Microservices Design Patterns using Spring frameworks Anil Allewar




- Slides: 22

Microservices Design Patterns – using Spring frameworks Anil Allewar 17 -Dec-2020 Confidential & Proprietary

Agenda 1 What are Microservices? 2 Guiding principles 3 Design Patterns 4 Demo 5 Questions Confidential & Proprietary 2

Guidelines! ? This meetup is for learning & discussion; please feel free to ask question! We’ll do live demo and murphy's law applies! Please be patient if we run into glitches. . Please keep your connected devices on mute unless you are asking questions! All the code for the demo is available at – 1. https: //github. com/anilallewar/microservice s-basics-spring-boot 2. https: //github. com/anilallewar/microservice s-basics-cloud-config Confidential & Proprietary 3

Microservices – what are they? Confidential & Proprietary 4

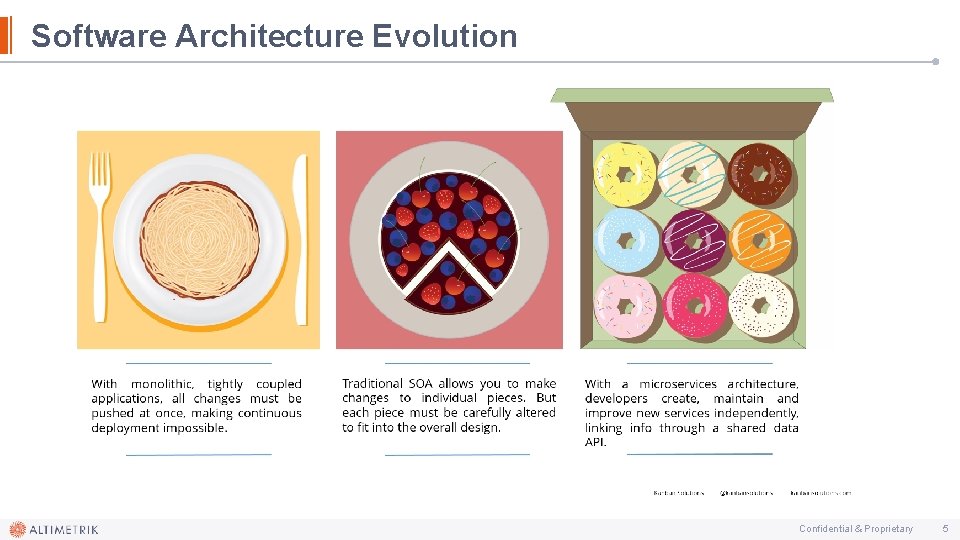
Software Architecture Evolution Confidential & Proprietary 5

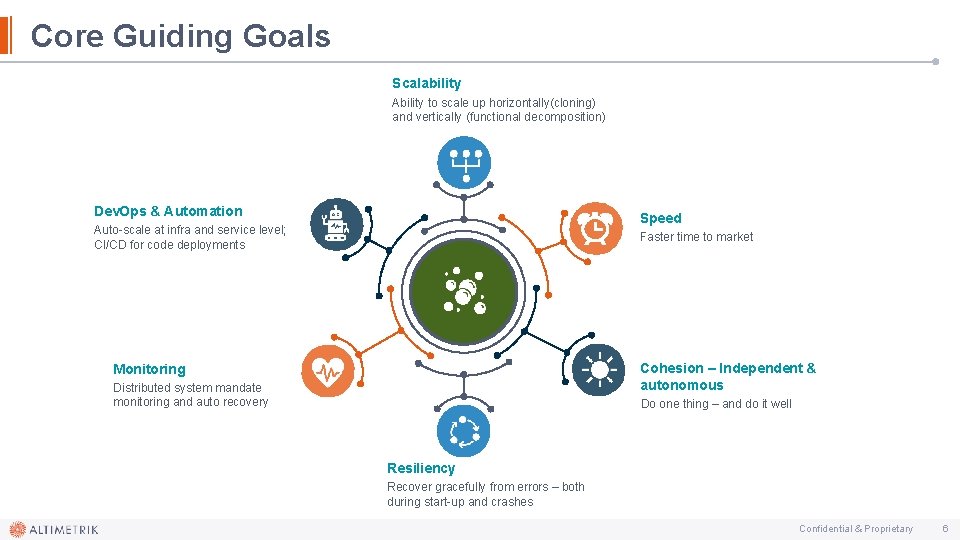
Core Guiding Goals Scalability Ability to scale up horizontally(cloning) and vertically (functional decomposition) Dev. Ops & Automation Speed Auto-scale at infra and service level; CI/CD for code deployments Faster time to market Cohesion – Independent & autonomous Monitoring Distributed system mandate monitoring and auto recovery Do one thing – and do it well Resiliency Recover gracefully from errors – both during start-up and crashes Confidential & Proprietary 6

