Outline Priority Inversion Priority Inheritance Protocol 2 Resource








- Slides: 17


Outline • Priority Inversion • Priority Inheritance Protocol 2 嵌入式即時作業系統

Resource • A resource is any software structure – A variable, a memory area, a file, etc. • A resource may be shared or private. • Exclusive resource – A shared resource that is protected against concurrent access • A piece of code executed under mutual exclusion to guarantee exclusive resource accesses is called critical section 3 嵌入式即時作業系統

Priority Inversion • A high-priority job can experience two kinds of blocking – Bounded • For example, a high-priority job waits for the executions of a lowpriority job to acquire a resource • The blocking time is no longer than that of the critical section where the lower priority job owns the resources • Necessary to ensure resource consistence – Unbounded • When a third job preempts the low-priority job during the inversion, thus delaying the high-priority job even more • Would lead to uncontrolled blocking and cause high-priory job miss its deadline • Have to be solved 4 嵌入式即時作業系統

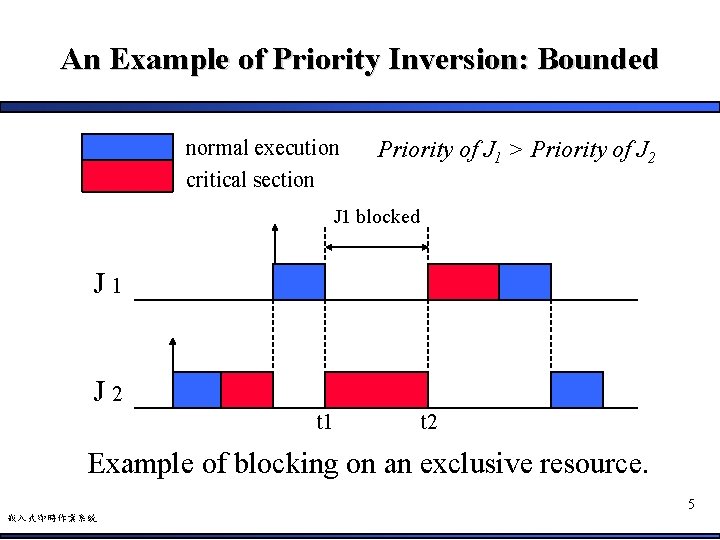
An Example of Priority Inversion: Bounded normal execution critical section Priority of J 1 > Priority of J 2 J 1 blocked J 1 J 2 t 1 t 2 Example of blocking on an exclusive resource. 5 嵌入式即時作業系統

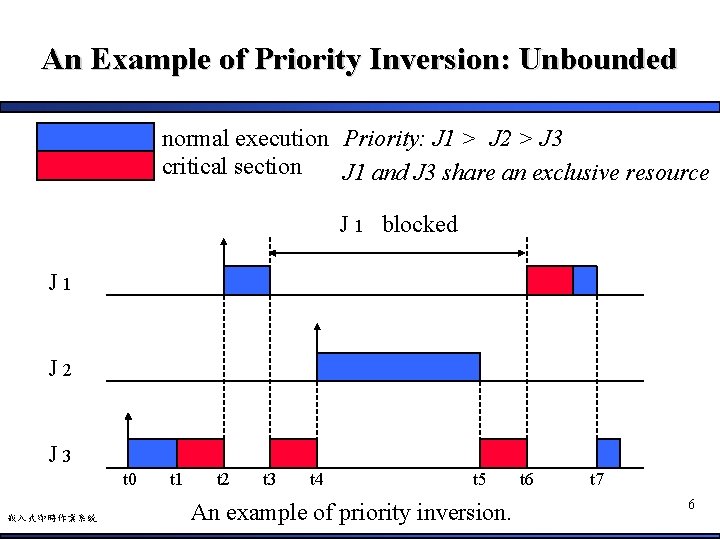
An Example of Priority Inversion: Unbounded normal execution Priority: J 1 > J 2 > J 3 critical section J 1 and J 3 share an exclusive resource J 1 blocked J 1 J 2 J 3 t 0 嵌入式即時作業系統 t 1 t 2 t 3 t 4 t 5 An example of priority inversion. t 6 t 7 6

Priority Inversion (Cont. ) • Solution – Disallow preemption during the execution of all critical sections • Only appropriate for very short critical sections because it may create unnecessary blocking – Priority Inheritance Protocol – Priority Ceiling Protocol 7 嵌入式即時作業系統

Priority Inheritance Protocol • When a job Ti is blocked by a lower priority job Tk, Ti transmits priority to the Tk. – In general, a job inherits the highest priority of the jobs blocked by it. • Priority inheritance is transitive; – If J 3 blocks J 2, and J 2 blocks J 1, then J 3 inherits the priority of J 1 via J 2. 8 嵌入式即時作業系統

