Nov 2003 doc IEEE 802 11 03 0854







- Slides: 10

Nov 2003 doc. : IEEE 802. 11 -03 -0854 -00 -000 k Protection of Action Frames Jon Edney Markku T. Niemi Nokia Corp. Submission 1 Jon Edney, Markku Niemi, Nokia

Nov 2003 doc. : IEEE 802. 11 -03 -0854 -00 -000 k Issue • Action management frame has been defined and used in TGh. • Also proposed for use in TGe & TGk • Currently there is no security protection for action frame: – No integrity protection – No privacy Submission 2 Jon Edney, Markku Niemi, Nokia

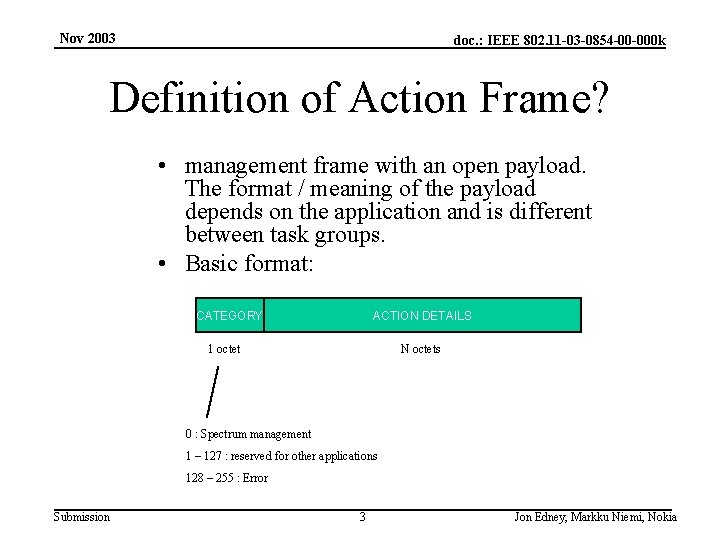
Nov 2003 doc. : IEEE 802. 11 -03 -0854 -00 -000 k Definition of Action Frame? • management frame with an open payload. The format / meaning of the payload depends on the application and is different between task groups. • Basic format: CATEGORY ACTION DETAILS 1 octet N octets 0 : Spectrum management 1 – 127 : reserved for other applications 128 – 255 : Error Submission 3 Jon Edney, Markku Niemi, Nokia

Nov 2003 doc. : IEEE 802. 11 -03 -0854 -00 -000 k Why is protection needed? • TGk plan to use the action frame to send data about the current status of stations and access points. Security policy and require that this information be private. External monitoring could reveal information such as the location of stations in a building • Forging of action frames could cause unwanted network behaviour – active attacks are possible Submission 4 Jon Edney, Markku Niemi, Nokia

Nov 2003 doc. : IEEE 802. 11 -03 -0854 -00 -000 k Suggested approaches • Don’t use actions frames – use data frame with special Ethertype • Protect all actions frames using key derived from group key • Protect unicast with pairwise key and multicast with group key Submission 5 Jon Edney, Markku Niemi, Nokia