Microservices – Design Patterns Confidential & Proprietary 7

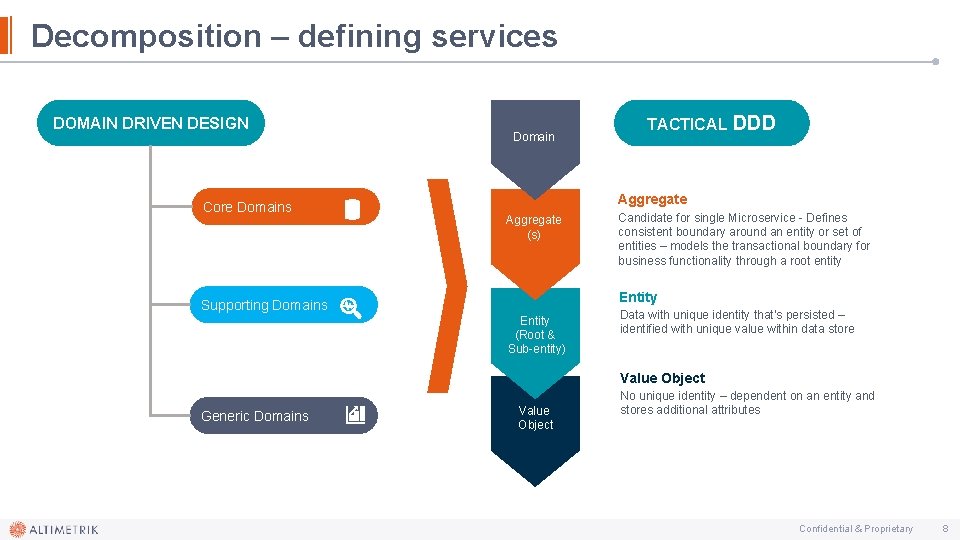
Decomposition – defining services DOMAIN DRIVEN DESIGN Core Domains Domain TACTICAL DDD Aggregate (s) Candidate for single Microservice - Defines consistent boundary around an entity or set of entities – models the transactional boundary for business functionality through a root entity Entity Supporting Domains Entity (Root & Sub-entity) Data with unique identity that’s persisted – identified with unique value within data store Value Object Generic Domains Value Object No unique identity – dependent on an entity and stores additional attributes Confidential & Proprietary 8

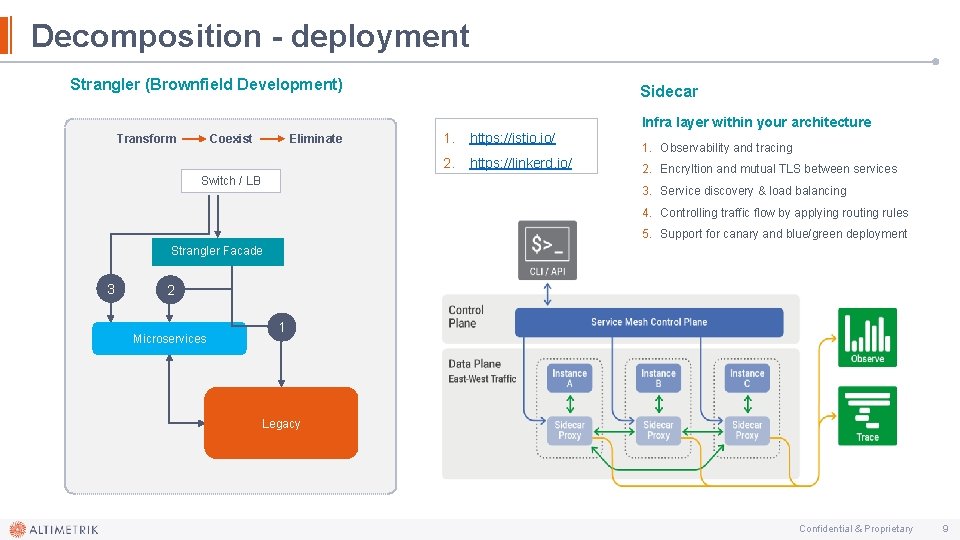
Decomposition - deployment Strangler (Brownfield Development) Transform Coexist Eliminate Switch / LB Sidecar Infra layer within your architecture 1. https: //istio. io/ 2. https: //linkerd. io/ 1. Observability and tracing 2. Encryltion and mutual TLS between services 3. Service discovery & load balancing 4. Controlling traffic flow by applying routing rules 5. Support for canary and blue/green deployment Strangler Facade 3 2 Microservices 1 Legacy Confidential & Proprietary 9

