the need for a PIV credential to be issued to the Applicant, and provides sponsorship to the Applicant. The PIV Sponsor requests the issuance of a PIV credential to the Applicant. PIV Registrar—The entity responsible for identity proofing of the Applicant and ensuring the successful completion of the background checks. The PIV Registrar provides the final approval for the issuance of a PIV credential to the Applicant. PIV Issuer—The entity that performs credential personalization operations and issues the identity credential to the Applicant after all identity proofing, background checks, and related approvals have been completed. The PIV Issuer is also responsible for maintaining records and controls for PIV credential stock to ensure that stock is only used to issue valid credentials.

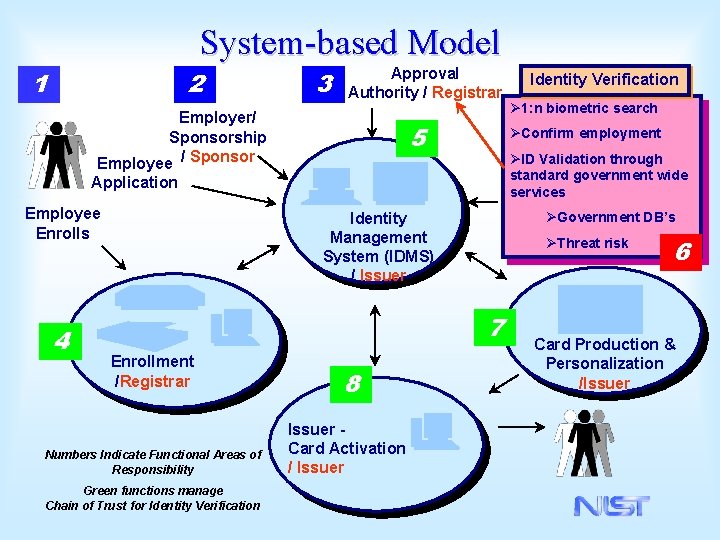
System-based Model 1 2 3 Approval Authority / Registrar Employer/ Sponsorship Employee / Sponsor 5 4 ØID Validation through standard government wide services Identity Management System (IDMS) / Issuer ØGovernment DB’s ØThreat risk 7 Enrollment /Registrar Numbers Indicate Functional Areas of Responsibility Green functions manage Chain of Trust for Identity Verification 8 Issuer Card Activation / Issuer Ø 1: n biometric search ØConfirm employment Application Employee Enrolls Identity Verification 6 Card Production & Personalization /Issuer

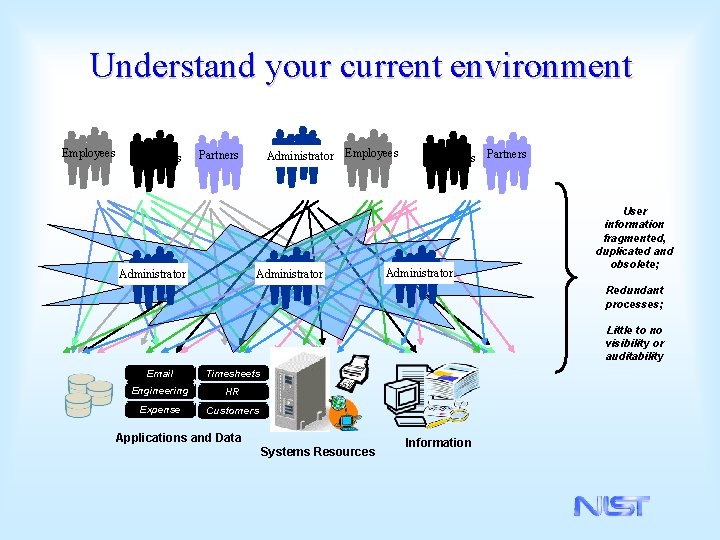
Understand your current environment Employees Customers Administrator Employees Partners Administrator Customers Partners Administrator User information fragmented, duplicated and obsolete; Redundant processes; Little to no visibility or auditability Email Timesheets Engineering HR Expense Customers Applications and Data Systems Resources Information