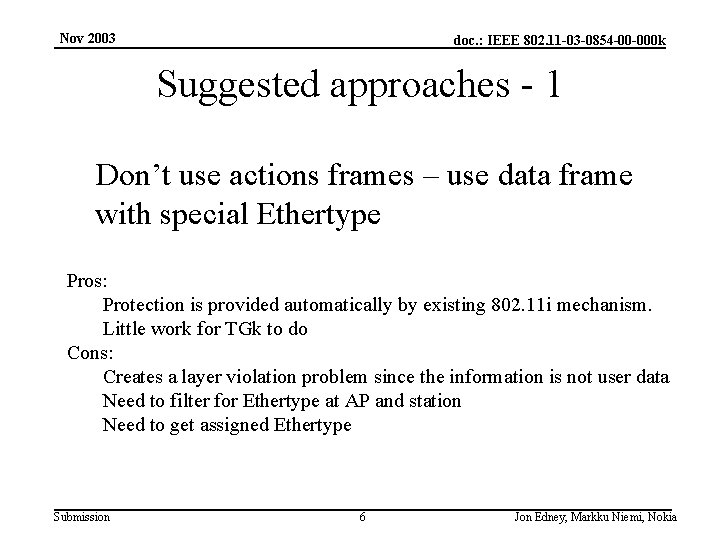
Nov 2003 doc. : IEEE 802. 11 -03 -0854 -00 -000 k Suggested approaches - 1 Don’t use actions frames – use data frame with special Ethertype Pros: Protection is provided automatically by existing 802. 11 i mechanism. Little work for TGk to do Cons: Creates a layer violation problem since the information is not user data Need to filter for Ethertype at AP and station Need to get assigned Ethertype Submission 6 Jon Edney, Markku Niemi, Nokia

Nov 2003 doc. : IEEE 802. 11 -03 -0854 -00 -000 k Suggested approaches – 2 (Recommended) Protect all actions frames using key derived from group key Pros: Able to leverage existing keys therefore no new key management is needed Can use in conjunction with security protocol used for data (e. g. 802. 11 i) Simple to implement because only one key is used for protection Cons: All association stations can see data in action frames even when these are sent via unicast Submission 7 Jon Edney, Markku Niemi, Nokia

Nov 2003 doc. : IEEE 802. 11 -03 -0854 -00 -000 k Suggested approaches - 3 Protect unicast with pairwise and multicast with group key Pros: Able to leverage existing keys therefore no new key management is needed Can use in conjunction with security protocol used for data (e. g. 802. 11 i) Per station privacy for IEEE 802. 11 i implementations Cons: Need station key look up for unicast frames Submission 8 Jon Edney, Markku Niemi, Nokia

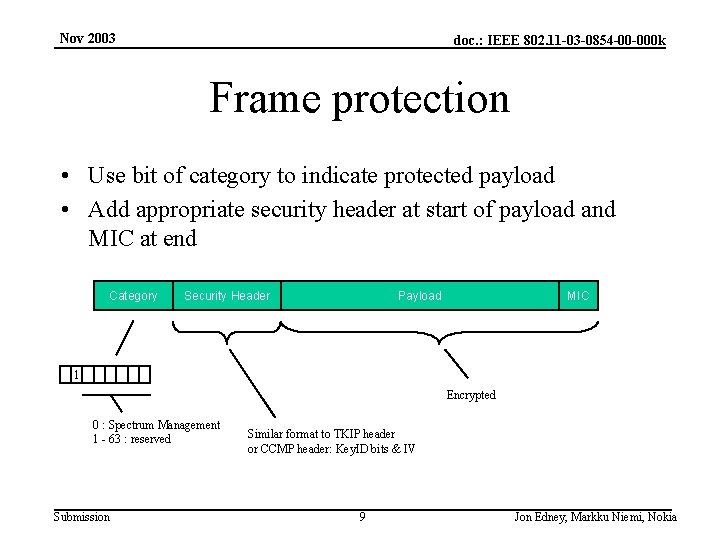
Nov 2003 doc. : IEEE 802. 11 -03 -0854 -00 -000 k Frame protection • Use bit of category to indicate protected payload • Add appropriate security header at start of payload and MIC at end Category Security Header Payload MIC 1 Encrypted 0 : Spectrum Management 1 - 63 : reserved Submission Similar format to TKIP header or CCMP header: Key. ID bits & IV 9 Jon Edney, Markku Niemi, Nokia

Nov 2003 doc. : IEEE 802. 11 -03 -0854 -00 -000 k Conclusion • There is a need to protect the Action Management Frame • We are recommending an approach that uses the existing group key infrastructure • We propose to develop normative text for consideration by the group at the next meeting. Submission 10 Jon Edney, Markku Niemi, Nokia