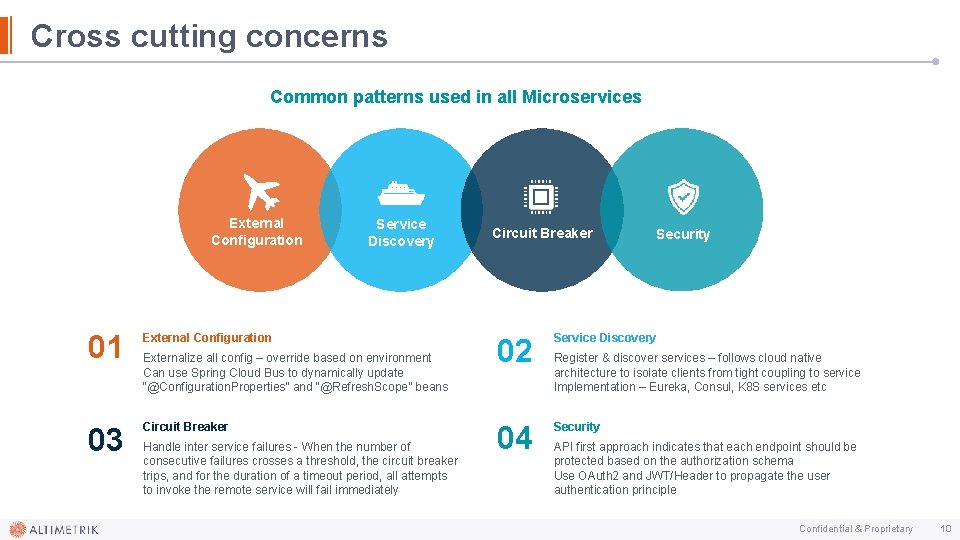
Cross cutting concerns Common patterns used in all Microservices External Configuration 01 External Configuration 03 Circuit Breaker Service Discovery Externalize all config – override based on environment Can use Spring Cloud Bus to dynamically update “@Configuration. Properties” and “@Refresh. Scope” beans Handle inter service failures - When the number of consecutive failures crosses a threshold, the circuit breaker trips, and for the duration of a timeout period, all attempts to invoke the remote service will fail immediately Circuit Breaker Security 02 Service Discovery 04 Security Register & discover services – follows cloud native architecture to isolate clients from tight coupling to service Implementation – Eureka, Consul, K 8 S services etc API first approach indicates that each endpoint should be protected based on the authorization schema Use OAuth 2 and JWT/Header to propagate the user authentication principle Confidential & Proprietary 10