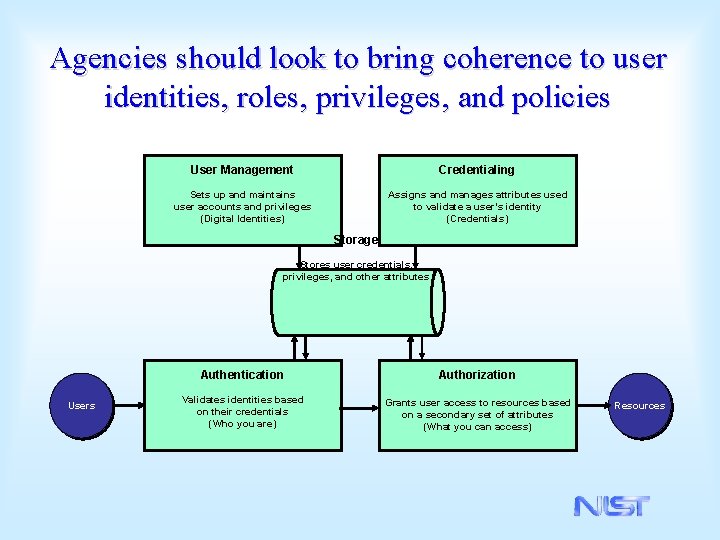
Agencies should look to bring coherence to user identities, roles, privileges, and policies User Management Credentialing Sets up and maintains user accounts and privileges (Digital Identities) Assigns and manages attributes used to validate a user’s identity (Credentials) Storage Stores user credentials, privileges, and other attributes Users Authentication Authorization Validates identities based on their credentials (Who you are) Grants user access to resources based on a secondary set of attributes (What you can access) Resources

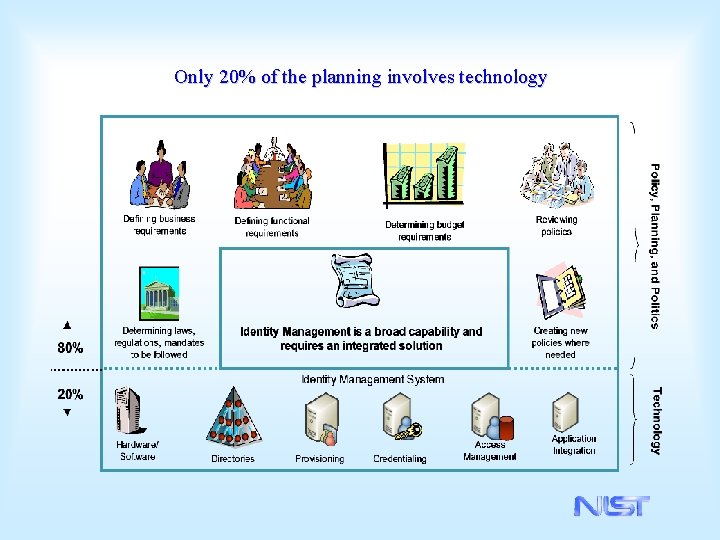
Only 20% of the planning involves technology

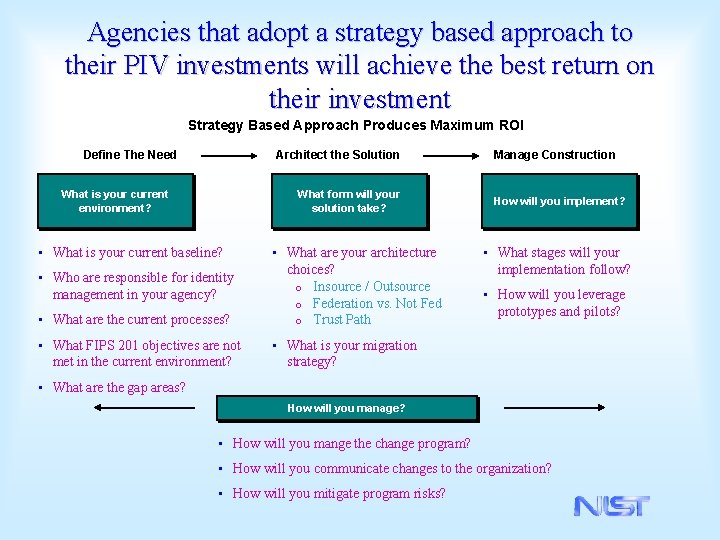
Agencies that adopt a strategy based approach to their PIV investments will achieve the best return on their investment Strategy Based Approach Produces Maximum ROI Architect the Solution Define The Need What is your current environment? What form will your solution take? • What is your current baseline? • Who are responsible for identity management in your agency? • What are the current processes? • What FIPS 201 objectives are not met in the current environment? • What are your architecture choices? o Insource / Outsource o Federation vs. Not Fed o Trust Path Manage Construction How will you implement? • What stages will your implementation follow? • How will you leverage prototypes and pilots? • What is your migration strategy? • What are the gap areas? How will you manage? • How will you mange the change program? • How will you communicate changes to the organization? • How will you mitigate program risks?