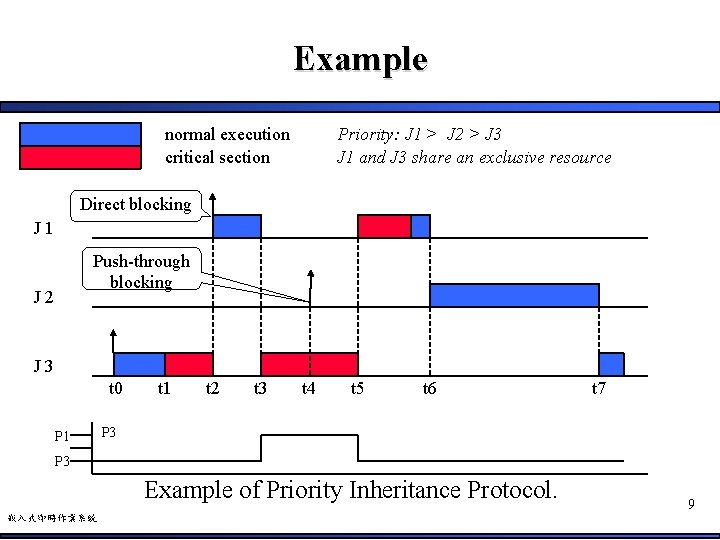
Example normal execution critical section Priority: J 1 > J 2 > J 3 J 1 and J 3 share an exclusive resource Direct blocking J 1 Push-through blocking J 2 J 3 t 0 P 1 t 2 t 3 t 4 t 5 t 6 t 7 P 3 Example of Priority Inheritance Protocol. 嵌入式即時作業系統 9

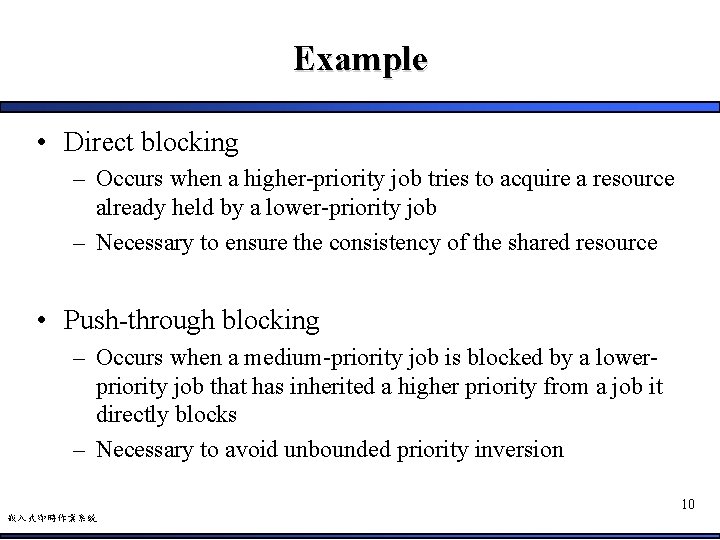
Example • Direct blocking – Occurs when a higher-priority job tries to acquire a resource already held by a lower-priority job – Necessary to ensure the consistency of the shared resource • Push-through blocking – Occurs when a medium-priority job is blocked by a lowerpriority job that has inherited a higher priority from a job it directly blocks – Necessary to avoid unbounded priority inversion 10 嵌入式即時作業系統

Priority Inheritance Protocol (Cont. ) • Unsolved problems – Chained blocking • The blocking duration for a job can still be substantial because a chain of blocking can be formed – Deadlock • The protocol does not prevent deadlocks 11 嵌入式即時作業系統

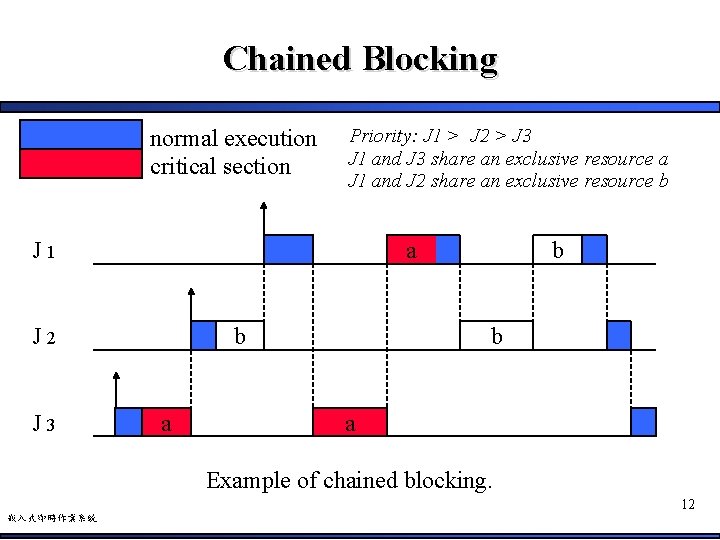
Chained Blocking normal execution critical section Priority: J 1 > J 2 > J 3 J 1 and J 3 share an exclusive resource a J 1 and J 2 share an exclusive resource b a J 1 b J 2 J 3 a b b a Example of chained blocking. 12 嵌入式即時作業系統