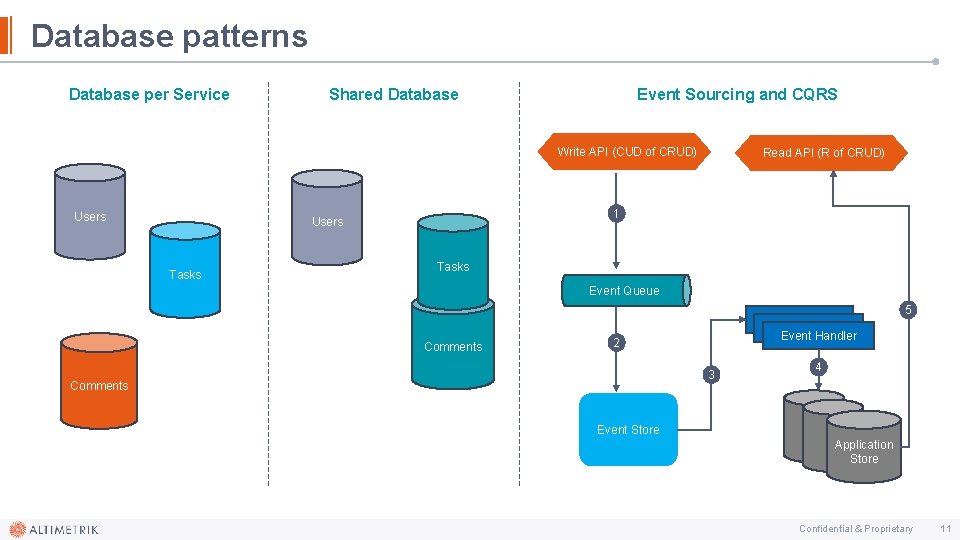
Database patterns Database per Service Event Sourcing and CQRS Shared Database Write API (CUD of CRUD) Users 1 Users Tasks Read API (R of CRUD) Tasks Event Queue 5 Comments Event Handler 2 3 Comments 4 Event Store Application Store Confidential & Proprietary 11

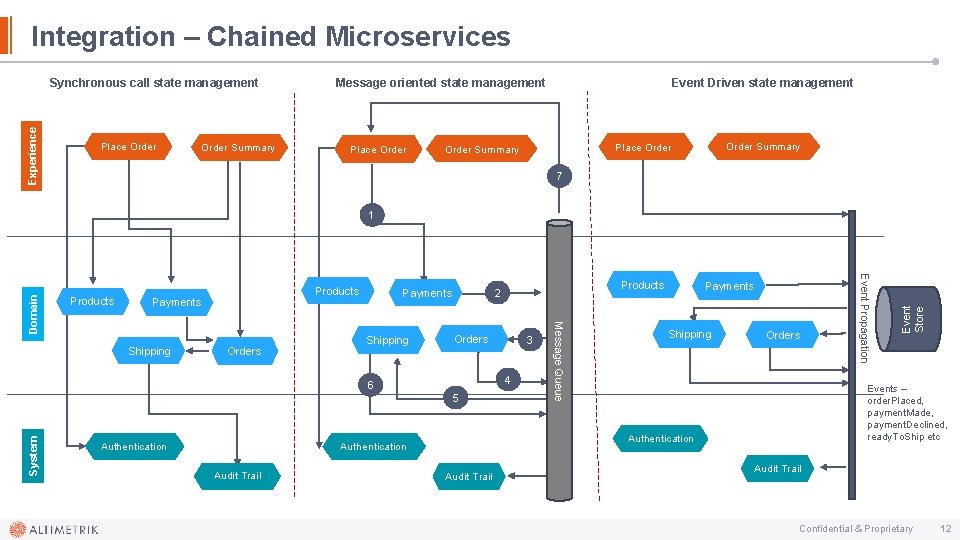
Integration – Chained Microservices Experience Synchronous call state management Place Order Summary Message oriented state management Place Order Event Driven state management Order Summary Place Order Summary 7 Shipping Orders 4 6 System 5 Authentication Shipping Orders Events – order. Placed, payment. Made, payment. Declined, ready. To. Ship etc Authentication Audit Trail 3 Payments Audit Trail Event Store Payments Products 2 Payments Event Propagation Products Message Queue Domain 1 Audit Trail Confidential & Proprietary 12

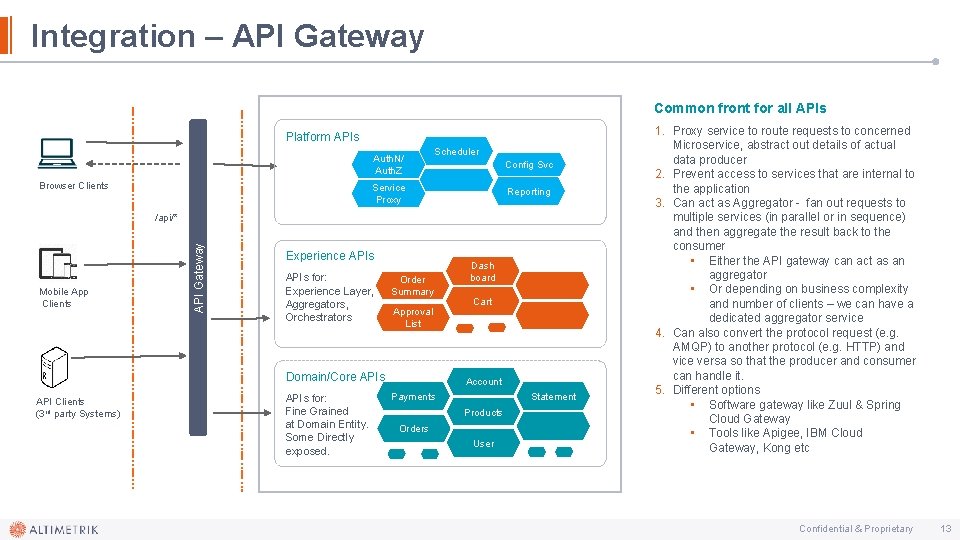
Integration – API Gateway Common front for all APIs Platform APIs Auth. N/ Auth. Z Browser Clients Service Proxy Scheduler Config Svc cv Reporting Mobile App Clients API Gateway /api/* Experience APIs for: Experience Layer, Aggregators, Orchestrators Order Summary Approval List Domain/Core APIs API Clients (3 rd party Systems) APIs for: Fine Grained at Domain Entity. Some Directly exposed. Dash board Cart Account Statement Payments Products Orders User 1. Proxy service to route requests to concerned Microservice, abstract out details of actual data producer 2. Prevent access to services that are internal to the application 3. Can act as Aggregator - fan out requests to multiple services (in parallel or in sequence) and then aggregate the result back to the consumer • Either the API gateway can act as an aggregator • Or depending on business complexity and number of clients – we can have a dedicated aggregator service 4. Can also convert the protocol request (e. g. AMQP) to another protocol (e. g. HTTP) and vice versa so that the producer and consumer can handle it. 5. Different options • Software gateway like Zuul & Spring Cloud Gateway • Tools like Apigee, IBM Cloud Gateway, Kong etc Confidential & Proprietary 13

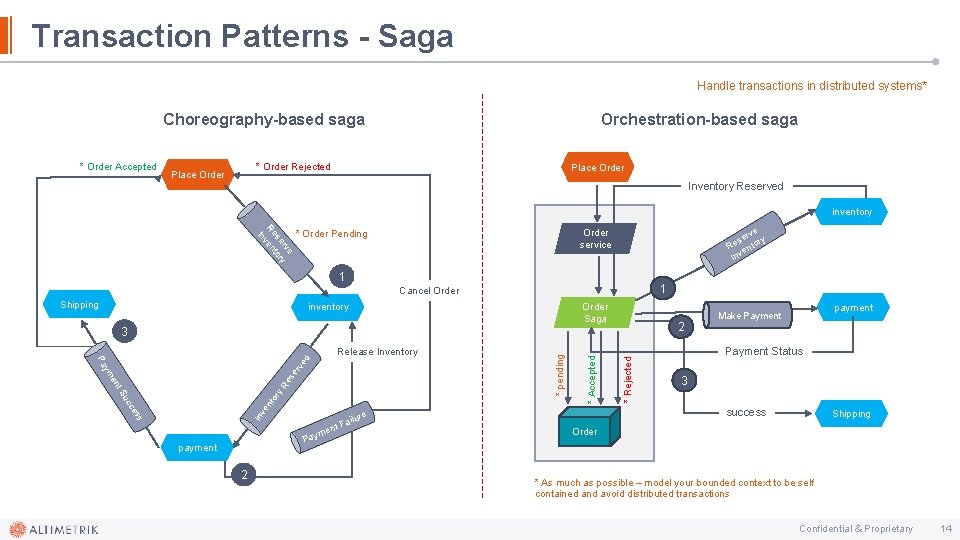
Transaction Patterns - Saga Handle transactions in distributed systems* Choreography-based saga * Order Accepted Orchestration-based saga * Order Rejected Place Order Inventory Reserved inventory e rv y se tor Re ven In rve se ory e R ent Inv Order service * Order Pending 1 1 Cancel Order Shipping inventory Order Saga 2 ss In ve ce 2 * Rejected Payment Status 3 success e ilur Fa ent m Pay payment * Accepted nt uc or t. S y. R en es er ym ve Pa d Release Inventory * pending 3 payment Make Payment Shipping Order * As much as possible – model your bounded context to be self contained and avoid distributed transactions Confidential & Proprietary 14