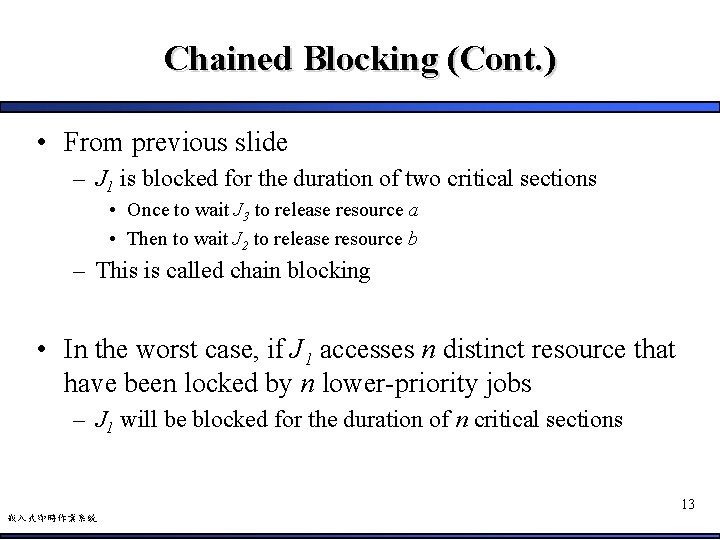
Chained Blocking (Cont. ) • From previous slide – J 1 is blocked for the duration of two critical sections • Once to wait J 3 to release resource a • Then to wait J 2 to release resource b – This is called chain blocking • In the worst case, if J 1 accesses n distinct resource that have been locked by n lower-priority jobs – J 1 will be blocked for the duration of n critical sections 13 嵌入式即時作業系統

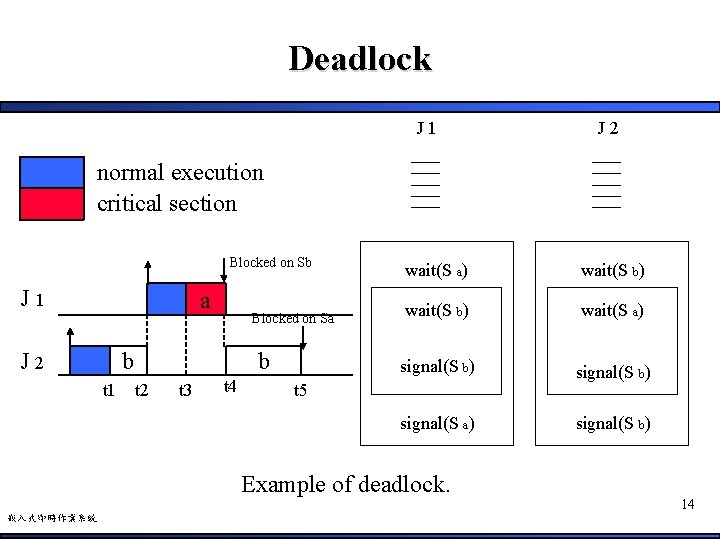
Deadlock J 1 J 2 normal execution critical section Blocked on Sb J 1 a Blocked on Sa b J 2 t 1 b t 2 t 3 t 4 wait(S a) wait(S b) wait(S a) signal(S b) signal(S a) signal(S b) t 5 Example of deadlock. 嵌入式即時作業系統 14

Deadlock (Cont. ) • Two jobs that use two semaphores in a nested fashion but in reverse order • J 1 is blocked on Sb at time t 4. Then, J 2 is blocked on Sa at time t 5 – Deadlock 15 嵌入式即時作業系統

Deadlock (Cont. ) • Notably, the deadlock does not depend on the Priority Inheritance Protocol – But is caused by an erroneous use of semaphores – The deadlock problem can be solved by the mechanisms introduced in the Operating System • E. g. , impose an total ordering on the resource access 16 嵌入式即時作業系統

Reference • Giorgio C. Buttazzo, “Hard Real-Time Computing Systems: Predictable Scheduling Algorithms and Applications, ” Kluwer Academic Publishers, 1997 • Jane W. S. Liu, “Real-Time Systems, ” Prentice Hall, 2002 17 嵌入式即時作業系統