Observation & Monitoring Critical to troubleshoot issues with distributed systems Log Aggregator Perf Monitoring Distributed Tracing Health Check Centralized logging service that aggregates logs from each service instance – can be used to search & analyze the logs and trigger alerts based on patters. Eg: ELK / EFK stack, Amazon cloud watch, Graylog etc Monitor patterns so that application performance can be tracked & alerted for issues 1. APM tools like App. Dynamics, New. Relic etc have agents running with the Microservice that PUSH data to monitoring service 2. Tools like Prometheus PULL metrics from the Microservice Follow a single logical request (the trace) as it spans through multiple services( each being a span) that get called – specially relevant for Microservice chaining and aggregation Eg: Zipkin, Jaeger, Appdash Provide specific endpoint (such as /health) that provides information on whether the service is healthy or not. Critical to orchestrate APIs using container orchestration platform like Kubernetes Eg: Spring Actuator framework, socker based ping checks etc Confidential & Proprietary 15

What should we strive for? Confidential & Proprietary 16

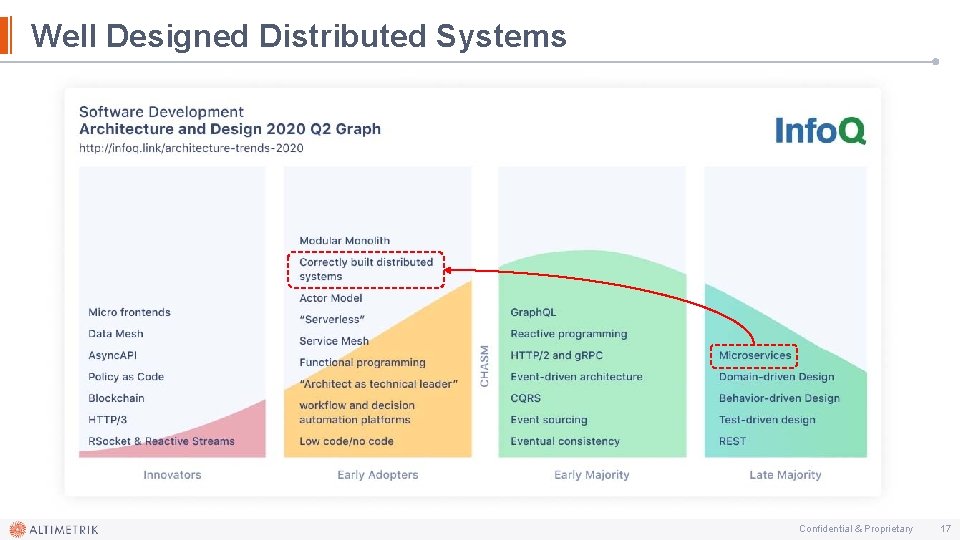
Well Designed Distributed Systems Confidential & Proprietary 17

About Altimetrik Confidential & Proprietary 18

Company Snapshot We deliver outcomes for our clients by rapidly enabling digital business & culture and infuse speed and agility into enterprise technology and connected solutions. Industry Expertise: • Retail/Consumer/Supply Chain • Banking, Financial Services • Payments and Fin. Tech • Healthcare & Pharma • Manufacturing and Automotive 2500+ Professionals Worldwide Confidential. For internal use only.

Certification and Awards

Questions? We are hiring!! https: //www. altimetrik. com/about-altimetrik/lets-talk/join-our-team/ Email - altirefer-in@altimetrik. com Confidential & Proprietary 21

Thank you Confidential & Proprietary 22